IPsec
as openvpn is one of the popular TLS/SSL based VPN services, StrongSwan is the IPsec based counterpart.
- is an open-source IPsec based VPN solution that comes with pretty much every Unix system.
- is known for its high-performance, security and compatibility with other IPsec based VPN solutions.
- supports a wide range of encryption and authentication algorithms, including AES, 3DES, and Blowfish, as well as SHA1, SHA256, and SHA384
- is compliant with most of the IKE standards.
I will be using StrongSwan to connect to the IKE service with the pre-shared key extracted earlier
Client Configuration
Here are some good references on client configuration setup. I will refer to that. Linode tecmint
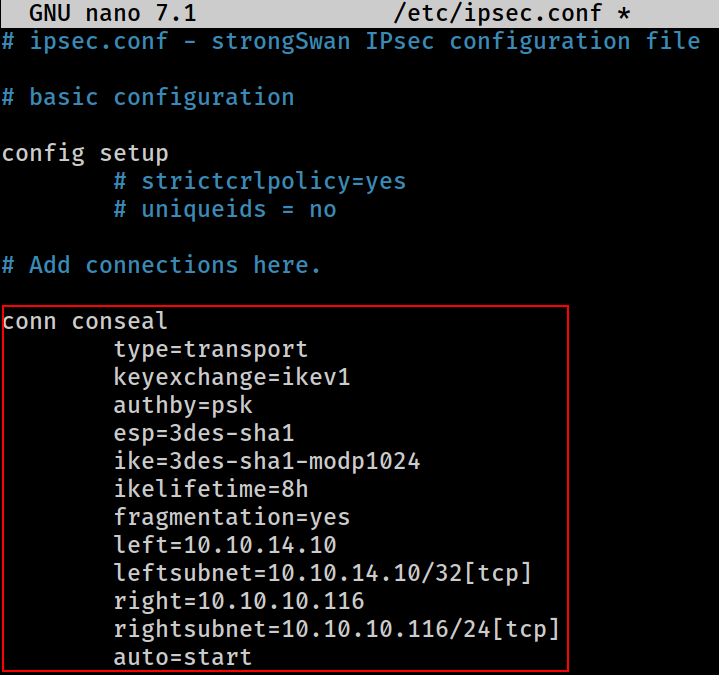 The configuration file is located at
The configuration file is located at /etc/ipsec.conf
Declare the connection, “conceal”, with:
typeset to transportkeyexchangeset to ikev1 as the IKE service uses IKE version 1authbyset to psk as described in the SAespset to 3des-sha1 as described in the SAikeset to 3des-sha1-modp1024 as described in the SAikelifetimeset to 8h as described in the SAfragmentationset to yes as described in the SAleftset to 10.10.14.10 for local (Kali)leftsubnetset to 10.10.14.10/24[tcp] for the local subnet and the desired layer 4 protocol to be usedrightset to 10.10.10.116 for remote (Target Host)rightsubnetset to 10.10.10.116/24[tcp] for the remote subnet and desired layer 4 protocol to be usedautoset to start for loading a connection and bringing it up immediately
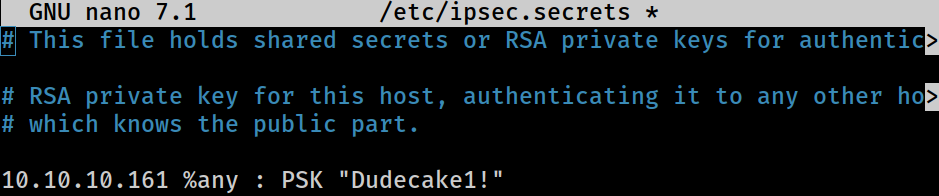 Now I need to add the extracted pre-shared key to the authentication file at
Now I need to add the extracted pre-shared key to the authentication file at /etc/ipsec.secrets
10.10.10.161 %any : PSK "Dudecake1!"
<HOST> USER : <AUTHENTICATION TYPE> <PASSWORD or KEY FILE>
This is the format
Connection
┌──(kali㉿kali)-[~/archive/htb/labs/conceal]
└─$ sudo ipsec start --nofork
Starting strongSwan 5.9.8 IPsec [starter]...
00[DMN] Starting IKE charon daemon (strongSwan 5.9.8, Linux 6.0.0-kali6-amd64, x86_64)
00[lib] providers loaded by openssl: default legacy
00[CFG] loading ca certificates from '/etc/ipsec.d/cacerts'
00[CFG] loading aa certificates from '/etc/ipsec.d/aacerts'
00[CFG] loading ocsp signer certificates from '/etc/ipsec.d/ocspcerts'
00[CFG] loading attribute certificates from '/etc/ipsec.d/acerts'
00[CFG] loading crls from '/etc/ipsec.d/crls'
00[CFG] loading secrets from '/etc/ipsec.secrets'
00[CFG] loaded IKE secret for 10.10.10.161 %any
00[lib] loaded plugins: charon aesni aes rc2 sha2 sha1 md5 mgf1 random nonce x509 revocation constraints pubkey pkcs1 pkcs7 pkcs12 pgp dnskey sshkey pem openssl pkcs8 fips-prf gmp agent xcbc hmac kdf gcm drbg attr kernel-netlink resolve socket-default connmark stroke updown eap-mschapv2 xauth-generic counters
00[LIB] dropped capabilities, running as uid 0, gid 0
00[JOB] spawning 16 worker threads
charon (314786) started after 20 ms
06[cfg] received stroke: add connection 'conceal'
06[CFG] added configuration 'conceal'
08[cfg] received stroke: initiate 'conceal'
08[IKE] initiating Main Mode IKE_SA transport[1] to 10.10.10.116
08[ENC] generating ID_PROT request 0 [ SA V V V V V ]
08[net] sending packet: from 10.10.14.10[500] to 10.10.10.116[500] (236 bytes)
09[net] received packet: from 10.10.10.116[500] to 10.10.14.10[500] (208 bytes)
09[ENC] parsed ID_PROT response 0 [ SA V V V V V V ]
09[IKE] received MS NT5 ISAKMPOAKLEY vendor ID
09[IKE] received NAT-T (RFC 3947) vendor ID
09[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
09[IKE] received FRAGMENTATION vendor ID
09[enc] received unknown vendor id: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
09[enc] received unknown vendor id: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
09[cfg] selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
09[ENC] generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
09[net] sending packet: from 10.10.14.10[500] to 10.10.10.116[500] (244 bytes)
10[net] received packet: from 10.10.10.116[500] to 10.10.14.10[500] (260 bytes)
10[ENC] parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
10[ENC] generating ID_PROT request 0 [ ID HASH N(INITIAL_CONTACT) ]
10[net] sending packet: from 10.10.14.10[500] to 10.10.10.116[500] (100 bytes)
12[net] received packet: from 10.10.10.116[500] to 10.10.14.10[500] (68 bytes)
12[ENC] parsed ID_PROT response 0 [ ID HASH ]
12[IKE] IKE_SA transport[1] established between 10.10.14.10[10.10.14.10]...10.10.10.116[10.10.10.116]
12[IKE] scheduling reauthentication in 28010s
12[IKE] maximum IKE_SA lifetime 28550s
12[ENC] generating QUICK_MODE request 4041634572 [ HASH SA No ID ID ]
12[net] sending packet: from 10.10.14.10[500] to 10.10.10.116[500] (220 bytes)
11[net] received packet: from 10.10.10.116[500] to 10.10.14.10[500] (188 bytes)
11[ENC] parsed QUICK_MODE response 4041634572 [ HASH SA No ID ID ]
11[cfg] selected proposal: ESP:3DES_CBC/HMAC_SHA1_96/NO_EXT_SEQ
11[IKE] CHILD_SA transport{1} established with SPIs c4b7f593_i 6c3a4a30_o and TS 10.10.14.10/32[tcp] === 10.10.10.116/32[tcp]
11[ENC] generating QUICK_MODE request 4041634572 [ HASH ]
11[net] sending packet: from 10.10.14.10[500] to 10.10.10.116[500] (60 bytes)
13[net] received packet: from 10.10.10.116[500] to 10.10.14.10[500] (76 bytes)
13[ENC] parsed QUICK_MODE response 4041634572 [ HASH N(INIT_CONTACT) ]
13[IKE] ignoring fourth Quick Mode messageConnecting
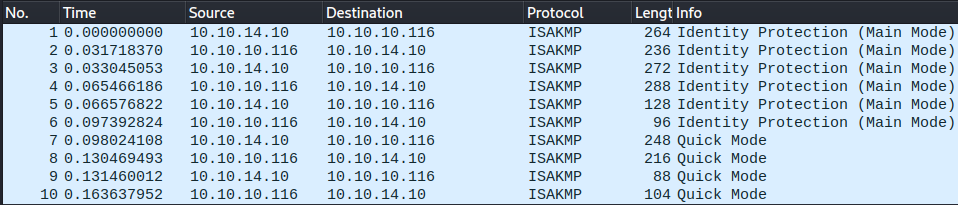 As shown in Wireshark, the connection is initialized and established over
As shown in Wireshark, the connection is initialized and established over ISAKMP
┌──(kali㉿kali)-[~/archive/htb/labs/conceal]
└─$ echo 'This is a testing packet' | nc $IP 80Now when I send out a packet to the target host
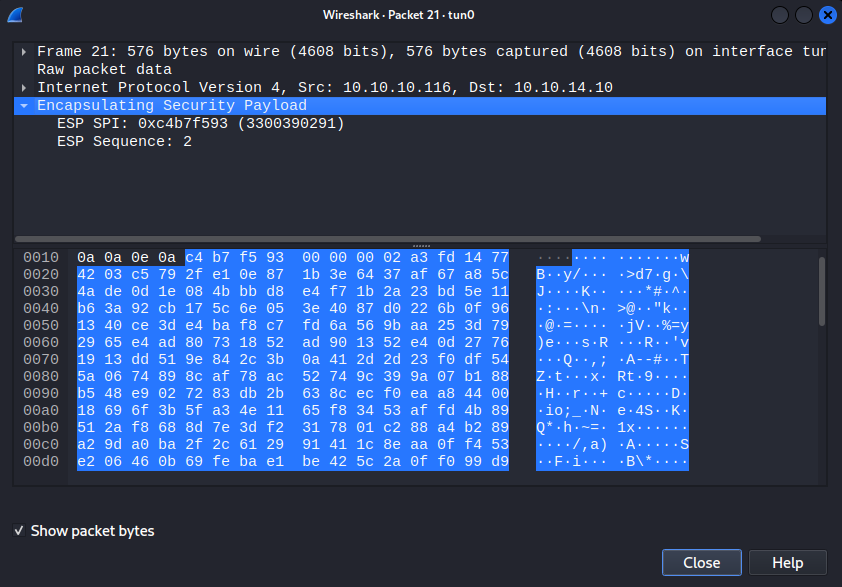 IPsec uses ESP(Encapsulating Security Payload), and payload gets all encrypted
IPsec uses ESP(Encapsulating Security Payload), and payload gets all encrypted
Now that the VPN connection is established, I should be able to reach those services that I could not reach