Achat
Nmap scan showed two unusual open ports of 9255 and 9256
It was unable to enumerate further.
I will perform an additional scan
┌──(kali㉿kali)-[~/archive/htb/labs/chatterbox]
└─$ nmap -Pn -sC -sV -p9255,9256 $IP
starting nmap 7.93 ( https://nmap.org ) at 2023-01-21 11:00 CET
Nmap scan report for 10.10.10.74
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
9255/tcp open http AChat chat system httpd
|_http-title: Site doesn't have a title.
|_http-server-header: AChat
9256/tcp open achat AChat chat system
service detection performed. please report any incorrect results at https://nmap.org/submit/ .
nmap done: 1 IP address (1 host up) scanned in 7.30 secondsscanning those two ports for enumeration revealed that they are used for achat
Port 9255 being HTTP, I’d image that the service is hosted over a web server
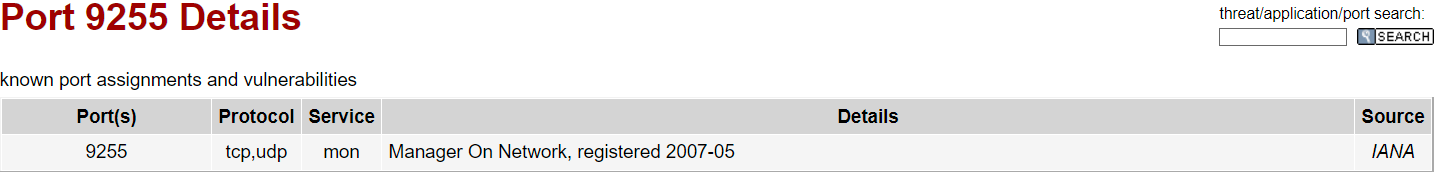
 a quick google search reveals that the UDP port
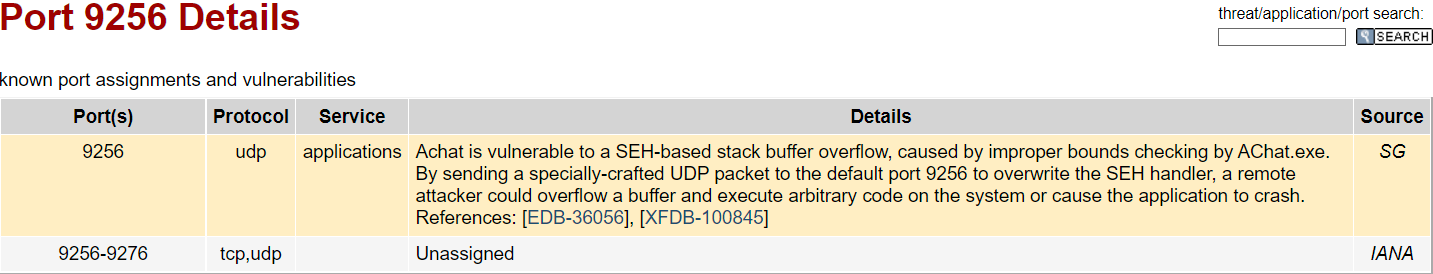
a quick google search reveals that the UDP port 9256 is indeed used for Achat
It also shows that the application is vulnerable to Buffer Overflow
Web
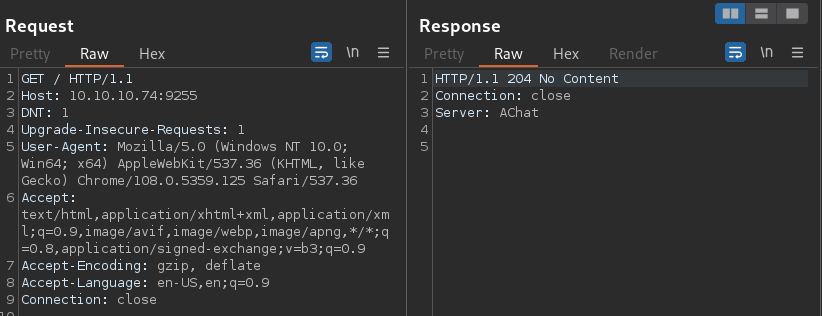 Sending a GET request to the port
Sending a GET request to the port 9255 returns a 204
I will fuzz it to see if there is any directories
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/chatterbox]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/raft-large-directories-lowercase.txt -u http://$IP:9255/FUZZ
________________________________________________
:: Method : GET
:: URL : http://10.10.10.74:9255/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-directories-lowercase.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
achat [status: 200, Size: 0, Words: 1, Lines: 1, Duration: 227ms]
cf-4 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 30ms]
ci-2 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 38ms]
cl-2 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 40ms]
ct-3 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 34ms]
du-4 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 28ms]
es-4545434 [status: 500, Size: 35, Words: 6, Lines: 1, Duration: 41ms]
mr-2 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 30ms]
uw-4 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 29ms]
uw-5 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 29ms]
vm-2 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 47ms]
sa-1 [status: 500, Size: 29, Words: 6, Lines: 1, Duration: 31ms]
:: Progress: [56164/56164] :: Job [1/1] :: 675 req/sec :: Duration: [0:01:27] :: Errors: 1107 ::ffuz return a single 200, but that is empty The rest are all 500s
Vulnerability
As noted earlier, Achat is vulnerable. But, not only does the source specifies the version, I could not enumerate it myself
┌──(kali㉿kali)-[~/archive/htb/labs/chatterbox]
└─$ searchsploit achat
------------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------------ ---------------------------------
Achat 0.150 beta7 - Remote Buffer Overflow | windows/remote/36025.py
Achat 0.150 beta7 - Remote Buffer Overflow (Metasploit) | windows/remote/36056.rb
MataChat - 'input.php' Multiple Cross-Site Scripting Vulnerabilit | php/webapps/32958.txt
Parachat 5.5 - Directory Traversal | php/webapps/24647.txt
------------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No Resultssearchsploit returns a Python script for Remote BoF on the version 0.150 I guess that’s it’s going to spray-n-pry