Webmin
matt@postman:~$ ps -auxwww | grep -i webmin
root 721 0.0 3.1 90944 28716 ? ss 10:58 0:00 /usr/bin/perl /usr/share/webmin/miniserv.pl /etc/webmin/miniserv.confAs discovered initially, the Webmin instance is running in the security context of the root user
This would mean that compromising the web application would elevate the current privilege to the root user
matt@postman:~$ dpkg --list | grep -i webmin
ii webmin 1.910 all web-based administration interface for Unix systemsAdditionally, the Webmin instance is severely outdated as identified earlier, 1.910, and suffers from an authenticated RCE vulnerability
matt@postman:~$ ll /etc/webmin/
total 548
drwxr-xr-x 118 root root 4096 Aug 26 2019 ./
drwxr-xr-x 82 root root 4096 Sep 29 2020 ../
[...REDACTED...]
-rw-r--r-- 1 root root 463 Aug 26 2019 config
-rw-r----- 1 root root 146 Aug 26 2019 Matt.acl
[...REDACTED...]While checking the configuration directory of the Webmin instance, I found 2 files that suggests a critical information
Webmin ACL
 Webmin supports ACL (Access Control List) much like that of Active Directory.
Webmin ACLs are used to control access to the Webmin web-based administration interface on Unix-like systems. They allow administrators to specify which users or groups have access to specific modules and what actions they can perform within those modules. Additionally, Webmin ACLs use a text-based format with rules and directives defined in
Webmin supports ACL (Access Control List) much like that of Active Directory.
Webmin ACLs are used to control access to the Webmin web-based administration interface on Unix-like systems. They allow administrators to specify which users or groups have access to specific modules and what actions they can perform within those modules. Additionally, Webmin ACLs use a text-based format with rules and directives defined in <USER>.acl files. These files specify access rights and restrictions for individual users or groups.
This suggests that the Matt user might be also a Webmin user
config
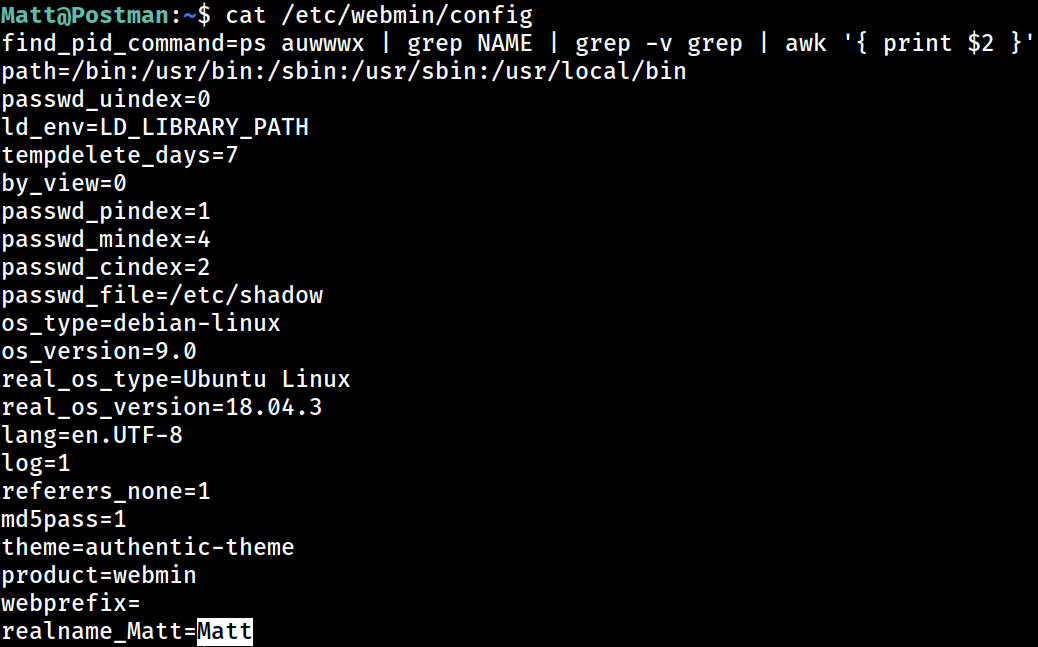 The
The config file confirms that the Matt user is a valid Webmin user
Since the Matt user has already been compromised, I can now move on to the [[Postman_Privilege_Escalation#[CVE-2019-12840](https //nvd.nist.gov/vuln/detail/CVE-2019-12840)|Privilege Escalation]] phase