Jenkins Installation
Checking for the installation of the target Jenkins instance after conducting basic enumeration
c:\Users\Administrator\.jenkins> icacls .
. jeeves\kohsuke:(OI)(CI)(F)
nt authority\system:(I)(OI)(CI)(F)
builtin\administrators:(I)(OI)(CI)(F)
jeeves\administrator:(I)(OI)(CI)(F)
Successfully processed 1 files; Failed processing 0 filesOne of the most interesting things that I have noticed upon gaining the initial foothold was the location
both hudson_home and jenkins_home environment variables are set to the c:\Users\Administrator\.jenkins directory, which is a sub-directory within the home directory of the administrator user
Ironically, the current user, kohsuke, has a complete control over the directory
jeeves Web App
C:\Users\Administrator\.jenkins> dir C:\inetpub\wwwroot
dir C:\inetpub\wwwroot
Volume in drive C has no label.
Volume Serial Number is 71A1-6FA1
Directory of C:\inetpub\wwwroot
11/05/2017 09:34 PM <DIR> .
11/05/2017 09:34 PM <DIR> ..
11/05/2017 07:39 PM 23,964 Ask-Jeeves-whatever-happened-to-32225327-270-301.jpg
11/05/2017 09:35 PM 50 error.html
11/05/2017 09:34 PM 503 index.html
11/05/2017 09:08 PM 463,431 jeeves.PNG
11/05/2017 09:27 PM 3,744 style.css
5 File(s) 491,692 bytes
2 Dir(s) 2,329,788,416 bytes freeAdditionally, the jeeves web app turns out to be completely static
Jenkins Secrets
these files are needed to decrypt jenkins secrets:
- JENKINS_HOME/secrets/hudson.util.Secret
- This file contains the secret key used by Jenkins to secure sensitive information and data.
- It’s used for encryption and decryption of sensitive data stored in Jenkins, including credentials, passwords, and other confidential information.
- The contents of this file should be kept confidential and protected from unauthorized access. Losing this file can have severe security consequences.
- It’s recommended to back up this file regularly to prevent data loss and potential security breaches.
- JENKINS_HOME/secrets/master.key
- This file is part of Jenkins’ security infrastructure and is used to encrypt and decrypt sensitive data, including credentials and secrets.
- It’s used in conjunction with the
hudson.util.Secretfile to provide an extra layer of security for Jenkins. - Like the
hudson.util.Secretfile, themaster.keyfile should be treated as highly sensitive and protected from unauthorized access. - Losing or compromising this file can jeopardize the security of Jenkins and its sensitive data.
such secrets can usually be found in:
- [[#configxml|JENKINS_HOME/users/
/*.xml]] - The
usersdirectory contains subdirectories for each user who has an account on the Jenkins server. - Inside the user’s subdirectory, you will find XML files that store user-specific configuration and settings.
- These files include details about the user’s preferences, permissions, and other configuration settings.
- For example,
config.xmlwithin a user’s directory may store information about their email address, full name, and other profile-related settings. - It’s essential to protect these files and ensure that only authorized users have access to their own user-specific configuration.
- The
Found something even better below!
Initial Admin Password
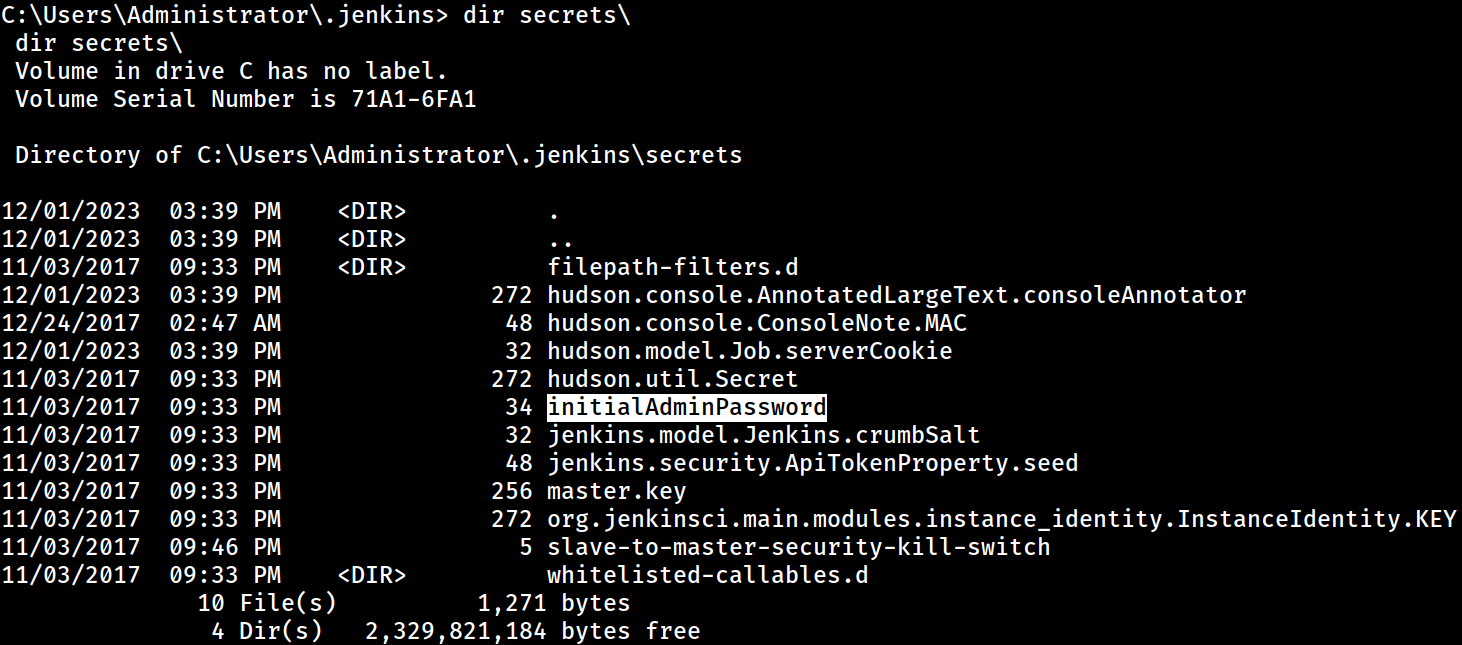 While prepping to extract and decrypt Jenkins secrets, I found an interesting file named,
While prepping to extract and decrypt Jenkins secrets, I found an interesting file named, secrets\initialAdminPassword
According to the official Jenkins documentation, the initialAdminPassword file is generated upon successful installation
C:\Users\Administrator\.jenkins> type secrets\initialAdminPassword
ccd3bc435b3c4f80bea8acca28aec491It’s always worth checking
 Authentication successful
Authentication successful
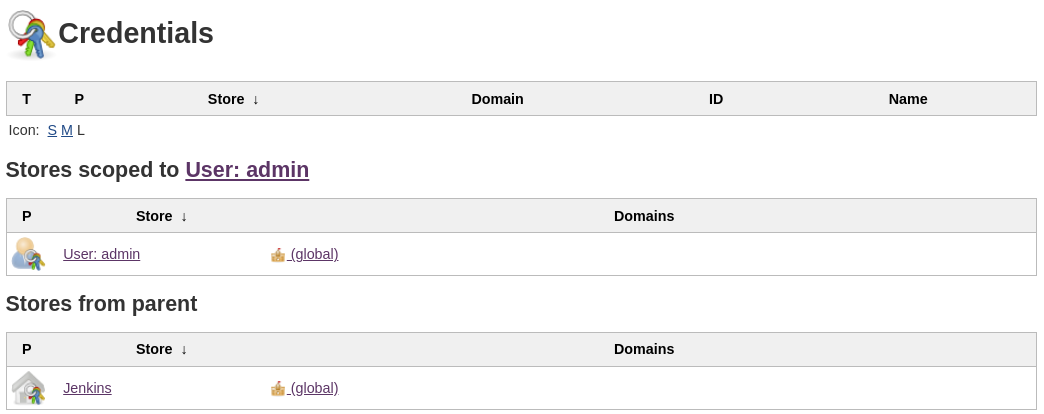
 Unfortunately, compromising the
Unfortunately, compromising the admin user on the target Jekins instance doesn’t really lead anywhere as the user shares the same security context as anonymous users
Additionally, there isn’t any user-specific build either