Web
Nmap discovered a web server on the target port 8080
The running service is Apache tomcat 9.0.38
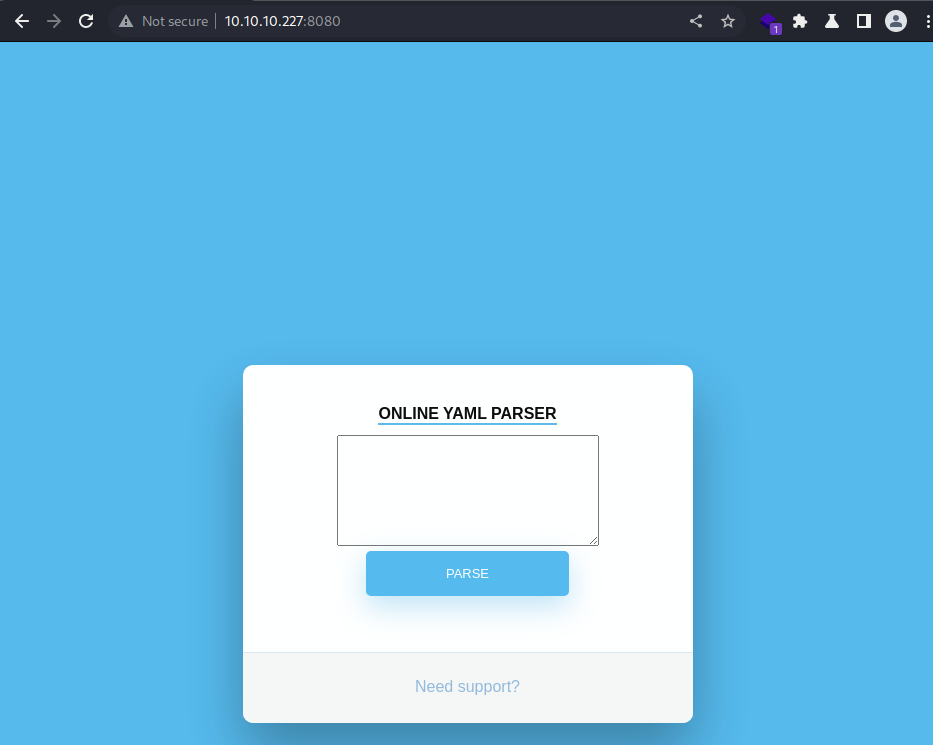 Webroot
It’s a YAML parser tool being hosted online
Webroot
It’s a YAML parser tool being hosted online
 The application is written in Java
The application is written in Java
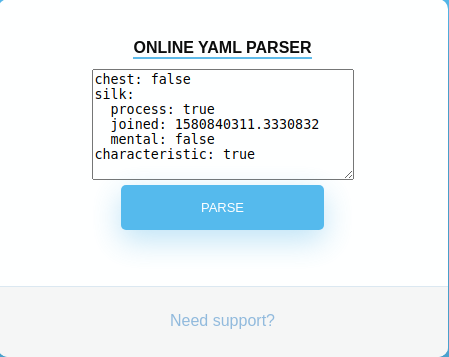 while i the need support? button doesn’t function at all, i will send in some dummy yaml data to test out the feature
while i the need support? button doesn’t function at all, i will send in some dummy yaml data to test out the feature
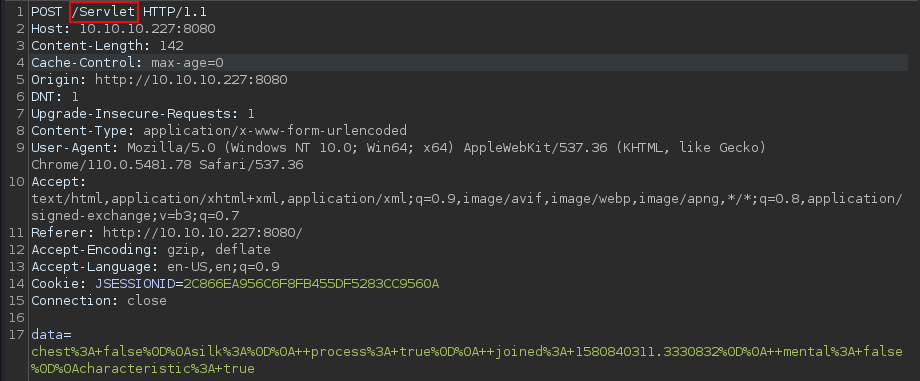 It send out a POST request to
It send out a POST request to /Servlet
It also uses JSESSIONID as a session cookie.
this tells me that the web server is on j2ee(Java 2 Enterprise Edition), which is expected, given the fact the it’s written in Java
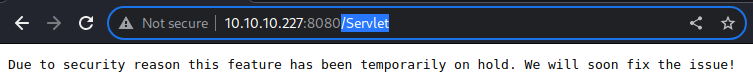 The response is rather interesting.
It states that the feature has been on a temporal hold due to some security reason
The response is rather interesting.
It states that the feature has been on a temporal hold due to some security reason
 The Ophiuchi earlier revealed that the web server is running off of
The Ophiuchi earlier revealed that the web server is running off of Apache Tomcat version 9.0.38
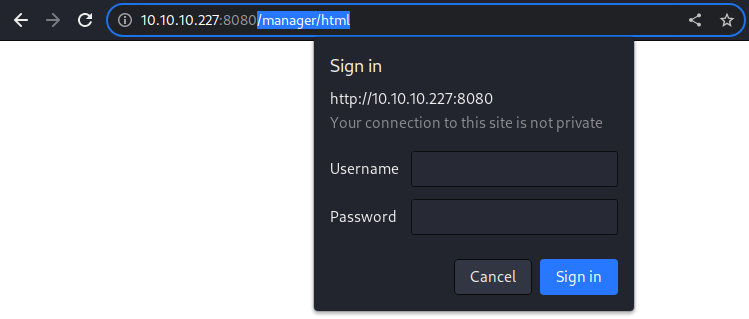 As expected in every Tomcat instance, navigating to
As expected in every Tomcat instance, navigating to /manager/html prompts the basic HTTP authentication
I tried some default credentials and none of them worked.
a typical entry in tomcat instance is through uploading a reverse shell war file, which requires access to the manager panel with a credential that has the manager role
I don’t have any credential for now. I will look elsewhere.
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/ophiuchi]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -u http://$IP:8080/FUZZ -ic -e .html,.php,.txt
________________________________________________
:: Method : GET
:: URL : http://10.10.10.227:8080/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Extensions : .html .php .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
Servlet [Status: 200, Size: 0, Words: 1, Lines: 1, Duration: 31ms]
manager [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 34ms]
test [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 29ms]
yaml [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 28ms]
:: Progress: [81904/81904] :: Job [1/1] :: 1397 req/sec :: Duration: [0:01:15] :: Errors: 0 ::Fuzzing the web server reveals 2 additional directories; test and yaml
/test
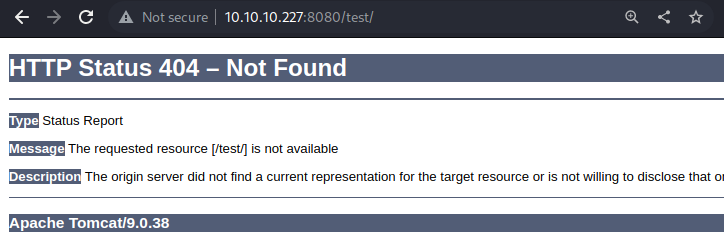 Navigating to the
Navigating to the /test directory, I got re-directed to /test/ and a 404
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/ophiuchi]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -u http://$IP:8080/test/FUZZ -ic -e .html,.php,.txt
________________________________________________
:: Method : GET
:: URL : http://10.10.10.227:8080/test/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Extensions : .html .php .txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
test.txt [Status: 200, Size: 5, Words: 1, Lines: 1, Duration: 29ms]
:: Progress: [81904/81904] :: Job [1/1] :: 1232 req/sec :: Duration: [0:01:01] :: Errors: 0 ::Fuzzing the /test/ directory reveals a file; /test/test.txt
/test/test.txt
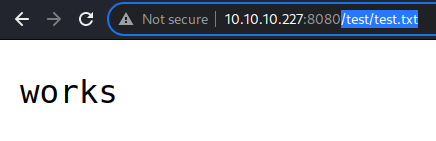 It just says “works”
What “works”?
It just says “works”
What “works”?
Nothing in the source code as well.
/yaml
 The
The /yaml directory is just the same main page.
It’s probably routed this way.
I tested the feature and it’s disabled just as seen earlier.
Structure
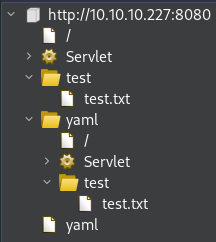 So far I have mapped the web structure this way
So far I have mapped the web structure this way
Vulnerability
 While testing things out, I found something interesting.
When I sent out a single quotation mark as if I were testing for SQLi
While testing things out, I found something interesting.
When I sent out a single quotation mark as if I were testing for SQLi
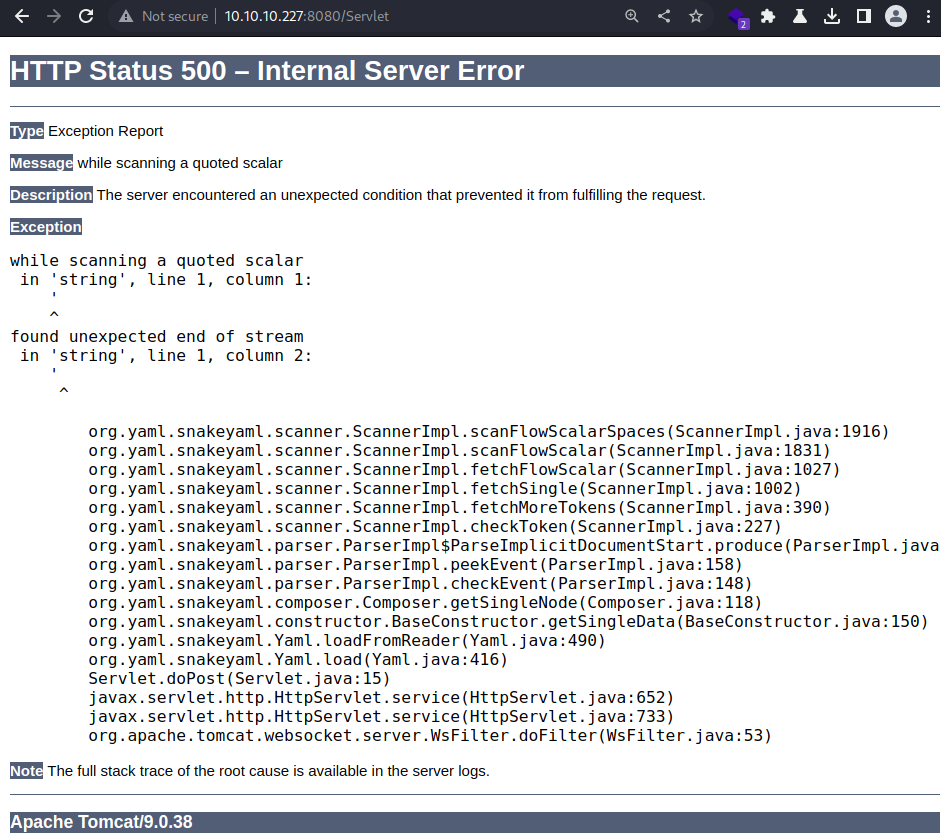 The web server responses with a code 500 with an error message from the application.
The error message indicates that the application is using snakeyaml to parse YAML data
The web server responses with a code 500 with an error message from the application.
The error message indicates that the application is using snakeyaml to parse YAML data
While the snakeyaml Java library has many vulnerabilities, I will focus on Java Deserialization