Guly
After making some basic enumeration, I realized that I had access to a few files in the home directory of the guly user
bash-4.2$ ll
total 28K
4.0k -r--------. 1 guly guly 33 jan 27 15:05 user.txt
0 lrwxrwxrwx. 1 root root 9 sep 7 13:05 .bash_history -> /dev/null
4.0k drwxr-xr-x. 2 guly guly 4.0k sep 6 15:57 .
0 drwxr-xr-x. 3 root root 18 Jul 2 2019 ..
4.0K -r--r--r--. 1 root root 782 Oct 30 2018 check_attack.php
4.0K -rw-r--r-- 1 root root 44 Oct 30 2018 crontab.guly
4.0K -rw-r--r--. 1 guly guly 18 Oct 30 2018 .bash_logout
4.0K -rw-r--r--. 1 guly guly 193 Oct 30 2018 .bash_profile
4.0K -rw-r--r--. 1 guly guly 231 Oct 30 2018 .bashrcThere is a crontab file for the guly user and another interesting file, check_attack.php
crontab.guly
bash-4.2$ cat crontab.guly
*/3 * * * * php /home/guly/check_attack.phpThe crontab is set to execute the PHP script, /home/guly/check_attack.php, every 3 minute
check_attack.php
bash-4.2$ cat check_attack.php<?php
require '/var/www/html/lib.php';
$path = '/var/www/html/uploads/';
$logpath = '/tmp/attack.log';
$to = 'guly';
$msg= '';
$headers = "x-mailer: check_attack.php\r\n";
$files = array();
$files = preg_grep('/^([^.])/', scandir($path));
foreach ($files as $key => $value) {
$msg='';
if ($value == 'index.html') {
continue;
}
#echo "-------------\n";
#print "check: $value\n";
list ($name,$ext) = getnameCheck($value);
$check = check_ip($name,$value);
if (!($check[0])) {
echo "attack!\n";
# todo: attach file
file_put_contents($logpath, $msg, FILE_APPEND | LOCK_EX);
exec("rm -f $logpath");
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
echo "rm -f $path$value\n";
mail($to, $msg, $msg, $headers, "-F$value");
}
}
?>The PHP script above is basically an extension to the security measure that was placed in the web server.
It removes the would-be malicious files and notifies the guly user by mail.
I will go through a quick debugging
Debugging
bash-4.2$ php -a
Interactive shellphp > require '/var/www/html/lib.php';
php > $path = '/var/www/html/uploads/';
php > $logpath = '/tmp/attack.log';
php > $to = 'guly';
php > $msg= '';
php > $headers = "X-Mailer: check_attack.php\r\n";
php > $files = array();
php > $files = preg_grep('/^([^.])/', scandir($path));I first started an interactive PHP session and loaded the necessary variables
Notice the script still uses the /var/www/html/lib.php file that was also used in the web server
php > print_r($files);
Array
(
[2] => 10_10_14_11.jpg
[3] => 10_10_14_11.php.jpg
[4] => 127_0_0_1.png
[5] => 127_0_0_2.png
[6] => 127_0_0_3.png
[7] => 127_0_0_4.png
[8] => index.html
)I can then use the PHP print_r() function to print out the array variable, $files,
It lists out every files at the $path directory, except for the one, starting with the dot(.)
I can see the test file as well as the payload
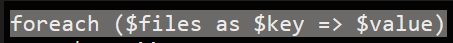 There is then a for-loop to store the index number as
There is then a for-loop to store the index number as $key and filename as $value
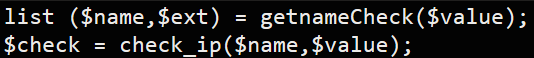
$value is then passed through a function, getnameCheck(), resulting the list of ($name,$ext)
$name and $value are then passed through the check_ip() function resulting a variable $check
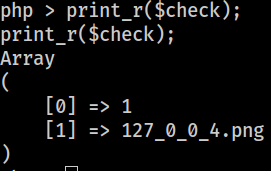 The array variable,
The array variable,$check, looks like this by now
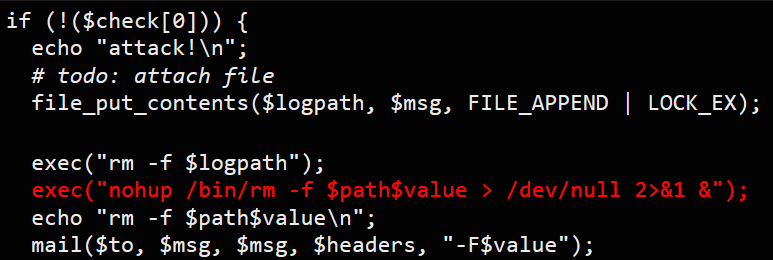 Then there is the important part.
If
Then there is the important part.
If $check[0] returns false, it echos out "attack!\m" and write the content to /tmp/attack.log as a log file, which eventually gets wiped out along with the original file as it gets shipped through a mail to the user
The whole process is basically preventing to write a file to the directory, and the only file that is allowed is uploaded through the web server with the renaming scheme.
exec("nohup /bin/rm -f $path$value > /dev/null 2>&1 &");
This line is particularly interesting as it uses the exec() function to make a system call to wipe the original file at the $path directory
I have control over $value variable because the /var/www/html/uploads directory is set to be write-able by anyone
Therefore, I may be able to inject OS command through here.
Testing
bash-4.2$ touch /var/www/html/uploads/testest123.phpI decided to double-check the whole process by testing it out. Creating a file that is not uploaded and following the naming scheme will go through the process
I will run an interactive PHP session again and load all the variables as well as features described above
bash-4.2$ php -a
Interactive shellphp > require '/var/www/html/lib.php';
php > $path = '/var/www/html/uploads/';
php > $logpath = '/tmp/attack.log';
php > $to = 'guly';
php > $msg= '';
php > $headers = "x-mailer: check_attack.php\r\n";
php >
php > $files = array();
php > $files = preg_grep('/^([^.])/', scandir($path));
php >
php > foreach ($files as $key => $value) {
php { $msg='';
php { if ($value == 'index.html') {
php { continue;
php { }
php { #echo "-------------\n";
php {
php { #print "check: $value\n";
php { list ($name,$ext) = getnameCheck($value);
php { $check = check_ip($name,$value);
php { }
}
php > print_r($check);
print_r($check);
Array
(
[0] =>
[1] => 4tt4ck on file testest123.php: prefix is not a valid ip
)upon executing print_r($check);, i can see that $check[0] is empty, indicating it is false, confirmed by the string below ‘4tt4ck on file test123.php: prefix is not a valid ip’
The script successfully detect the file as it wasn’t named properly, let alone validating the IP address. This wouldn’t necessarily wipe the whole thing as I only put the script without the logging, wiping, mailing part
However, if I re-run this… by directly executing the script on the command line
bash-4.2$ touch /var/www/html/uploads/testest123.php
bash-4.2$ php check_attack.php
attack!
rm -f /var/www/html/uploads/testest123.phpThere is that attack! from echo "attack!\n";
I can also see the wiping command
The file must be gone by now
bash-4.2$ ll
total 68K
4.0k drwxrwxrwx. 2 root root 4.0k jan 27 19:39 .
12k -rw-r--r-- 1 apache apache 9.1k jan 27 18:03 10_10_14_11.php.jpg
28k -rw-r--r-- 1 apache apache 25k jan 27 17:12 10_10_14_11.jpg
4.0K drwxr-xr-x. 4 root root 4.0K Jul 9 2019 ..
4.0K -rw-r--r--. 1 root root 3.9K Oct 30 2018 127_0_0_1.png
4.0K -rw-r--r--. 1 root root 3.9K Oct 30 2018 127_0_0_2.png
4.0K -rw-r--r--. 1 root root 3.9K Oct 30 2018 127_0_0_3.png
4.0K -rw-r--r--. 1 root root 3.9K Oct 30 2018 127_0_0_4.png
4.0K -r--r--r--. 1 root root 2 Oct 30 2018 index.htmlAs expected, /var/www/html/uploads/test123.php is gone
This confirms the OS command execution, which can be exploited.
Moving on to Privilege Escalation phase