Web
Nmap discovered a Web server on the target port 80
The running service is Apache httpd 2.4.41 ((Ubuntu))
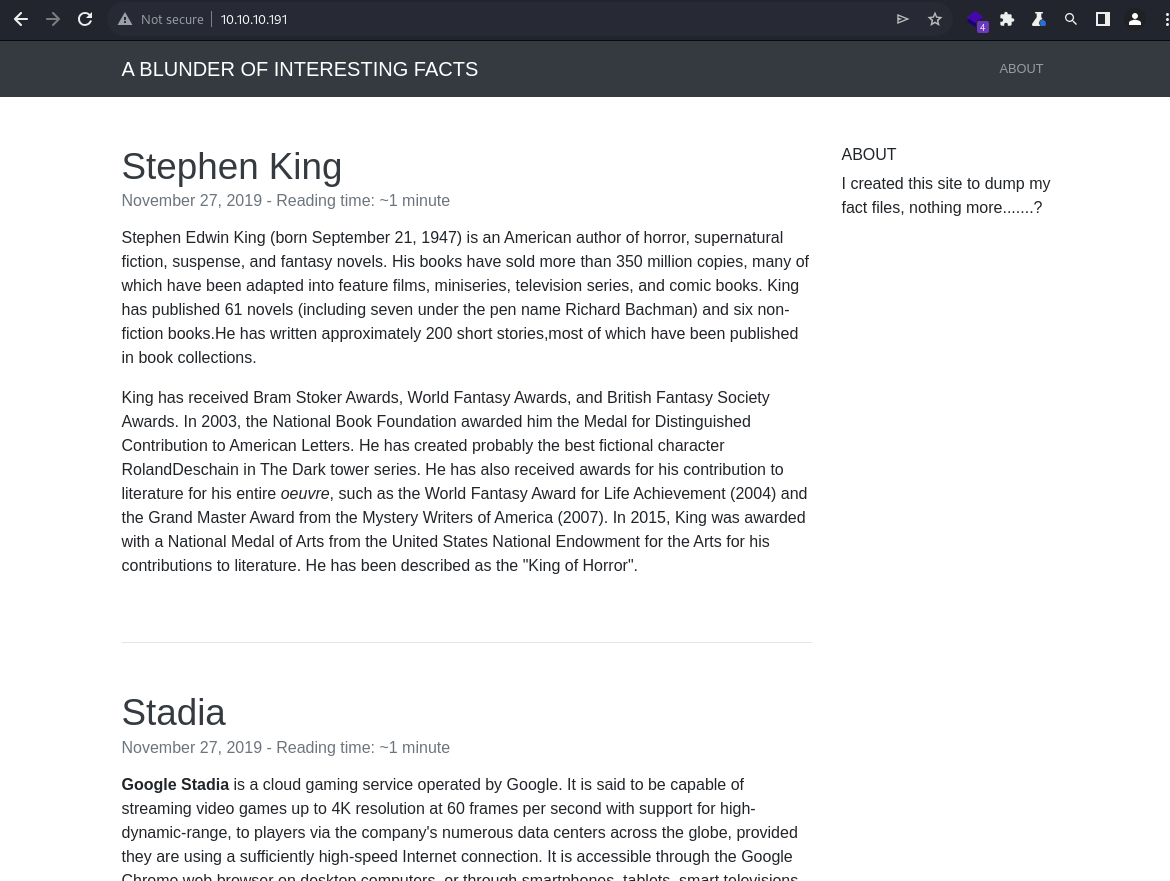 Webroot
Webroot
 It appears to be a blog and there are 3 articles
It appears to be a blog and there are 3 articles
About
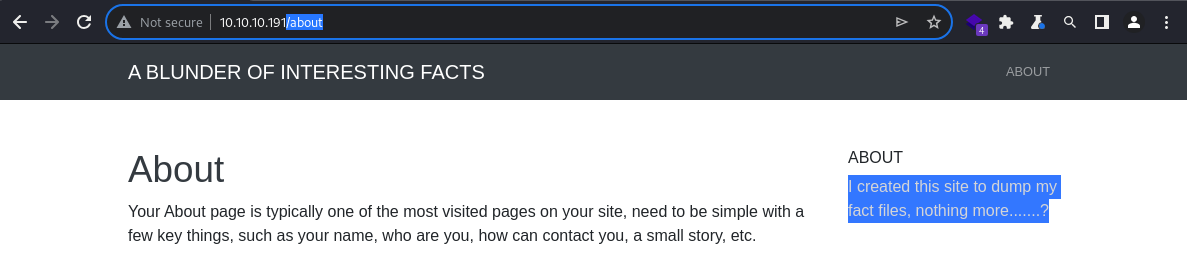 The
The /about page appear rather suggestive
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/blunder]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-lowercase-2.3-medium.txt -u http://$IP/FUZZ -ic -e .txt,.php
________________________________________________
:: Method : GET
:: URL : http://10.10.10.191/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
:: Extensions : .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
[status: 200, Size: 3281, Words: 225, Lines: 106, Duration: 167ms]
* fuzz: about
[status: 301, Size: 0, Words: 1, Lines: 1, Duration: 52ms]
* fuzz: admin
[status: 200, Size: 30, Words: 5, Lines: 1, Duration: 316ms]
* fuzz: install.php
[status: 200, Size: 22, Words: 3, Lines: 2, Duration: 115ms]
* fuzz: robots.txt
[status: 200, Size: 118, Words: 20, Lines: 5, Duration: 49ms]
* fuzz: todo.txt
[status: 200, Size: 3960, Words: 304, Lines: 111, Duration: 32ms]
* fuzz: usb
[status: 403, Size: 277, Words: 20, Lines: 10, Duration: 25ms]
* fuzz: server-status
:: Progress: [622890/622890] :: Job [1/1] :: 121 req/sec :: Duration: [1:04:26] :: Errors: 0 ::ffuf returned a few files and directories
robots.txt
 Empty
Empty
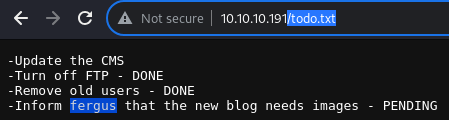
todo.txt
 The
The todo.txt file contains some interesting information
- Update the CMS
- This suggest that the website is built with a CMS and it’s outdated
- Turn off FTP - DONE
- This must the reason why Nmap was returning FTP data even though it’s “closed”
- Remove old users - DONE
- Inform fergus that the new blog needs images - PENDING
- The
fergususer might be the admin user
- The
admin
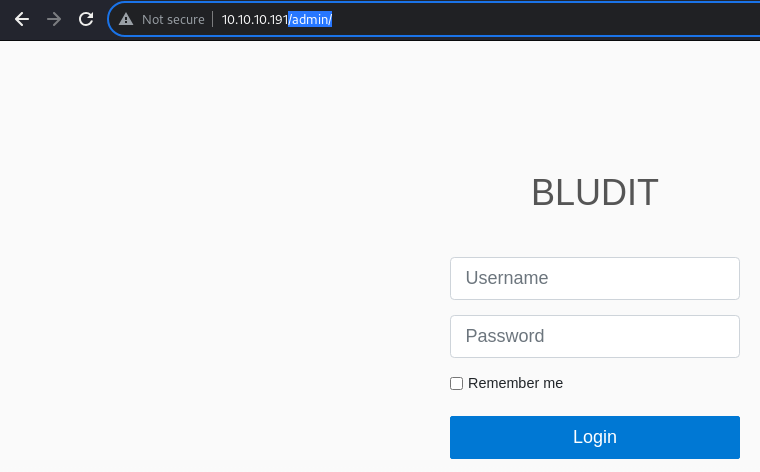 301 to
301 to /admin/
This appears to be the login page to the administrative panel
BLUDIT stands out there.
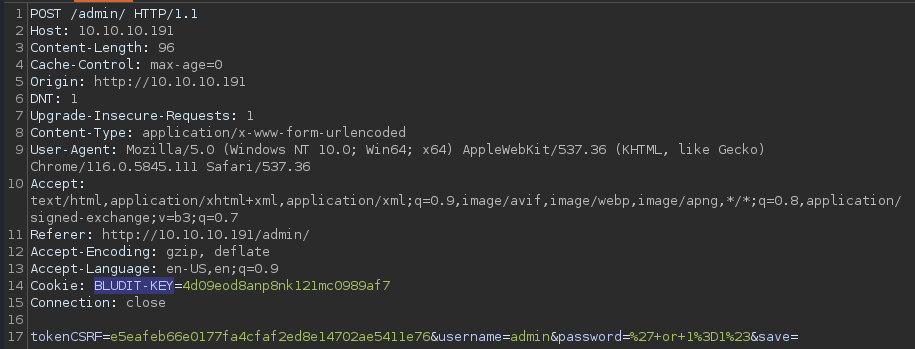 The POST request contains 4 parameters;
The POST request contains 4 parameters; tokenCSRF, username, password and save
tokenCSRF appears to be used for brute-force attack mitigation
Interestingly, it uses BLUDIT-KEY as a cookie
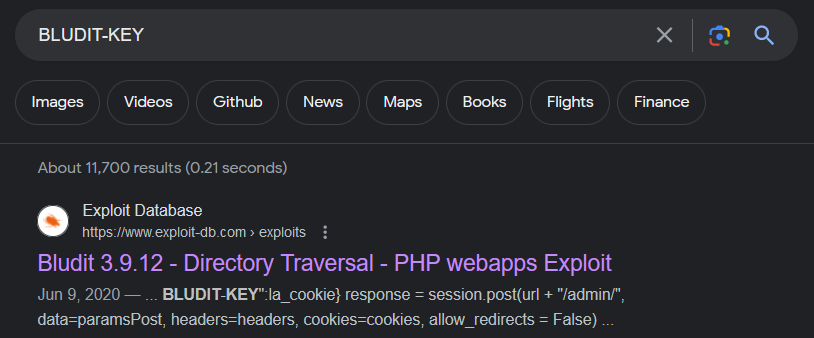 Looking it up online,
Looking it up online, BLUDIT-KEY appears to be a cookie used exclusively by a CMS; Bludit
This would mean that the website is built with Bludit CMS
Bludit
 bludit is a flat file content management system that can be used to set up websites or blogs. files are used to store the content JSON . The Remote Content plugin can also be used to publish content that is on a platform such as GitHub
bludit is a flat file content management system that can be used to set up websites or blogs. files are used to store the content JSON . The Remote Content plugin can also be used to publish content that is on a platform such as GitHub
 the source code is available through the official github page
the source code is available through the official github page
Version
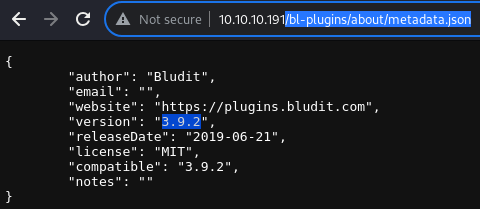 The version information is available at the
The version information is available at the /bl-plugins/about/metadata.json file
It’s Bludit 3.9.2
Vulnerability
┌──(kali㉿kali)-[~/archive/htb/labs/blunder]
└─$ searchsploit bludit 3.9.2
----------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
----------------------------------------------------------------------- ---------------------------------
Bludit 3.9.2 - Authentication Bruteforce Mitigation Bypass | php/webapps/48746.rb
Bludit 3.9.2 - Auth Bruteforce Bypass | php/webapps/48942.py
Bludit 3.9.2 - Authentication Bruteforce Bypass (Metasploit) | php/webapps/49037.rb
Bludit 3.9.2 - Directory Traversal | multiple/webapps/48701.txt
Bludit < 3.13.1 Backup Plugin - Arbitrary File Download (Authenticated | php/webapps/51541.py
----------------------------------------------------------------------- ---------------------------------
shellcodes: No Results
papers: No ResultsMultiple vulnerabilities found for Bludit 3.9.2
- [[Blunder_CVE-2019-17240#[CVE-2019-17240](https //nvd.nist.gov/vuln/detail/CVE-2019-17240)|CVE-2019-17240]]
- [[Blunder_CVE-2019-16113#[CVE-2019-16113](https //nvd.nist.gov/vuln/detail/CVE-2019-16113)|CVE-2019-16113]]