Jetty
Nmap discovered a Jetty server instance on the port 50000
The running service is Jetty 9.4.z-SNAPSHOT
 Webroot
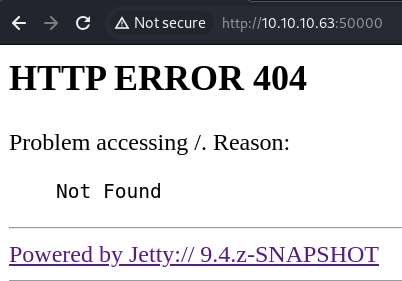
It returns 404
The footer indicates the version information;
Webroot
It returns 404
The footer indicates the version information; Jetty 9.4.z-SNAPSHOT
Vulnerability
 While looking up the instance version online reveals a few relevant information, none of them seems to precisely describe the target Jetty instance
While looking up the instance version online reveals a few relevant information, none of them seems to precisely describe the target Jetty instance
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/jeeves]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -t 200 -u http://$IP:50000/FUZZ -ic -e .txt
________________________________________________
:: Method : GET
:: URL : http://10.10.10.63:50000/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
askjeeves [status: 302, Size: 0, Words: 1, Lines: 1, Duration: 102ms]
:: Progress: [441094/441094] :: Job [1/1] :: 1763 req/sec :: Duration: [0:03:56] :: Errors: 0 ::ffuf returned a single directory; askjeeves
askjeeves is a web application hosted on the target port 80
There was not much going on as the web app appeared to configured badly
Jenkins
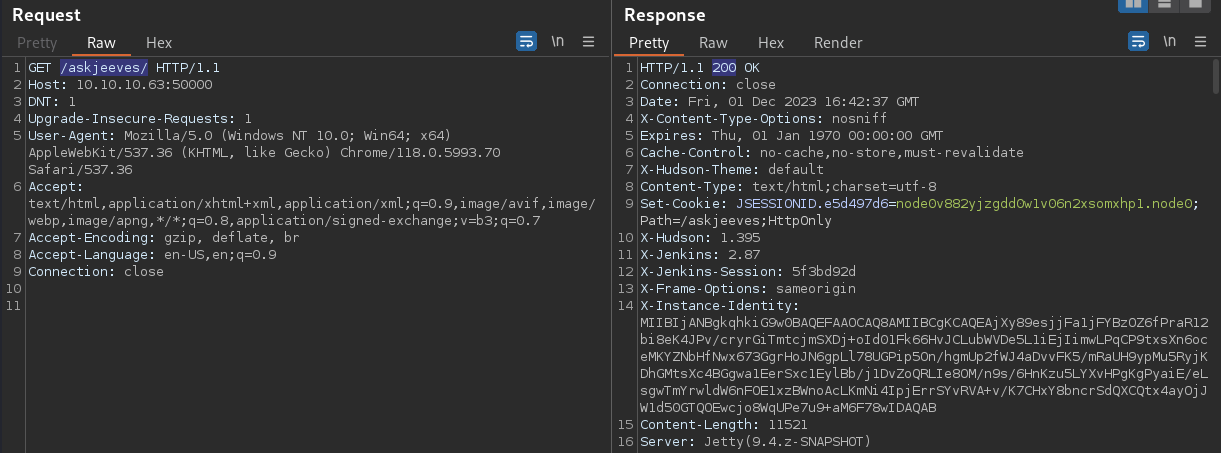 Sending a GET request to the
Sending a GET request to the /askjeeves/ directory returned 200 with the HTTP headers indicating a Jenkins instance
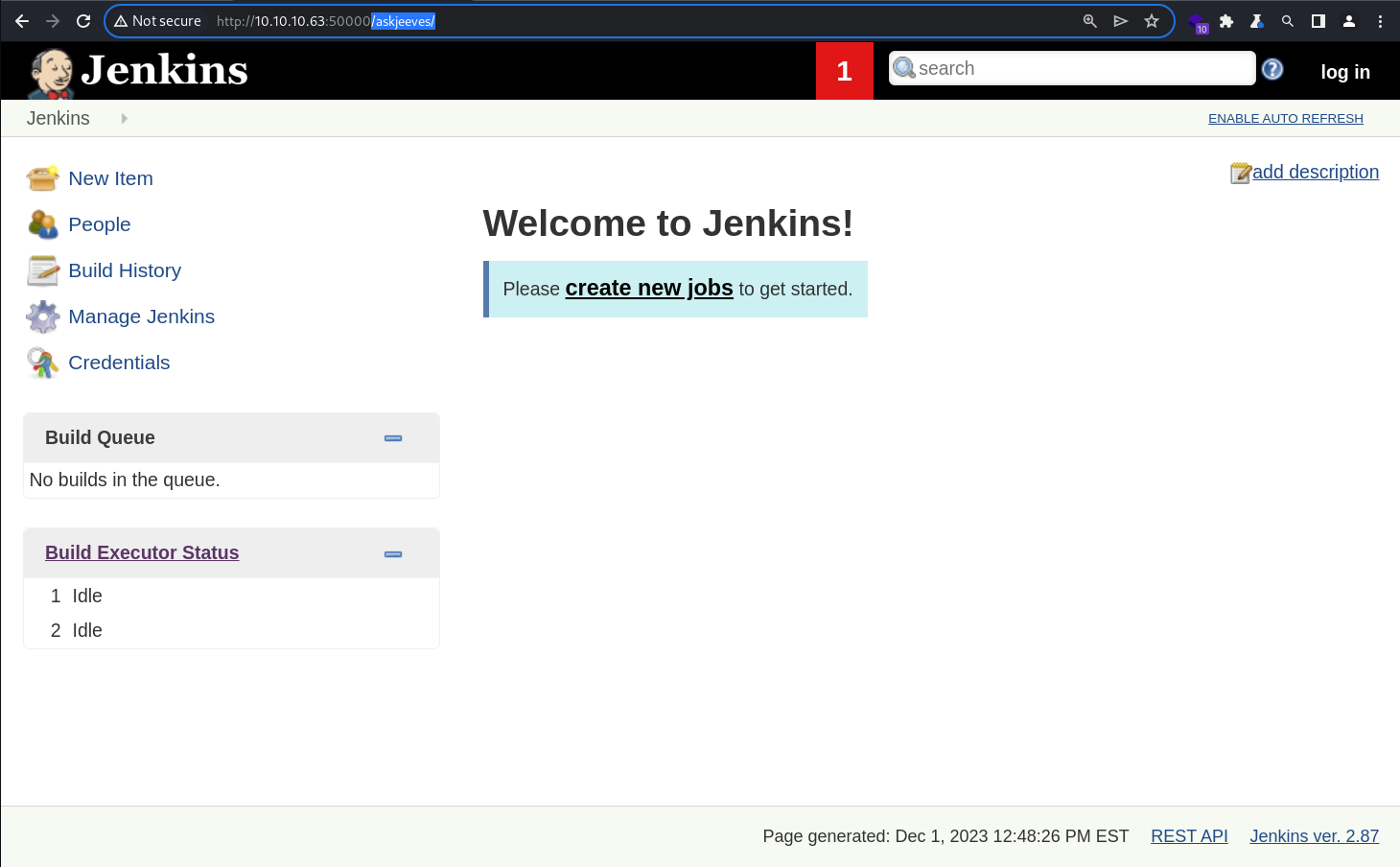 It is indeed Jenkins
It is indeed Jenkins
Users
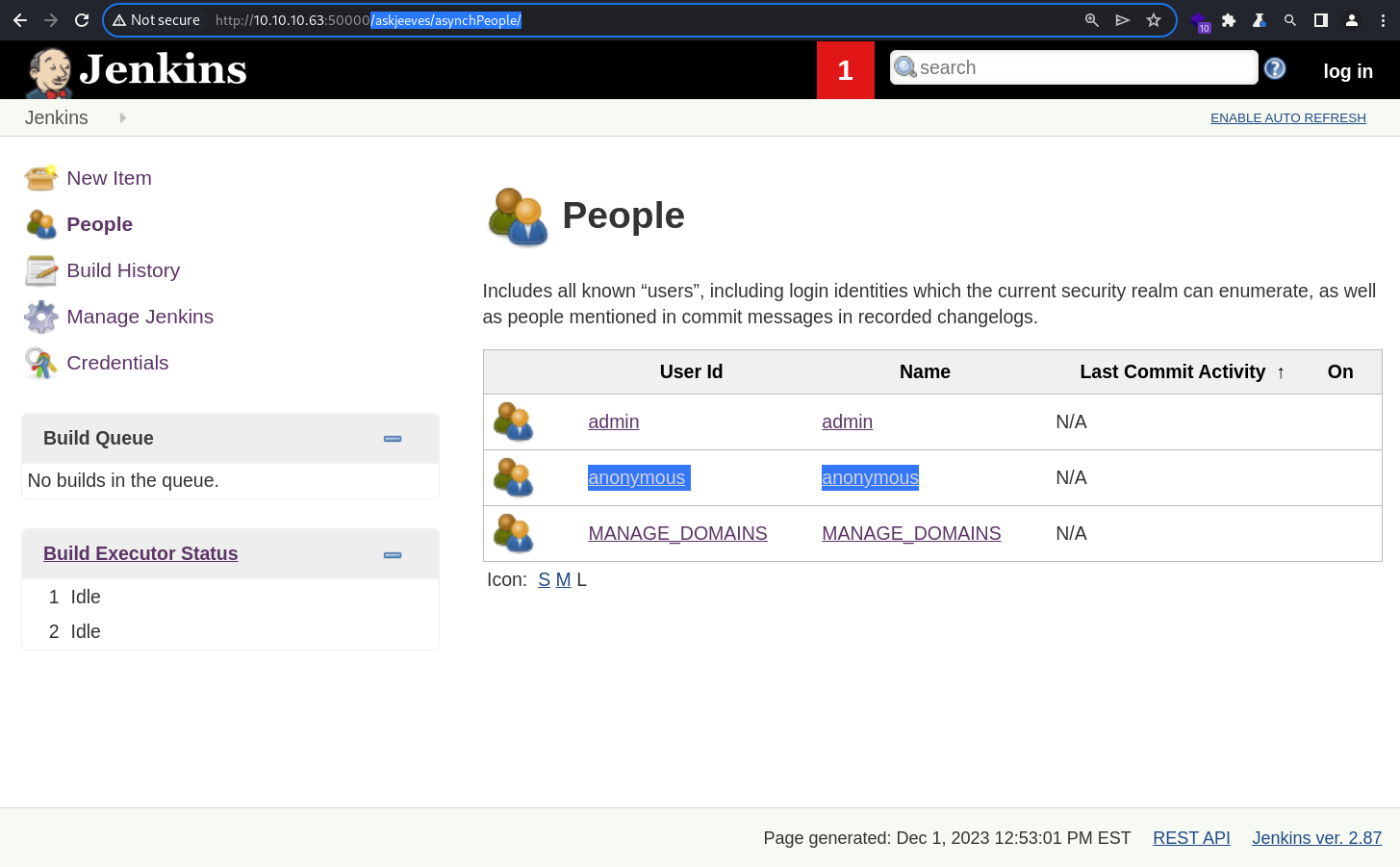 Checking the People menu reveals 3 users, including the
Checking the People menu reveals 3 users, including the anonymous user
This indicates that the target Jenkins instance support anonymous access. That’s how I am able to access it without authentication
Security
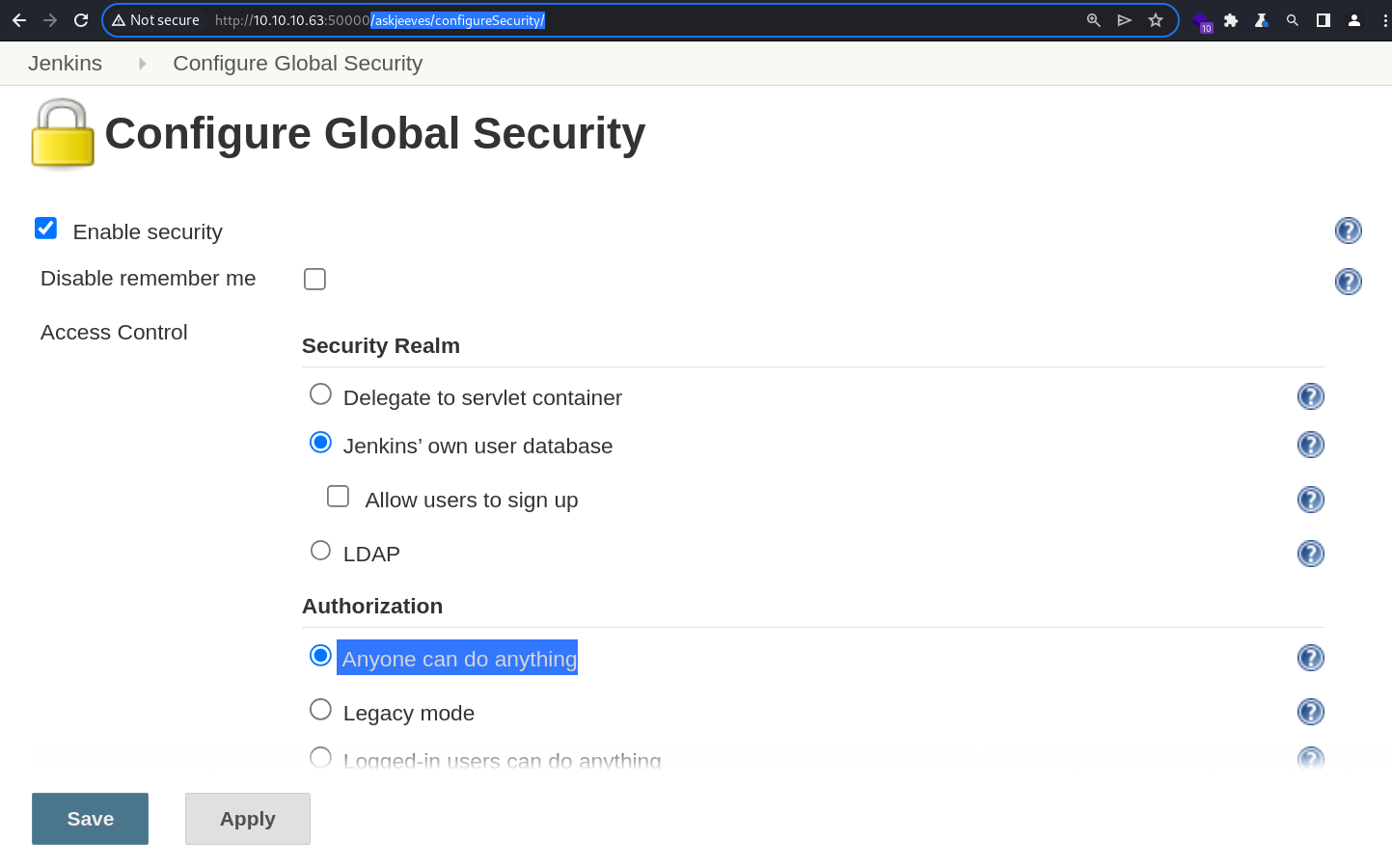 The Configure Global Security menu confirms the speculation made above.
The Configure Global Security menu confirms the speculation made above.
Authorization
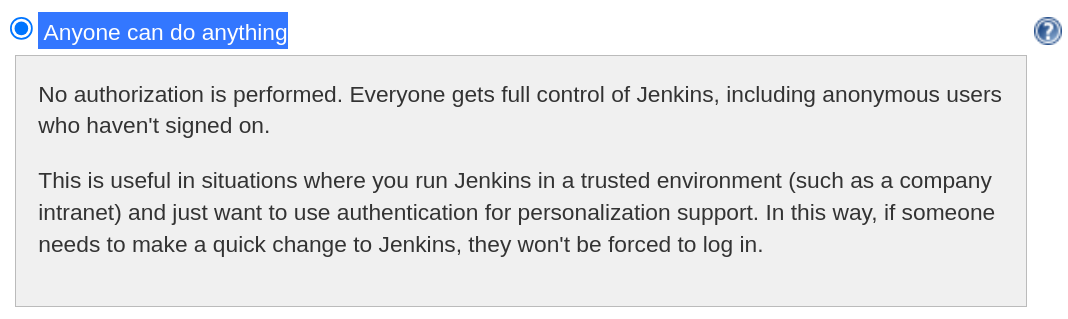 authorization is set to the Anyone can do anything option
This essentially means that I am able to read/build/execute
authorization is set to the Anyone can do anything option
This essentially means that I am able to read/build/execute
Script Console
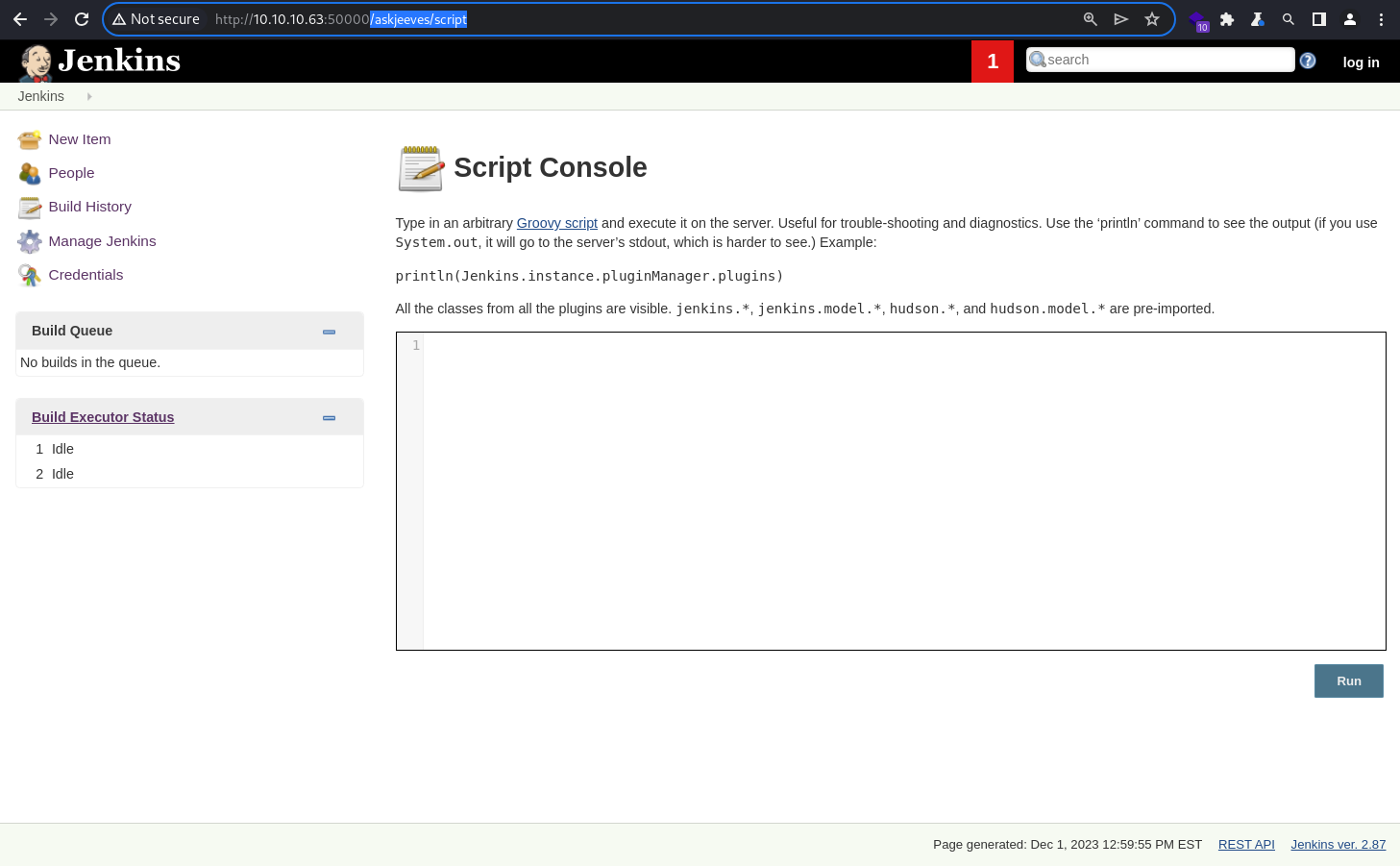 Script Console within Jenkins supports arbitrary Groovy scripts within the Jenkins controller runtime or in the runtime on agents.
Given the current security context, code execution is achievable through here.
Script Console within Jenkins supports arbitrary Groovy scripts within the Jenkins controller runtime or in the runtime on agents.
Given the current security context, code execution is achievable through here.
Moving on to Exploitation phase