Web
Nmap enumerated that the web server is using Drupal 7
 Webroot
I can confirm that it is a Drupal website
Webroot
I can confirm that it is a Drupal website
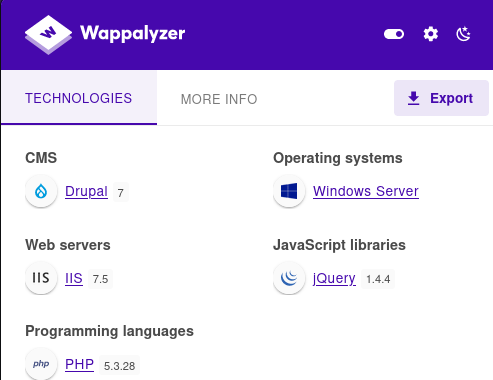 wappalyzer also checks the CMS
The website is written in PHP
wappalyzer also checks the CMS
The website is written in PHP
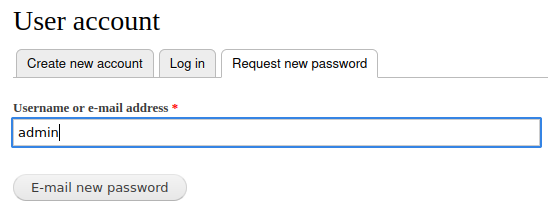
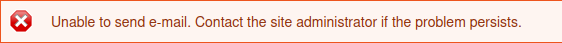
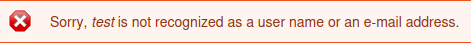 There is a login page at
Username enumeration via error message can be done
There is a login page at
Username enumeration via error message can be done
droopescan
droopescan is an excellent tool to enumerate Drupal-powered web servers. It’s designed for that.
┌──(kali㉿kali)-[~/archive/htb/labs]
└─$ droopescan scan drupal -u http://$IP:80/ -e a
[+] Plugins found:
ctools http://10.10.10.9:80/sites/all/modules/ctools/
http://10.10.10.9:80/sites/all/modules/ctools/CHANGELOG.txt
http://10.10.10.9:80/sites/all/modules/ctools/changelog.txt
http://10.10.10.9:80/sites/all/modules/ctools/CHANGELOG.TXT
http://10.10.10.9:80/sites/all/modules/ctools/LICENSE.txt
http://10.10.10.9:80/sites/all/modules/ctools/API.txt
libraries http://10.10.10.9:80/sites/all/modules/libraries/
http://10.10.10.9:80/sites/all/modules/libraries/CHANGELOG.txt
http://10.10.10.9:80/sites/all/modules/libraries/changelog.txt
http://10.10.10.9:80/sites/all/modules/libraries/CHANGELOG.TXT
http://10.10.10.9:80/sites/all/modules/libraries/README.txt
http://10.10.10.9:80/sites/all/modules/libraries/readme.txt
http://10.10.10.9:80/sites/all/modules/libraries/README.TXT
http://10.10.10.9:80/sites/all/modules/libraries/LICENSE.txt
services http://10.10.10.9:80/sites/all/modules/services/
http://10.10.10.9:80/sites/all/modules/services/README.txt
http://10.10.10.9:80/sites/all/modules/services/readme.txt
http://10.10.10.9:80/sites/all/modules/services/README.TXT
http://10.10.10.9:80/sites/all/modules/services/LICENSE.txt
profile http://10.10.10.9:80/modules/profile/
php http://10.10.10.9:80/modules/php/
image http://10.10.10.9:80/modules/image/
[+] Themes found:
seven http://10.10.10.9:80/themes/seven/
garland http://10.10.10.9:80/themes/garland/
[+] Possible version(s):
7.54
[+] Possible interesting urls found:
Default changelog file - http://10.10.10.9:80/CHANGELOG.txt
Default admin - http://10.10.10.9:80/user/login
[+] Scan finished (0:50:35.382811 elapsed)droopescan enumerated the CMS version
Drupal 7.54
Searchsploit
┌──(kali㉿kali)-[~/archive/htb/labs]
└─$ searchsploit drupal 7.54
------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------- ---------------------------------
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | php/webapps/44542.txt
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | php/webapps/44449.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploit) | php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC) | php/webapps/44448.py
Drupal < 8.5.11 / < 8.6.10 - RESTful Web Services unserialize() Remote Command Execution (Metasploit) | php/remote/46510.rb
Drupal < 8.6.10 / < 8.5.11 - REST Module Remote Code Execution | php/webapps/46452.txt
Drupal < 8.6.9 - REST Module Remote Code Execution | php/webapps/46459.py
------------------------------------------------------------------------------------------------------- ---------------------------------
shellcodes: No Results
papers: No ResultsDrupal 7.54 is vulnerable