Web
Nmap Admirer a Web server on the target port 80
The running service is Apache httpd 2.4.25
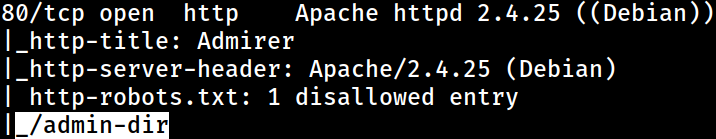 Nmap also found a single disallowed entry through the
Nmap also found a single disallowed entry through the robots.txt file
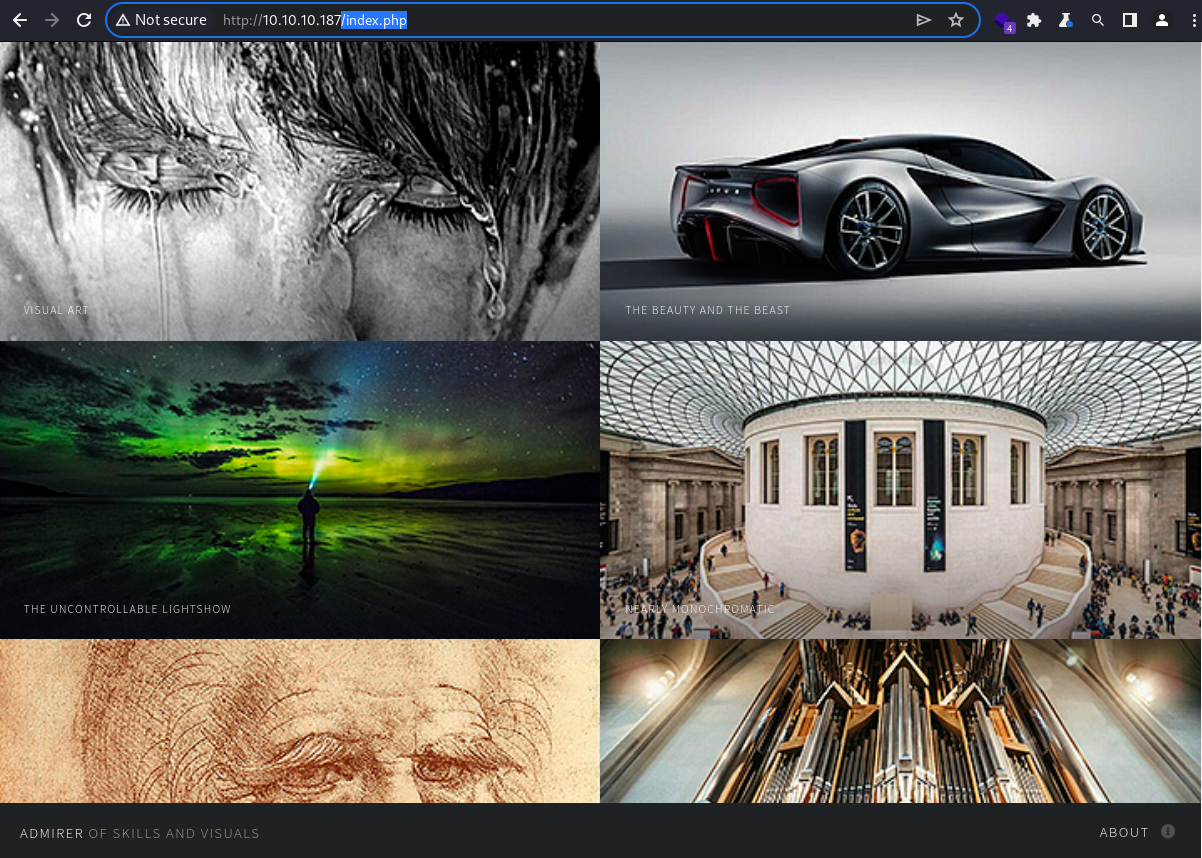 Webroot
It appears to be a personal blog, showcasing several concepts and ideas
Webroot
It appears to be a personal blog, showcasing several concepts and ideas
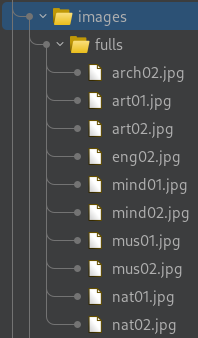 Those images seem to be loaded from the
Those images seem to be loaded from the /images/fulls directory
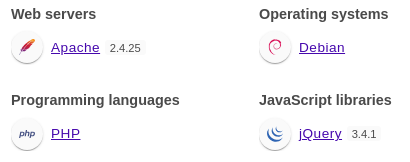 Wappalyzer identified technologies involved
It’s written in PHP
Wappalyzer identified technologies involved
It’s written in PHP
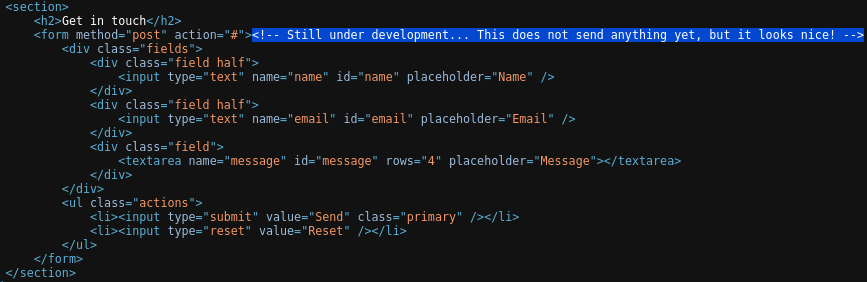 The ABOUT button opens up a contact form, which doesn’t seem to be functional as the comment in the source code suggests
That seems to be it as far as what’s visible on the webroot.
Opting out to fuzzing
The ABOUT button opens up a contact form, which doesn’t seem to be functional as the comment in the source code suggests
That seems to be it as far as what’s visible on the webroot.
Opting out to fuzzing
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/admirer]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://$IP/FUZZ -ic -e .php,.txt
________________________________________________
:: Method : GET
:: URL : http://10.10.10.187/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
images [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 88ms]
.php [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 93ms]
index.php [Status: 200, Size: 6051, Words: 385, Lines: 154, Duration: 93ms]
assets [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 88ms]
robots.txt [Status: 200, Size: 138, Words: 21, Lines: 5, Duration: 99ms]
.php [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 85ms]
server-status [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 85ms]
:: Progress: [661641/661641] :: Job [1/1] :: 460 req/sec :: Duration: [0:25:38] :: Errors: 0 ::The robots.txt file was picked up from the earlier Recon phase
robots.txt
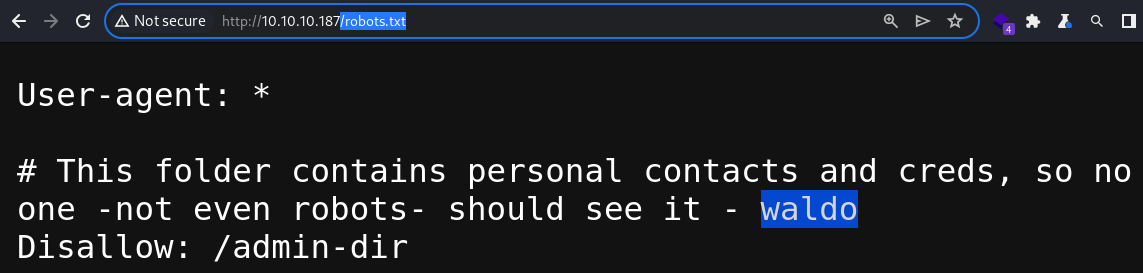 Along with the directory that was initially discovered by Nmap earlier, the
Along with the directory that was initially discovered by Nmap earlier, the robots.txt file also contains a small note made by a potential user, waldo
It mentions that the directory contains personal contacts and credentials
admin-dir
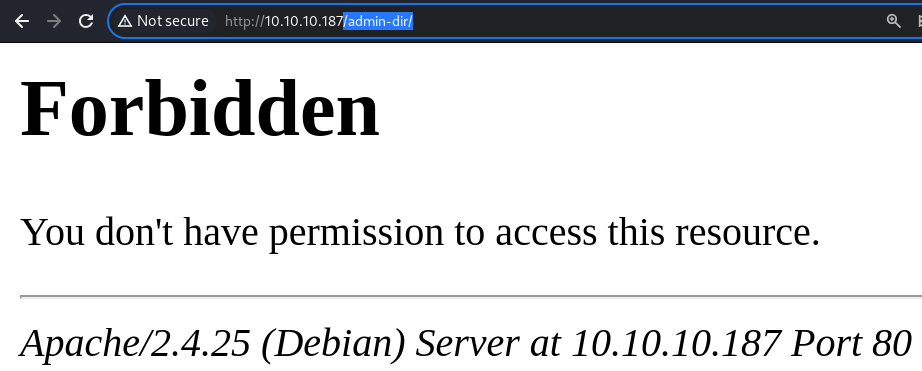 403 on the
403 on the /admin-dir/ directory
I will try to fuzz the directory
┌──(kali㉿kali)-[~/archive/htb/labs/admirer]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://$IP/admin-dir/FUZZ -ic -e .php,.txt
________________________________________________
:: Method : GET
:: URL : http://10.10.10.187/admin-dir/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .php .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
contacts.txt [Status: 200, Size: 350, Words: 19, Lines: 30, Duration: 90ms]
credentials.txt [Status: 200, Size: 136, Words: 5, Lines: 12, Duration: 96ms]
:: Progress: [661641/661641] :: Job [1/1] :: 333 req/sec :: Duration: [0:25:48] :: Errors: 0 ::Found 2 files; contacts.txt and credentials.txt
contacts.txt
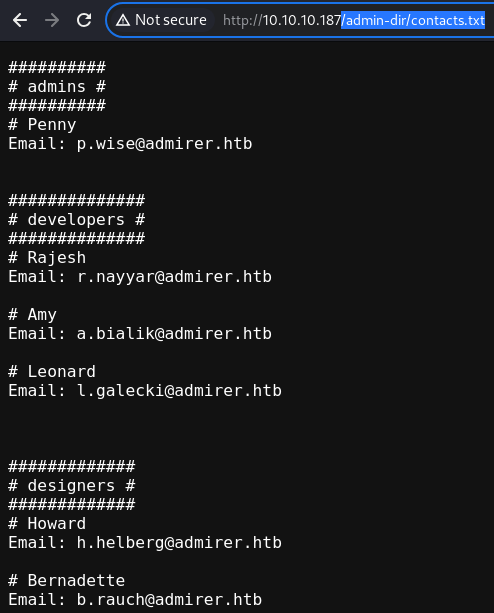 The
The contacts.txt file contains potential users and their contact information
These will be saved into a file; users.txt
Additionally, there is a domain mentioned; admirer.htb
 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resolution
credentials.txt
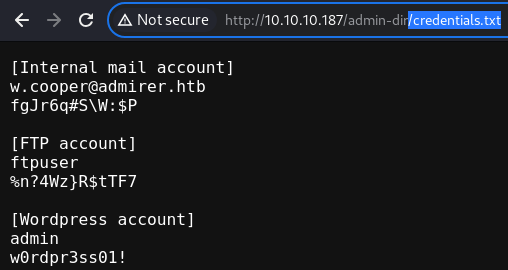 The
The credentials.txt file contains 3 credentials
One of them is for the FTP server and the other one suggests that the website might be running off of WordPress
These credentials will be saved into users.txt and passwords.txt files
utility-scripts
The FTP credential above was successfully validated to the target FTP server and it turned out to be hosting a backup archive of the Web server.
At a later stage, an unknown directory was discovered in the backup archive; /utility-scripts/
In the the following sections, I will confirm the presence of the directory in the LIVE web server
 It is present although it returned 403
It is present although it returned 403
admin_task.php
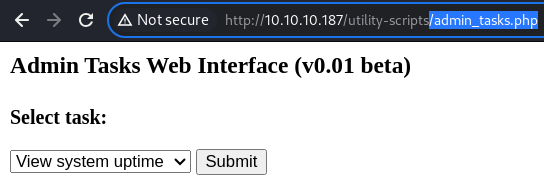 The
The admin_task.php file is present.
While this file contains a few functions, none of them can be exploited
phptest.php
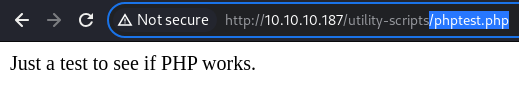 The
The phptest.php file also does exist in the LIVE web server here
info.php
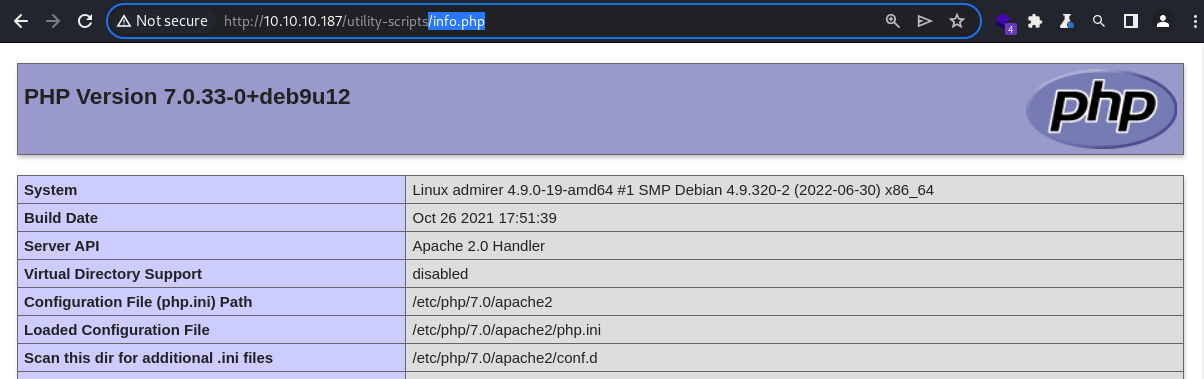 The
The info.php file exists
db_admin.php
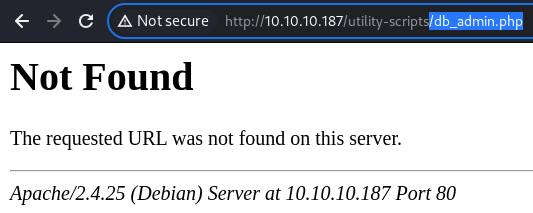 The
The db_admin file, on the other hand, is missing
This is rather an expected loss since the archive is a backup, presenting an older version of the web server
I will fuzz the directory to check if there’s anything more
Fuzzing /utility-script/
┌──(kali㉿kali)-[~/archive/htb/labs/admirer]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -u http://$IP/utility-scripts/FUZZ -ic -e .php
________________________________________________
:: Method : GET
:: URL : http://10.10.10.187/utility-scripts/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Extensions : .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htpasswd.php [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 97ms]
.htaccess [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 101ms]
.htpasswd [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 176ms]
.htaccess.php [Status: 403, Size: 277, Words: 20, Lines: 10, Duration: 185ms]
adminer.php [Status: 200, Size: 4295, Words: 189, Lines: 52, Duration: 97ms]
info.php [Status: 200, Size: 83814, Words: 4024, Lines: 962, Duration: 122ms]
phptest.php [Status: 200, Size: 32, Words: 8, Lines: 1, Duration: 145ms]
:: Progress: [40952/40952] :: Job [1/1] :: 350 req/sec :: Duration: [0:01:43] :: Errors: 0 ::There is one; adminer.php
adminer.php
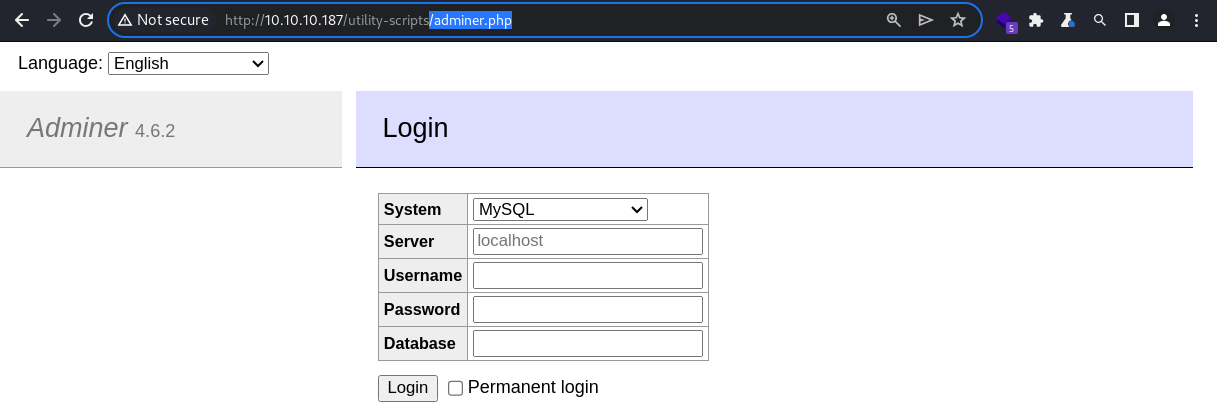 This seems to be a whole new thing. It will be thoroughly enumerated in the following section
This seems to be a whole new thing. It will be thoroughly enumerated in the following section