BloodHound
 BloodHound is a powerful tool used by adversaries to visualize and analyze Active Directory relationships, allowing them to quickly identify and exploit potential attack paths and privilege escalation opportunities within a network. It automates the reconnaissance phase of an attack, helping attackers pinpoint weak points and ultimately compromise Active Directory environments.
BloodHound is a powerful tool used by adversaries to visualize and analyze Active Directory relationships, allowing them to quickly identify and exploit potential attack paths and privilege escalation opportunities within a network. It automates the reconnaissance phase of an attack, helping attackers pinpoint weak points and ultimately compromise Active Directory environments.
Ingestion
Due to multiple installations of Python BloodHound ingestor, I will be setting one up in a virtual environment
┌──(kali㉿kali)-[~/…/htb/labs/blackfield/bloodhound]
└─$ python3 -m venv . ; source ./bin/activate Setting up a virtual environment
┌──(bloodhound)─(kali㉿kali)-[~/…/htb/labs/blackfield/bloodhound]
└─$ git clone https://github.com/dirkjanm/BloodHound.py ; pip3 install -e ./BloodHound.pyInstalling BloodHound.py
┌──(bloodhound)─(kali㉿kali)-[~/…/htb/labs/blackfield/bloodhound]
└─$ KRB5CCNAME=../support@dc01.blackfield.local.ccache BloodHound.py/bloodhound.py -d BLACKFIELD.LOCAL -u support -k -no-pass --auth-method kerberos -ns $IP -dc dc01.blackfield.local --zip -c ALL
Password:
INFO: Found AD domain: blackfield.local
INFO: Using TGT from cache
INFO: Found TGT with correct principal in ccache file.
INFO: Connecting to LDAP server: dc01.blackfield.local
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 18 computers
INFO: Connecting to LDAP server: dc01.blackfield.local
INFO: Found 316 users
INFO: Found 52 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer:
INFO: Querying computer: DC01.BLACKFIELD.local
INFO: Done in 00M 05S
INFO: Compressing output into 20231221111928_bloodhound.zipFor some reason, it still prompts for password, which I ignored
Using the TGT of the support account, the entire domain data can be ingested through bloodhound-python
Prep
┌──(kali㉿kali)-[~/…/htb/labs/blackfield/bloodhound]
└─$ sudo neo4j console
directories in use:
home: /usr/share/neo4j
config: /usr/share/neo4j/conf
logs: /usr/share/neo4j/logs
plugins: /usr/share/neo4j/plugins
import: /usr/share/neo4j/import
data: /usr/share/neo4j/data
certificates: /usr/share/neo4j/certificates
licenses: /usr/share/neo4j/licenses
run: /usr/share/neo4j/run
Starting Neo4j.
┌──(kali㉿kali)-[~/…/htb/labs/blackfield/bloodhound]
└─$ bloodhoundFiring up neo4j and bloodhound
 Upload complete
Upload complete
Kerberoast-able Accounts
 Interestingly,
Interestingly, krbtgt is the only kerberoast-able account according to bloodhound
This is rather contradictory to the Kerberoasting attempt made earlier
support
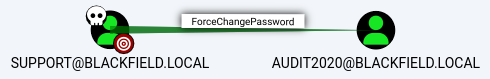 the
the support user has the forcechangepassword privilege over the audit2020 account
svc_backup
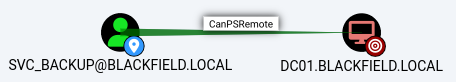 With a membership to the
With a membership to the Remote Management Users group, the svc_backup account is able to WinRM to the DC host; dc01.blackfield.local
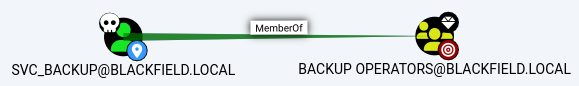 Additionally, the
Additionally, the svc_backup account has a membership to the Backup Operators group, which is a privileged group