PEAS
Conducting an automated enumeration after performing a manual enumeration
*Evil-WinRM* PS C:\tmp> upload winPEASx64.exe .
Info: Uploading /home/kali/archive/htb/labs/university/winPEASx64.exe to C:\tmp\.
Data: 13122900 bytes of 13122900 bytes copied
Info: Upload successful!Using the established WinRM session to upload PEAS
 Executing PEAS
Executing PEAS
ENV
ÉÍÍÍÍÍÍÍÍÍ͹ User Environment Variables
È Check for some passwords or keys in the env variables
COMPUTERNAME: DC
PUBLIC: C:\Users\Public
LOCALAPPDATA: C:\Users\WAO\AppData\Local
PSModulePath: C:\Users\WAO\Documents\WindowsPowerShell\Modules;C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
PROCESSOR_ARCHITECTURE: AMD64
Path: C:\Program Files\Python310\Scripts\;C:\Program Files\Python310\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files (x86)\gnupg\bin;C:\Users\WAO\AppData\Local\Microsoft\WindowsApps
CommonProgramFiles(x86): C:\Program Files (x86)\Common Files
ProgramFiles(x86): C:\Program Files (x86)
PROCESSOR_LEVEL: 25
ProgramFiles: C:\Program Files
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.PY;.PYW;.CPL
USERPROFILE: C:\Users\WAO
SystemRoot: C:\Windows
ALLUSERSPROFILE: C:\ProgramData
DriverData: C:\Windows\System32\Drivers\DriverData
ProgramData: C:\ProgramData
PROCESSOR_REVISION: 0101
USERNAME: WAO
CommonProgramW6432: C:\Program Files\Common Files
CommonProgramFiles: C:\Program Files\Common Files
OS: Windows_NT
PROCESSOR_IDENTIFIER: AMD64 Family 25 Model 1 Stepping 1, AuthenticAMD
ComSpec: C:\Windows\system32\cmd.exe
SystemDrive: C:
TEMP: C:\Users\WAO\AppData\Local\Temp
NUMBER_OF_PROCESSORS: 4
APPDATA: C:\Users\WAO\AppData\Roaming
TMP: C:\Users\WAO\AppData\Local\Temp
ProgramW6432: C:\Program Files
windir: C:\Windows
USERDOMAIN: UNIVERSITY
USERDNSDOMAIN: university.htb
ÉÍÍÍÍÍÍÍÍÍ͹ System Environment Variables
È Check for some passwords or keys in the env variables
ComSpec: C:\Windows\system32\cmd.exe
DriverData: C:\Windows\System32\Drivers\DriverData
OS: Windows_NT
Path: C:\Program Files\Python310\Scripts\;C:\Program Files\Python310\;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files (x86)\gnupg\bin
PATHEXT: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.PY;.PYW
PROCESSOR_ARCHITECTURE: AMD64
PSModulePath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
TEMP: C:\Windows\TEMP
TMP: C:\Windows\TEMP
USERNAME: SYSTEM
windir: C:\Windows
NUMBER_OF_PROCESSORS: 4
PROCESSOR_LEVEL: 25
PROCESSOR_IDENTIFIER: AMD64 Family 25 Model 1 Stepping 1, AuthenticAMD
PROCESSOR_REVISION: 0101LAPS

LSA Protection

Credentials Guard

Cached Creds

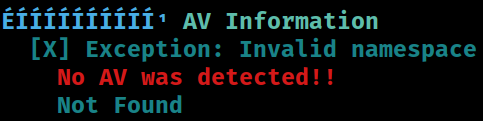
AV
UAC

PowerShell

KrbRelayUp

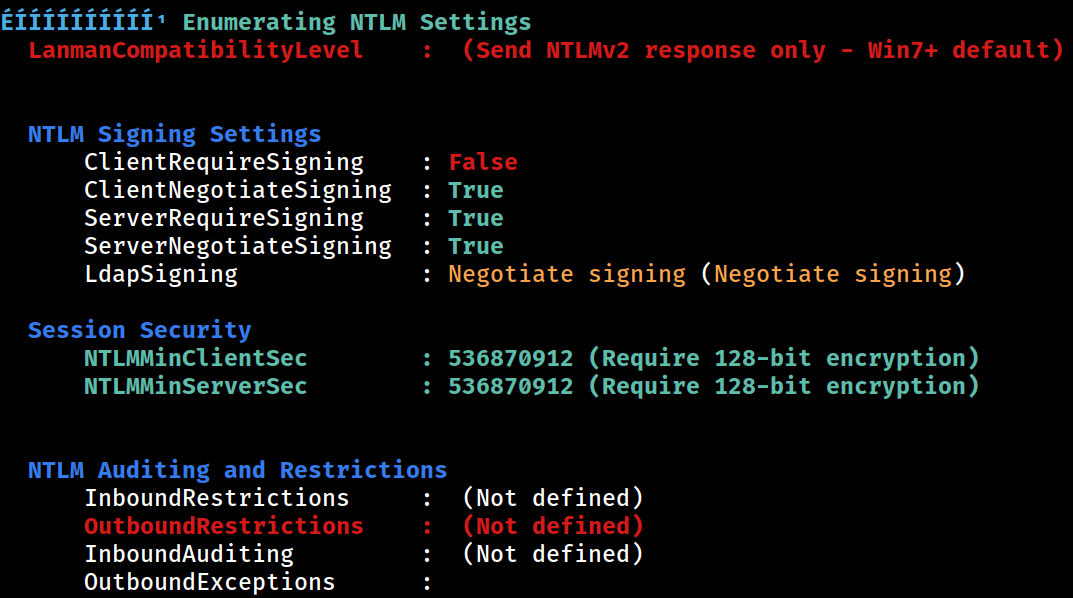
NTLM
AutoLogon

PS C:\> reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DefaultDomainName REG_SZ UNIVERSITY
DefaultUserName REG_SZ
DisableBackButton REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
ShellAppRuntime REG_SZ ShellAppRuntime.exe
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x544b8ff3
ShutdownFlags REG_DWORD 0x13
DisableLockWorkstation REG_DWORD 0x0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKeyDLL Hijacking

C:\Program Files (x86)\gnupg\bin as wao
Installed Programs

C:\Program Files\Automatiopn-ScriptsC:\Program Files\Hyper-V
Scheduled Tasks
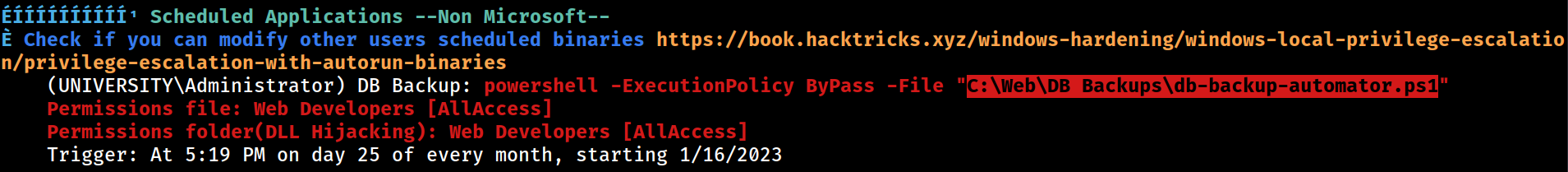
\DB Backup
adPEAS
*Evil-WinRM* PS C:\tmp> upload adPEAS.ps1 .
Info: Uploading /home/kali/archive/htb/labs/university/adPEAS.ps1 to C:\tmp\.
Data: 4159704 bytes of 4159704 bytes copied
Info: Upload successful!Using the established WinRM session to upload **adPEAS
 Executing adPEAS
Executing adPEAS
Domain / Domain Controller



Policies

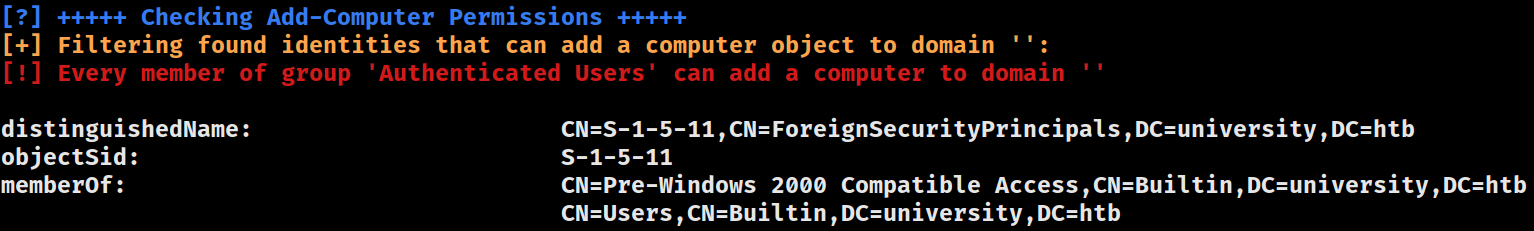
Add-Computer
DCSync

Choco.L
gMSA

GMSA-PClient01$

prometheus.university.htb
Computer with Unconstrained Delegation

WS-3$
Computer with Resource-Based Constrained Delegation


WS-3$
BloodHound

 Ingestion complete as part of the script
Ingestion complete as part of the script