Web
Nmap discovered a Web server on the target port 80
The running service is Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
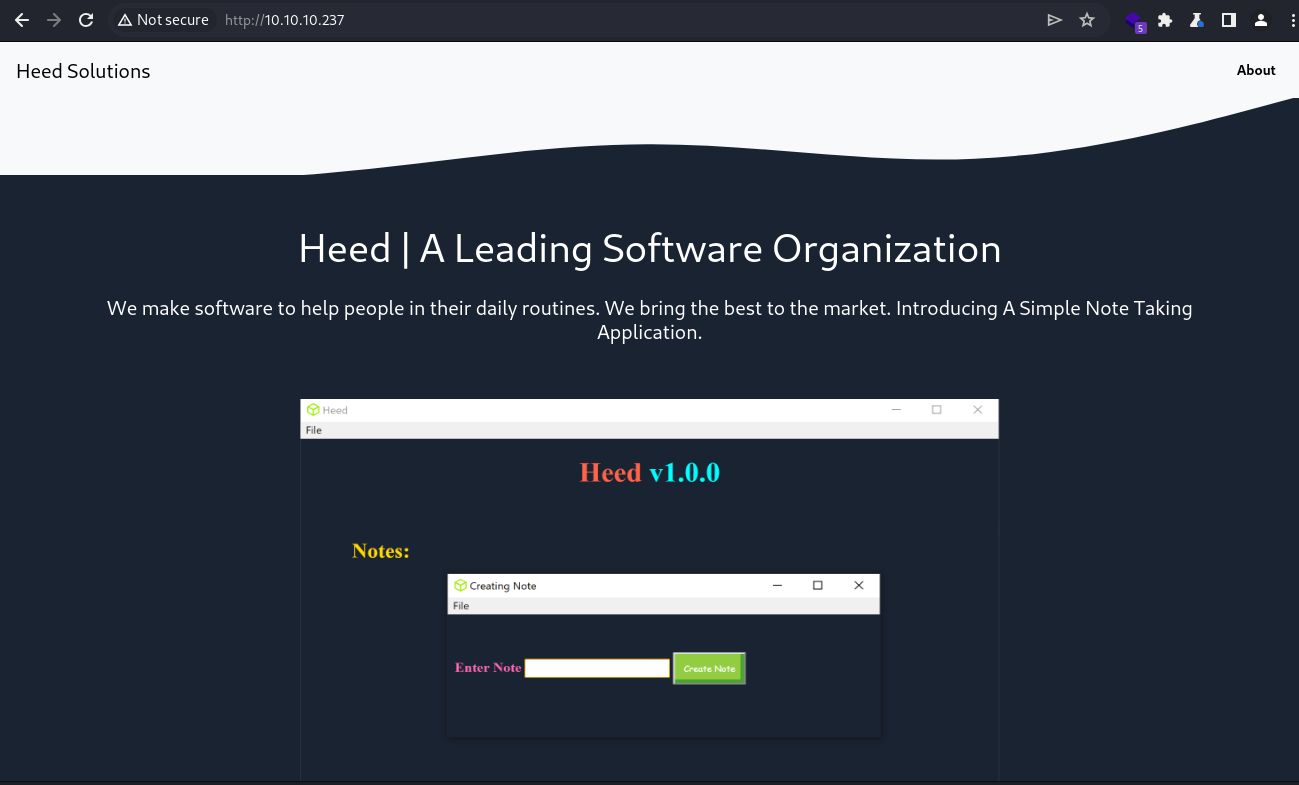 Webroot
It’s the organization behind the Heed software that was seen in the PDF file found in the target SMB server
Webroot
It’s the organization behind the Heed software that was seen in the PDF file found in the target SMB server
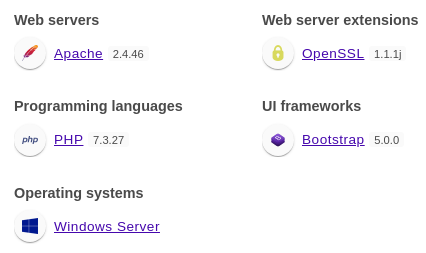 Wappalyzer identified technologies involved
It’s written in
Wappalyzer identified technologies involved
It’s written in PHP 7.3.27

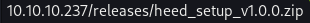 There appears to be a “Download” section that hosts the Heed software itself
It’s under the
There appears to be a “Download” section that hosts the Heed software itself
It’s under the /releases/ directory
OSX and Linux aren’t seem to be supported yet
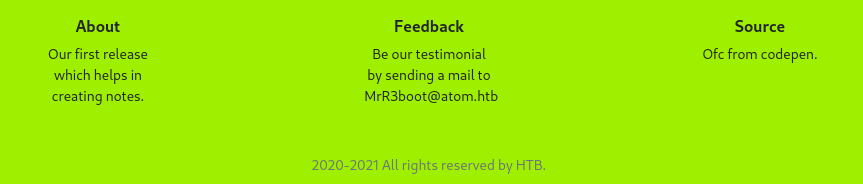 The footer contains a potential username;
The footer contains a potential username; MrR3boot
/releases/
 The archive is available at the
The archive is available at the /releases/ directory
┌──(kali㉿kali)-[~/archive/htb/labs/atom]
└─$ wget -q http://$IP/releases/heed_setup_v1.0.0.zipI will download it to Kali
Heed
┌──(kali㉿kali)-[~/archive/htb/labs/atom]
└─$ unzip heed_setup_v1.0.0.zip
archive: heed_setup_v1.0.0.zip
inflating: heedv1 Setup 1.0.0.exe
┌──(kali㉿kali)-[~/archive/htb/labs/atom]
└─$ file heedv1\ Setup\ 1.0.0.exe
heedv1 setup 1.0.0.exe: PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections
┌──(kali㉿kali)-[~/archive/htb/labs/atom]
└─$ exiftool heedv1\ Setup\ 1.0.0.exe
exiftool version number : 12.67
file name : heedv1 Setup 1.0.0.exe
directory : .
file size : 47 MB
file modification date/time : 2021:04:09 17:07:30+02:00
file access date/time : 2024:01:09 04:43:11+01:00
file inode change date/time : 2024:01:09 04:43:09+01:00
file permissions : -rwxr-xr-x
file type : Win32 EXE
file type extension : exe
mime type : application/octet-stream
machine type : Intel 386 or later, and compatibles
time stamp : 2018:01:30 04:58:52+01:00
image file characteristics : No relocs, Executable, No line numbers, No symbols, 32-bit
pe type : PE32
linker version : 6.0
code size : 26624
initialized data size : 473088
uninitialized data size : 16384
entry point : 0x338f
os version : 4.0
image version : 6.0
subsystem version : 4.0
subsystem : Windows GUI
file version number : 1.0.0.0
product version number : 1.0.0.0
file flags mask : 0x0000
file flags : (none)
file os : Win32
object file type : Executable application
file subtype : 0
language code : English (U.S.)
character set : Windows, Latin1
company name : MrR3boot
file description : Open Source Application provided by HackTheBox
file version : 1.0.0
legal copyright : Copyright © 2021 MrR3boot
product name : heedv1
product version : 1.0.0The extracted binary is a 32-bit Windows executable for installing Heed
There is a mention of MrR3boot
I will be porting it out to a Windows environment for further analysis
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/atom]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -t 200 -u http://$IP/FUZZ -ic -ic -e .txt,.html,.php
________________________________________________
:: Method : GET
:: URL : http://10.10.10.237/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
:: Extensions : .txt .html .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
images [Status: 301, Size: 338, Words: 22, Lines: 10, Duration: 40ms]
.html [Status: 403, Size: 302, Words: 22, Lines: 10, Duration: 44ms]
index.html [Status: 200, Size: 7581, Words: 2135, Lines: 192, Duration: 45ms]
releases [Status: 301, Size: 340, Words: 22, Lines: 10, Duration: 24ms]
licenses [Status: 403, Size: 421, Words: 37, Lines: 12, Duration: 24ms]
:: Progress: [830520/830520] :: Job [1/1] :: 177 req/sec :: Duration: [0:09:33] :: Errors: 8 ::Nothing new found